For the second time in as many weeks, Internet hosting provider Network Solutions is trying to limit the damage from a hacking incident that has left many customer Web sites serving up malicious code.
In a post to its blog on Sunday titled We Feel Your Pain and We are Working Hard to Fix This, Network Solutions spokesman Shashi Bellamkonda apologized for the incident.
“We have received reports that Network Solutions customers are seeing malicious code added to their websites and we are really sorry for this experience,” Bellamkonda wrote. “At this time since anything we say in public may help the perpetrators, we are unable to provide details.”
Reached by telephone Monday, company spokeswoman Susan Wade declined to offer much more detail about the incident, such as how many customers may have been impacted and whether Network Solutions had uncovered the cause.
“It’s not impacting the entire hosting platform, but a subset of customers,” Wade said. “We’re trying to be very careful of what we say publicly right now. We want to make sure we have our facts straight and that we understand the scope of the problem. We’re putting countermeasures in place, but we’re not quite ready to come out and talk about them just yet.”
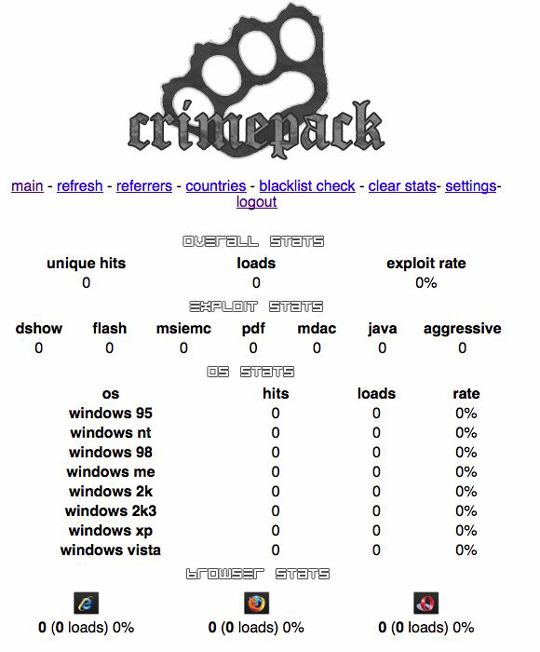
Unlike last week’s bout of customer site compromises, which seemed to impact mainly WordPress blogs, security experts have been hard-pressed to find a commonality among the victim sites, other than the malicious sites they are linking to.
“Note that this time we are seeing all kind of sites hacked, from WordPress, Joomla to just simple HTML sites,” wrote David Dede, a Brazilian security blogger who helped to raise the alarm over last week’s Network Solutions infections.
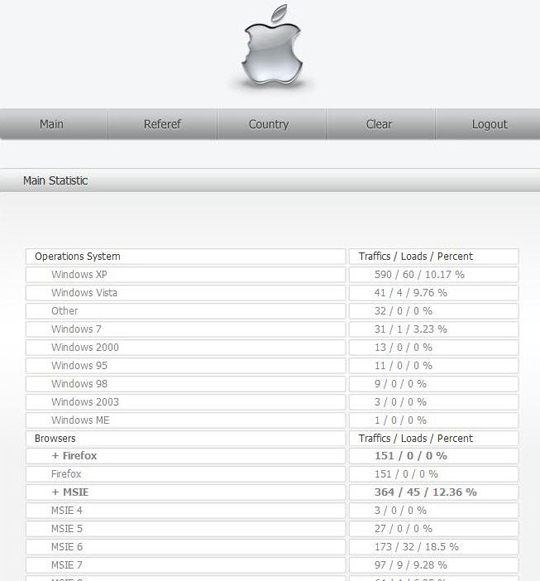
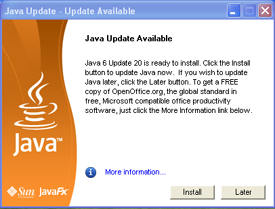
The StopMalvertising blog includes a host of information about the malicious scripts inserted into the hacked sites, indicating that the injected code redirects the visitor’s browser to Web pages that silently try to install malicious software using a variety of known vulnerabilities in popular Web browser plugins — such as Adobe PDF Reader — as well as insecure ActiveX (Internet Explorer) components.
 Readers may notice over the next day or so advertisements in one or two prominent spots on this blog. This is the result of a new partnership between Krebs on Security and Federated Media Publishing, a company that connects independent Web site authors with advertisers.
Readers may notice over the next day or so advertisements in one or two prominent spots on this blog. This is the result of a new partnership between Krebs on Security and Federated Media Publishing, a company that connects independent Web site authors with advertisers.