Authorities in the United States, Germany, the Netherlands and the U.K. last week said they dismantled the “RSOCKS” botnet, a collection of millions of hacked devices that were sold as “proxies” to cybercriminals looking for ways to route their malicious traffic through someone else’s computer. While the coordinated action did not name the Russian hackers allegedly behind RSOCKS, KrebsOnSecurity has identified its owner as a 35-year-old Russian man living abroad who also runs the world’s top spam forum.
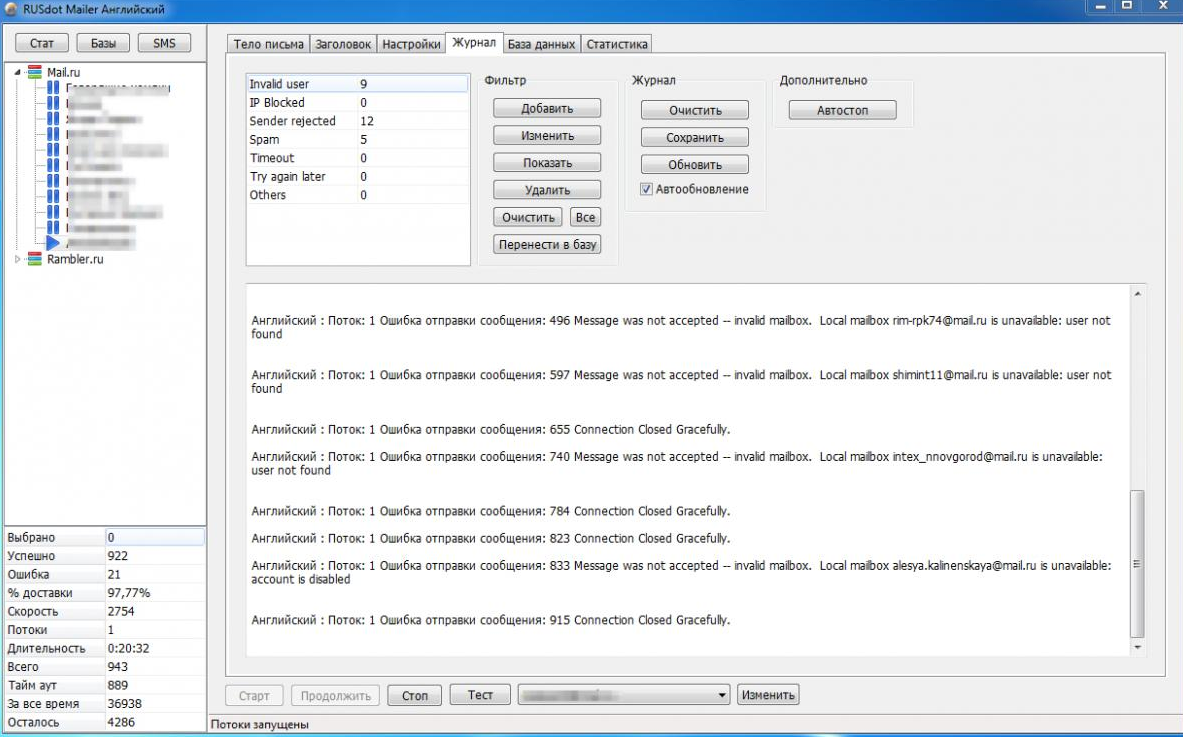
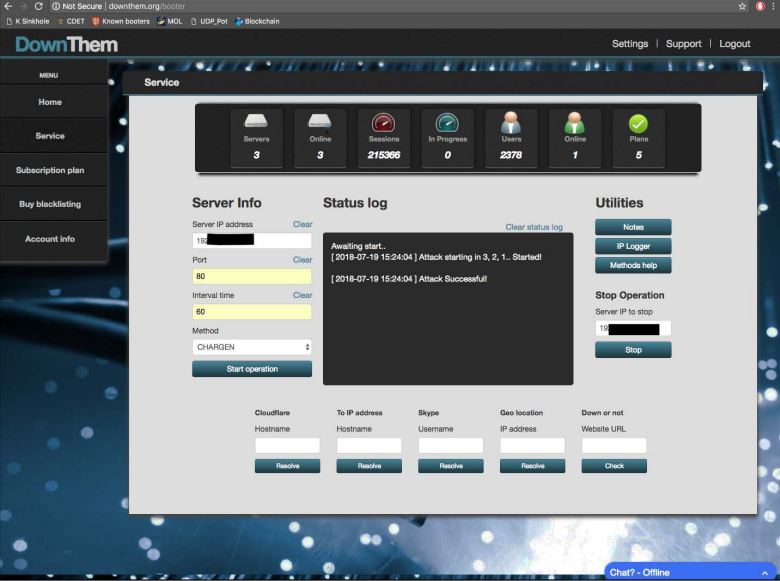
The RUSdot mailer, the email spamming tool made and sold by the administrator of RSOCKS.
According to a statement by the U.S. Department of Justice, RSOCKS offered clients access to IP addresses assigned to devices that had been hacked:
“A cybercriminal who wanted to utilize the RSOCKS platform could use a web browser to navigate to a web-based ‘storefront’ (i.e., a public web site that allows users to purchase access to the botnet), which allowed the customer to pay to rent access to a pool of proxies for a specified daily, weekly, or monthly time period. The cost for access to a pool of RSOCKS proxies ranged from $30 per day for access to 2,000 proxies to $200 per day for access to 90,000 proxies.”
The DOJ’s statement doesn’t mention that RSOCKS has been in operation since 2014, when access to the web store for the botnet was first advertised on multiple Russian-language cybercrime forums.
The user “RSOCKS” on the Russian crime forum Verified changed his name to RSOCKS from a previous handle: “Stanx,” whose very first sales thread on Verified in 2016 quickly ran afoul of the forum’s rules and prompted a public chastisement by the forum’s administrator.
Verified was hacked twice in the past few years, and each time the private messages of all users on the forum were leaked. Those messages show that after being warned of his forum infraction, Stanx sent a private message to the Verified administrator detailing his cybercriminal bona fides.
“I am the owner of the RUSdot forum (former Spamdot),” Stanx wrote in Sept. 2016. “In spam topics, people know me as a reliable person.”
A Google-translated version of the Rusdot spam forum.
RUSdot is the successor forum to Spamdot, a far more secretive and restricted forum where most of the world’s top spammers, virus writers and cybercriminals collaborated for years before the community’s implosion in 2010. Even today, the RUSdot Mailer is advertised for sale at the top of the RUSdot community forum.
Stanx said he was a longtime member of several major forums, including the Russian hacker forum Antichat (since 2005), and the Russian crime forum Exploit (since April 2013). In an early post to Antichat in January 2005, Stanx disclosed that he is from Omsk, a large city in the Siberian region of Russia.
According to the cyber intelligence firm Intel 471, the user Stanx indeed registered on Exploit in 2013, using the email address stanx@rusdot.com, and the ICQ number 399611. A search in Google for that ICQ number turns up a cached version of a Vkontakte profile for a Denis “Neo” Kloster, from Omsk, Russia. Continue reading