Comcast, the nation’s largest residential Internet service provider, announced last week that it is expanding an initiative to contact customers whose PCs appear to be infected with a malicious bot program.
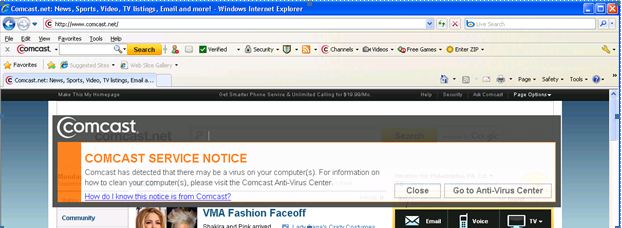
The Philadelphia-based cable Internet company is expanding nationwide a pilot program that began in Denver last year, which automatically informs affected customers with an e-mail urging them to visit the company’s security page. The system also sends the customer’s browser a so-called “service notice,” a semi-transparent banner that overlays a portion of whatever page is being displayed in the user’s Web browser.
Customers can then either move or close the alert, or click Go to Anti-Virus Center, for recommended next-steps, which for Windows customers includes:
- Downloading any missing Microsoft security updates.
- Making sure the customer has some kind of up-to-date anti-virus software running.
- Downloading and running Microsoft’s malicious software removal tool.
- Downloading and installing Secunia‘s free Personal Software Inspector tool, a program that periodically scans the user’s computer for missing security updates for commonly used third party applications, such as Adobe Reader, Flash, and Java, and QuickTime.
Comcast also is offering free subscriptions to Norton Security Suite for up to 7 computers per customer — including Mac versions of the Symantec suite.
For customers who receive a notice but are running a wireless router behind their cable modem, however, figuring out which computer is infected may not be so easy. That’s because while wireless routers plug directly into high-speed Internet modems — and allow multiple computers to use the same Internet address and connection — Comcast’s Constant Guard cannot isolate the infection beyond the Internet address assigned to the customer’s modem. Comcast users who have trouble with that are steered toward the option of paying for help from Norton Live.
Comcast spokesman Charlie Douglas declined to offer statistics on the number of customers who responded to alerts generated during the company’s pilot version of Constant Guard, but said the response has been “very positive.” He said customers who chose to ignore or close the service notice without taking action will be re-notified every few days until the problem is resolved.
Douglas said the bot intelligence is coming from Damballa, an Atlanta-based security company that monitors botnet activity and identifies botnet control networks. If Damballa spots a Comcast Internet address that is phoning home to one of these botnet command centers, Comcast’s system flags that customer’s address for a service notice.
“When we see instructions are being sent from that known evil [Internet address] to one of our customer addresses, we know the instructions from that address cannot be good and that there’s something not good happening on your network,” Douglas said.
Comcast has started rolling the system out on a market-by-market basis, and expects to have it deployed to most of its 16 million customers by the first quarter of 2011, Douglas said.





Phil:
This is NOT a case of big brother.
I think you need to check out the book Takedown written about Shimomura tracking down Kevin Mitnick. At one point he is looking at a huge volume of network traffic and that was in the early 1990s. He had to go through 2-3 ways to reduce the volume of network traffic examined before he could get any place. Now fast forward two decades. The amount of traffic of just one small city now probably vastly exceeds what a major hub like San Francisco had back then.
All Damballa will do is attempt to verify if packets are going and coming from known CC servers. That means it will look strictly at the IP addresses in the header and that is probably all it will have time to do for most packets. It is mostly automated and an attempt will be made to automate it even further to the point Comcast may not even know you were notified. At that point hopefully the detection that your machine is infected is correct and you can clean it up. Comcast will be happiest if that is done without one member of their staff looking at one single packet. If you have an FP you may be able to call Comcast and have them examine the traffic to / from your WAN IP but I doubt they will even do that. What happens if Comcast receives thousands of requests where people claim they are an FP? Comcast won’t have time to respond much less look into all of them. You have waits of 5-10 minutes now just to speak to somebody about your service as it is. So it will be shoved back on you again. If Comcast assumes you know what you are doing or that you really do have only all Macintoshes and Linux boxes, all with wired and no wireless connections possible they will attribute it to FPs with Damballa and the filteration will be tuned down to reduce the FPs until they are gone. The software itself may look into packets once they know they have a CC server packet but the first step is to eliminate the necessity of looking at all the packets that are not from CC servers.
Then they have to determine whether the packet from the CC server is a normal packet from the web server or a CC packet. The point is to reduce the amount of traffic you look at to a bare minimum. If you don’t do that you cannot succeed. If they try to go beyond that it will eventually collapse.
