When a retailer’s credit card systems get breached by hackers, banks usually can tell which merchant got hacked soon after those card accounts become available for purchase at underground cybercrime shops. But when companies that collect and sell sensitive consumer data get hacked or are tricked into giving that information to identity thieves, there is no easy way to tell who leaked the data when it ends up for sale in the black market. In this post, we’ll examine one idea to hold consumer data brokers more accountable.
 Some of the biggest retail credit card breaches of the past year — including the break-ins at Target and Home Depot — were detected by banks well before news of the incidents went public. When cards stolen from those merchants go up for sale on underground cybercrime shops, the banks often can figure out which merchant got hacked by acquiring a handful of their cards and analyzing the customer purchase history of those accounts. The merchant that is common to all stolen cards across a given transaction period is usually the breached retailer.
Some of the biggest retail credit card breaches of the past year — including the break-ins at Target and Home Depot — were detected by banks well before news of the incidents went public. When cards stolen from those merchants go up for sale on underground cybercrime shops, the banks often can figure out which merchant got hacked by acquiring a handful of their cards and analyzing the customer purchase history of those accounts. The merchant that is common to all stolen cards across a given transaction period is usually the breached retailer.
Sadly, this process of working backwards from stolen data to breach victim generally does not work in the case of breached data brokers that trade in Social Security information and other data, because too often there are no unique markers in the consumer data that would indicate from where the information was obtained.
Even in the handful of cases where underground crime shops selling consumer personal data have included data points in the records they sell that would permit that source analysis, it has taken years’ worth of very imaginative investigation by law enforcement to determine which data brokers were at fault. In Nov. 2011, I wrote about an identity theft service called Superget[dot]info, noting that “each purchasable record contains a two- to three-letter “sourceid,” which may provide clues as to the source of this identity information.”
Unfortunately, the world didn’t learn the source of that ID theft service’s data until 2013, a year after U.S. Secret Service agents arrested the site’s proprietor — a 24-year-old from Vietnam who was posing as a private investigator based in the United States. Only then were investigators able to determine that the source ID data matched information being sold by a subsidiary of big-three credit bureau Experian (among other data brokers that were selling to the ID theft service). But federal agents made that connection only after an elaborate investigation that lured the proprietor of that shop out of Vietnam and into a U.S. territory.
Meanwhile, during the more than six years that this service was in operation, Superget.info attracted more than 1,300 customers who paid at least $1.9 million to look up Social Security numbers, dates of birth, addresses, previous addresses, email addresses and other sensitive information on consumers, much of it used for new account fraud and tax return fraud.
Investigators got a lucky break in determining the source of another ID theft service that was busted up and has since changed its name (more on that in a moment). That service — known as “ssndob[dot]ru” — was the service used by exposed[dot]su, a site that proudly displayed the Social Security, date of birth, address history and other information on dozens of Hollywood celebrities, as well as public officials such as First Lady Michelle Obama, then FBI Director Robert Mueller, and CIA Director John Brennan.
As I explained in a 2013 exclusive, civilian fraud investigators working with law enforcement gained access to the back-end server that was being used to handle customer requests for consumer information. That database showed that the site’s 1,300 customers had spent hundreds of thousands of dollars looking up SSNs, birthdays, drivers license records, and obtaining unauthorized credit and background reports on more than four million Americans.
Although four million consumer records may seem like a big number, that figure did not represent the total number of consumer records available through ssndob[dot]ru. Rather, four million was merely the number of consumer records that the service’s customers had paid the service to look up. In short, it appeared that the ID theft service was drawing on active customer accounts inside of major consumer data brokers.
Investigators working on that case later determined that the same crooks who were running ssndob[dot]ru also were operating a small, custom botnet of hacked computers inside of several major data brokers, including LexisNexis, Dun & Bradstreet, and Kroll. All three companies acknowledged infections from the botnet, but shared little else about the incidents.
Despite their apparent role in facilitating (albeit unknowingly) these ID theft services, to my knowledge the data brokers involved have never been held publicly accountable in any court of law or by Congress.
