Last month KrebsOnSecurity published research into a large distributed network of apparently compromised systems being used to relay huge blasts of junk email promoting “online dating” programs — affiliate-driven schemes traditionally overrun with automated accounts posing as women. New research suggests that another bot-promoting botnet of more than 80,000 automated female Twitter accounts has been pimping the same dating scheme and prompting millions of clicks from Twitter users in the process.
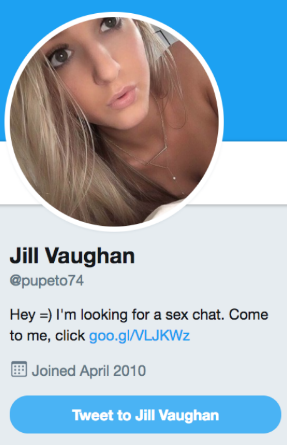
One of the 80,000+ Twitter bots ZeroFOX found that were enticing male Twitter users into viewing their profile pages.
Not long after I published Inside a Porn-Pimping Spam Botnet, I heard from researchers at ZeroFOX, a security firm that helps companies block attacks coming through social media.
Zack Allen, manager of threat operations at ZeroFOX, said he had a look at some of the spammy, adult-themed domains being promoted by the botnet in my research and found they were all being promoted through a botnet of bogus Twitter accounts.
Those phony Twitter accounts all featured images of attractive or scantily-clad women, and all were being promoted via suggestive tweets, Allen said.
Anyone who replied was ultimately referred to subscription-based online dating sites run by Deniro Marketing, a company based in California. This was the same company that was found to be the beneficiary of spam from the porn botnet I’d written about in June. Deniro did not respond to requests for comment.
“We’ve been tracking this thing since February 2017, and we concluded that the social botnet controllers are probably not part of Deniro Marketing, but most likely are affiliates,” Allen said.
ZeroFOX found more than 86,262 Twitter accounts were responsible for more than 8.6 million posts on Twitter promoting porn-based sites, many of them promoting domains in a swath of Internet address space owned by Deniro Marketing (ASN19884).
Allen said 97.4% of bot display names had the pattern “Firstname Surname” with the first letters of each name capitalized, and each name separated by a single whitespace character that corresponded to common female names.
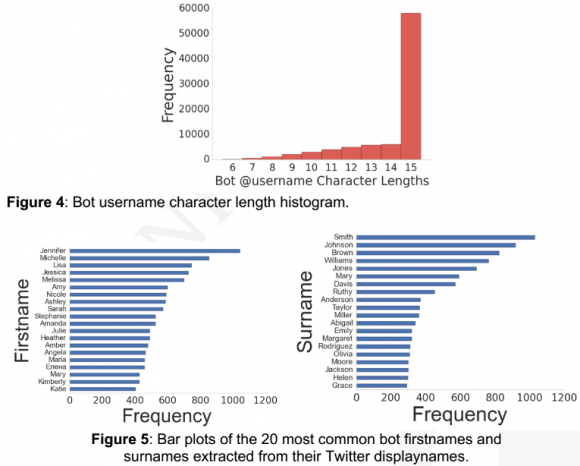
An analysis of the Twitter bot names used in the scheme. Graphic: ZeroFOX.
The accounts advertise adult content by routinely injecting links from their twitter profiles to a popular hashtag, or by @-mentioning a popular user or influencer on Twitter. Those profile links are shortened with Google’s goo.gl link shortening service, which then redirects to a free hosting domain in the dot-tk (.tk) domain space (.tk is the country code for Tokelau — a group of atolls in the South Pacific).
From there the system is smart enough to redirect users back to Twitter if they appear to be part of any automated attempt to crawl the links (e.g. by using site download and mirroring tools like cURL), the researchers found. They said this was likely a precaution on the part of the spammers to avoid detection by automated scanners looking for bot activity on Twitter. Requests from visitors who look like real users responding to tweets are redirected to the porn spam sites.
Because the links promoted by those spammy Twitter accounts all abused short link services from Twitter and Google, the researchers were able to see that this entire botnet has generated more than 30 million unique clicks from February to June 2017.
[SIDE NOTE: Anyone seeking more context about what’s being promoted here can check out the Web site datinggold[dot]com [Caution: Not-Safe-for-Work], which suggests it’s an affiliate program that rewards marketers who drive new signups to its array of “online dating” offerings — mostly “cheating,” “hookup” and “affair-themed” sites like “AdsforSex,” “Affair Hookups,” and “LocalCheaters.” Note that this program is only interested in male signups.]
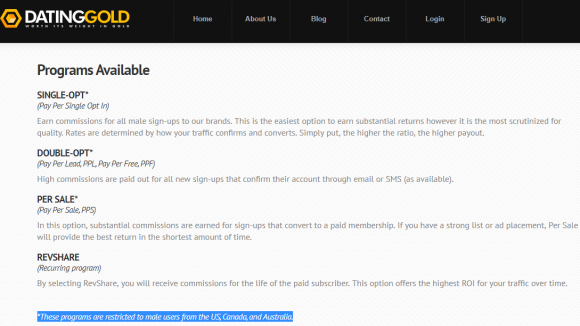
The datinggold affiliate site which pays spammers to bring male signups to “online dating” services.
