A 16-year-old male from Ottawa, Canada has been arrested for allegedly making at least 30 fraudulent calls to emergency services across North America over the past few months. The false alarms — two of which targeted this reporter — involved calling in phony bomb threats and multiple attempts at “swatting” — a hoax in which the perpetrator spoofs a call about a hostage situation or other violent crime in progress in the hopes of tricking police into responding at a particular address with deadly force.
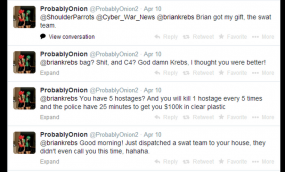 On March 9, a user on Twitter named @ProbablyOnion (possibly NSFW) started sending me rude and annoying messages. A month later (and several weeks after blocking him on Twitter), I received a phone call from the local police department. It was early in the morning on Apr. 10, and the cops wanted to know if everything was okay at our address.
On March 9, a user on Twitter named @ProbablyOnion (possibly NSFW) started sending me rude and annoying messages. A month later (and several weeks after blocking him on Twitter), I received a phone call from the local police department. It was early in the morning on Apr. 10, and the cops wanted to know if everything was okay at our address.
Since this was not the first time someone had called in a fake hostage situation at my home, the call I received came from the police department’s non-emergency number, and they were unsurprised when I told them that the Krebs manor and all of its inhabitants were just fine.
Minutes after my local police department received that fake notification, @ProbablyOnion was bragging on Twitter about swatting me, including me on his public messages: “You have 5 hostages? And you will kill 1 hostage every 6 times and the police have 25 minutes to get you $100k in clear plastic.” Another message read: “Good morning! Just dispatched a swat team to your house, they didn’t even call you this time, hahaha.”
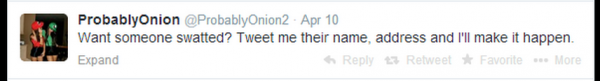
I told this user privately that targeting an investigative reporter maybe wasn’t the brightest idea, and that he was likely to wind up in jail soon. But @ProbablyOnion was on a roll: That same day, he hung out his for-hire sign on Twitter, with the following message: “want someone swatted? Tweet me their name, address and I’ll make it happen.”
Several Twitter users apparently took him up on that offer. All told, @ProbablyOnion would claim responsibility for more than two dozen swatting and bomb threat incidents at schools and other public locations across the United States.
On May 7, @ProbablyOnion tried to get the swat team to visit my home again, and once again without success. “How’s your door?” he tweeted. I replied: “Door’s fine, Curtis. But I’m guessing yours won’t be soon. Nice opsec!”
I was referring to a document that had just been leaked on Pastebin, which identified @ProbablyOnion as a 19-year-old Curtis Gervais from Ontario. @ProbablyOnion laughed it off but didn’t deny the accuracy of the information, except to tweet that the document got his age wrong. A day later, @ProbablyOnion would post his final tweet: “Still awaiting for the horsies to bash down my door,” a taunting reference to the Royal Canadian Mounted Police (RCMP).
According to an article in the Ottawa Citizen, the 16-year-old faces 60 charges, including creating fear by making bomb threats. Ottawa police also are investigating whether any alleged hoax calls diverted responders away from real emergencies.
Most of the people involved in swatting and making bomb threats are young males under the age of 18 — the age when kids seem to have little appreciation for or care about the seriousness of their actions. According to the FBI, each swatting incident costs emergency responders approximately $10,000. Each hoax also unnecessarily endangers the lives of the responders and the public.
Take, for example, the kid who swatted my home last year: According to interviews with multiple law enforcement sources familiar with the case, that kid is only 17 now, and was barely 16 at the time of the incident in March 2013. Identified in several Wired articles as “Cosmo the God,” Long Beach, Calif. resident Eric Taylor violated the terms of his 2011 parole, which forbade him from using the Internet until his 21st birthday. Taylor pleaded guilty in 2011 to multiple felonies, including credit card fraud, identity theft, bomb threats and online impersonation.
In nearly every case I’m aware of, these kids who think swatting is fun have serious problems at home, if indeed they have any meaningful parental oversight in their lives. It’s sad because with a bit of guidance and the right environment, some of these kids probably would make very good security professionals. Heck, Eric Taylor was even publicly thanked by Google for finding and reporting security vulnerabilities in the fourth quarter of 2012 (nevermind that this was technically after his no-computer probation kicked in).