CURRENT ID THEFT SERVICES
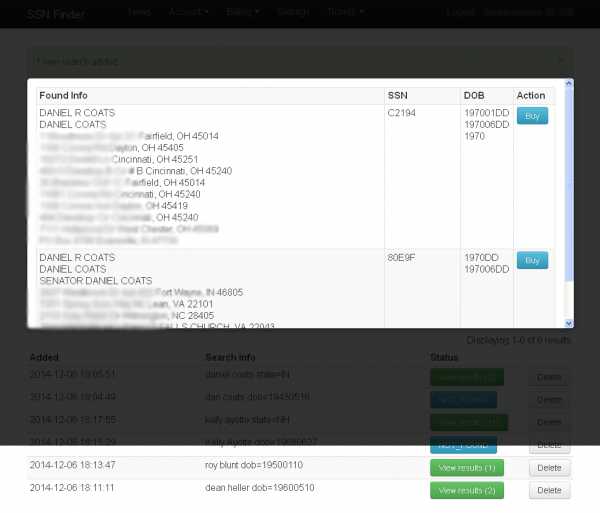
At present, there are multiple shops in the cybercrime underground that sell everything one would need to steal someone’s identity in the United States or apply for new lines of credit in their name — including Social Security numbers, addresses, previous addresses, phone numbers, dates of birth, and in some cases full credit history. The price of this information is shockingly low — about $3 to $5 per record.
KrebsOnSecurity conducted an exhaustive review of consumer data on sale at some of the most popular underground cybercrime sites. The results show that personal information on some of the most powerful Americans remains available for just a few dollars. And of course, if one can purchase this information on these folks, one can buy it on just about anyone in the United States today.
As an experiment, this author checked two of the most popular ID theft services in the underground for the availability of Social Security numbers, phone numbers, addresses and previous addresses on all members of the Senate Commerce Committee‘s Subcommittee on Consumer Protection, Product Safety and Insurance. That data is currently on sale for all thirteen Democrat and Republican lawmakers on the panel.
Between these two ID theft services, the same personal information was for sale on Edith Ramirez and Richard Cordray, the heads of the Federal Trade Commission (FTC) and the Consumer Financial Protection Bureau (CFPB), respectively.
Getting these ID theft service Web sites shut down might feel good, but it is not a long-term solution. Both services used to conduct these lookups of the public figures mentioned above are second- and third-generation shops that have re-emerged from previous takedown efforts. In fact, at least one of them appears to be a reincarnation of ssndob[dot]ru, while the other seems little more than a reseller of that service.
Rather, it seems clear that what we need is more active oversight of the data broker industry, and new tools to help law enforcement (and independent investigators) determine the source of data being resold by these identity theft services.
Specifically, if there were a way for federal investigators to add “breach canaries” — unique, dummy identities — to records maintained by the top data brokers, it could make it far easier to tell which broker is leaking consumer data either through breaches or hacked/fraudulent accounts.
Data brokers like Experian have strongly resisted calls from regulators for greater transparency in their operations and in the data that they hold about consumers. When the FTC recommended the creation of a central website where data brokers would be listed — with links to these companies, their privacy policies and also choice options, giving consumers the capability to review/amend the data that companies maintain — Experian lobbied against the idea, charging that it would “have the unintended effect of confusing consumers and eroding trust in e-commerce.”
The company’s main sticking point was essentially that it was unfair to impose such requirements on the bigger data brokers and ignore the rest. Experian’s chief lobbyist Tony Hadley has made the argument that there are just too many companies that have and share all this consumer data, which seems precisely the problem.
“The Direct Marketing Association (DMA) estimates that even a narrow definition of a marketing information service provider is likely to include more than 2,500 companies from all sectors of the economy,” Hadley wrote in a blog post earlier this year. “Simply put, the entire data industry – extremely vital to the US economy — cannot be neatly or accurately identified and then subjected to unrealistic requirements.”
My guess is that if the data broker giants are opposed to the idea of inserting dummy identities into their records to act as breach canaries, it is because such a practice could expose data-sharing relationships and record-keeping practices that these companies would rather not see the light of day. But barring any creative ideas to help investigators quickly learn the source of data being sold by identity theft services online, data brokers will remain free to facilitate and even profit from an illicit market for sensitive consumer information.




What needs to happen is that Visa needs to open source CAMS (compromised account management system), and let 10 or 20 other companies who want to put the resources into finding fraud find it faster and easier.
This of course, will never happen. Then again, I said that about EMV 10 years ago.
Great report as usual. But wish you’d get your site responsive so I could read it on my phone. PM if you need help with a better responsive theme.
That might be a ‘your phone’ issue – just read and typing this response on a Galaxy Note 2 using Chrome browser, works an absolute treat
He said a phone!
The web site doesn’t work on my Western Electric Model 500 either.
