Aaron Wendel opened the doors of his business to some unexpected visitors on the morning of Mar. 16, 2011. The chief technology officer of Kansas City based hosting provider Wholesale Internet found that two U.S. marshals, a pair of computer forensics experts and a Microsoft lawyer had come calling, armed with papers allowing them to enter the facility and to commandeer computer hard drives and portions of the hosting firm’s network. Anyone attempting to interfere would be subject to arrest and prosecution.
Weeks earlier, Microsoft had convinced a federal judge (PDF) to let the software giant seize control of server hard drives and reroute Internet addresses as part of a carefully timed takedown of the Rustock botnet, which had long reigned as the world’s most active spam-spewing crime machine.
In tandem with the visit to Wholesale Internet, Microsoft employees and U.S. marshals were serving similar orders at several other hosting providers at locations around country. Microsoft’s plan of attack — which it spent about six months hatching with the help of a tightly knit group of industry and academic partners — was to stun the Rustock botnet, by disconnecting more than 100 control servers that the botnet was using to communicate with hundreds of thousands of infected Windows PCs.
Only two of the control servers were located outside the United States; the rest operated from hosting providers here in the US, many at relatively small ISPs in Middle America.
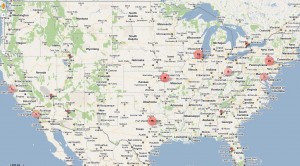
Microsoft was careful not to make any accusations that hosting providers were complicit in helping the Rustock botmasters; however, some of these control servers existed for more than a year, and most likely would have continued to operate undisturbed had Microsoft and others not intervened. Using data gathered by Milpitas, Calif. based security firm FireEye, which assisted Microsoft in the takedown, I was able to plot the location and lifetime of each control server (the map above is clickable and should let you drill down to the details of each control server; the raw data is here). The average life of each controller was 251 days — a little over eight months.
Wholesale Internet’s Wendel said his organization takes action against any customers that appear to be violating the company’s terms of use or its policies. But he insisted that the visit by Microsoft and the marshals was the first time he’d heard that any of the 16 Rustock command and control servers were located on his network.
“To be perfectly honest with you, we never heard of Rustock until Wednesday,” Wendel said in a phone interview last Friday. Wendel also said he hadn’t heard anything about the problematic servers from either Spamhaus or Shadowserver, which allow ISPs and hosting providers to receive reports about apparent botnet control servers and bot infections on their networks. Both Shadowserver and Spamhaus dispute this claim, saying that while they certainly did not alert Wholesale to all of the problem Internet addresses that it may have had on its network, they filed several reports with the company over the past six months that should have given the company cause to take a closer look at its customers and systems.
PUSHING THE LEGAL ENVELOPE
This is not the first time Microsoft has used the courts to kneecap a major spam botnet. In February 2010, Microsoft convinced a court to give it ownership of 276 domain names that were being used to control the massive Waledac botnet.
But Microsoft was forced to go a slightly different legal route in this civil case, said Richard Boscovich, senior attorney for Microsoft’s Digital Crimes Unit. Boscovich said the company gained authority for last week’s action by using a novel legal interpretation of The Lanham Act, federal statutes that prohibit trademark infringement, trademark dilution and false advertising.
For years, authorities and companies have used The Lanham Act to get permission to seize a range of counterfeit goods, such as knockoff designer handbags and pirated DVDs. In this case, Microsoft worked with pharmaceutical giant Pfizer, whose brand name blockbuster Viagra was among the trademarks most abused in the millions of spam emails being sent out daily by Rustock-infected PCs. According to a supporting document filed by Pfizer (PDF), company investigators followed the links in the junk e-mails, and purchased pills advertised as Viagra from the rogue online pharmacies linked in the messages.
Boscovich said that in addition to promoting rogue pharmacies, Rustock spam also was pimping lottery scams that abused Microsoft’s trademarks. Microsoft wanted to gather evidence of the spam “templates” (HTML content) the Rustock control servers were forwarding to infected machines for junk e-mail delivery.