Update, 2:42 p.m. ET: The FBI also has issued a press release about this arrest, although it also does not name the 16 year-old.




Has there been any advancement in technology to prevent or flag callerID spoofing? Maybe flagging or outcasting switches that are known to condone the practice?
Brian,
Would love to see a blog on callerID technology & efforts to reduce or eliminate the practice of spoofing… or info about why it’s so hard to do.
Caller ID’s are insecure by design. They have always been spoofable. There are valid uses for spoofing caller IDs but sadly, today, spoofing is being used for more worse than good.
I like this comment, because it fits against most everything we talk about with anonymity and the Internet and so on. It’s really the crux of our discussions for decades in security: How much misuse constitutes stealing away freedoms?
“valid uses for spoofing caller ID”
Like?
Whistleblower afraid of retaliation?
Or a company with multiple phone lines that want all of them to show the “main” number.
Or a company using backup trunking to route calls through another site when their primary lines are down (we do this all the time).
The existence of some reasons to use an alternate caller ID different from the inbound number, is no reason for the Telco to allow an Arbitrary caller ID.
They could require a ‘confirmation process’; where the phone company will Call the actual number, before approving a line with a different number to use that number as Caller ID. And paperwork documenting ownership of the line whose caller ID is to be reused.
Some simple changes to the workflow used by Telco providers, could prevent these exceptional situations from being used as a way of spoofing arbitrary caller ID numbers.
This is nota workflow isue, it is a engineering isue. sec urity was not a factor when the engineering was completed and implementd, so the “hooks” are not present to enable the right design changes. with voip, se curity design flaws can be resolved, but new processes in the telco industry only take place with regulatory infuences.
Reading the rest of the comments… 140 on 19-May-2014, I’m even more curious about spoofed callerID, use of ANI, ways that individual switches could reduce the ability spoofing (ie, flag calls from outside a TELCO’s set of local switches). Here is a quick set of links to assist anyone else that is curious…
http://lifehacker.com/5853056/how-to-spoof-caller-id
https://encrypted.google.com/books?id=1PVZHtB6XAwC&pg=PT924&lpg=PT924&dq=%22how+to+spoof+ani%22&source=bl&ots=svMDYv1k9N&sig=t5qaAyqllqCT-GBDCMarKSLu4eA&hl=en&sa=X&ei=v4J6U9f8MMOXyASrloCYCA&ved=0CDIQ6AEwAQ#v=onepage&q=%22how%20to%20spoof%20ani%22&f=false
http://www.bloggernews.net/123057
One of the recommendations is to cancel your landline… think I might just do that!
Troy.
#
I actually hope that someone continues to engage in “swatting”. While I doubt this kid had anything else except harassment on his mind, the practice actually identifies a weakness in the system. Namely that tactical units are deployed with far too little actual evidence or intelligence. The fact that a phone call can incite a tactical unit deployment is deplorably irresponsible use of force on the side of law enforcement.
The question that the public should be asking is not “who called this in”, but “why the hell are you deploying tactical response units with nothing more to go on than a phone call”???
Brilliant points, Mr Fitzner!
Kurt, don’t you think that the nature of an emergency is such that your suggestion is inherently unworkable? The word is defined as “a serious, unexpected, and often dangerous situation requiring immediate action.” So, should fire departments also wait until they can smell the smoke before deploying? There is no way to responsibly implement your suggestion.
+1
Since emergency response isn’t instantaneous, a response team can be dispatched while the the call center simultaneously trackbacks the call. Even calling the caller ID # to see if it’s valid should be a minimum response. That should even be an automated process and I question why that isn’t already being done for everyone and not just those that have been previously SWATed. At no place ever, do you get police response in under 3 minutes and certainly not a SWAT response in under 5 minutes. Period!
You’re right. And the moment a call isn’t responded to in a timely fashion and someone(s) is killed due to it, then we’re get outcry in the other direction.
What do you propose?
Another +1
I can tell you why… it’s called September 11th.
no thanks, i prefer not being swatted by teenage pranksters, especially since those guns being pointed at me have real bullets and the finger on the trigger is very twitchy
You really do get the weirdos, don’t you? Sadly, this kid is probably related to me somehow (I’m related to everyone in the Ottawa Valley) so on behalf of Ottawanians, I apologize.
There is ahuge missing part to this story.
“a document that had just been leaked on Pastebin”
Who leaked it?
