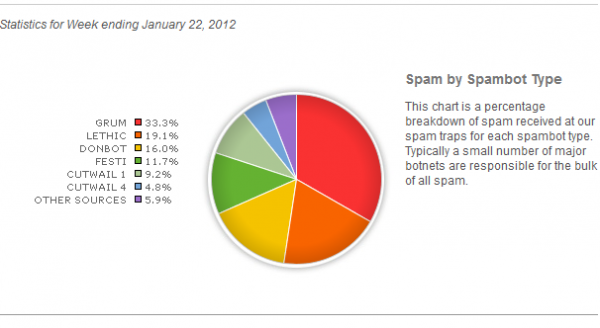
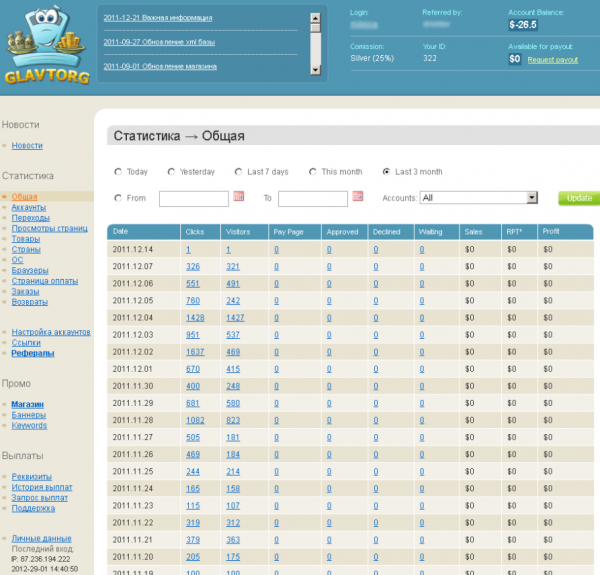
Microsoft on Monday named a Russian man as allegedly responsible for running the Kelihos botnet, a spam engine that infected an estimated 40,000 PCs. But closely held data seized from a huge spam affiliate program suggests that the driving force behind Kelihos is a different individual who commanded a much larger spam empire, and who is still coordinating spam campaigns for hire.
Kelihos shares a great deal of code with the infamous Waledac botnet, a far more pervasive threat that infected hundreds of thousands of computers and pumped out tens of billions of junk emails promoting shady online pharmacies. Despite the broad base of shared code between the two malware families, Microsoft classifies them as fundamentally different threats. The company used novel legal techniques to seize control over and shutter both botnets, sucker punching Waledac in early 2010 and taking out Kelihos last fall.
On Monday, Microsoft filed papers with a Virginia court stating that Kelihos was operated by Andrey N. Sabelnikov, a St. Petersburg man who once worked at Russian antivirus and security firm Agnitum. But according to the researcher who shared that intelligence with Microsoft — and confidentially with Krebs On Security weeks prior to Microsoft’s announcement — Sabelnikov is likely only a developer of Kelihos.
“It’s the same code with modifications,” said Brett Stone-Gross, a security analyst who came into possession of the Kelihos source code last year and has studied the two malware families extensively.
Rather, Stone-Gross said, the true coordinator of both Kelihos and Waledac is likely another Russian who is well known to anti-spam activists.
WHO IS SEVERA?
A variety of indicators suggest that the person behind Waledac and later Kelihos is a man named “Peter Severa” — known simply as “Severa” on underground forums. For several years running, Severa has featured in the Top 10 worst spammers list published by anti-spam activists at Spamhaus.org (he currently ranks at #5). Spamhaus alleged that Severa was the Russian partner of convicted U.S. pump-and-dump stock spammer Alan Ralsky, and indeed Peter Severa was indicted by the U.S. Justice Department in a related and ongoing spam investigation.
It turns out that the connection between Waledac and Severa is supported by data leaked in 2010 after hackers broke into the servers of pharmacy spam affiliate program SpamIt. The data also include tantalizing clues about Severa’s real identity.
In multiple instances, Severa gives his full name as “Peter North;” Peter Severa translates literally from Russian as “Peter of the North.” (The nickname may be a nod to the porn star Peter North, which would be fitting given that Peter North the spammer promoted shady pharmacies whose main seller was male enhancement drugs).
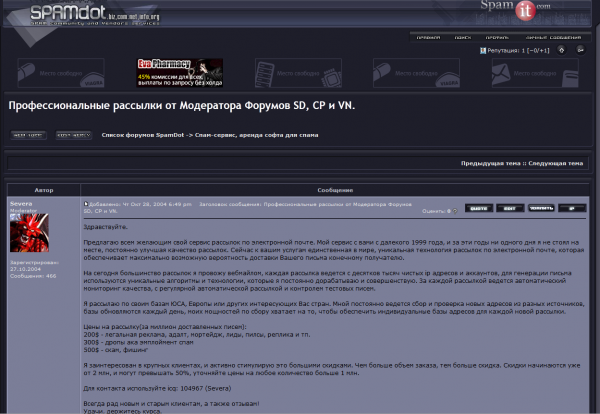
Spamdot.biz moderator Severa listing prices to rent his Waledac spam botnet.
According to SpamIt records, Severa brought in revenues of $438,000 and earned commissions of $145,000 spamming rogue online pharmacy sites over a 3-year period. He also was a moderator of Spamdot.biz (pictured at right), a vetted-members-only forum that included many of SpamIt’s top earners, as well as successful spammers/malware writers from other affiliate programs such as EvaPharmacy and Mailien.
Severa seems to have made more money renting his botnet to other spammers. For $200, vetted users could hire his botnet to send 1 million pieces of spam; junk email campaigns touting employment/money mule scams cost $300 per million, and phishing emails could be blasted out through Severa’s botnet for the bargain price of $500 per million.
Spamhaus says Severa’s real name may be Peter Levashov. The information Severa himself provided to SpamIt suggests that Spamhaus’s intelligence is not far off the mark.
Severa had his SpamIt earnings deposited into an account at WebMoney, a virtual currency popular in Russia and Eastern Europe. According to a source that has the ability to look up identity information tied to WebMoney accounts, the account was established in 2001 by someone who entered a WebMoney office and presented the Russian passport #454345544. The passport bore the name of a then 26-year-old from Moscow — Viktor Sergeevich Ivashov.
Continue reading →
 Sandboxing is an established security mechanism that runs the targeted application in a confined environment that blocks specific actions by that app, such as installing or deleting files, or modifying system information. The same technology has been built into the latest versions of Adobe Reader X, and it has been enabled for some time in Google Chrome, which contains its own integrated version of Flash. But this is the first time sandboxing has been offered in a public version of Flash for Firefox.
Sandboxing is an established security mechanism that runs the targeted application in a confined environment that blocks specific actions by that app, such as installing or deleting files, or modifying system information. The same technology has been built into the latest versions of Adobe Reader X, and it has been enabled for some time in Google Chrome, which contains its own integrated version of Flash. But this is the first time sandboxing has been offered in a public version of Flash for Firefox.