Yes, I realize that’s an ambitious title for a blog post about staying secure online, but there are a handful of basic security principles that — if followed religiously — can blunt the majority of malicious threats out there today.
Point-of-Sale Skimmers: Robbed at the Register
Michaels Stores said this month that it had replaced more than 7,200 credit card terminals from store registers nationwide, after discovering that thieves had somehow modified or replaced machines to include point of sale (POS) technology capable of siphoning customer payment card data and PINs. The specific device used by the criminal intruders has not been made public. But many devices and services are sold on the criminal underground to facilitate the surprisingly common fraud.
POS skimmers typically are marketed and sold in one of three ways: Pre-compromised POS terminals that can be installed at the cash register; Fake POS devices that do not process transactions but are designed to record data from swiped cards and PIN entries; or Do-it-yourself kits that include all parts, wiring and instructions needed to modify an existing POS terminal.
I spoke at length to a POS skimmer seller who has been peddling POS modification devices on an exclusive underground fraud forum for more than a year. From the feedback left on his profile it is clear he had many satisfied customers. Buyers specify the make and model of the POS equipment they want to compromise (this guy specializes in hacking VeriFone devices, but he also advertises kits for devices manufactured by POS makers Ingenico, Xyrun, TechTrex).
His skimmer kit includes a PIN pad skimmer and two small circuit boards; One is a programmable board with specialized software designed to interact with the real card reader and to store purloined data; The other is a Bluetooth-enabled board that allows the thief to wirelessly download the stolen card data from the hacked device using a laptop or smartphone.
The PIN pad skimmer is an ultra-thin membrane that is inserted underneath the original silicon PIN pad. It records every button pressed with a date and time stamp. The thief must also solder the two boards to the existing PIN pad device to hijack the machine’s power and data processing stream.
Something Old is New Again: Mac RATs, CrimePacks, Sunspots & ZeuS Leaks
New and novel malware appears with enough regularity to keep security researchers and reporters on their toes. But, often enough, there are seemingly new perils that really are just old threats that have been repackaged or stubbornly lingering reports that are suddenly discovered by a broader audience. One of the biggest challenges faced by the information security community is trying to decide which threats are worth investigating and addressing. To illustrate this dilemma, I’ve analyzed several security news headlines that readers forwarded to me this week, and added a bit more information from my own investigations.
I received more than two dozen emails and tweets from readers calling my attention to news that the source code for the 2.0.8.9 version of the ZeuS crimekit has been leaked online for anyone to download. At one point last year, a new copy of the ZeuS Trojan with all the bells and whistles was fetching at least $10,000. In February, I reported that the source code for the same version was being sold on underground forums. Reasonably enough, news of the source leak was alarming to some because it suggests that even the most indigent hackers can now afford to build their own botnets.
We may see an explosion of sites pushing ZeuS as a consequence of this leak, but it hasn’t happened yet. Roman Hüssy, curator of ZeusTracker, said in an online chat, “I didn’t see any significant increase of new ZeuS command and control networks, and I don’t think this will change things.” I tend to agree. It was already ridiculously easy to start your own ZeuS botnet before the source code was leaked. There are a number of established and relatively inexpensive services in the criminal underground that will sell individual ZeuS binaries to help novice hackers set up and establish ZeuS botnets (some will even sell you the bulletproof hosting and related amenities as part of a package), for a fraction of the price of the full ZeuS kit.
My sense is that the only potential danger from the release of the ZeuS source code is that more advanced coders could use it to improve their current malware offerings. At the very least, it should encourage malware developers to write more clear and concise user guides. Also, there may be key information about the ZeuS author hidden in the code for people who know enough about programming to extract meaning and patterns from it.
Are RATs Running Rampant?
