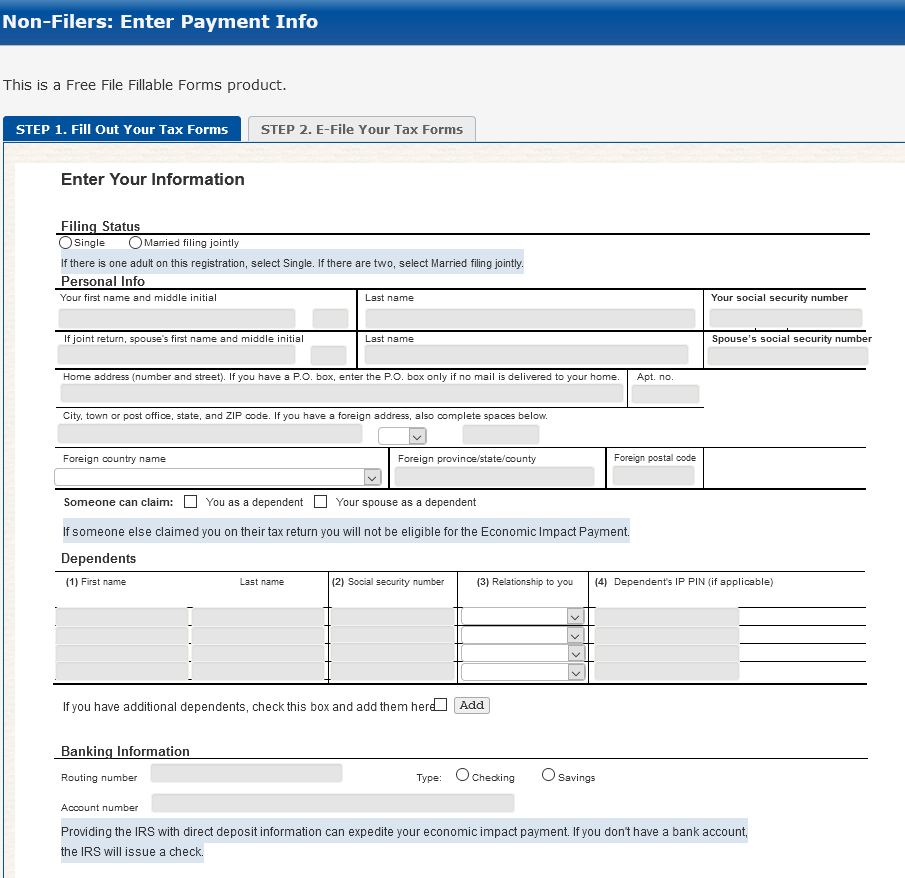
The past few weeks have seen a large number of new domain registrations beginning with the word “reopen” and ending with U.S. city or state names. The largest number of them were created just hours after President Trump sent a series of all-caps tweets urging citizens to “liberate” themselves from new gun control measures and state leaders who’ve enacted strict social distancing restrictions in the face of the COVID-19 pandemic. Here’s a closer look at who and what appear to be behind these domains.
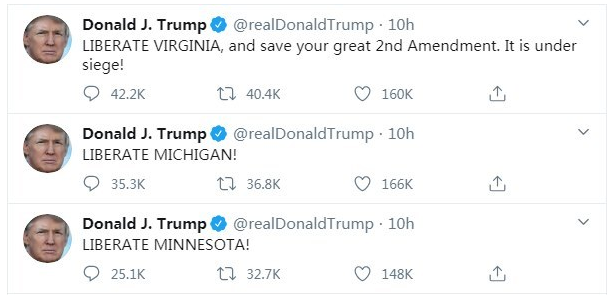
A series of inciteful tweets sent by President Trump on April 17, the same day dozens of state-themed “reopen” domains were registered — mostly by conservative groups and gun rights advocates.
KrebsOnSecurity began this research after reading a fascinating Reddit thread over the weekend on several “reopen” sites that seemed to be engaged in astroturfing, which involves masking the sponsors of a message or organization to make it appear as though it originates from and is supported by grassroots participants.
The Reddit discussion focused on a handful of new domains — including reopenmn.com, reopenpa.com, and reopenva.com — that appeared to be tied to various gun rights groups in those states. Their registrations have roughly coincided with contemporaneous demonstrations in Minnesota, California and Tennessee where people showed up to protest quarantine restrictions over the past few days.

