An entrepreneur and virtual currency investor is suing AT&T for $224 million, claiming the wireless provider was negligent when it failed to prevent thieves from hijacking his mobile account and stealing millions of dollars in cryptocurrencies. Increasingly frequent, high-profile attacks like these are prompting some experts to say the surest way to safeguard one’s online accounts may be to disconnect them from the mobile providers entirely.

The claims come in a lawsuit filed this week in Los Angeles on behalf of Michael Terpin, who co-founded the first angel investor group for bitcoin enthusiasts in 2013. Terpin alleges that crooks stole almost $24 million worth of cryptocurrency after fraudulently executing a “SIM swap” on his mobile phone account at AT&T in early 2018.
A SIM card is the tiny, removable chip in a mobile device that allows it to connect to the provider’s network. Customers can legitimately request a SIM swap when their existing SIM card has been damaged, or when they are switching to a different phone that requires a SIM card of another size.
But SIM swaps are frequently abused by scam artists who trick mobile providers into tying a target’s service to a new SIM card and mobile phone that the attackers control. Unauthorized SIM swaps often are perpetrated by fraudsters who have already stolen or phished a target’s password, as many banks and online services rely on text messages to send users a one-time code that needs to be entered in addition to a password for online authentication.
Terpin alleges that on January 7, 2018, someone requested an unauthorized SIM swap on his AT&T account, causing his phone to go dead and sending all incoming texts and phone calls to a device the attackers controlled. Armed with that access, the intruders were able to reset credentials tied to his cryptocurrency accounts and siphon nearly $24 million worth of digital currencies.
According to Terpin, this was the second time in six months someone had hacked his AT&T number. On June 11, 2017, Terpin’s phone went dead. He soon learned his AT&T password had been changed remotely after 11 attempts in AT&T stores had failed. At the time, AT&T suggested Terpin take advantage of the company’s “extra security” feature — a customer-specified six-digit PIN which is required before any account changes can be made.
Terpin claims an investigation by AT&T into the 2018 breach found that an employee at an AT&T store in Norwich, Conn. somehow executed the SIM swap on his account without having to enter his “extra security” PIN, and that AT&T knew or should have known that employees could bypass its customer security measures.
Terpin is suing AT&T for his $24 million worth of cryptocurrencies, plus $200 million in punitive damages. A copy of his complaint is here (PDF).
AT&T declined to comment on specific claims in the lawsuit, saying only in a statement that, “We dispute these allegations and look forward to presenting our case in court.”
AN ‘IDENTITY CRISIS’?
Mobile phone companies are a major weak point in authentication because so many companies have now built their entire procedure for authenticating customers on a process that involves sending a one-time code to the customer via SMS or automated phone call.
In some cases, thieves executing SIM swaps have already phished or otherwise stolen a target’s bank or email password. But many major social media platforms — such as Instagram — allow users to reset their passwords using nothing more than text-based (SMS) authentication, meaning thieves can hijack those accounts just by having control over the target’s mobile phone number.
Allison Nixon is director of security research at Flashpoint, a security company in New York City that has been closely tracking the murky underworld of communities that teach people how to hijack phone numbers assigned to customer accounts at all of the major mobile providers.
Nixon calls the current SIM-jacking craze “a major identity crisis” for cybersecurity on multiple levels.
“Phone numbers were never originally intended as an identity document, they were designed as a way to contact people,” Nixon said. “But because of all these other companies are building in security measures, a phone number has become an identity document.”
In essence, mobile phone companies have become “critical infrastructure” for security precisely because so much is riding on who controls a given mobile number. At the same time, so little is needed to undo weak security controls put in place to prevent abuse.
“The infrastructure wasn’t designed to withstand the kind of attacks happening now,” Nixon said. “The protocols need to be changed, and there are probably laws affecting the telecom companies that need to be reviewed in light of how these companies have evolved.”
Unfortunately, with the major mobile providers so closely tied to your security, there is no way you can remove the most vulnerable chunks of this infrastructure — the mobile store employees who can be paid or otherwise bamboozled into helping these attacks succeed.
No way, that is, unless you completely disconnect your mobile phone number from any sort of SMS-based authentication you currently use, and replace it with Internet-based telephone services that do not offer “helpful” customer support — such as Google Voice.
Google Voice lets users choose a phone number that gets tied to their Google account, and any calls or messages to that number will be forwarded to your mobile number. But unlike phone numbers issued by the major mobile providers, Google Voice numbers can’t be stolen unless someone also hacks your Google password — in which case you likely have much bigger problems.
With Google Voice, there is no customer service person who can be conned over the phone into helping out. There is no retail-store employee who will sell access to your SIM information for a paltry $80 payday. In this view of security, customer service becomes a customer disservice.
Mind you, this isn’t my advice. The above statement summarizes the arguments allegedly made by one of the most accomplished SIM swap thieves in the game today. On July 12, 2018, police in California arrested Joel Ortiz, a 20-year-old college student from Boston who’s accused of using SIM swaps to steal more than $5 million in cryptocurrencies from 40 victims.
Ortiz allegedly had help from a number of unnamed accomplices who collectively targeted high-profile and wealthy people in the cryptocurrency space. In one of three brazen attacks at a bitcoin conference this year, Ortiz allegedly used his SIM swapping skills to steal more than $1.5 million from a cryptocurrency entrepreneur, including nearly $1 million the victim had crowdfunded.

