I was fortunate to spend several hours this past week with two reporters whose work I admire. Both wanted to learn more about my job as an independent investigative reporter. Their stories about my story are below.
 Mark Stencel, a former colleague at Washingtonpost.com who similarly worked his way up from an entry-level job at the publication, wanted to hear about the challenges and rewards of going solo. Stencel’s piece, Reporter Brian Krebs Hacks it on His Own, One Scoop at a time, was written for poynter.org, an online publication for and about journalists.
Mark Stencel, a former colleague at Washingtonpost.com who similarly worked his way up from an entry-level job at the publication, wanted to hear about the challenges and rewards of going solo. Stencel’s piece, Reporter Brian Krebs Hacks it on His Own, One Scoop at a time, was written for poynter.org, an online publication for and about journalists.
Stencel writes:
“All of this reporting pays off with loyal readers, even at companies who fear finding themselves covered on his site. “As someone who does payment card security for a brick and mortar retailer, ‘Brian Krebs’ is a name I never ever want to see flash across my Caller ID,” one admirer wrote in a recent reader comment.”
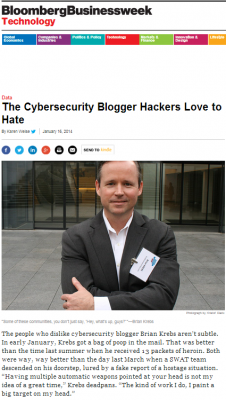
Separately, I spent half a day with with Business Week reporter Karen Weise, whose profile, The Cybersecurity Blogger Hackers Love to Hate, appears in this coming week’s print edition. Weise observes:
“Krebs’s talent for exposing the weaknesses in online security has earned him respect in the IT business and loathing among cybercriminals. His track record of scoops, including the Dec. 18 revelation that hackers stole tens of millions of customers’ financial data from Target (TGT), has helped him become the rare blogger who supports himself on the strength of his reputation for hard-nosed reporting.”
My favorite part of both these stories are the observations from readers. For instance, Weise quoted Lance James, head of intelligence at Deloitte, with whom I co-presented last year at the Black Hat conference in Las Vegas.
“No intelligence agency could get as much as Brian Krebs does,” BW quotes James as saying. “Everybody wants to share with him.”
Fortunately, that’s very true: Key information that informs some of my best scoops is just as likely to come from people actively engaged in cybercrime as it is industry experts working to fight fraud. So, once again, a sincere thank you to all of my readers — lovers and haters alike.




I enjoy your posts – keep it coming!
Favorite part of the BusinessWeek story:
“Since he broke the Target story, about 100 readers have donated anywhere from a few dollars to several hundred via PayPal (EBAY) or Bitcoin.”
It’s truly awesome when readers are so moved by your work that they actually want to contribute financially. Congratulations!
BRIAN KREBS IS GOD. FULL STOP.
Always impressed with your work, Mr. Krebs. As someone in the banking industry, I thank you for your tireless efforts.
Brian, Brian, you are leaving your non-native speakers behind using such titles. I had to go to “Urban Dictionary” to see what you meant with “Gumshoe”.
Next to that congratulation for the well-deserved recognition.
I came to your site in February or March 2010 and never left since.
But George, think of all the idioms you have picked up along the way!
Not to mention taking to wearing onions on his belt, as was the style of the time.
Hi,
First of all congrats for kerbs for its fascinating reporting. It made my day many times.
it seems that intercrawler is reporting that they had uncovered author of blackpos. It is the.malicious code behind target attack. Someone named ree4/ Sergey Taraspov.
Brian can you please update us on this?
Looking forward for your post.
Keep the stories coming 😛
Looking forward to your talk at RSA.
Brian ’s Upcoming Sessions Gumshoes – Security Investigative Journalists Speak Out USA 2014 February 26, 2014 | 9:20am – 10:20am | West | Room: 3014 – See more at: http://www.rsaconference.com/speakers/brian-krebs#sthash.RRI65ZCt.dpuf
Keep up the awesome journalism, looking forward to the book as well.
Congrats Brian, it is well deserved. Your blog is a very helpful resource for me.
Two Mexican citizens were arrested at the Texas/Mexico border with 96 fraudulent credit cards. The Secret Service confirmed that the fraudulent accounts traced back to the original Target data breach in Dec. 2013.
http://www.chron.com/news/texas/article/2-nabbed-at-Texas-border-in-credit-card-fraud-case-5159281.php?cmpid=hpbn
Most importnat things in life are Family, Happiness, Commitment, Safety and Security. In Brian’s case, add in a few more, such as good connections ( aka “informants”), good connections (internet DoS survivability) and up to date tools to keep what you own safe.
One should never forget where you came from. Many people have helped each other to the path of success. Remember this because one day you will probably step off the path and onto a retreat. Let some other “whipper-snapper” pick up, but not mimic that same path.
Brian enjoys that sort of thing more than heroin. Doesn’t even matter that Bloomberg recently threw their top guy in China under the bus to appease the commies.
I a TED cynic, so Brian, I hope not to see you there. The problem with TED is that the presentations are more about being slick and motivational than educational or informative. To me, that really doesn’t fit with the sort of day to day hassle of good security practices. On the other hand, TED has a huge audience. A dilemma of association with a questionable format vs the opportunity of reaching a large audience.
Which leads me to the more interesting question: You obviously deal with criminals as news sources. How do you decide where to draw the line in terms of what you will offer criminals vs. what they want you to publish?
Most recently with the Target breach, you: ” identified a Ukrainian man [you’d] determined was selling the stolen data. In an online chat that Krebs later posted, the man offered him $10,000 to back off. Krebs declined and ran the story.” Of course thats a hot item, an interview with a central figure in a major crime. But where to you draw the line between ethical journalism, promoting criminal egos, and maybe impeding prosecution?
The question is somewhat rhetorical, but perhaps you can work it in to a future post.