>wish you’d get your site responsive so I could read it on my phone
Works fine on my iPhone 4s / Safari
My phone is Samsung Galaxy S3. I have to zoom and rotate to read this site. Other responsive sites work OK.
Stop trying to read material in 2014, with a phone from 2011.
I am afraid that although a real clever idea, I don’t think its going to work.
If the canary data is “special” (that is, not traded among other brokers), who’s to say its going to be searchable like other pieces of data, so it wouldn’t necessarily sing.
But if the canary is just a normal set of records, the amount of data trading between brokers will make it impossible to tell the source of the leak, because any single canary might breed massively, and find itself in every major database.
Also, the invesitgators do have such canaries if they want: Simply do a search on someone pretty obscure and unique, and demand information from the brokers on who looked that up about the time they do their query, since these services are not downloading the brokers’ databases. Yet the same problem will exist: the investigators may know but do nothing.
I’ve actually mentioned and to be honest kind of hope exactly this happens, even if spread by criminals it would bring about necessary changes to these quasi-legal entities that suck up everything they can without any way to purge or control it. Having a few billion false positives in their treasure trove of stolen data might be exactly the right amount of poison to cure the illness.
Brilliant idea. If a merchant gets breached and credit cards are stolen, The thieves are limited to the cards used at that merchant. If a company that has access to all our Information (data brokers) is compromised then we ALL are exposed. One breached data broker is too many and is more harmful to consumers than 25 breached merchants losing credit cards. You can always get a new credit card but you can’t get a new birthday etc.
Sounds like we need to move the public dialog from “too big to fail” to a robust discussion of “Too Big to Breach”.
So multiple websites sell all of our personal information to include dob and ssn for $5 or less…why again are we so collectively obsessed with people hacking and selling bank issued credit cards when this is so clearly 100x more harmful to consumers? It’s time for the government to more meaningfully regulate these brokers who profit off of selling our information.
Yes, Ed…er…Lance, that’s exactly right. While I’ve been happy to have my site be the recipient of traffic from all the breaking stories, it’s been bittersweet, and I’ve been trying to steer the conversation toward this topic whenever possible.
This is a crucial point that NEVER gets discussed. A big reason why it’s never talked about is specificly due to the money being made via “online advertising”. Too many websites (and the people that run them) seem to feel it’s not only their ‘right’ but also their responsibility to collect any and all information about you that they can. This includes SS#’s. So often, if you read the fine print on things (like EULA’s), you’ll find that social security numbers and drivers license numbers and NOT seen as private data at all. Such a big part of the problem is that so many people collect this data in the first place. People don’t seem to mind though; but want to complain when bad things happen.
Because they are not regulated fixing errors is also not really their priority and often impossible. There have been numerous reports on this where any and all disputes get routed to some foreign country where someone gets a few cents an hour to reject as many as they can.
Agree +1 with Lance!
You already have your answer, the big Data Brokers lobby against any real change. Until that is changed… nothing will change.
The problem with canaries will be several fold. With the way the brokers share data ( intentionally or unintentionally ) will cause canaries to quickly lose value. You could have a way to filtering canaries, but then the filter itself becomes very valuable. Know the canaries and you have a significant advantage over the competition. I think canaries also presume that they are all not involved in the leaking of data to criminal enterprises.
Rather than trust the canaries to the foxes, why doesn’t the SS/FBI just create them? Create fake people and fake lives ( they do have the power ) get CC’s and use them as models for various “normal” activities? Seems like a much more powerful tool than trusting the data brokers not to screw this up. With detailed records it should be trivial to identify breach patterns as they are happening.
But cry me a frigging river, if your business is enabling crooks expect regulations to be knocking at your door.
Hi Brian,
Another fantastic article, I have more of a tactical question. What advice do you have for someone who wants to determine if their information is being sold on one of these websites?
Short answer…all our information is being sold. Freeze your credit at all 3 bureaus.
Your information is being sold. It’s being sold mostly to credit card companies who do bulk information requests before sending out those “You’ve already been approved!” offers. It’s being sold in great big lots with millions of other people’s data to marketers, banks, and political action groups (among others). Fraudsters pose as one of the “legitimate” users of this kind of info and buy up huge lots of data same as anybody else. Whether or not your data has been sold to one of them is basically a crap shoot at this point, but your data has been sold, and is currently being sold to somebody.
Just assume it’s being sold, because it very likely is. And if it hasn’t been yet, it will be, so just get ready for it.