“To do that we would potentially have to seize servers or hard drives, and my job as the lawyer on the team was to come up with some sort of legal strategy, because the legal remedy we’d used with Waledac didn’t give us the authority to seize” [physical property],” Boscovich told KrebsOnSecurity.com. “But the Lanham Act has a provision that allows you – under certain circumstances — to seize infringing items without notice, and then hold a hearing on the seizure several days later. So what I did was I used the analog in the cyber world, to get seizure warrants in all of the machines across the country that were [managing] the bots. And there we anticipated we would find templates on those drives with our trademarks and Pfizer’s would be present, and we would seize or copy those drives and that would be the evidence.”
But not everyone is comfortable with Microsoft or any other company pushing the envelope on civil statutes to seize digital equipment, particularly server hardware that may contain data that goes far beyond the scope of the alleged infringement used to justify the seizure order.
“When you treat hard drives as nothing more than a piece of equipment as opposed to a repository of information, some of which may be relevant to the case and some of which is not, you could run into a lot of trouble,” said Mark Rasch, a former computer crimes prosecutor for the U.S. Justice Department.
“We need to have a better, more efficient way of shutting down botnets in the US and internationally,” Rasch said. “I’d prefer that there was a separate remedy at our disposal that had privacy protections built-in.”
THE TAKEDOWN TOLL AND COMING CLEANUP EFFORT
According to the court order, Microsoft also won control over more than 1,500 domain names that Rustock-infected PCs could use to self-generate new control networks. Security experts believe Rustock has a mechanism for randomly generating and seeking out new Web site names that could be registered by the botmaster(s) to regain control over the pool of still-infected PCs.
In addition, the takedown effort involved the purchase of an unspecified number of as-yet-unregistered domains that Rustock may seek in the days and weeks ahead. Boscovich declined to say how many of these resurrection domains the company had registered, or for how long into the future it had registered them. But he said Microsoft and its partners in the takedown were seeking help from domain registrars and registries to avoid purchasing more new domains, which he said can become “very expensive” even for a short duration.
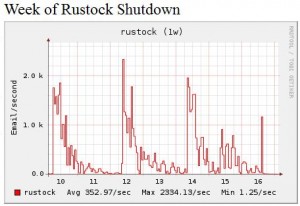
The stun against Rustock appears to have worked according to plan, at least for now. A new report published by the Composite Block List (CBL), the anti-spam group that gathers data used by Spamhaus, shows that Rustock had been pushing spikes of spam that regularly account for 80% of all spam. The CBL said this happened almost every other day, with a gradual decline in spam volume over the rest of each day and sometimes into the next.
From the CBL report:
“At 14:45 GMT on March 16, Rustock appears to have been ‘caught’ just at the beginning of one of these spikes, and abruptly and precipitously fell to essentially zero output. The shape of the event is more dramatic than the Rustock ‘vacation‘ during late Dec 2010 and early Jan 2011, and if prolonged, will represent a more significant event than the McColo shutdown in November 2008.”
Microsoft now is turning its attention to cleaning up the substantial pool of Windows PCs that remain infected with Rustock. The company believes upwards of a million computers may still be compromised by Rustock, which the software giant said often comes steeped in a “devil’s brew” of between 16 and 20 other malicious programs.
“We feel confident working with our industry partners that the fallback mechanisms embedded in the malware won’t succeed” [in resurrecting the botnet],” Boscovich said. “Now, our long term objective is to notify ISPs and get them to help clean the infected systems — not only of Rustock but a host of other bad things on them.”
Microsoft said that at the time of the Waledac takedown in February 2010, it observed approximately 70,000 to 80,000 infected IP addresses. “Thanks to clean-up efforts by the industry and customers, aided by natural decay, we are currently seeing just over 22,000 Waledac infected IP addresses, and we expect that number to continue to decline,” the company said in an e-mailed statement.
That cleanup effort could take a long time, even if Rustock does remain inactive. Unfortunately, even if this effort succeeds, there is no guarantee that other botnets won’t arise to fill the gap. Spamming is so profitable that other malefactors will soon jump in. No one has yet devised a long-term, fail-safe solution to the problem.