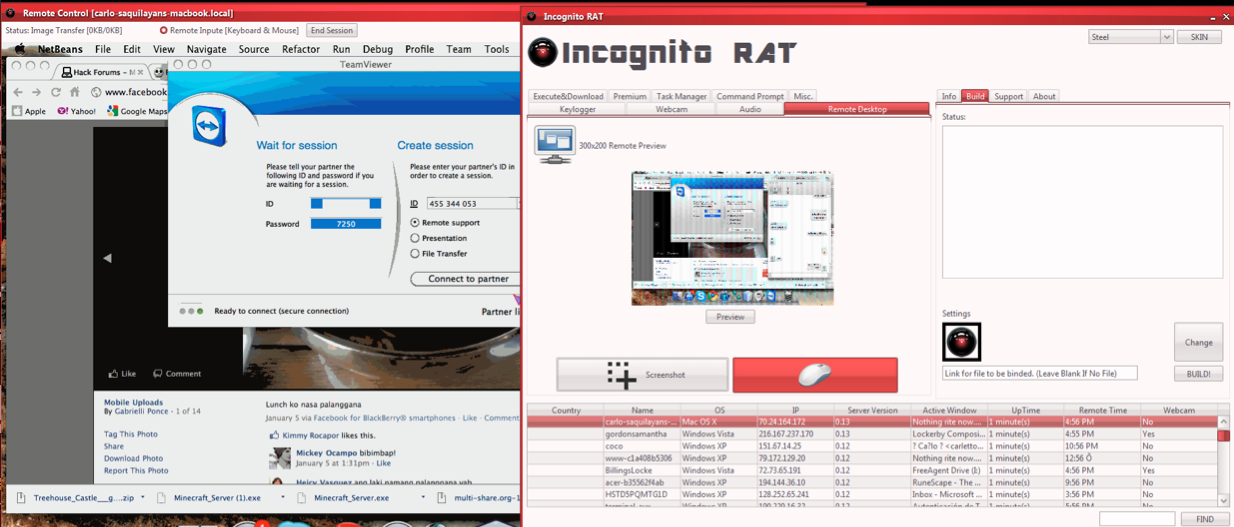
Last week, the McAfee blog included an interesting post about a cross-platform “remote administration tool” (RAT) called IncognitoRAT that is based on Java and can run on Linux, Mac and Windows systems. The blog post featured some good details on the functionality of this commercial crimeware tool, but I wanted to learn more about how well it worked, what it looks like, and some background on the author.
Those additional details, and much more, were surprisingly easy to find. For starters, this RAT has been around in one form or another since last year. The screen shot below shows an earlier version of IncognitoRAT being used to remotely control a Mac system.
The kit also includes an app that allows customers to control botted systems via jailbroken iPhones.
The following video shows this malware in action on a Windows system. This video was re-recorded from IncognitoRAT’s YouTube channel (consequently it’s a little blurry), but if you view it full-screen and watch carefully you’ll see a sequence in the video that shows how the RAT can be used to send e-mail alerts to the attacker. The person making this video is using Gmail; we can see a list of his Gchat contacts on the left; and his IP address at the bottom of the screen. That IP traces back to a Sympatico broadband customer in Toronto, Canada, which matches the hometown displayed in the YouTube profile where this video was hosted. A Gmail user named “Carlo Saquilayan” is included in the Gchat contacts visible in the video.
Critical Flash Player Update Plugs 11 Holes
Adobe has released another batch of security updates for its ubiquitous Flash Player software. This “critical” patch fixes at least 11 vulnerabilities, including one that reports suggest is being exploited in targeted email attacks.
![]() In the advisory that accompanies this update, Adobe said “there are reports of malware attempting to exploit one of the vulnerabilities, CVE-2011-0627, in the wild via a Flash (.swf) file embedded in a Microsoft Word (.doc) or Microsoft Excel (.xls) file delivered as an email attachment targeting the Windows platform. However, to date, Adobe has not obtained a sample that successfully completes an attack.”
In the advisory that accompanies this update, Adobe said “there are reports of malware attempting to exploit one of the vulnerabilities, CVE-2011-0627, in the wild via a Flash (.swf) file embedded in a Microsoft Word (.doc) or Microsoft Excel (.xls) file delivered as an email attachment targeting the Windows platform. However, to date, Adobe has not obtained a sample that successfully completes an attack.”
