Criminals have developed a component of the ZeuS Trojan designed to run on Google Android phones. The new strain of malware comes as security experts are warning about the threat from mobile malware that may use tainted ads and drive-by downloads.
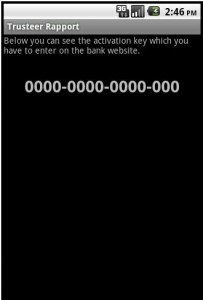
Researchers at Fortinet said the malicious file is a new version of “Zitmo,” a family of mobile malware first spotted last year that stands for “ZeuS in the mobile.” The Zitmo variant, disguised as a security application, is designed to intercept the one-time passcodes that banks send to mobile users as an added security feature. It masquerades as a component of Rapport, a banking activation application from Trusteer. Once installed, the malware lies in wait for incoming text messages, and forwards them to a remote Web server.
Trusteer published a lengthy blog post today that mentions an attack by this threat “that was used in conjunction with Zeus 2.1.0.10. The user was first infected with Zeus on their PC and then Zeus showed the message requesting the user to download the Android malware component.” In a phone interview, Trusteer CEO Mickey Boodaei said crooks used the Trojan in live attacks against several online banking users during the first week of June, but that the infrastructure that supported the attacks was taken offline about a month ago.
Boodaei offers a bold and grim forecast for the development of mobile malware, predicting that within 12 to 24 months more than 1 in 20 (5.6%) of Android phones and iPads/iPhones could become infected by mobile malware if fraudsters start integrating zero-day mobile vulnerabilities into leading exploit kits.
The last bit about exploit kits is key, because almost all mobile malware developed so far uses some type of social engineering to install itself on a device. Boodaei predicts a future time when crooks begin incorporating mobile phone vulnerabilities into automated exploit kits like BlackHole and Eleonore, which use security flaws to install malicious software when the user visits a booby-trapped site with a vulnerable device.