A picture may be worth a thousand words, but a single tainted digital image may be worth thousands of dollars for computer crooks who are using weaknesses in Google’s Image Search to foist malicious software on unsuspecting surfers.
For several weeks, some readers have complained that clicking on Google Images search results directed them to Web pages that pushed rogue anti-virus scareware via misleading security alerts and warnings. On Wednesday, the SANS Internet Storm Center posted a blog entry saying they, too, were receiving reports of Google Image searches leading to fake anti-virus sites. According to SANS, the attackers have compromised an unknown number of sites with malicious scripts that create Web pages filled with the top search terms from Google Trends. The malicious scripts also fetch images from third-party sites and include them in the junk pages alongside the relevant search terms, so that the automatically generated Web page contains legitimate-looking content.
Google’s Image Search bots eventually will index this bogus content. If users are searching for words or phrases that rank high in the current top search terms, it is likely that thumbnails from these malicious pages will be displayed beside other legitimate results.
As SANS handler Bojan Zdrnja explains, the exploit happens when a user clicks on one of these tainted thumbnails. “This is where the ‘vulnerability’ is,” Zdrnja wrote. “The user’s browser will automatically send a request to the bad page which runs the attacker’s script. This script checks the request’s referrer field and if it contains Google (meaning this was a click on the results page in Google), the script displays a small JavaScript script…[that] causes the browser to be redirected to another site that is serving FakeAV. Google is doing a relatively good job removing (or at least marking) links leading to malware in normal searches, however, Google’s image search seem to be plagued with malicious links.”
Denis Sinegubko, a Russian malware researcher who has been studying the fake anti-virus campaigns, called this tactic “the most efficient black hat trick ever,” and said it is exceedingly easy to set up. He said he’s received access logs from the owners of several hacked sites, and has used the data to estimate the traffic Google sends to these bogus image search pages. Sinegubko reckons that there are more than 5,000 hacked sites, and that the average site has been injected with about 1,000 of these bogus pages. The average page receives a visitor from Google approximately every 10 days, he said, which means Google is referring about a half million visits to fake anti-virus sites every day, or about 15 million visits each month.
For example, one of the hacked sites Sinegubko said he saw access logs for was in Croatia; It had a Google page rank of zero prior to being compromised with the phony image search scripts. The logs showed that the site had been hacked on Mar. 18, 2011, and that Google began indexing the tainted image pages the next day. “During the next 5 weeks it has indexed 27,200+ doorway pages on this site,” he wrote in a blog post on his findings. “During the same 5 weeks Google Image search has sent 140,000+ visitors to this small site.”
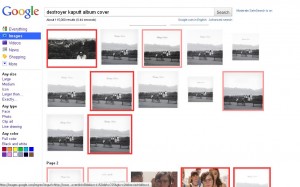
Sinegubko is developing an add-on for Firefox that can flag malicious Google Image search results by placing a red box around images that appear to link to hostile sites; Images with a pale pink box around them are hot-linked and may also be malicious, Sinegubko said. I tested the add-on (which is not ready for public release) searching for the cover art for the album “Kaputt” by the Canadian band Destroyer. As you can see from the image above, most of the images returned link to sites pushing fake anti-virus.