The previous two posts on this blog have featured stories about banks buying back credit and debit card accounts stolen in the Target hack and that ended up for sale on rescator[dot]la, a popular underground store. Today’s post looks a bit closer at open-source information on a possible real-life identity for the proprietor of that online fraud shop.
Rescator[dot]la is run by a miscreant who uses the nickname Rescator, and who is a top member of the Russian and English language crime forum Lampeduza[dot]la. He operates multiple online stores that sell stolen card data, including rescator[dot]la, kaddafi[dot]hk, octavian[dot]su and cheapdumps[dot]org. Rescator also maintains a presence on several other carding forums, most notably cpro[dot]su and vor[dot]cc.
![A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator's email flood service at the bottom.](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-pm-cpro-600x153.png)
A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator’s email flood service at the bottom; this will become important as you read on.
![Rescator, a.k.a. "Hel" a.k.a. "Helkern" the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.](https://krebsonsecurity.com/wp-content/uploads/2013/12/vor-1edited-600x414.png)
Rescator, a.k.a. “Hel” a.k.a. “Helkern” the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.
The only darklife member who matched that nickname was “Helkern,” one of darklife’s three founders. Darklife administrators were all young men who fancied themselves skilled hackers, and at one point the group hacked into the venerable and closely-guarded Russian hacking forum cih[dot]ms after guessing the password of an administrator there.
![Darklife admin "Helkern" brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.](https://krebsonsecurity.com/wp-content/uploads/2013/12/cihhacked-600x470.png)
Darklife admin “Helkern” brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.
And a self-portrait of Helkern:
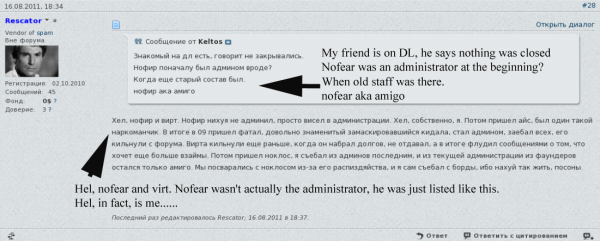
So if Helkern is Rescator, who is Helkern? If we check at some of the other Russian forums that Helkern was active in at the time that Darklife was online in 2008, we can see he was a fairly frequent contributor to the now-defunct Grabberz[dot]com; in this cached post, Helkern can be seen pasting an exploit he developed for a remote SQL injection vulnerability. In it, he claims ownership of the ICQ instant messenger address 261333.
In this introductions page from a Russian language gaming forum, a user named Helkern also was active in 2008 and claimed that same ICQ address. Helkern said his email address was root@helkern.net.ua, his Skype address was helkern_skype, and that he lived in Odessa, the third-largest city in Ukraine. Helkern — going by his shortened username “Hel,” also was a VIP member of xaker[dot]name. In this cached post we can see him again claiming the 261333 ICQ address, and pointing out to other members that his real nickname is Helkern.
A historic WHOIS lookup ordered from domaintools.com shows that helkern.net.ua was first registered in 2008 to an Andrey Hodirevski from Illichivsk, a city in the Odessa province of southwestern Ukraine.
I located a relatively recent Livejournal profile (ikaikki.livejournal.com/profile) for an Andrew Hodirevski from Odessa, Ukraine that includes several profile pictures which are remarkably similar to the photos of Helkern leaked by the cih[dot]ms guys. That profile (“ikaikki“) says Hodirevski’s email address is ikaikki@livejournal.com, that his Jabber instant message address is ikaikki@neko.im, and that his Twitter account is “purplexcite” (that Twitter has since been deleted). In almost a dozen posts on LiveJournal, Hodirevski talks about his interest in Java programming, and even includes a few pictures of himself attending an instructional class on Java.
The same anime profile image for Andrew’s LiveJournal page is also on the LinkedIn profile for an Andrew Hodirevski from Ukraine, and the two pages share the aforementioned Twitter profile (purplexcite). Andrew’s LinkedIn page also says he is the administrator and Web developer at a hosting company in Ukraine called ghost.ua.