Read more about the impact of the Rustock botnet takedown:
FireEye: An Overview of Rustock





Actually, from your map it looks like 3 servers outside the US — there’s also one marked in Ontario, Canada.
So, did Microsoft make any arrangements to have those servers taken down as well?
Hiya Spaf. Thanks for the comment, and I’m glad for your question so soon, because I probably should have pointed this out in the story more clearly, and I expect I’ll still get a lot of questions because of that.
Basically, the map I built the data off of has historical (dead) C&C locations as well as the locations of those C&Cs that were active when Microsoft et. al. served the orders. So if you drill down to the Ontario location, you’ll see there’s a “First Seen” date of 3/27/2010, and a last seen date of 11/1/2010, which shows that this particular C&C was taken offline back in November and was not part of those that was nixed by this March takedown.
I used FireEye’s data for this chart, and I thought about just using the locations of the servers that were live on 3/16/2011, but I wanted to show how the bot herders apparently came back to the same hosting providers time and again.
Thanks Brian for the great report.
I used to be one of those insufferable Microsoft haters but I’m starting to like them now, despite the controversial legal tactics.
” . . . Spamhaus or Shadowserver . . . they filed several reports with the company over the past six months that should have given the company cause to take a closer look at its customers and systems.”
Just out of curiosity, does anyone know what tools, analytics or routines that hosting companies use to discover this kind of abusive (or infected) use of their servers ?
They can’t just be waiting for Spamhaus to send them an email. They’re just running some kind of anti-virus/malware software ? – or is it more sophisticated than that.
The easiest, no-cost way is to subscribe to Shadowserver’s daily report.
Of course, once you get the e-mail you have to actually use it — read the message, identify the customer(s), and then communicate with the customer. If the customer is non-responsive or unwilling to do anything about it, it may mean suspending their service until they come in compliance with your AUP.
“When you treat hard drives as nothing more than a piece of equipment as opposed to a repository of information, some of which may be relevant to the case and some of which is not, you could run into a lot of trouble,” said Marc Rasch, a former computer crimes prosecutor for the U.S. Justice Department.
“We need to have a better, more efficient way of shutting down botnets in the US and internationally,” Rasch said. “I’d prefer that there was a separate remedy at our disposal that had privacy protections built-in.”
——————————————————
Those 2 remedies are called statutes and treaties and while Microsoft used a novel legal approach to take down Rustock, Microsoft and their partners legal departments should be able to address the statute drafting and if they can’t, I CERTAINLY CAN, IF they contact me seeking help in those regards.
@ Brucerelator,
Unless the statute / treaties root is taken the “copyright infringment” path will fail as those running such a system will go for encryption etc.
This has a two found issue, the first is that showing how the infringment came about will be both technicaly and legaly difficult. It will fall to “expert testimony” and that can be fraught is the defence has the resources to rip into the prosecution resources.
Secondly it obviates an issue that is currently not be talked about and is going to become very significant in future times as the cloud takes off.
Communications companies (ie data in transit) usually have the protection of “common carrier” status, however those “who publish” carry liability for the actions of those they publish for.
But what about those who store data or process it in some way for another partie? At the moment the situation is ambiguous at best. In a traditional storage company senario you would not expect the company to look in the boxes and folders so they have little or no liability. But in a more old fashioned role of data processing (think typing pool) the person carrying out the processing has some responsability if it can be shown that a reasonable person would have known it to be questionable (ie typing up a blackmail note etc).
But what of a “blind service” where a computer owned by another processes the data in some way?
The problem as we have seen in the UK with the Computer Mis-Use Act a broad scoping of legislation suffers from the law of unintended consiquences. Whereby a software contractor was prosecuted and found guilty for mis-use because he put a time out clause in the software incase the client (who had a history of poor payment) decided yet again not to pay for his work…
Thus drafting such statutes often suffers from the law of “unintended consiquences” and I’m very sure that those who drafted the legislation Microsoft used had absolutly no notion it would or even could be used in the way it did.
