Since the dawn of the Internet, tutorials showing would-be scammers how to fleece others have been available online. But for novices who can’t be bothered to scour the Net for these far flung but free resources, the tricks of the trade now can be learned through the equivalent of community college classes in e-thievery, or or via intensive, one-on-one online apprenticeships.
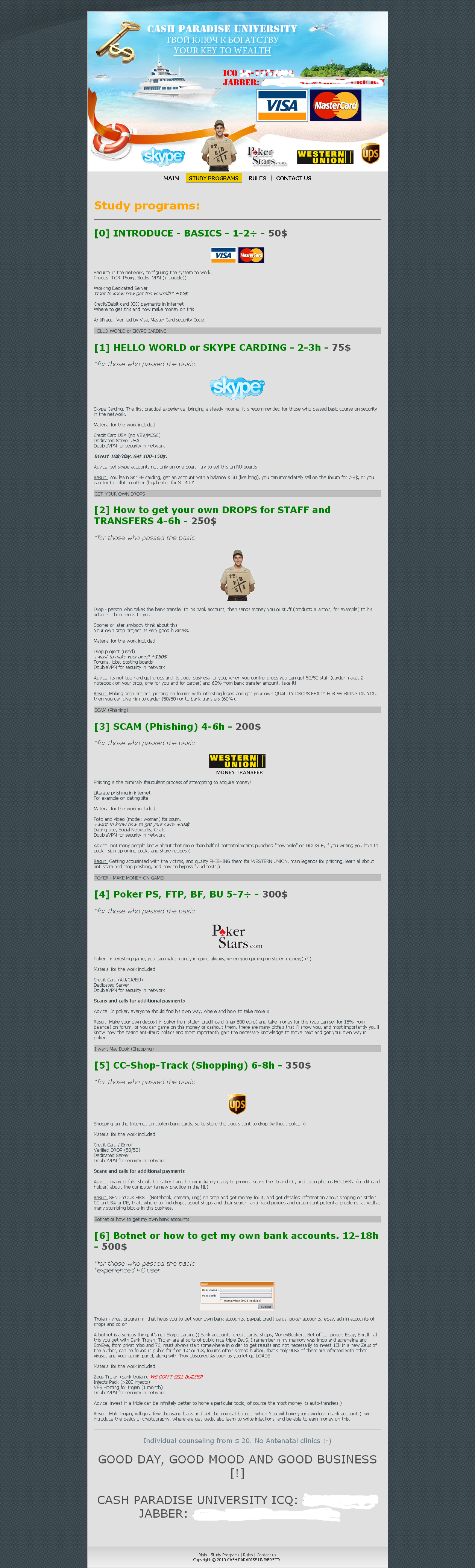
Take the program currently being marketed on several fraud forums — it’s called Cash Paradise University (see screen shot below). For $50, a newbie scammer can learn the basics of online fraud, such as hiding one’s identity and location online, and how to obtain reliable stolen credit card numbers. For a $75 fee and an investment of about 2 to 3 hours, one can become fluent in the ways of “Skype carding,” or selling hacked and newly-created Skype accounts that have been loaded with funds from stolen credit cards.
The prices go up as the fledgling fraudster progresses from the Scam 101 courses to the more crafty classes, which naturally depend on the earlier courses as prerequisites (“for those who passed the basic,” admonishes the Scam U. professor). Learning the basics of “carding” merchandise — such as intercepting the shipments and selling the loot online — requires an investment of four to six hours and at least $250, with course materials adding as much as $150 to the cost of the class.
Tackling the tenets of cashing out stolen credit card numbers using Internet gambling sites could take up to seven hours of study time and require a $300 admittance fee. The master class — learning how to bootstrap and build out a botnet of computers infected with the ZeuS Trojan — can take upwards of 18 hours of classroom instruction, and cost at least $500 (although a copy of ZeuS bot builder is not included in the price of tuition!).
According to this fraud instructor’s profile on a top scammer forum, more than a dozen novice hackers have already paid for and progressed through the course work, and most appear to be giving their teacher high marks.
“Please note: due to change in the place of stay, I’ll be offline on 12-13 September,” the headmaster of CPU says to potential new students. “Classes take place from September 14, do not waste! Good luck in business.” For those ADHD students who need more individual attention, there is private tutoring available starting at $20 extra per class.
But don’t count paying for the classes with a (stolen?) credit card: This institution only accepts irreversible forms of payment, such as Western Union or virtual currencies like WebMoney and Liberty Reserve.
[EPSB]
Have you seen:
I’ll Take Two MasterCards and a Visa, Please…When you’re shopping for stolen credit and debit cards online, there are so many choices these days. A glut of stolen data — combined with innovation and cutthroat competition among vendors — is conspiring to keep prices for stolen account numbers exceptionally low. Even so, many readers probably have no idea that their credit card information is worth only about $1.50 on the black market.
[/EPSB]
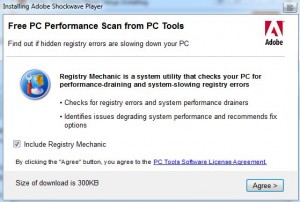 The Shockwave patch plugs 11 security holes in program, most of which attackers could use remotely to take control over an affected system. Updates are available for Mac and Windows computers, from this link. The latest version is 11.5.9.615. Before you blithely click through the process, keep a lookout for pre-checked “free” software that will install alongside this Shockwave update if you simply accept all the default options. When I tested the Shockwave installer, it included a “free PC performance scan from PC Tools’s Registry Mechanic. I opted to untick the check mark next to that option before proceeding with the rest of the install, which was otherwise uneventful.
The Shockwave patch plugs 11 security holes in program, most of which attackers could use remotely to take control over an affected system. Updates are available for Mac and Windows computers, from this link. The latest version is 11.5.9.615. Before you blithely click through the process, keep a lookout for pre-checked “free” software that will install alongside this Shockwave update if you simply accept all the default options. When I tested the Shockwave installer, it included a “free PC performance scan from PC Tools’s Registry Mechanic. I opted to untick the check mark next to that option before proceeding with the rest of the install, which was otherwise uneventful.