I told you before, this is not a case of big brother. Comcast has neither the time nor resources to look at any packets other than ones that IDS (Intrusion Detection Systems) IPS (Intrusion Prevention Systems) deem to be malicious that are headed towards THEIR servers. They want this new system just to look for CC packets that are headed towards your machine and CC requests sent from your machine. My wget to see if a ZBot config file is still at the CC server would be correctly identified that I may be infected. How can Damballa’s software distinguish between what your PC Windows machine did on its own and what I did deliberately? It is like looking for a needle in a hay-stack. Comcast are providing you with a tool like Damballa just to try to protect you. Your biggest problem will be the FPs, at least at the start. Hopefully that can be ironed out. But that exec at Microsoft that suggested this will work has had his eyes opened with such a major gaffe at the outset.
Disclaimer: I have nothing to do with Comcast other than being one of their customers.
Yes, I’m familiar with Takedown; I read it at the time. And I was very uneasy with some of the things that Stoll did. As a private individual he wasn’t subject to the restrictions that the Bill of Rights places on government agents, but if all of the computer laws now in place were in effect then he might well have run afoul of them himself.
You keep saying this isn’t Big Brother, but then you tell me that Comcast wants to examine the packets to and from my systems.
I fully understand that this is being done by machine, not by human eyes. We don’t have to have the philosophical discussion about whether a machine can violate someone’s privacy if no human ever sees what it sees. Assuming that only their machines see what I send or receive, I am still concerned that they might automatically decide, according to inscrutable rules known only to Comcast or their contractors, to block me from sending or receiving certain kinds of traffic or cut me off entirely. That’s unacceptable.
No ISP should have the power to block an Internet user from receiving any kind of traffic they wish to receive. And no ISP should have the power to block someone from sending any kind of traffic to a willing recipient.
That means I don’t have a problem with an ISP acting on the basis of recipient complaints (spam, harassment, etc), but I do have a very big problem with ISPs taking it on themselves to decide what constitutes objectionable traffic and blocking it absent a request by its intended recipient.
That request can be explicit (i.e., a complaint) or even implicit (e.g., a request to an ISP to block certain kinds of traffic on the user’s inbound stream). But again the key is that the recipient must always have ultimate control over what he does or doesn’t receive.
“I do have a very big problem with ISPs taking it on themselves to decide what constitutes objectionable traffic and blocking it absent a request by its intended recipient.”
And, coming back to the start of this discussion, I also have a very VERY big problem with ISPs modifying or spoofing traffic for which they are neither the sender nor destination.
If a packet wasn’t generated by one of their own computers, they have no right to control or change its contents. And if it’s not addressed to one of their own computers they have no right to even look at the contents, much less modify them or take any other action other than forwarding it to its intended recipient.
The only exception is when the intended recipient of a packet has given explicit permission to do so.
If an ISP sees a need to alert its customers, it has plenty of legitimate options. If none of them will work, we can devise a new protocol for the purpose. But modifying or spoofing traffic neither sourced by nor addressed to the ISP’s own computers is simply unacceptable.
Good discussion.
I disagree with some of the implications that are being used here.
Eveyone keeps saying that the “bot” or identified baddie , is out to get All of you. that somehow one persons computer is a threat to Yours.
while the Initial implementation of a security measures like this that might be a true statement , how technology like this will be applied will go WELL beyond that.
If you would like to argue that there are laws or humans that will stop this COMCAST BOT (yes IT is a Bot) from doing way more than protecting You from some lesser computer user who is infected, then you havent lived longer than 5 years.
while arguing For this great service of having a BOT tell you that a BOT is on your computer, and Call comcast and get a Phone BOT, you should also identify that your not willing for this to become More than it is now.
and you KNOW it will. just keep lying to yourself that it wont, in 5 years, MY statement will be valid, yours not.
For the people who are saying that a Zombie computer should be immediatly cut off from the web, That is a most curious and illogical “solution” to your computer being attacked by the zombies.
Thousands of Zombie infected computers USERS are on the web when NO virus protection crap could fix them or help them with thier issues.
many places on the web are now assisting users ON THE WEB, to disinfect thier computers when no software CAN even yet, because the virus is not yet in the update databases.
As “security” for the ISP they would love to just hack off all activity that doesnt meet thier criteria, look at the port closings, take a look at what has been done to whole countries via what some people IN that country have done.
As long as i am living in america, freedom and justice sometimes means you dont condemn everyone or everything just because a Freaking Computer tells you so.