A July 2018 posting from the “OG” Instagram account “0”, allegedly an account hijacked by Joel Ortiz (pictured holding an armload of Dom Perignon champagne).
Ortiz reportedly was a core member of OGUsers[dot]com, a forum that’s grown wildly popular among criminals engaging in SIM swaps to steal cryptocurrency and hijack high-value social media accounts. OG is short for “original gangster,” and it refers to a type of “street cred” for possession of social media account names that are relatively short (between one and six characters). On ogusers[dot]com, Ortiz allegedly picked the username “j”. Short usernames are considered more valuable because they confer on the account holder the appearance of an early adopter on most social networks.
Discussions on the Ogusers forum indicate Ortiz allegedly is the current occupant of perhaps the most OG username on Twitter — an account represented by the number zero “0”. The alias displayed on that twitter profile is “j0”. He also apparently controls the Instagram account by the same number, as well as the Instagram account “t”, which lists its alias as “Joel.”
Shown below is a cached snippet from an Ogusers forum posting by “j” (allegedly Ortiz), advising people to remove their mobile phone number from all important multi-factor authentication options, and to replace it with something like Google Voice.
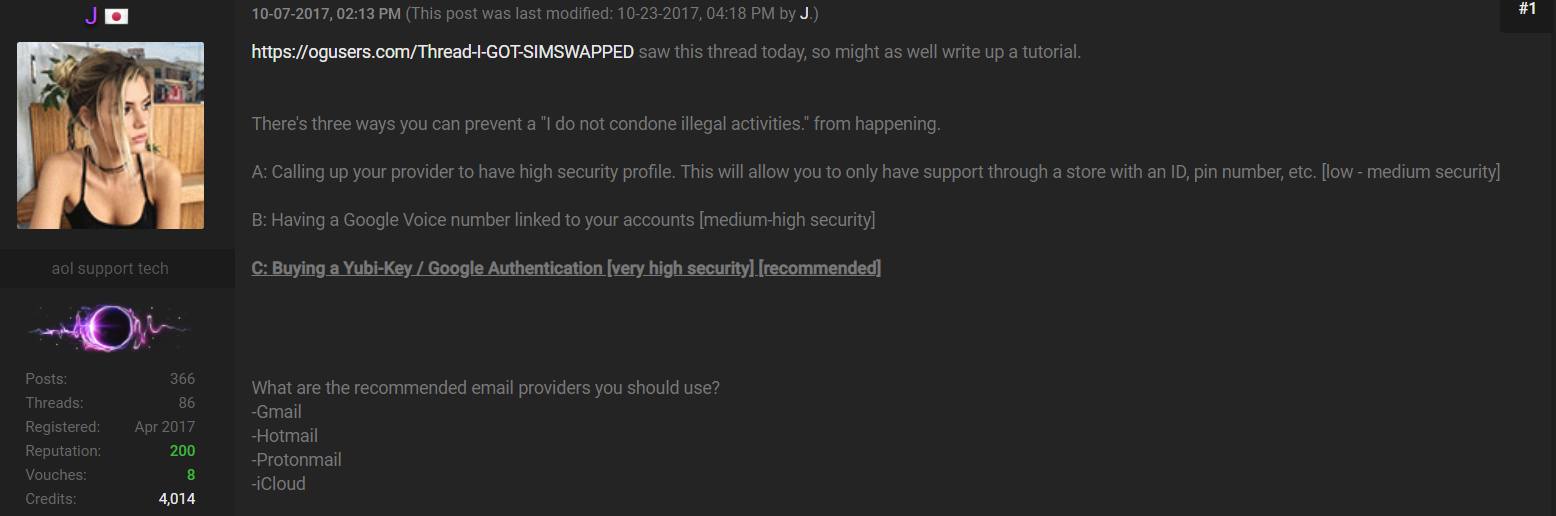
Ogusers SIM swapper “j” advises forum members on how not to become victims of SIM swapping. Click to enlarge.
Continue reading →











 According to security firm Ivanti, the first of the two zero-day flaws (
According to security firm Ivanti, the first of the two zero-day flaws ( “The FBI has obtained unspecified reporting indicating cyber criminals are planning to conduct a global Automated Teller Machine (ATM) cash-out scheme in the coming days, likely associated with an unknown card issuer breach and commonly referred to as an ‘unlimited operation’,” reads a confidential alert the FBI shared with banks privately on Friday.
“The FBI has obtained unspecified reporting indicating cyber criminals are planning to conduct a global Automated Teller Machine (ATM) cash-out scheme in the coming days, likely associated with an unknown card issuer breach and commonly referred to as an ‘unlimited operation’,” reads a confidential alert the FBI shared with banks privately on Friday.
 TCM is a subsidiary of Washington, D.C.-based ICBA Bancard Inc., which helps community banks provide a credit card option to their customers using bank-branded cards.
TCM is a subsidiary of Washington, D.C.-based ICBA Bancard Inc., which helps community banks provide a credit card option to their customers using bank-branded cards.