That site is no longer online, but a cached copy of it at archive.org shows that the business is located in Odessa at this address, and the phone number +38 (048) 799-53-13. Ghost.ua lists several pricing plans for its servers, naming them after different despotic leaders, including Fidel Castro and Muammar Gaddafi (it is spelled “Kaddafi” on Ghost.ua). Recall as I mentioned at the top of this post that one of the clones of the card shop at Rescator[dot]la is kaddafi[dot]hk.
This page at it-portfolio.net lists an Andrey Hodirevski from Odessa with the same anime profile image, the “purplexcite” Twitter profile, and a Skype address by the same name. It says his professional skills include programming in Java, CakePHP and MySQL, among others. This Google groups discussion about CakePHP includes a message from an Andrey Hodirevski who uses the email address andrew@purpled.biz.
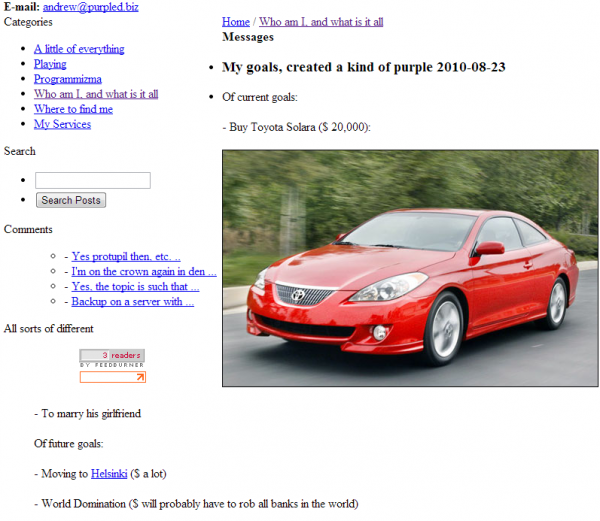
Purpled.biz is no longer online, but a cached copy of it from archive.org shows it was once Andrew’s personal site. Here we learned that Andrew’s current goals (as of 2010) were to get married to his girlfriend, buy the $20,000 Toyota Solara pictured below, move to Helsinki, and to achieve world domination. In order to accomplish the latter goal, Andrew jokes that he “will probably have to rob all the banks in the world.”
 After searching my huge personal archive of hacked cybercrime forums for Andrew’s various email and Jabber addresses, I found several private messages sent by different users on the Spamdot[dot]biz forum who recommended to other members the “ikaikki@neko.im” Jabber address as someone to contact in order to hire a service that could be used to flood someone’s Gmail inbox with tens or hundreds of thousands of junk messages. Recall that this Jabber address is the same one listed at Andrew’s LiveJournal profile.
After searching my huge personal archive of hacked cybercrime forums for Andrew’s various email and Jabber addresses, I found several private messages sent by different users on the Spamdot[dot]biz forum who recommended to other members the “ikaikki@neko.im” Jabber address as someone to contact in order to hire a service that could be used to flood someone’s Gmail inbox with tens or hundreds of thousands of junk messages. Recall that this Jabber address is the same one listed at Andrew’s LiveJournal profile.
To bring this full circle, one of the many services that Rescator sells these days is a popular email flooding service at rescator[dot]me. Turns out, Yours Truly has already been the direct target of an attack launched through Rescator’s service; I wrote about it in this July 2012 story, Cyberheist Smokescreen: Email, Phone, SMS Floods.
I have no idea if Rescator/Helkern/Andrew was involved in hacking Target, but it’s a good bet that he at least knows who was. I sought comment from various contact addresses listed above for this individual, and received a reply from someone at kaddafi[dot]me who said he knew Andrew and would relay my questions to him. Ultimately, he came back to me not with answers, but with a bribe not to run my story.(1:48:35 PM) krebs//: hi
(1:48:44 PM) krebs//: brian krebs here
(1:49:05 PM) krebs//: trying to reach rescator
(1:49:11 PM) krebs//: aka andrey
(1:51:12 PM) krebs//: don’t believe it’s really krebs?