My guess is NSA resources were used and then enough information was assembled into a Pastebin document to be able to use that as a plausible coverstory. Assuming this is true (which it very well may not be), this is why I worry about all that data NSA collects. It’s just too useful to be able to say “terrorism only!” It will increasingly be used for solving all kinds of criminal activity and eventually will become routinely used for the common and mundane such as child support payments, etc. It’s a monster just waiting to be let loose.
+1
LOL! 😀 Funny. Actually it’s credited to @CherryTheGod, another kid (? not sure) with great skills, who use them to make a good things instead of harm other people. According to him, he has used Google and some leaked databases only.
Try to think about what you write down. Do you think that NSA use Pastebin for their internal documents? 😀
Hmmm… @CherryTheGod follows @ProbablyOnion
Is this a case of human malware?
I always find it funny when the so called untouchables get their life taken away in a matter of seconds
damn srs hacking and swatting discussions on twitter is one of the deepest trenches in the spergnet
If its true that his father was beating him, I would very much like to see him put on trial as well; he is truly responsible for this boy’s actions.
Clarification, the hacker who leaked the dox attributed his actions to his father’s abuse and gender confusion.
I submit that the boy is responsible for his own actions. Lots of people go through beatings and don’t end up swatting strangers. However, that doesn’t mean an abusive parent isn’t responsible for for *his* actions, and that may include being a contributing factor to the boy’s misdeeds. I would not give the boy a “pass” because he’s been beaten, but if he was then there’s blame and aplenty to go around, and Dad should own his share.
I wonder how come the police aren’t checking ANI before responding, to identify possible spoofing.
I assume it is the new callerID service they are spoofing successfully, which really has no security — many providers let the user customize the callerID.
The ANI / Calling party billing phone number, however, is not supposed to be customer-definable.
I’m not entirely sure about this but I remember that a fair majority of swatting calls are from Text to Phone relay services as those provided by AT&T.
Caller ID spoofing is not always used for calls like these.
Brian,
It’s been a while since I wrote on your site, but I had to comment on this.
First of all; loved how you sucked him in and then dropped the internet hammer on him.
Second on my list; thanks for writing these stories about these little useless piles of amphibious whale crap and exposing them for what they are.
Brilliant sir, just fing brilliant!!
Curtis,
Thanks for the laugh you little hemorrhoid on the butt of our society. You can’t fix stupid….boy
911 centers do use ANI and not caller id… And although ANI is more difficult to spoof it still relies on the telcos to identify someone is messing with the data. That is where the problem is currently… Someone with the right equipment can inject bad data to the telco and one branch office will pass it on to the next one with no vquestions asked.
Dispatchers are trained to get help to the scene as quickly as possible and lack the ability (due to policy not skill/etc mind you) to question if a call is legitimate. The investigation comes from those with badges and guns.
Y’all are forgetting that a large percentage of “swatting” calls come from cell phones, including many (including throw-aways) that have been “retired” but that can still be used to dial 911. Neither CallerID nor ANI are of any value because it’s almost impossible to locate these callers.
In fact, in the Bay Area of CA, it is believed that one individual is responsible for literally hundreds, if not thousands, of “swatting” calls and has defied the best efforts to locate him.
So let’s recognize that there is a problem out there and even someone who’s 16 or 17 knows full well what they’re doing and its implications… but like online hackers, they simply don’t care about who gets hurt.
Until it’s them. Let’s hope more get caught and dealt with to the FULLEST extent of the law.
lol @ curtisg
“these kids who think swatting is fun have serious problems at home, if indeed they have any meaningful parental oversight in their lives”
Terribly, there are also some grown adults who do this to their enemies. Neal Rauhauser comes to mind. He is connected to many SWATting incidents in what is apparently a harassment-for-hire avocation.
The general pattern, of making false police reports in order to damage opponents, poses serious threats to law & order, so the deterrent against abusers ought to be appropriately severe.
You won’t / shouldn’t see his name in Canadian media, as offenders under the age of 18 have their identity protected in Canada under the Youth Criminal Justice Act (Part 6, Section 110). I suspect this is why the FBI did not disclose his identity in their announcement.
Sucks that he targetted you, but glad that he got arrested!
Seriously? One delayed response to investigate the accuracy of a report could cost lives then we’d never hear the end of it. Law enforcement HAS to take reports seriously & approach w/ caution The solution is to fix the swatters abity to spoof callerID & prosecute fully those who perpetrate these incidents
Given the kid IS legally a minor, shouldn’t you be removing his name from the post. Don’t know about the US but in many countries, naming minors charged with crimes in publically accessible media would get you into hot water.
