“Our dependence on all things cyber as a society is now inestimably irreversible and irreversibly inestimable.”
Yeah, I had to re-read that line a few times, too. Which is probably why I’ve put off posting a note here about the article from which the above quote was taken, a thought-provoking essay in the Harvard National Security Journal by Dan Geer, chief information security philosopher officer for In-Q-Tel, the not-for-profit venture capital arm of the Central Intelligence Agency.
The essay is well worth reading for anyone remotely interested in hard-to-solve security problems. Geer is better than most at tossing conversational hand grenades and then walking away, and this piece doesn’t disappoint. For example:
“Looking forward, without universal strong authentication, tomorrow’s cybercriminal will not need the fuss and bother of maintaining a botnet when, with a few hundred stolen credit cards, he will be able to buy all the virtual machines he needs from cloud computing operators. In short, my third conclusion is that if the tariff of security is paid, it will be paid in the coin of privacy.”
Geer’s prose can be long-winded and occasionally sesquipedalian (such as the phrase “Accretive sequestration of social policy”), but then he turns around and shows off his selective economy with words by crafting statements like:
“..demand for security expertise so outstrips supply that the charlatan fraction is rising.”
In the essay, Geer touches on a pet issue of mine: Accountability for insecurity. I recently wrote an editorial for CSO Online addressing a public request for advice by the Federal Communications Commission (FCC), which wants ideas on how to craft a “Cybersecurity Roadmap” as part of its $7 billion national broadband initiative.
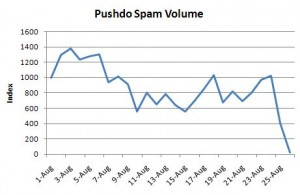
In that column, I suggest that the FCC find a way to measure and publish data about the number and longevity of specific cyber security threats resident on domestic ISPs and hosting providers. I also suggest that the government could achieve this goal largely by collecting and analyzing data from the many mainly volunteer-led efforts that are already measuring this stuff.
Geer warns readers that “the demand for ‘safe pipes’ inexorably leads to deputizing those who own the most pipes.” But mine isn’t a “punish or regulate ISPs-for-having-lots-of-security-problems” approach. Instead, it’s more of a “publish a reputation score with the imprimatur of the federal government in the hopes that the ISPs will be shamed into more proactively addressing abuse issues” idea.
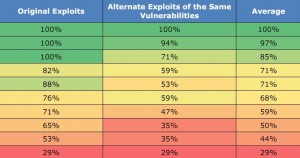
Who knows if my idea would work, but it wouldn’t be terribly risky or expensive to try. After all, as Geer said, “security is a means and that game play cannot improve without a scorekeeping mechanism.”
“These are heady problems,” he concludes. “They go to the heart of sovereignty. They go to the heart of culture. They go to the heart of ‘Land of the Free and Home of the Brave’. They will not be solved centrally, yet neither will they be solved without central assistance. We have before us a set of bargains, bargains between the Devil and the Deep Blue Sea. And not to decide is to decide.”
Cue the music.