(1:51:15 PM) krebs//: http://krebsonsecurity.com/wp-content/uploads/2013/12/kaddaficon.png
(1:53:32 PM) krebs//: 🙂
(1:53:53 PM) krebs//: tyt?
(2:00:14 PM) kaddafi.me: Hello Brian 🙂
(2:00:24 PM) kaddafi.me has not been authenticated yet. You should authenticate this buddy.
(2:00:24 PM) Unverified conversation with kaddafi.me/Muammar started. Your client is not logging this conversation.
(2:00:30 PM) kaddafi.me: ooo you’ve got OTR
(2:00:37 PM) kaddafi.me: Afraid of NSA? )
(2:01:38 PM) kaddafi.me: Why do you want to talk to Andrew?
(2:03:46 PM) krebs//: i am more afraid of others
[Image] (2:03:56 PM) The privacy status of the current conversation is now: Private
(2:04:11 PM) kaddafi.me: Yeah well you should after someone sent you drugs from silkroad.
(2:04:24 PM) krebs//: 🙂
(2:04:59 PM) krebs//: you’re right of course, it’s andrew 🙂
(2:05:17 PM) kaddafi.me: What’s all the commotion about Rescator anyways?
(2:05:20 PM) krebs//: well i have a story about him going up tomorrow
(2:05:23 PM) kaddafi.me: Did you even notice other shops are selling same shit?
(2:05:32 PM) krebs//: sure
(2:05:46 PM) krebs//: but I’m not looking at other shops right now
(2:06:05 PM) kaddafi.me: Well you should )
(2:06:10 PM) krebs//: in time 🙂
Kaddafi promised a response by 10 p.m. ET yesterday. This morning, not seeing a response, I pinged this individual again, and received the following response:
(10:08:46 AM) kaddafi.me: Hi.
(10:09:19 AM) kaddafi.me: You better contact me from another jabber that’s not associated with your name, I’ve got an offer for you.
(10:11:12 AM) krebs//: why from a different jabber?
(10:11:33 AM) kaddafi.me: Because I’ve got an offer for you. So you don’t think I’m trying to play games and fool around with logs after you read my offer.
(10:11:52 AM) krebs//: what kind of offer?
(10:12:27 AM) $10.000 not to post your article
Obviously, I did not take him up on his offer, assuming he was not just messing with me. Here is a mind map I put together (using MindNode Pro for Mac) that outlines how much of this information was derived and connected.






![The email flood service at rescator[dot]me](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-me-news-600x360.png)

wow, nice one Brian!
You are a serious hacker, stop acting like a whitehat..
thanks, but I can’t resist: one can’t be a serious hacker and be a whitehat at the same time? 🙂
Who’s the man? Brian Krebs is the man! I would love to enter your brain to see how you map all this out. 🙂
Nice work Brian! Keep up the great work!
Brilliant!!! you catch the predator!!! happy christmas and congratulations…
nice work, BK and +1 archive.org
You are amazing, Brian! I’m glad you’re on our side!
Brian, the feds are having problems catching these thieves for the very same reasons you outline.
Apparently there is an extensive network, and that is what they want.
Talk about creating a web. They are creating webs all over internet to confuse any authority trying to hunt them down.
They open and close shop so fast there is no trace left to find them. However, they are going to slip up.
One day the authorities will catch them. Many people are struggling at the worst time of year.
How can you lose money when you hardly have money?
You should have taken the money, and donated them to the ones in need, the ones affected by this breach or me. That’s a lesson learned Brian.
Your response, Malcolm, suggests you don’t really understand how these guys work. Absolutely nothing can be gained from someone in my position accepting money from these guys, no matter what my intentions are in connection with such an idea.
Accepting stolen funds and donating them to charity is not legal, nor is it good karma. Also, by donating stolen money to charity, you unwittingly embroil yet another innocent party in criminal activity.