If these underground sites that are reselling information they’ve gleaned from access to several databases belonging to the “professional” data brokers, couldn’t they simply eliminate canary data from their results? Selling this data could lead to an investigation that would discover their illegitimate access to the data, so they could reduce their risk of that happening by doing some cross-referencing using their multiple sources to eliminate any records that are likely “canary” data. This assumes they are cognizant of such techniques and recognize them as a potential risk to their data sources, which might not be the case.
Great article
I’ve alway wondered who died and made outfits like Experian untouchable.
Brian, say you didn’t kill that little birdie!
Well done on a great article Brian! There are certainly several important concepts in this piece.
The sentence that caught my attention most was: “In short, it appeared that the ID theft service was drawing on active customer accounts inside of major consumer data brokers”.
You write that there were botnets inside “several major data brokers, including LexisNexis, Dun & Bradstreet, and Kroll”. I’m intrigued as to why these are described as “botnets” rather than APTs. Do you have any additional information to elaborate on this?
Yes.
http://krebsonsecurity.com/2013/09/data-broker-giants-hacked-by-id-theft-service/
Yest those same data brokers are all to wiling to put canaries into their data to track misuse that harms their sales directly – that goes all the way back to the time that we started buying adress listings for mailings. These contained fake addresses, so that the vendor could see how often you used them…
Hi Brian
Just a crazy idea i had: How about we exterminate all of those data brokers?
No more data brokers, no more selling of PII?
What harm to the consumer does that do?
I dutifully create a new email address for every vendor I establish a relationship/retaliationship with.
That way I can tell who has lost or has been selling my email address.
This is probably not practical for everyone to do, but thought I’d mention it. It’s practical for me, as I run my own email server.
Of course, when confronted, the losers/sellers of my email address denied having lost or sold my info.
Any multi-state corporation names we should be aware of? Say, has Wells Fargo or BofA sold you out? Do tell.
Those of us without our own mail servers can do this sometimes, too. For sites that allow it, I create a unique e-mail address using plus-addressing (e.g. username+somethingunique@gmail.com). From the spam I receive via those addresses, I can tell that there have been breaches at Washingtonian.com, GoodNiteLight.com, Takeout Taxi, and WAMU.org.
A lot of sites defeat this by rejecting any e-mail address that contains a plus sign, based usually on the misguided belief that valid e-mail addresses don’t contain plus signs.
>> I dutifully create a new email address for every vendor I establish a
>> relationship with. That way I can tell who has lost or has been
>> selling my email address.
I also have my own eMail server and do exactly the same thing for the same reason. It would be nice if the major eMail players allowed you to do the same. (Note: I have not gone looking for such capability.) I do two things differently, tho. I add a few random characters which I can later change if the address is compromised but still keep a special address for that recipient. I also have aliases for each of my personal recipients since they get hacked all the time.
These sites have 1. Name 2. Dob 3. SSN 4. Address 5. Previous addresses. They don’t typically have email addresses, mothers maiden names, account info…that’s called fulls or fullz. That’s not what this story is about.
They don’t sell the email accounts of 200M Americans and most bad guys who commit identity fraud don’t necessarily care about email addresses unless they have the accompanying PW. Therefore, while it might be fun to see who is trading with your information , you are doing precious little to help identify the source of the PII.
I’ve also been doing this for years (15 to be exact). I recall the first “big” one was AmeriTrade. I called to complained and they denied any problems around late 2004. I said, “Look, no one could possibly know my email address because it has your name in it and the year/month/day that I opened the account.” Then they suggested my system was possibly hacked (doubtful, Linx on the Desktop since 1999, iptables, ipsec, tripwire, etc.). AmeriTrade was warned by me and no others (I recall when the story broke, many others online talked of the same issue and the same non-response by Ameritrade), but they ignored it until sued in 2008.
http://www.wired.com/2008/07/ameritrade-hack/
Oh and before that they lost unencrypted backup tapes.
http://www.nbcnews.com/id/7561268/ns/technology_and_science-security/t/ameritrade-warns-clients-lost-data/
I was a customer prior to 2005, so I’ve always wondered how my data was lost – via these backup tapes, or more likely an online breach.
Maybe what we need to do is move towards a system of credit and banking where the individuals’ personal info (DoB, SSN etc) is only a small piece of the set required to obtain credit or impact the savings etc. This *used* to be so, when the teller at the local savings and trust knew you by sight, and you had to show up in person to make transactions. Multifactor authentication’s time has come.
