The unceasing barrage of targeted email attacks that leverage zero-day software flaws to steal sensitive information from businesses and the U.S. government often are described as being ultra-sophisticated, almost ninja-like in stealth and anonymity. But according to expert analysis of several recent zero-day attacks – including the much publicized break-in at security giant RSA — the Chinese developers of those attack tools left clues aplenty about their identities and locations, with one apparent contender even Tweeting about having newly discovered a vulnerability days in advance of its use in the wild.
Zero-day threats are attacks which exploit security vulnerabilities that a software vendor learns about at the same time as the general public does; The vendor has “zero days” to fix the flaw before it gets exploited. RSA and others have labeled recent zero-day attacks as the epitome of the so-called “advanced persistent threat” (APT), a controversial term describing the daily onslaught of digital assaults launched by attackers who are considered highly-skilled, determined and possessed of a long-term perspective on their mission. Because these attacks often result in the theft of sensitive and proprietary information from the government and private industry, the details usually are shrouded in secrecy when law enforcement and national security investigators swoop in.
Open source information available about the tools used in recent attacks labeled APT indicates that some of the actors involved are doing little to cover their tracks: Not only are they potentially identifiable, they don’t seem particularly concerned about suffering any consequences from their actions.
Bragging rights may play a part in the attackers’ lack of duplicity. On Apr. 11, 2011, security experts began publishing information about a new zero-day attack that exploited a previously unknown vulnerability in Adobe‘s Flash Player software, a browser plug-in installed in 96 percent of the world’s Microsoft Windows PCs . The exploit code was hidden inside a Microsoft Word document titled “Disentangling Industrial Policy and Competition Policy.doc,” and reportedly was emailed to an unknown number of U.S. government employees and contractors.
Four days earlier, on Apr. 7, an individual on Twitter calling himself “Yuange” and adopting the humble motto “No. 1 hacker in China top hacker in the world,” tweeted a small snippet of exploit code, apparently to signal that he had advance knowledge of the attack:
“call [0x1111110+0x08].”
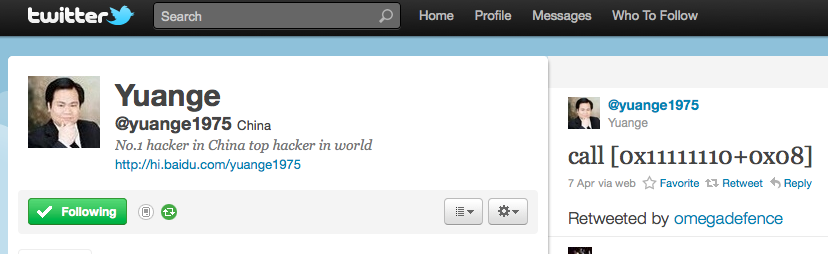
It wasn’t long before malware researchers were extracting that exact string from the innards of a Flash exploit that was landing in email inboxes around the globe.
Tweeting a key snippet of code hidden in a zero-day exploit in advance of its public release may seem like the hacker equivalent of Babe Ruth pointing to the cheap seats right before nailing a home run. But investigators say the Chinese Internet address used to download the malicious files in the early hours of the April Flash zero-day attacks — 123.123.123.123 — was in some ways bolder than most because that address would appear highly unusual and memorable to any reasonably vigilant network administrator.
This wasn’t the first time Yuange had bragged about advance knowledge of impending zero-day attacks. On Oct. 27, 2010, he boasted of authoring a zero-day exploit targeting a previously unknown vulnerability in Mozilla’s Firefox Web browser:
“Wrote the firefox 0day. You may see “for(inx=0’inx<0x8964;inx++). You should know why 0x8964 here.”
That same day, experts discovered that the Web site for the Nobel Peace Prize was serving up malicious software that exploited a new vulnerability in Firefox. An analysis of the attack code published by a member of Mozilla’s security team revealed the exact code snippet Yuange had tweeted.
On February 28, 2011, Yuange taunted on Twitter that new zero-day traps were being set:
“ready? new flash 0day is on the way.”
On Mar. 14, Adobe acknowledged that a new Flash flaw was being exploited via a booby-trapped Flash component tucked inside of Microsoft Excel files. Three days after that, EMC’s security division RSA dropped a bombshell: Secret files related to its widely used SecurID authentication tokens had been stolen in “an extremely sophisticated cyber attack.” A follow-up blog post from RSA’s Uri River two weeks later stated that the break-in was precipitated by the zero-day Adobe had warned about on Mar. 14, and that the lure used in the attack on RSA was an Excel file named “2011 Recruitment Plan.”
Continue reading →
![]() In the advisory that accompanies this update, Adobe said “there are reports of malware attempting to exploit one of the vulnerabilities, CVE-2011-0627, in the wild via a Flash (.swf) file embedded in a Microsoft Word (.doc) or Microsoft Excel (.xls) file delivered as an email attachment targeting the Windows platform. However, to date, Adobe has not obtained a sample that successfully completes an attack.”
In the advisory that accompanies this update, Adobe said “there are reports of malware attempting to exploit one of the vulnerabilities, CVE-2011-0627, in the wild via a Flash (.swf) file embedded in a Microsoft Word (.doc) or Microsoft Excel (.xls) file delivered as an email attachment targeting the Windows platform. However, to date, Adobe has not obtained a sample that successfully completes an attack.”