A “reopen California” protest over the weekend in Huntington Beach, Calif. Image: Reddit.
Suspecting that these were but a subset of a larger corpus of similar domains registered for every state in the union, KrebsOnSecurity ran a domain search report at DomainTools [an advertiser on this site], requesting any and all domains registered in the past month that begin with “reopen” and end in “.com.”
That lookup returned approximately 150 domains; in addition to those named after the individual 50 states, some of the domains refer to large American cities or counties, and others to more general concepts, such as “reopeningchurch.com” or “reopenamericanbusiness.com.”
Many of the domains are still dormant, leading to parked pages and registration records obscured behind privacy protection services. But a review of other details about these domains suggests a majority of them are tied to various gun rights groups, state Republican Party organizations, and conservative think tanks, religious and advocacy groups.
For example, reopenmn.com forwards to minnesotagunrights.org, but the site’s WHOIS registration records (obscured since the Reddit thread went viral) point to an individual living in Florida. That same Florida resident registered reopenpa.com, a site that forwards to the Pennsylvania Firearms Association, and urges the state’s residents to contact their governor about easing the COVID-19 restrictions.
Reopenpa.com is tied to a Facebook page called Pennsylvanians Against Excessive Quarantine, which sought to organize an “Operation Gridlock” protest at noon today in Pennsylvania among its 68,000 members.
Both the Minnesota and Pennsylvania gun advocacy sites include the same Google Analytics tracker in their source code: UA-60996284. A cursory Internet search on that code shows it also is present on reopentexasnow.com, reopenwi.com and reopeniowa.com.
More importantly, the same code shows up on a number of other anti-gun control sites registered by the Dorr Brothers, real-life brothers who have created nonprofits (in name only) across dozens of states that are so extreme in their stance they make the National Rifle Association look like a liberal group by comparison.
This 2019 article at cleveland.com quotes several 2nd Amendment advocates saying the Dorr brothers simply seek “to stir the pot and make as much animosity as they can, and then raise money off that animosity.” The site dorrbrotherscams.com also is instructive here.
A number of other sites — such as reopennc.com — seem to exist merely to sell t-shirts, decals and yard signs with such slogans as “Know Your Rights,” “Live Free or Die,” and “Facts not Fear.” WHOIS records show the same Florida resident who registered this North Carolina site also registered one for New York — reopenny.com — just a few minutes later.
Merchandise available from reopennc.com.
Some of the concept reopen domains — including reopenoureconomy.com (registered Apr. 15) and reopensociety.com (Apr. 16) — trace back to FreedomWorks, a conservative group that the Associated Press says has been holding weekly virtual town halls with members of Congress, “igniting an activist base of thousands of supporters across the nation to back up the effort.”
Reopenoc.com — which advocates for lifting social restrictions in Orange County, Calif. — links to a Facebook page for Orange County Republicans, and has been chronicling the street protests there. The messaging on Reopensc.com — urging visitors to digitally sign a reopen petition to the state governor — is identical to the message on the Facebook page of the Horry County, SC Conservative Republicans.
