In very few of the many stories I’ve written about online banking fraud against businesses has insurance paid for much — if any — of the losses victim companies suffered. However, several victims I’ve interviewed in recent incidents did have cybersecurity insurance coverage bundled as part of larger business risk insurance policies. In each case, the businesses suffered fairly substantial thefts, and appear likely to recoup all of their direct financial losses.
 The most recent incident involved Golden State Bridge Inc., a Martinez, Calif. engineering and construction company that builds bridges. The thieves used an extremely stealthy but as-yet-unclassified strain of malicious software to steal the company’s online banking credentials, and on May 19th, the crooks used that access to set up a series of fraudulent payroll payments totaling more than $125,000.
The most recent incident involved Golden State Bridge Inc., a Martinez, Calif. engineering and construction company that builds bridges. The thieves used an extremely stealthy but as-yet-unclassified strain of malicious software to steal the company’s online banking credentials, and on May 19th, the crooks used that access to set up a series of fraudulent payroll payments totaling more than $125,000.
Initially, the attackers set up two batches of automated clearing house (ACH) payments –one for $50,000 and another for $75,000 – effectively sending a series of transfers to a dozen different money mules, willing or unwitting individuals lured into helping the criminals launder stolen funds by wiring the funds overseas and taking a small commission (usually 8 percent) for themselves.
When the first two batches were processed by Golden State’s bank on May 20, the thieves apparently figured they were home free, and set in motion another seven bundles of fraudulent payments for several hundred thousand dollars more, according to Ann Talbot, the company’s chief financial officer.
“Once they executed those first two successfully, they must have been like, ‘Oh, we’ve hit the mother lode! Let’s go for it!’,” Talbot recalled. “Had they succeeded in putting those through, we and the bank would have been looking at losses of more than $750,000.”
But Talbot noticed the fraudulent transfers the day the money started moving out of Golden State’s accounts, and sprang into action to get the seven new batches canceled. Unfortunately, by that point most of the mules who were sent loot in the first two batches had already withdrawn their transfers.
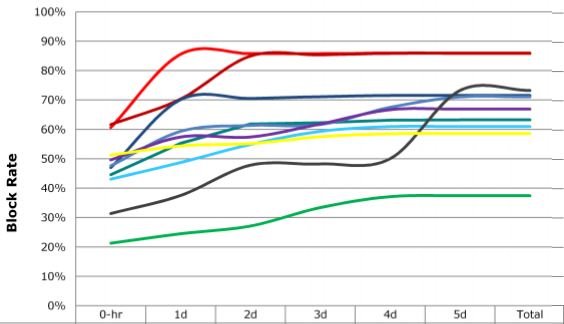
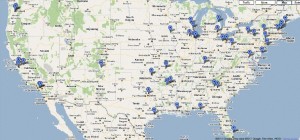 Talbot said nearly all of the money mules were located on the East Coast, which she believes is a tactic designed to give the attackers the longest head start possible before West Coast victims notice the fraudulent transfers.
Talbot said nearly all of the money mules were located on the East Coast, which she believes is a tactic designed to give the attackers the longest head start possible before West Coast victims notice the fraudulent transfers.
“These mules were with East Coast banks, and most of them had [withdrawn] the money from their banks before we were even open for business,” Talbot said.
For what it’s worth, I observed this same pattern of the thieves relying mainly East Coast mules in an earlier post, Charting the Carnage from eBanking Fraud.
SECRET QUESTION CHECKUPS
Like many financial institutions serving primarily business customers, the California Bank of Commerce — Golden State’s bank — pushes most of the security and authentication for its online banking systems out to customers, requiring a simple username and password, and occasionally prompting customers to provide the correct answer to one or more of their “secret questions”.
Read more after the jump….
Continue reading →
![]() Adobe Systems Inc. is urging users to update installations of Adobe Reader and Acrobat to fix a critical flaw that attackers have been exploiting to break into vulnerable systems.
Adobe Systems Inc. is urging users to update installations of Adobe Reader and Acrobat to fix a critical flaw that attackers have been exploiting to break into vulnerable systems.