Sometimes as in the UK this “pushing the boundries” on legislation gets called out by the judiciary, as was the case of R – Gold and Schifren that missuesd fraud legislation. And saddly gave rise to the drafting of the Computer Mis-Use Act and it’s overly broad “section 3”. Which sadly has been further expanded to cover the possession of “hacking tools” even though they are legitimate network and research tools…
Well done, Brian.
I’d be interested if you have a guesstimate on what revenue Wholesale Internet would have derived (in dollars/month) from hosting this botnet…lot of hard drives in that pic.
Thanks,
–Michael
I’d assume that pile of drives isn’t just from the one datacentre.
A whole lot of hard drives? Not really. I see less than 20 in the picture. The report said more than 100 servers at several locations. Even taking into account virtual servers and assuming multiple servers might reside upon a single host, that host was likely to have had RAID in place, requiring the removal of multiple drives per host. The number of drives confiscated was likely much greater than the number depicted.
I would not assume that they were making any money off of “hosting” these C&C servers at all.
These are spammers after all, who probably compromised the boxen in question.
Such great news account for substantially more than “A Little Sunshine”. Since I read that the Dutch High-Tech Crime Unit participated in the take-down, I gather/hope the 2 Control Servers in the Netherlands were also seized/taken offline.
On a different line of thought, Marc Rasch is right. With more and more hosting providers offering virtualized or even cloud based servers, often with external storage behind RAID controllers, how is going to continue this initiative to seize hard-drives without hurting legitimate customers whose only fault was their data happened to be in the same Raid group with the virtual storage used by a C&C server. And this doesn’t even consider the difficulty to use in court as evidence data (possibly originally encrypted) which was reconstructed from 64K-width Raid5 hardware stripes while the metadata is still somewhere in the not-seized controller’s flash.
Well I said it before Kudos to them for taking these guys down. While it would be great to see a law that relates to taking down BotNets, and other malware C&C’s in place sometime down the road, I say use what is available. One would have to believe that Microsft used this tactic against the Rustock gang because after they took down Waldec they need to change and evolve their game to try and keep them offline for a longer period of time and also use the seized data to do a little reverse engineering on the way it communicates, get instructions, and where and how it get it’s updates and who is behind it. While my e-mail and I have enjoyed looking at “zero” content in our junk mail section of our inbox I know that won’t last forever. I do take joy though at knowing that other botnet operators are probobaly quaking in their chairs at the thought that they may be the next target of a takedown By Micorsoft and some of it’s allies and I am sure they are all scrambling as we speak to try and thwart this. Let’s hope this is the start of a trend that makes things difficult to get these guys back on line and hits them where it hurts the most, their wallet! Maybe Brian will do an update on what some of the Botnet masters are discussing in ways to stave off being the next to go down!
Well gosh…..Wendel was totally surprised. Tough sheet Wendel.
I’m a retired Financial Advisor and our little semi-surbuban street has “group” email to alert us to neighborhood problems. Suddenly we received multiple emails from a neighbor with a single site listing that, when opened, “jumped” to a Candianian “RxPharmacy” that was loaded with every size and shape of Viagra including “Pink Viagra” and “supplemental” products that I had never heard of (but I’m old so what can I say?). He said he didn’t do it but it was sent to our group and multiple contacts of his. After receiving 4 over a 2-week period, they stopped. Does this sound like the type of spam that just pops up if someone accidentally hits that site?
It sounds like a pwned account to me. I’m surprised you only received 4 spam emails! Email accounts get cracked everyday by spammers looking for unprotected accounts, or accounts with weak passwords. Perhaps the “friend” who slipped up, changed their password?
Thanks for response….I gave him the AT&T tech number used when I had some internet problems….haven’t heard back but will ask. Of the 4 emails sent to our group and his list, all had different single web addresses but all opened to the same site with all the Viagra goodies. My hospital pharmacist told me those Canadian sites often have no idea where the meds come from….but I couldn’t tell anyway….I never tried it….a coupla beers and a charming young lady, or maybe not quite so young, always worked for me….but I’m old so what do I know?
