Both Facebook and Yahoo! recently fixed security holes that let hackers hijack user accounts. Interestingly, access to methods for exploiting both of the flaws appears to have been sold by the same miscreant in the cybercrime underground.
According to Softpedia, Facebook has addressed a serious vulnerability after being notified by independent security researcher Sow Ching Shiong.
“The security hole allowed hackers to change the passwords of accounts they had compromised without knowing the old passwords. Whenever users change the password that protects their Facebook account, they’re required to enter the current password before they can set the new one. However, the expert found that cybercriminals could change a user’s password without knowing the old one by accessing the “https://www.facebook.com/hacked” URL, which automatically redirected to the compromised account recovery page.”
Information obtained by KrebsOnSecurity indicates that this “exploit” was being sold to a handful of members of an elite underground forum for $4,000 per buyer. The individual selling the exploit is the same hacker that I reported last year as selling access to a vulnerability in Yahoo! that let attackers hijack email accounts.
In late November 2012, I wrote about a cross-site scripting (XSS) vulnerability in Yahoo! that was being sold for $700 in the underground by an Egyptian hacker named TheHell. Shortly after that story, the hacker changed his nickname, but continued selling the exploit. Earlier this week, The Wall Street Journal‘s AllThingsD blog reported that Yahoo! had fixed the flaw I pictured in the video from that blog post.
“Web giant Yahoo just confirmed that it has been dealing with a vulnerability to its email service that may be connected to a surge in breaches of email accounts that are being used to send spam and other annoying content,” wrote Arik Hesseldahl. “I just got a statement from a Yahoo spokeswoman saying that the vulnerability seen in a video has been fixed.”



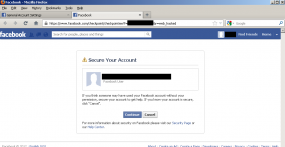

I got more information about the facebook bug
http://attack-secure.com/index.php/the-most-critical-flaw-in-facebook-worth-just-500-usd/
I’m still receiving a NoScript XSS warning when logging out of Yahoo mail. Maybe Hesseldahl is correct in conjecturing it might be a new problem and not that of Nov. 12
It appears to be still active, and NoScript appears to be successful at preventing the exploit. The XSS message — and apparently, the attack itself — can be prevented by tightening NoScript’s Yahoo permissions as described in this post at NoScript forum:
http://forums.informaction.com/viewtopic.php?p=46982#p46982