What’s more, all bribes are an invitation to expose the accepter to accusations of the same type of avarice and injustice that fueled the bribe in the first place. Bribery is harmless when it is offered, but potentially very damaging and irreversibly so if accepted, regardless of the rationale.
Plus a 4 billion dollar breach payoff of 10k, jeez, at least a billion cmon….
Are new comments being moderated in this post? I’ve tried to post some additional data I dug up on this guy (nothing earth shattering) but it appears as if my posts just disappear after I submit them….
I’ll check. My guess is you pasted a lot of links, in which case your comment will get auto-flagged as spam.
While I am not saying this is the case, if somebody were going to write a lot of horrible accusations about someone and attach your name and pictures to it, especially if you were innocent and you knew it was going to tarnish your reputation, how would you go about refuting it?
From what I’ve seen it’s difficult to prove a negative without providing the positive identification of the “actual” person.
This is a serious question, not a jab: How could or should one refute or prevent being “doxed” in this manner? Have you made mistakes before and caught them before you published? Again this is not meant as an insult. I am genuinely curious what the proper approach would be (clearly one can rule out offering you money :)). Thank you.
Outstanding work, Brian!
Now can you get him to share his source? Or at least the sales thur far?
Heres a bit more I dug up, nothing real interesting, other than he likes Xbox, knows about SEO, and wants to be a bodyguard
SEO Forum Profile:
hxxp://www[dot]maultalk[dot]com/user19441[dot]html
Xbox Forum:
hxxp://xbox360games[dot]com[dot]ua/forum/search[dot]php?keywords=&terms=all&author=purple&sc=1&sf=all&sk=t&sd=d&sr=posts&st=0&ch=300&t=0&submit=Поиск
hxxp://www[dot]xboxland[dot]net/forum/user/48875-purple/
Other:
hxxp://a404[dot]ru/profile/purple/
What appears to be his old personal blog on becoming a bodyguard, although its not a fun experience to navigate an archive[dot]org page through google translate, so I didnt look around too much, but the site shop2sms[dot]net is linked from all his profiles in the above (although those dont have recent activity on them)
Just some extra fun! (sorry if this is a double post, the first time I posted it nothing showed up for me in the comments)
Bravo Brian! One plus vote for integrity.
Thank you for not accepting dirty money from these crooks. They don’t deserve anything but lots of prison time for what they have done/are doing.
Merry Christmas!
The guy says “why aren’t you exposing the other sites?” The answer to that question is, they offered a lot more than 10k.
Good reply! Dangit, why didn’t I think of that?
It was way too easy to deanon Andrew. Everything points to the fact that this gentleman is simply a script kiddie. He is unlikely to have been involved in the Target incident directly, he is merely selling the goods. It is plausibly that he received the dumps anonymously. But please do carry on, Brian!
Given the seeming joke of an effort of to hide oneself of many other criminals featured on this this blog I think your assessment is BS.
I was on a conference call with MasterCard yesterday for a briefing of the Target breach. They mentioned that the forensic investigation is still taking place. Has anyone from that investigation contacted you for advice/assistance? It appears that you have dug up valuable intel. At the very least you are on the right crumb trail that will lead to the responsible parties.
Question is, even if you find the right parties will they be able to do much when the suspects are in countries that look the other way? They can always nab them if they travel or something but what are the chances of the crooked russian government actually going to arrest the guy?
I would just want to salute your courage and extend utmost respect…
Oh, and excellent job on this fantastic investigative work, Brian. I feel the term blog falls woefully short of the work you are doing.