Anyway, after reading all this, I just installed “Microsoft Security Essentials”, ran it, and it found no infections. So, hopefully, whatever that RxPharmacy thing was, it may not have left any residuals but we’ll keep checking anyway.
You should NOT click on links in emails, or open attachments to them, regardless of what security measures you have installed on your computer, unless you are absolutely sure of the sender. Multiple messages containing only links should have raised suspicions a lot sooner. When you aren’t certain what you’ve received, prudence would dictate that you call the named sender before you do anything with the email.
Ok, you’re right BUT I occasionally get emails from trusted folks who found a pertinent article to send, usually about medical advances (this is a medical family) or related info that they want to share so they copy the URL or simply send a note with it copied into the text. However, you are correct that these 4 were without any other text, each just with a single address that bounced to the pharmacy site. When I tried to seach for just the original base of the address, a message came up “forbidden site” or something similar.
But, again, if someone finds an interesting article on, say, Yahoo Finance, and want to send it, what is wrong with merely copying the address and forwarding it?….I guess the answer probably is that you only open one if you are really sure the person had already viewed it and isn’t sending you something problematic. Gee, ain’t technology wonderful??????
@ Jim E – There’s nothing wrong with sending links that you know are okay – a personalized message along with the link will reassure a savvy recipient that you sent it.
It’s just that a lot of spam will have a subject line that’s vague and general, something along the lines of “Look what I found,” or “I know you want to see this,” not necessarily using those exact words though. Spam sent through a botnet will have a sender’s name that may be someone you recognize, so it’s not enough to say “Oh, this is from so-and-so, whom I trust.”
It can get really wild on the internet, so be careful, especially since you know that at least one spammer already has your email address, whether they are currently using it or not.
To: JBV…thanks again…I received those 4 bad sites through our neighborhood “group” site so I don’t think whoever did it may have realized who would be getting it individually…..not that they would care, of course….but I doubt it they have anyone’s individual email address except my neighbor’s and the other several contacts his site was addressing, even if by “accident”.
But you advice is well-heeded…stay away from opening anything suspicious. One of my favorite sites is “www.fbi.gov” wherein you can subscribe to their email notices which include all the latest scams being investigated wheather phone, email, postal mail or whatever. What’s frightening is how many financial scammers they keep catching…..this was my old business and it is really one where you must trust your advisor and then some.
Two more things to reflect on Jim;
Clicking on anything in an email window can notify the spammer that your address is valid; then you will be bombed. A good email service will disable any email not on your trusted sender list, so that you can’t accidentally do this. Hotmail is one of them, and it is web-based email.
The other thing is that many addresses are generated by random name/address generators. They have no idea the address is valid until you respond.
Just remembering these simple rules has kept my inbox very clean for over ten years.
Oh! And third, don’t forget to change your password, if you suspect the group has been infiltrated by spammers. This is true for FaceBook and a lot of other places spammers like to pwn.
This is the sort of thing Microsoft should do much more to help restore some faith in Microsoft PCs as “secure”.
The reasons for insecure PCs and servers may have nothing to do with MS directly, and yet they will continue to bear the reputational impacts as long as they rely upon regular folks to lock down their own gear.
Perhaps, Brian, you might conduct some followup research to see how many, if any, legitimate small businesses had their web presence wiped out with the removal of the Rustock data and hardware from these hosting providers.
While the folks at Microsoft are thumping their chest, what efforts did they make to ensure they didn’t destroy legitimate mom and pop operations who do nothing but pay their mortgage by selling widgets on the internet. Certainly, this isn’t the first time a hosting provider and it’s hundreds of legitimate customers has been taken down by search warrant.
I’m certainly glad that neither myself, nor any of my clients, may of whom are non-profits desperately scraping by, were affected by this, this would be a really bad time for us to find ourselves scrambling to regain our presence and customer confidence.
