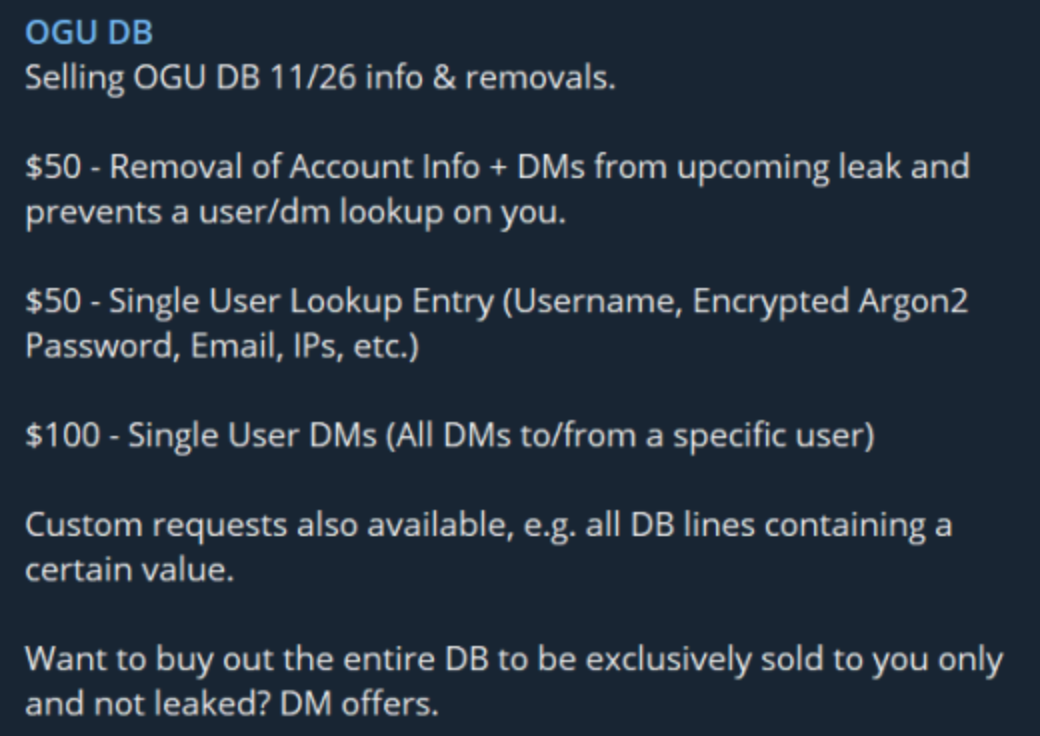
Fraudsters redirected email and web traffic destined for several cryptocurrency trading platforms over the past week. The attacks were facilitated by scams targeting employees at GoDaddy, the world’s largest domain name registrar, KrebsOnSecurity has learned.

The incident is the latest incursion at GoDaddy that relied on tricking employees into transferring ownership and/or control over targeted domains to fraudsters. In March, a voice phishing scam targeting GoDaddy support employees allowed attackers to assume control over at least a half-dozen domain names, including transaction brokering site escrow.com.
And in May of this year, GoDaddy disclosed that 28,000 of its customers’ web hosting accounts were compromised following a security incident in Oct. 2019 that wasn’t discovered until April 2020.
This latest campaign appears to have begun on or around Nov. 13, with an attack on cryptocurrency trading platform liquid.com.
“A domain hosting provider ‘GoDaddy’ that manages one of our core domain names incorrectly transferred control of the account and domain to a malicious actor,” Liquid CEO Mike Kayamori said in a blog post. “This gave the actor the ability to change DNS records and in turn, take control of a number of internal email accounts. In due course, the malicious actor was able to partially compromise our infrastructure, and gain access to document storage.”
In the early morning hours of Nov. 18 Central European Time (CET), cyptocurrency mining service NiceHash disccovered that some of the settings for its domain registration records at GoDaddy were changed without authorization, briefly redirecting email and web traffic for the site. NiceHash froze all customer funds for roughly 24 hours until it was able to verify that its domain settings had been changed back to their original settings.
“At this moment in time, it looks like no emails, passwords, or any personal data were accessed, but we do suggest resetting your password and activate 2FA security,” the company wrote in a blog post.
NiceHash founder Matjaz Skorjanc said the unauthorized changes were made from an Internet address at GoDaddy, and that the attackers tried to use their access to its incoming NiceHash emails to perform password resets on various third-party services, including Slack and Github. But he said GoDaddy was impossible to reach at the time because it was undergoing a widespread system outage in which phone and email systems were unresponsive.
“We detected this almost immediately [and] started to mitigate [the] attack,” Skorjanc said in an email to this author. “Luckily, we fought them off well and they did not gain access to any important service. Nothing was stolen.”
Skorjanc said NiceHash’s email service was redirected to privateemail.com, an email platform run by Namecheap Inc., another large domain name registrar. Using Farsight Security, a service which maps changes to domain name records over time, KrebsOnSecurity instructed the service to show all domains registered at GoDaddy that had alterations to their email records in the past week which pointed them to privateemail.com. Those results were then indexed against the top one million most popular websites according to Alexa.com.
The result shows that several other cryptocurrency platforms also may have been targeted by the same group, including Bibox.com, Celsius.network, and Wirex.app. None of these companies responded to requests for comment.
In response to questions from KrebsOnSecurity, GoDaddy acknowledged that “a small number” of customer domain names had been modified after a “limited” number of GoDaddy employees fell for a social engineering scam. GoDaddy said the outage between 7:00 p.m. and 11:00 p.m. PST on Nov. 17 was not related to a security incident, but rather a technical issue that materialized during planned network maintenance.
“Separately, and unrelated to the outage, a routine audit of account activity identified potential unauthorized changes to a small number of customer domains and/or account information,” GoDaddy spokesperson Dan Race said. “Our security team investigated and confirmed threat actor activity, including social engineering of a limited number of GoDaddy employees.”
“We immediately locked down the accounts involved in this incident, reverted any changes that took place to accounts, and assisted affected customers with regaining access to their accounts,” GoDaddy’s statement continued. “As threat actors become increasingly sophisticated and aggressive in their attacks, we are constantly educating employees about new tactics that might be used against them and adopting new security measures to prevent future attacks.”
Race declined to specify how its employees were tricked into making the unauthorized changes, saying the matter was still under investigation. But in the attacks earlier this year that affected escrow.com and several other GoDaddy customer domains, the assailants targeted employees over the phone, and were able to read internal notes that GoDaddy employees had left on customer accounts.
What’s more, the attack on escrow.com redirected the site to an Internet address in Malaysia that hosted fewer than a dozen other domains, including the phishing website servicenow-godaddy.com. This suggests the attackers behind the March incident — and possibly this latest one — succeeded by calling GoDaddy employees and convincing them to use their employee credentials at a fraudulent GoDaddy login page. Continue reading →