Yes this always looks good, and we all want to protect the children, but it is unfortunately taken to the extreme where children become the new dictators of society, and mad tyrants run amok! You have to have a balance somewhere or the Tribulation will surely follow!
The association of crime to criminal and his identity became public, when the minor posted to Twitter. Also, providing shielding for his good name from the consequences of his actions would only serve to encourage more misguided teens to follow in his footsteps to put other people in danger.
I hope throw put this little moron in a very deep hole and leave him there for a very long time…toss him potato peels and apple cores to eat, and maybe when he comes out he will learn to leave other people alone. Ya’ think?
As an investigative journalist you do realize it’s against the law to name a minor .. even if that information has been uploaded by another source? You realize you can be sued for this right?
I agree swatting is ridiculous and a waste of a city’s resources, and can prove dangerous in some situations, but you need to let the police handle it. I’d strongly advise you edit this copy.
Are you giving legal advice to attempt to censor information already released to the public? What are your credentials to do so?
1979: Smith v. Daily Mail, U.S. Supreme Court: Journalists’ first amendment rights include the right to use the names of minors in newsworthy stories as long as the information is lawfully obtained and truthfully reported.
Eighteen years as a journalist. Expert in libel in three countries. There are different laws protecting youth in the UK and US .. Canada has very strict regulations about naming minors, even when they have been convicted. It could result in jail time for the person who named them. I would strongly advise this author to revise the copy and let the police sort it out.
Brian isn’t a resident of Canada and he’s U.S. based security researcher/journalist. I’m no expert in any type of law, but I don’t see how Canadian law applies to Brian’s reporting in the U.S., i.e., Canada doesn’t seem to have any legal standing to bring charges against Brian.
Moreover, since the U.S. Supreme Court has already settled the matter in regard to the naming of juveniles in the U.S., I can’t imagine any attempt to extradite Brian would be successful.
You will note how the Citizen handled it, there is a paragraph citing this very information in the story linked above.
Please note how the Ottawa Citizen handled it in its copy. Note the citation of laws in Canada near the bottom of the story.
Journalist,
Not its not!!!! He believed the man was 19 years old….but obviously you have trouble reading.
I can only cite what I know and upon learning that this kid is a minor, he should not have cited any identifying information about the kid. He posted this blog after it was discovered (and wrote about the tweet identifying that the child was a minor in the above blogpost). The tweet clarifying error in age is May 7, this blog post is May 12 .. there’s liability there.
Couldn’t agree more.
I just don’t get it how can Brian happily allow people to put up comments mentioning , even as a joke, that this child is to be raped (!) and remove my comments about overall stupidity of the whole post, as one must really be nuts to feel glorious about stuff like this.
Brian do you condone underage rape or what?!
Anyways, I say Freedom to Curtis!
you have never been swatted before, it si a very dangerous experience, and when innocent people shoot innocent people because some kid wanted a laugh?? really, you want this??
hes 16 btw lol
So what happens when you have a real problem?
There is a strong argument for tying in emergency responder phone numbers (e.g. 911) to phone companies, to immediately trace the number from which emergency calls originate.
E.g. suppose a “swatter” spoofs my phone number, and tells police that there is an armed home invasion or hostage situation at my house. My number may show up on the police’s caller ID system but, if they can immediately trace phone activity to my phone company, the phone company’s records will show that my number did not call the police line.
This would prevent people with phone spoofing systems from making bomb threats with impunity, or making other false reports to agencies of public safety.
Brian,
They all may be teenagers but I can assured you that they were hired and paid by some parasite. They are not lone rangers.
This article gives a perfect example of the growing importance of computer forensic analysts in today’s IT industry. Cybercrimes are becoming more popular, some more serious than others, but there are people studying the best ways to investigate these problems and how to solve them. By learning how to obtain evidence track down these people to prevent them from committing these crimes, hopefully there will be a decrease in these types of incidents.
here is the pastebin in question, http://pastebin.com/G2Yp4wSR. Not sure why krebs deleted my original post about it.
Why would I delete your pastebin link? I almost never delete comments, but I consider exceptions for people who groundlessly accuse me of doing so.
In any case, I see three comments from you, including the original pastebin link, so I’m not sure what your problem is exactly.
I’m stupid and didnt click the Older Comments button. My apologizes bruh!
Sorry about that Krebs.Even here in canada we have our dumbass kids also.
Kid needs a good smack upside the head.