Allen said the Twitter botnet relies heavily on accounts that have been “aged” for a period of time as another method to evade anti-spam techniques used by Twitter, which may treat tweets from new accounts with more prejudice than those from established accounts. ZeroFOX said about 20 percent of the Twitter accounts identified as part of the botnet were aged at least one year before sending their first tweet, and that the botnet overall demonstrates that these affiliate programs have remained lucrative by evolving to harness social media.
“The final redirect sites encourage the user to sign up for subscription pornography, webcam sites, or fake dating,” ZeroFOX wrote in a report being issued this week. “These types of sites, although legal, are known to be scams.”
Perhaps the most well-known example of the subscription-based dating/cheating service that turned out to be mostly phony was AshleyMadison. After AshleyMadison’s user databases were plundered and published online, the company admitted that its service used at least 70,000 female chatbots that were programmed to message new users and try to entice them into replying — which required a paid account.
“Many of the sites’ policies claim that the site owners operate most of the profiles,” ZeroFOX charged. “They also have overbearing policies that can use personally information of their customers to send to other affiliate programs, yielding more spam to the victim. Much like the infamous ‘partnerka’ networks from the Russian Business Network, money is paid out via clicks and signups on affiliate programs” [links added].
Although the Twitter botnet discovered by ZeroFOX has since been dismantled, it not hard to see how this same approach could be very effective at spreading malware. Keep your wits about you while using or cruising social media sites, and be wary of any posts or profiles that match the descriptions and behavior of the bot accounts described here.
For more on this research, see ZeroFOX’s blog post Inside a Massive Siren Social Network Spam Botnet.




Brian, I’m always educated by your investigative journalism and enjoy your sleuthing. Thanks for another fine article.
The battle against SPAM and PORNO SPAM, on all fronts, may need to go up a notch all many fronts, technical as well as legal. TWITTER may need to pick up its efforts if it wants to survive.
As of now, many have to abandon an email address because too many spammers have it (a result in my case, and many others, of security breaches).
If spammers start losing money SPAM will disappear.
Thanks for another informative article.
Actually, if spammers start losing money, they will adjust and find another, and likely more insidious, way of making money off of people. The criminal and devious mentality is still the same, they will just be forced to adapt. That’s the way these sort of people work.
” Twitter accounts has been pimping the same dating scheme and ginning up millions of clicks from Twitter users in the process.”
Hopefully well received suggestion, but I believe you meant “gaining” instead of ginning
It’s not wrong, from a manner of speaking, but it’s not clear either so I’ve changed it to be more clear.
Here’s the usage to which I was referring earlier: https://thebettereditor.wordpress.com/2012/03/10/time-to-gin-up-an-explanation/
For the Krebs on Etymology discussion board:
http://www.etymonline.com/index.php?term=gin };^D
For the Krebs on Etymology discussion board:
h t t p : / /w w w . etym online . com / index . p h p ? term = gin
};^D
Actually, ‘gin up’ is a legitimate, if uncommon, phrase.
http://www.dictionary.com/browse/gin-up
Boy this guy is a gem:
http://www.danhatesspam.com/cases/deniro_4ac.pdf
Interesting read , Brian
Yes, I did notice lately that I would get likes on my random tweets or retweets by accounts with attractive images of females. And then if you check, the account literally has 2 or 3 pictures of different 🙂 scantily clad females, about a dozen of followers and a handful of similar tweets. All with shortened goog.gl links. I never clicked those to see where they lead.
BTW, if I see those I usually click the … button in their account and report it as spam and then block them. So hopefully someone at Twitter takes them down.
Yes not wonder why its so evil, 90% cybercriminals are devil worshippers anyways. no wonder they are so evil
What’s the fourth-least frequent first name on that chart?
It’s “Elena,” with the L in the cyrillic equivalent: л
Thanks!
I only got likes from twitterbots on my comments, so sad jajjaaj. Excelente investigación.
It’s easy for me to pick out spam. If an attractive woman wants to contact me, it’s spam, and she’s a ‘bot.
Just a small typo – Deniro Marketing is AS 19884 not 19984 (it’s wrong in the text, but not in the target URL)
When i created my Twitter account at least 3 bots like these follow me. I have block them because i knew it was some kind of fraud… The question is. How did they know when someone just signup on Twitter?
They know u horny, bruh!
Here are all the spam friendly employees of Deniro Marketing on Linked In: https://www.linkedin.com/search/results/people/?facetCurrentCompany=%5B%22804733%22%5D
The WhoIS matches with the individual in the LI employee listing.
I read this post on July 27th. The next morning I get a Twitter notice about a Like on my pinned tweet. I hover over the name and lo and behold, it exactly follows the format described in this post and the ZeroFOX blog. Sometime the Universe has impeccable timing.