Luis Corrons spent much of the last year helping Spanish police with an investigation that led to the arrest of three local men suspected of operating and renting access to a massive and global network of hacked computers. Then, roughly 60 days after their arrest, something strange happened: Two of them unexpectedly turned up at Corrons’ office and asked to be hired as security researchers.
Luis Corrons spent much of the last year helping Spanish police with an investigation that led to the arrest of three local men suspected of operating and renting access to a massive and global network of hacked computers. Then, roughly 60 days after their arrest, something strange happened: Two of them unexpectedly turned up at Corrons’ office and asked to be hired as security researchers.
Corrons, a technical director and blogger for Spanish security firm Panda Security, said he received a visit from the hackers on the morning of March 22. The two men, known by the online nicknames “Netkairo” and “Ostiator,” were arrested in February by Spanish police for their alleged role in running the “Mariposa” botnet, a malware distribution platform that spread malicious software to more than 12 million Internet addresses from 190 countries (mariposa is Spanish for “butterfly”).
Now, here the two Mariposa curators were at Panda’s headquarters in Bilbao, their resumes in hand, practically begging for a job, Corrons said.
“At first, I couldn’t believe it, and I thought someone in the office was playing a practical joke on me,” Corrons said. “But these guys were the real guys, and they were serious.
“Ostiator told me, ‘The thing is, with everything that’s been happening, we’re not earning any money at the moment,” Corrons recalled. “He said, ‘We thought we could look for some kind of agreement in which both sides would benefit. We think we have knowledge [that] could be useful to Panda and thought we could have some kind of agreement with Panda.'”
Spanish police do not typically release the names of individuals who have been arrested, and Netkairo and Ostiator haven’t yet been charged with any crime. But Corrons recognized that the names and addresses on the resumes matched those that police had identified as residences belonging to Netkairo and Ostiator.
Corrons said Panda’s lawyers were unwilling to release the full names of the two men that visited Panda Labs, but said Ostiator’s first name is Juan Jose, and that he is a 25-year-old male from Santiago de Compostela. Corrons said Netkairo is a 31-year-old from Balmaseda named Florencio.
Shortly after the arrests were announced, local Spanish media said the third individual arrested by Spanish authorities in connection with Mariposa — a 30-year-old identified by his initials “JPR” — used the hacker nickname “Johny Loleante” and lived in Molina de Segura, Murcia.
On Mar. 3, I had the opportunity to interview Captain Cesar Lorenzana, deputy head technology crime division of the Spanish Civil Guard. Lorenzana told Krebsonsecurity.com that Netkairo and his associate were earning about 3,000 Euros each month renting out the Mariposa botnet to other hackers.
Interviewing the same hackers less than three weeks later, Corrons asked them how they got started creating Mariposa.
“Basically, they said they started it as kind of a hobby, and that they weren’t working at the time,” Corrons said. “Suddenly, they started to earn money, a few hundred Euros a week to start, and then discovered they couldn’t stop. And the whole time, their network kept growing.”
Continue reading →
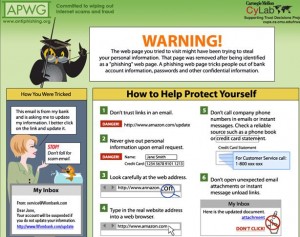 For the past 20 months, Jason Hong, assistant professor of computer science at Carnegie Mellon University‘s Human Computer Interaction Institute, has been measuring referrals from phishing sites to an education page set up by the Anti-Phishing Working Group (APWG), an industry consortium. Hong said the site now receives close to 25,000 referrals per month from phishing sites that brand owners have modified.
For the past 20 months, Jason Hong, assistant professor of computer science at Carnegie Mellon University‘s Human Computer Interaction Institute, has been measuring referrals from phishing sites to an education page set up by the Anti-Phishing Working Group (APWG), an industry consortium. Hong said the site now receives close to 25,000 referrals per month from phishing sites that brand owners have modified.