ISPs must have abuse contacts, but there is no validation that behind that abuse email address is a valid abuse process that actions legitimate abuse complaints. In my experience the vast majority of ISPs do not staff their abuse desk adequately to deal with even a small portion of the complaints that they receive.
When I last worked in a Network Operations Center we did not respond to each abuse complaint. However it was policy to contact the possible abuser. We would try to get there side of the story and help them solve issues with compromised systems. If we were unable to get ahold of someone or they refused help we would wait for three abuse complaints from different origins and then shut them off until they called in for service. At which time we would assist them in solving the issue. I also have a serious issue with Microsoft or our government seizing hard drives. I believe if we allow such behaviour we will see cases where victims of a virus will be victimised by seizures. For a better idea of how seizures can go wrong look at the seizure of “moo.com”. I’m all for putting more pressure on the ISP or hosting service, but seizures are a very dangerous game.
Now that the threat of seizures is very real, the risk of service disruption to end-customers may be real enough that data center and network operators may pay more attention.
From a customer perspective, who wants to colo in a facility where there’s the risk that my business may be put out of service? Maybe prospective customers will look for their data center and network operators to provide some assurances about their abuse handling policy and responsiveness.
If this was supposed to reduce spam volume dramatically, or even modestly, it did not work on my end. My Hotmail webmail spam box had more bogus pharmaceuticals crap in it today than it has in weeks.
I’m in the same situation as Mark except my spam monitoring Gmail account went a little silent for about 24 hours and by Friday (3/18) spam levels were back up.
I have had a few email addresses available online for 12-13 years, and the volume of spam dropped off the table completely. Hope it stays this way for as long as possible.
Drop by Microsoft’s Digital Crimes section on facebook and give them a thumbs up.
Maybe it’s a coincidence, but my last junk email is dated 3-16. The problem was so bad before, I had looked into how I could block the viagra and pharm ads at my ISP. Unfotunately, there is no option to block on subject or message content/keywords. Good job MS!
@K. Moore;
It has been my experience that occasionally spammers figure a way around the MS filters for hotmail. I will get bombed for a day or two; but past that, they disappear as MSN figures out how to block them.
I have NEVER seen this kind of efficiency with Gmail, Yahoo!, or any other service. I always mark them as junk, to help them along. This has happened less and less in recent years. In fact – I can’t remember one incident within two years past.
@me:
> While the folks at Microsoft are thumping their chest, what
> efforts did they make to ensure they didn’t destroy
> legitimate mom and pop operations who do nothing but pay
> their mortgage by selling widgets on the internet.
> Certainly, this isn’t the first time a hosting provider and
> it’s hundreds of legitimate customers has been taken down by
> search warrant.
I strongly recommend that you read FireEye Research’s blog about that.
http://blog.fireeye.com/research/2011/03/an-overview-of-rustock.html
Another interesting note is that to aggravate attribution, many were also
running TOR nodes and other services (sorry Abuse Desk, that
wasn’t me, it was just someone on TOR!). Another possibly is
that they did this to bolster the TOR network for their own
criminal interests — we saw this happen in the McColo case
as well. It should be of no surprise to anyone that these
servers were dedicated purely to the criminal actors, which
is shown by our own metrics (including traffic monitoring at
large access points and passive DNS research) as well as the
fact that no one has come forward to complain that their
legit sites were taken down. Additionally, there was a
substantial pile of money put up as a bond in case we were
in err.
FireEye – whose research regarding botnets overall has been really solid going on several years now – assisted with the months-long investigation (in fact they were researching Rustock for years before this.) They ascertained that these servers *solely* existed to engage in this malicious activity. This has been mentioned in the official microsoft blog as well and I’m baffled that so many readers haven’t digested it. This was not a “hey let’s shut everyone down on a whim” action. Microsoft and all of their assisting researchers and legal staff made 100% certain these servers were being operated by criminals before they drafted the first warrant.