The vulnerabilities exist in Flash versions 10.2.159.1 and earlier for Windows, Mac, Linux and Solaris. To learn which version of Flash you have, visit this link. The new version for most platforms is 10.3.181.14; Android users should upgrade to Flash Player 10.3.185.21 available by browsing to the Android Marketplace on an Android phone; Google appears to have updated Chrome users automatically with this version of Flash back on May 6 (Chrome versions 11.0.696.68 and later have the newest Flash version).
Anonymous Splinter Group Implicated in Game Company Hack
The Web sites for computer game giant Eidos Interactive and one of its biggest titles — Deus Ex— were defaced and plundered on Wednesday in what appears to have been an attack from a splinter cell of the hacktivist group Anonymous. The hack comes just days after entertainment giant Sony told Congress that Anonymous members may have been responsible for break-ins that compromised personal information on more than 100 million customers of its PlayStation Network and other services.
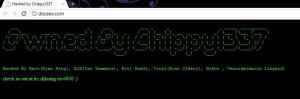
For several hours early Thursday morning, the Deus Ex Web site, user forum, and Eidos.com were unreachable. For a brief period late Wednesday evening, the sites displayed a defacement banner that read “Owned by Chippy1337” (click screen shot at right for a larger version), along with several names and hacker handles of those supposedly responsible for the break-in.
KrebsOnSecurity.com obtained an archived copy of the attackers’ online chatter as they were covering their tracks from compromising the sites. A hacker using the alias “ev0” discusses having defaced the sites and downloading some 9,000 resumes from Eidos. ev0 and other hackers discuss leaking “src,” which may refer to source code for Deus Ex or other Eidos games. In a separate conversation, the hackers also say they have stolen information on at least 80,000 Deus Ex users and that they plan to release the data on file-sharing networks.
Neither Eidos nor its parent company Square Enix Co. could be immediately reached for comment. (This may not be the first time Eidos was breached: In a story I wrote earlier this year, I detailed how hackers on an underground criminal forum claimed to be selling access to Eidos’ customer database).
The attack seems to have been engineered by a faction of the hacker collective that recently seized control over Internet relay chat (IRC) channels previously used by Anonymous to help plan and conduct other, high-profile attacks. According to several news sites which covered that coup, the Anonymous control networks were taken over by a 17-year-old hacker from the United Kingdom who uses the handle “Ryan,” (shown in the chat conversation included below using the nickname “Blackhatcat”).
Security Fixes for Microsoft Windows, Office
Microsoft issued just two updates today to fix at least three security flaws in its Windows and Microsoft Office products, a merciful respite following last month’s record-setting patch push. One of the patches issued today earned a critical rating, the company’s most serious.
![]() The critical patch is mainly a concern for enterprises that are running Windows Server 2003 and 2008 server operating systems. The Office update fixes two vulnerabilities in Microsoft Powerpoint, and affects older versions of Office, including Office XP, Office 2003, Office 2007 and 2004 for Mac (Office 2010 for Mac and Windows are not affected).
The critical patch is mainly a concern for enterprises that are running Windows Server 2003 and 2008 server operating systems. The Office update fixes two vulnerabilities in Microsoft Powerpoint, and affects older versions of Office, including Office XP, Office 2003, Office 2007 and 2004 for Mac (Office 2010 for Mac and Windows are not affected).
Updates are available through Windows Update or via Automatic Updates. As always, please leave a note in the comments if you experience any troubles during or after the installation of these patches.
Breach at Michaels Stores Extends Nationwide
Earlier this month, arts & crafts chain Michaels Stores disclosed that crooks had tampered with some point-of-sale devices at store registers in the Chicago area in a scheme to steal credit and debit card numbers and associated PINs. But new information on the investigation shows that many Michaels stores across the country have discovered compromised payment terminals.