You missed this interesting bit from his livejournal: http://ikaikki.livejournal.com/795.html
“Но если и ехать туда — то как минимум через ~2 месяца, потому что сейчас под подпиской о невыезде”
March 25th, 2011
So it means he was under “recognisance not to leave” (don’t know an english equivalent, it’s http://ru.wikipedia.org/wiki/%D0%9F%D0%BE%D0%B4%D0%BF%D0%B8%D1%81%D0%BA%D0%B0_%D0%BE_%D0%BD%D0%B5%D0%B2%D1%8B%D0%B5%D0%B7%D0%B4%D0%B5_%D0%B8_%D0%BD%D0%B0%D0%B4%D0%BB%D0%B5%D0%B6%D0%B0%D1%89%D0%B5%D0%BC_%D0%BF%D0%BE%D0%B2%D0%B5%D0%B4%D0%B5%D0%BD%D0%B8%D0%B8), i.e. was convicted for something
Out of curiosity Brian, and maybe I missed something in the write up, but how did you get from 1 to 2 in this image:
https://i.imgur.com/9sEJ5SC.png
Just simply trying to understand the article better.
“In an Aug. 2011 thread that has since been deleted, Rescator introduced himself to the existing members of vor[dot]cc, a fairly exclusive Russian carding forum. When new members join a carding community, it is customary for them to explain their expertise and list previous nicknames and forums on which they have established reputations.
In this particular thread, pictured in the screenshot above, we can see Rescator listing his bona fides and telling others he was “Hel,” one of three founders of darklife[dot]ws, a now-defunct hacker forum.
In this particular thread, pictured in the screenshot above, we can see Rescator listing his bona fides and telling others he was “Hel,” one of three founders of darklife[dot]ws, a now-defunct hacker forum.
The only darklife member who matched that nickname was “Helkern,” one of darklife’s three founders. Darklife administrators were all young men who fancied themselves skilled hackers, and at one point the group hacked into the venerable and closely-guarded Russian hacking forum cih[dot]ms after guessing the password of an administrator there.
“A historic WHOIS lookup ordered from domaintools.com shows that helkern.net.ua was first registered in 2008 to an Andrey Hodirevski from Illichivsk, a city in the Odessa province of southwestern Ukraine.”
So those russian characters by the first label descr: must translate to Andrey Hodirevski, which probably can also mean Andew Hodirevski.
Notice … on the back passenger door of the (Russian?) jeep, in white, what appears to be a “s w a s t i k a” … also appears to be on the front fender (although not as defined).
Can’t make make out the lettering on the rear passenger door below the two symbols … anybody?
Do I also recall correctly that he had termed this ‘sales’ activity (of CC info) “Operation Barbarossa”?
.
Yes BARBAROSSA is the name of one of the subsequent CC bases, Tourtuga was the initial one, which based on the carder forums I have been reading, these are the best bases to come along in a long time…
I dont know that id make much of the swastika….Could easily have been a picture taken in a random place and the jeep had been vandalized by others. Not even sure what the implication would be….hes not selling card data out of racial / ethnic motives.
Great reporting, Brian.
If anyone is curious as to why Target’s IT infrastructure was lacking, I suggest going to their jobs website (below) and searching for “technical&architect”. You will see 34 jobs, most of which are located in Karnataka, Bangalore, India. Outsourcing has a price.
http://targetcareers.target.com/search/
And yet even if the company goes bankrupt, the CEOs and executives who decided to go cheap or outsource, who decided to sell or not protect customer information will still float away on golden parachutes, set for life and uncaring about the concerns of the peasant class. I just watched ‘Ethos’ and it raises a lot of valid points.. Every major company in America these days has one and only one legal concern – make as much money as possible as fast as possible, which means cutting corners wherever possible as often as possible. Which also means incidents like this are going to happen again and often, regardless of the outcome.
Yes that is the reason why corporations are successful and you’re goddam right they should make as much money as fast as possible. What is your problem?
If unfettered capitalism is your god, then move to China, or better yet, Somalia, the libertarian paradise. No pesky government there.
And since you must have slept through Economics 101, I will explain it to you. Outsourced workers do not buy large-ticket appliances, new cars, or homes. This is a major reason why our economy has not started working again.
Research how Henry Ford paid his employees double the regular wage so they could buy his cars.