SiL / IKS concerned citizen
From a gut level ‘social reverse engineering’ POV, me’s complaint resembles the seemingly never ending ‘woe is me’ tales @ Craigslist’s ‘Flag Help’ forum. Everyone whose ad is flagged off is an innocent victim, just trying to earn an honest living. There’s no better place to learn a ‘caveat emptor’ POV.
Thanks Brian–amazing reporting as always.
RE: The FireEye post: “It should be of no surprise to anyone that these servers were dedicated purely to the criminal actors, which is shown by our own metrics (including traffic monitoring at large access points and passive DNS research) as well as the
fact that no one has come forward to complain that their legit sites were taken down.”
I believe FireEye and their data in this case. However, the judge was never presented any of this evidence regarding how they knew which IP addresses were Rustock before making a decision. What protects private parties from less thoroughly researched seizures? The end paperwork of a guesstimate and months of research looks the same to a judge.
RE: “Additionally, there was a substantial pile of money put up as a bond in case we were in err.”
This is very interesting and makes me feel a lot better about the tactics. I’d like to know the details of the arrangement in case of error. How much is a “pile of money” to Microsoft? What is the burden of proof for an error? The wrong parameters here could render this a meaningless token gesture.
Congratulations, Brian, great reporting. keep it up ..
This takedown of Rustock following the previous takedowms begs the question – what next? Next operations should be Lethic and Festi if you go by this report
http://www.m86security.com/labs/spam_statistics.asp
The writing must be on their walls.
I’m a sysadmin and manage numerous Exchange servers and hundreds of desktops. I always have to ask myself “WHY” when Microsoft gets involved in such “ultruistic” acts such as this. I can’t imagine it has anything to do with reducing the volume of SPAM, as that cost is usually not born by them. Possibly the ubiquity of network/mail delivered Malware, but again this is as common today as it was 5 years ago albeit the severity of the payload is greater.
One thing is fact! AV software vendors are having a tough time figuring out how to keep desktops uninfected, particularly systems not hammered down by IT departments. If this is the motivation I am glad, because corporate users are expecting far more flexibility on how they use their systems, and I even see Marketing departments developing entire LAN’s for themselves because they’re sick and tired of being limited by so called security systems and they feel like their competitors are leaving them behind because of it.
The reason MS is involved so much is the fact that most people associate the SPAM/malware problem with bugs in Microsoft’s codebase. There is a perception of a chain of events in public’s mind – Microsoft’s developer makes a mistake, spammer exploits it, fills our mailboxes with filth and steals money from our bank accounts. Now, if there was another desktop OS dominating today, it would be another company in this position because as we all know such bugs are almost inevitable. But as it is today, Microsoft gets the blame and they are trying to do what they can to be seen not just as a problem but as part of solution.
“..particularly server hardware that may contain data that goes far beyond the scope of the alleged infringement used to justify the seizure order.”
That part freaks me out. As a server admin, I’d push the panic button to wipe everything, take a local copy in my pocket to protect the data.
– “… Just a second…”
They shouldn’t be allowed to justbarge in and STEAL data from other companies. No matter the reason. There are other ways.
I wouldn’t wipe servers after having received a subpoena….
Just a thought here.
Why isn’t there a searchable database on the infected IP addresses?
I admit I’m naive about much of this security stuff.
I’m sure though – not counting professionals in the business – I read more than my share on security issues and I’ve not once come across (a) way that allows a person to cross check his IP address.
Such database will become inaccurate too fast – most infected PC’s have dynamic IP addresses. Given the shortage of IPv4 space, the lease times will likely to be less in the future which will make such database even less reliable.
Organizations such as Shadowserver have such lists of IP addresses, plus there’s the Google Safe Browsing page, ZeusTracker, StopBadWare, etc.
It’s out there, one just needs to subscribe or make shortcuts to their page and check regularly.
Good post frnkblk;
I figured someone had to maintain such a list – otherwise the popular host files wouldn’t work as well as they do, and MBAM wouldn’t do such a good job blocking malicious IP addresses!
I don’t think Rustock’s creators are so stupid to be taken out by surprise.
Tilting at windmills at it’s finest.