 Investigators close to the case, but who asked to remain anonymous because they did not have permission to speak publicly, said that at least 70 compromised POS terminals have been discovered so far in Michaels stores from Washington D.C. to the West Coast.
Investigators close to the case, but who asked to remain anonymous because they did not have permission to speak publicly, said that at least 70 compromised POS terminals have been discovered so far in Michaels stores from Washington D.C. to the West Coast.
In an alert (PDF) sent to customers, Irving, Texas based Michaels Stores said it learned of the fraud after being contacted by banking and law enforcement authorities regarding fraudulent debit card transactions traced back to specific stores. The Beacon-News, a Chicago Sun-Times publication, last week cited local police reports from several victims, describing the typical fraud as multiple unauthorized withdrawals of up to $500 made from ATMs at banks on the West Coast. It remains unclear when affected stores were compromised.
Security Group Claims to Have Subverted Google Chrome’s Sandbox
A French security research firm boasted today that it has discovered a two-step process for defeating Google Chrome‘s sandbox, the security technology designed to protect the browser from being compromised by previously unknown security flaws. Experts say the discovery, if true, marks the first time hackers have figured out a way around the vaunted security layer, and almost certainly will encourage attackers to devise similar methods of subverting this technology in Chrome and other widely used software.
 In an advisory released today, VUPEN Security said: “We are (un)happy to announce that we have official Pwnd Google Chrome and its sandbox.” The post includes a video showing the exploitation of what VUPEN claims is a previously undocumented security hole in Chrome v.11.0.696.65 on Microsoft Windows 7 SP1 (x64).
In an advisory released today, VUPEN Security said: “We are (un)happy to announce that we have official Pwnd Google Chrome and its sandbox.” The post includes a video showing the exploitation of what VUPEN claims is a previously undocumented security hole in Chrome v.11.0.696.65 on Microsoft Windows 7 SP1 (x64).
“While Chrome has one of the most secure sandboxes and has always survived the Pwn2Own contest during the last three years, we have now uncovered a reliable way to execute arbitrary code on any installation of Chrome despite its sandbox, ASLR and DEP,” the advisory notes. ASLR and DEP are two of the key security defenses built into Windows Vista and Windows 7
Google spokesman Jay Nancarrow said the company was unable to verify VUPEN’s claims, because VUPEN hadn’t shared any information about their findings. “Should any modifications become necessary, users will be automatically updated to the latest version of Chrome,” Nancarrow wrote in an email to KrebsOnSecurity.
Chaouki Bekar, VUPEN’s CEO and head of research, confirmed that the company had no plans to share any details about their findings with Google, nor was it aware of any steps users could take to mitigate the threat from this attack.
“No, we did not alert Google as we only share our vulnerability research with our Government customers for defensive and offensive security,” Bekar wrote in response to an emailed request for comment. “Unfortunately, we are not aware of any mitigation to protect against these vulnerabilities.”
Jeremiah Grossman, a Web application security expert and chief technology officer for the security consultancy WhiteHat Security, called the news “quite serious.”
“We have governments competing for 0days, and we’re not even sure who the buyers are, maybe the US government didn’t get the 0day,” Grossman said “One way or the other, consumers are unprotected from an 0day we can’t really verify but probably exists. I think that’s quite serious.”
Scammers Swap Google Images for Malware
A picture may be worth a thousand words, but a single tainted digital image may be worth thousands of dollars for computer crooks who are using weaknesses in Google’s Image Search to foist malicious software on unsuspecting surfers.
For several weeks, some readers have complained that clicking on Google Images search results directed them to Web pages that pushed rogue anti-virus scareware via misleading security alerts and warnings. On Wednesday, the SANS Internet Storm Center posted a blog entry saying they, too, were receiving reports of Google Image searches leading to fake anti-virus sites. According to SANS, the attackers have compromised an unknown number of sites with malicious scripts that create Web pages filled with the top search terms from Google Trends. The malicious scripts also fetch images from third-party sites and include them in the junk pages alongside the relevant search terms, so that the automatically generated Web page contains legitimate-looking content.