Like he says, there is an overall system and when you foster corruption and greed you get what we have now – recessions, poverty, sloppy practices that hurt everybody. Walmart makes billions a year in profits, right now most of that goes to 5 people while half their workers are propped up by the tax payers. What really changes about ‘capitalism’ if we the people say no and that profit goes to 10 million more workers who will actually use it? Go read up on your Adam Smith, he actually talks about it and what we have now is definitely not anything he would think is ANYWHERE close to ideal… We have corporatism plain and simple, with skewed tax breaks, monopolies, barriers of entry, and usury that destroys anything close to a level playing field. This breach wasn’t an accident, it was a planned risk that triggered because the executives decided to pocket the cost of hiring a few good and well trained researchers and devices that could have made all the difference.
There appears to be a swastika, a star, and the Russian word for peace (мир) spray-painted on the side of the military 4WD. It has not been driven in a while; note the leaves under it and the flat tire.
Why would anyone take a selfie in a lavatory?
S w a s t i k a, white star, and below them Мир which is Russian for either. “World” or “peace”.
Thank you Mike and PC. There is also something on the front door too (can see white from the concave structure of the door) when zooming into the image using other tools), and symbols on the hood as well. Looks like a heavily laden with paint paintbrush (versus say, spray paint) might have been used (notice the ‘dropped’ paint from perhaps a brush or paint-laden stick or piece of house baseboard trim or 1″ or so wide molding). A zoomed-in image and enhanced contrast/brightness adjust helps in seeing this artifacts/items.
CJD – Not sure what the implications are either; these are just observations at this point.
.
Yes, of course, but when was the last time you saw graffiti of “World” as compared to “Peace”?
And we know that the graffiti was left sometime after the Revolution because otherwise it would be миръ (from War and peace — Война и миръ). 🙂
Lots of people take selfies in the bathroom if their arms are short and they don’t have a better mirror. I suspect it means that at least at the time, he wasn’t living in a household with a woman in it, though 😉
I suspect Target is one of many targets this Holiday Season.
Good old Cash might make a return.
Krebs – You should have your own show in the style of CBS “48 Hours”
Good job Brian! A bit of shame for the city where I was born, but black sheep is a black sheep.
Here is one more piece of info which I found. Apparently guy was working for company called netpeak[dot]ua (SEO) and here is archived blog entry where you can see his picture with text saying Andrey Hodirevski AKA hel
http://archive-ua.com/page/126147/2012-07-15/http://netpeak.ua/blog/ne-sekretnii-insaid/
Great find, Cyberman. Going to grab some screen shots of that and update the story once some of it has been properly translated. He’s even wearing the same hoodie sweatshirt as in the other pictures already up on this site.
Brian,
This is absolutely stunning that you are not for sale it shows a good personality! I admirer the way you work and enjoy reading your posts and aspecialy learn from it!
Greetings from Holland
Holy #### we need to bring back the T.V. show Dragnet and have Kebs , do the part of Sergeant Friday working for the Bunco squad .
Dragnet Online 2014 (drama/crime) Fall 2014
Episode #1 ” “Grand credit Theft Bunco.” Plot: Sergeant Friday (Brian Krebs) goes online searching the Russian underground forums to investigate a recent major credit cards theft of a major retail store.
If anyone is interested in solving a current WhoDunnit there’s lots of dots we’d love to be able to connect over at:
http://www.amazon.com/gp/help/customer/forums/ref=cm_cd_pg_pg1?ie=UTF8&cdForum=Fx2NFGOONPZEXIP&cdPage=1&cdThread=Tx2EME4IL59BUP4
The common denominator is fraudulent charges of $9.84 (most if not all originating in London) showing up on lots of credit cards…similar websites claiming to sell online “educational” content…a hand full of similar “customer service” telephone numbers…a hand full of similar IP addresses…ETC.
Good to know these guys follow you as well, he knew about the drug ‘gift’. He’s really a fan, just didn’t admit it. You must track site logs to follow your ‘fans’…
Always enjoy your posts. Thanks!
Their is also listings for Andrey Hodirevski , or Andriy Hodirevski in Odessa Ukraine doing a deep web search
You are using Windows XP? Probably a VM, but really?
Wow..busted.
Brian = Sherlock Holmes of the Net!