Reopenmississippi.com was registered on April 16 to In Pursuit of LLC, an Arlington, Va.-based conservative group with a number of former employees who currently work at the White House or in cabinet agencies. A 2016 story from USA Today says In Pursuit Of LLC is a for-profit communications agency launched by billionaire industrialist Charles Koch. Continue reading




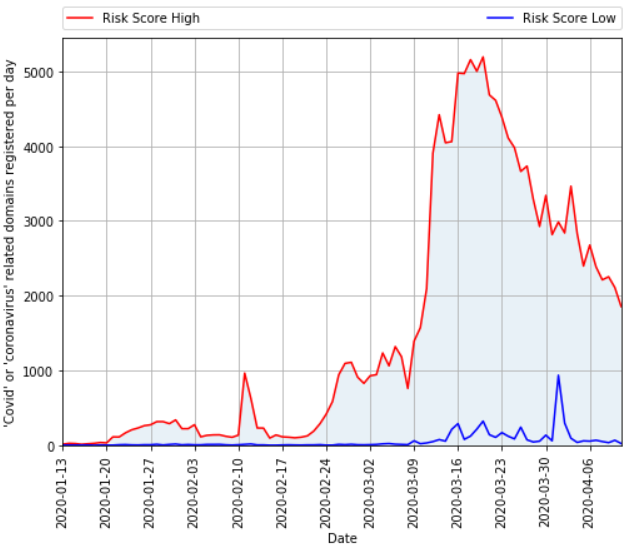
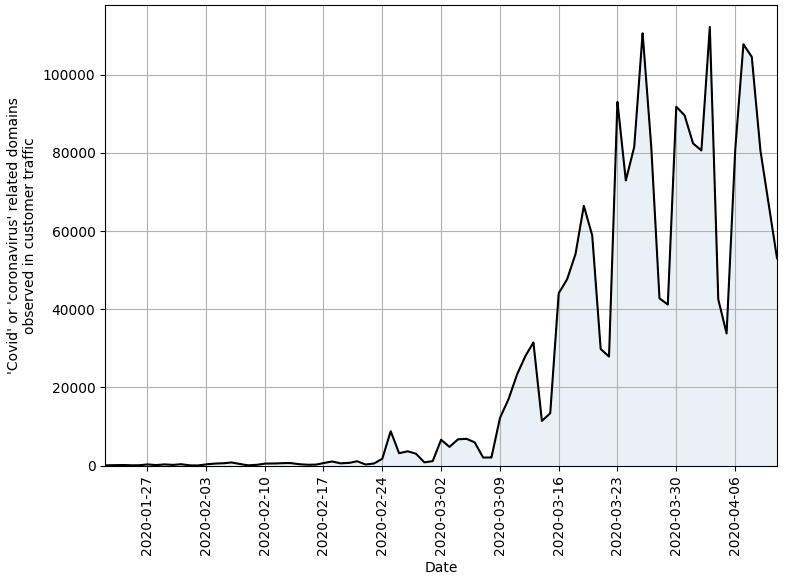
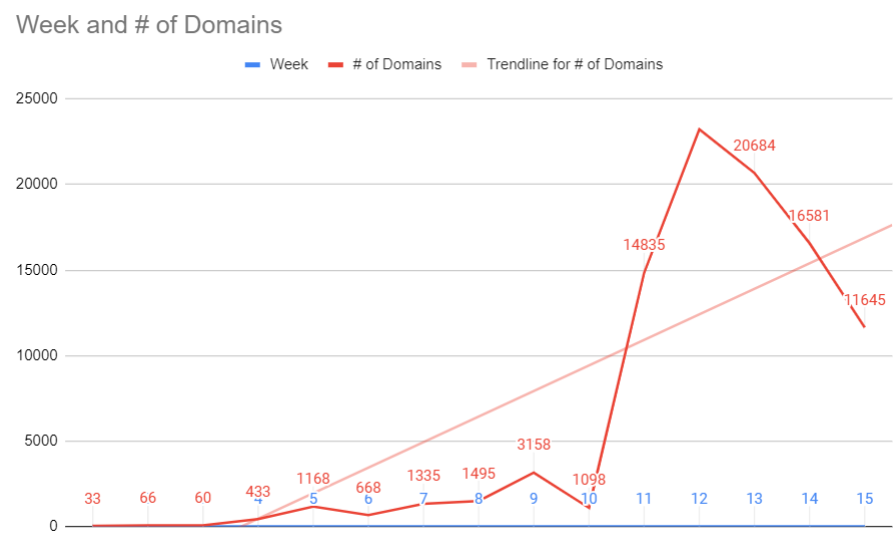
 At least three major industry groups are working to counter the latest cyber threats and scams. Among the largest in terms of contributors is the
At least three major industry groups are working to counter the latest cyber threats and scams. Among the largest in terms of contributors is the  Nineteen of the weaknesses fixed on this Patch Tuesday were assigned Microsoft’s most-dire “critical” rating, meaning malware or miscreants could exploit them to gain complete, remote control over vulnerable computers without any help from users.
Nineteen of the weaknesses fixed on this Patch Tuesday were assigned Microsoft’s most-dire “critical” rating, meaning malware or miscreants could exploit them to gain complete, remote control over vulnerable computers without any help from users.