Google’s Image Search bots eventually will index this bogus content. If users are searching for words or phrases that rank high in the current top search terms, it is likely that thumbnails from these malicious pages will be displayed beside other legitimate results.
As SANS handler Bojan Zdrnja explains, the exploit happens when a user clicks on one of these tainted thumbnails. “This is where the ‘vulnerability’ is,” Zdrnja wrote. “The user’s browser will automatically send a request to the bad page which runs the attacker’s script. This script checks the request’s referrer field and if it contains Google (meaning this was a click on the results page in Google), the script displays a small JavaScript script…[that] causes the browser to be redirected to another site that is serving FakeAV. Google is doing a relatively good job removing (or at least marking) links leading to malware in normal searches, however, Google’s image search seem to be plagued with malicious links.”
Denis Sinegubko, a Russian malware researcher who has been studying the fake anti-virus campaigns, called this tactic “the most efficient black hat trick ever,” and said it is exceedingly easy to set up. He said he’s received access logs from the owners of several hacked sites, and has used the data to estimate the traffic Google sends to these bogus image search pages. Sinegubko reckons that there are more than 5,000 hacked sites, and that the average site has been injected with about 1,000 of these bogus pages. The average page receives a visitor from Google approximately every 10 days, he said, which means Google is referring about a half million visits to fake anti-virus sites every day, or about 15 million visits each month.
For example, one of the hacked sites Sinegubko said he saw access logs for was in Croatia; It had a Google page rank of zero prior to being compromised with the phony image search scripts. The logs showed that the site had been hacked on Mar. 18, 2011, and that Google began indexing the tainted image pages the next day. “During the next 5 weeks it has indexed 27,200+ doorway pages on this site,” he wrote in a blog post on his findings. “During the same 5 weeks Google Image search has sent 140,000+ visitors to this small site.”
Sinegubko is developing an add-on for Firefox that can flag malicious Google Image search results by placing a red box around images that appear to link to hostile sites; Images with a pale pink box around them are hot-linked and may also be malicious, Sinegubko said. I tested the add-on (which is not ready for public release) searching for the cover art for the album “Kaputt” by the Canadian band Destroyer. As you can see from the image above, most of the images returned link to sites pushing fake anti-virus.
LastPass Forces Users to Pick Another Password
 LastPass.com, a free password management service that lets users unlock access to all of their password protected sites with a single master password, is forcing all of its approximately 1.25 million users to change their master passwords after discovering that intruders may have accessed the company’s user database.
LastPass.com, a free password management service that lets users unlock access to all of their password protected sites with a single master password, is forcing all of its approximately 1.25 million users to change their master passwords after discovering that intruders may have accessed the company’s user database.
In an alert posted to the company’s blog late Wednesday, LastPass said that on Tuesday morning it spotted a “traffic anomaly” — unexplained transfers of data — from one of the company’s databases. From that blog entry:
“Because we can’t account for this anomaly either, we’re going to be paranoid and assume the worst: that the data we stored in the database was somehow accessed. We know roughly the amount of data transfered [sic] and that it’s big enough to have transfered people’s email addresses, the server salt and their salted password hashes from the database. We also know that the amount of data taken isn’t remotely enough to have pulled many users encrypted data blobs.
If you have a strong, non-dictionary based password or pass phrase, this shouldn’t impact you – the potential threat here is brute forcing your master password using dictionary words, then going to LastPass with that password to get your data.Unfortunately not everyone picks a master password that’s immune to brute forcing.
To counter that potential threat, we’re going to force everyone to change their master passwords.”
LastPass consists of a core software application that sits on user machines, and a browser plug-in. Passwords are stored on the user’s system, so that no one at LastPass can access the information. What the company does keep is an encrypted blob of gibberish data that is generated by taking the user’s master password and email address and hashing the two. Any sensitive data saved to an account is secured by the encryption key on the user’s system and then sent to LastPass. Since the user’s encryption key is locally created each time users submit their master password and email to LastPass, all that the company stores is users’ encrypted data.