Here in Australia, we have to provide “100 points” of ID when opening a bank account, etc. Various pieces of ID carry different scores, I usually use a passport + driver’s license.
They have to be real documents: copied numbers carry no points.
So the real problem is that there are so many places that have collected our data and they want to profit from it.
Perhaps we should consider going to the Euro model of opt-in only. And disallow the use of SSN for any private/consumer use.
What value is my data if you can’t market to me or abuse my information?
Maybe that would be the beginning of the end, after another 20 years of unraveling the mess.
Would never happen as they have so much money to buy politicians that we will be under the thumb of these data brokers for ever.
It is nice to imagine a world where we actually owned our data and controlled our privacy.
Thanks Brian.. A followup question.. Was your own data out there also? If not what have you done differently? Thanks..
Canaries are an interesting idea. But as several have pointed out there are some significant challenges in this data use model that doesn’t exist in payments. The transaction flows, data use, and common points where you can track the data are different and some may not exist.
That isn’t to say that just because there are some challenges it shouldn’t be done. It will most definitely require some careful thought and analysis. It also seems to me that the topic is worthy of some academic papers. Keeping the canaries useful, protecting meta-data or functionality like filters, etc. will all need to be addressed.
I won’t go as far as saying it will never work. And while I think I may see some ways around a couple of the problems they would need to be explored. What I can say for certain that there will need to be legislation and regulation to get it done.
The other thing I will say for sure is that we should all very much want it to be done the right way rather than rolling out something half-baked.
Great story and one that needs further attention. Unfortunately, public officials don’t like this type of “research” being done on them and written about. I’d expect a visit from law enforcement or an IRS audit in the near future.
OK, I love the fact that another great Krebs cyberfraud investigation story ends with an ad for one of Kevin Mitnick’s seminars. No shortage of historical irony here.
I think this could easily be carried out by as a private effort by a research institution/university. It is not too difficult to insert fake records into these databases. Someone could create multiple fake identities with encoded information in the PII (ie. john experian smith, robert kroll smith). Something a little harder than the example but many fields there to work with employment, residence, etc. not to difficult to encode information in there. With enough variance could provide fingerprint of some of the data sources.
Hah, this reminds me of a time I signed up my kids for Denny’s free birthday club. I didn’t want to give my kids’ real names, so I filled out the form as “Denny R.” and “Denise R.” Sure enough, we started getting spam snail mail from many kid-related advertising sources.
I’ve used the same thing for DNS registrar registrations as well, embedding the Registrar’s name in the address “c/o Registrar SPAM Dept.” Companies should all do this and then monitor for loss of their canaries.
Brian,
I think what you’re seeing here indicates that true security occurs when identity can NOT be shared.
As one commenter mentioned, it used to be that “people knew you.” That is, even though your identity was right there for anyone to see, it could NOT be shared; at least, not without some pretty fancy makeup. Which is just another way of saying the business model for the criminal simply wasn’t there for the vast majority of potential victims. Identity information should be verifiable, but not shareable.
Or, to put it differently, if one’s security model allows the sharing of identity information, then it is inherently insecure–pretty much by definition.
Therefore, data sharing of PII should be outlawed. It’s simply too risky.
Suggestion: Compare the economic benefit of PII-sharing with the probable value of the risks (ie loss exposure) of the sharing. Seems to me, though I’m not adequately plugged into this knowledge, we might have sufficient data to perform this risk analysis. My hypothesis is that the loss exposure will exceed the economic benefit by a fair margin. IMO, if so, then the case is made.
2nd attempt to post – I will summarize. All of our personal data is already compromised – we need a system that simply verifies who is really there. Like a small town, where everyone knows you, as Mike Sangrey mentioned.
I’d imagine this system would have to be centralized so it would be easier to keep people from breaking in and messing up your true identity; but normally it wouldn’t need to worry about anonymity at all. As I said before, I’m not talking about RF chips implanted in the body or tattoos, as I’d be totally against that – in fact I think fingerprints should be left out of the picture also. There are many ways to ID a person with the technology we have now, there is no excuse we cannot come up with new methods.
I’m not a PhD computer science guy, but often when I’ve written programs, designing in the appropriate levels of abstraction can make programs so much easier to use/reuse/maintain code.
This authentication method used by our credit rating and financial companies, I think, effectively has only one level. They use our real names, dob, SSN – things that can’t really be changed, and can be stolen and misused.
Apple Pay, for example, puts one layer of abstraction between the point of sale and the real credit card number.
Steve Gibson’s SQRL system is interesting. It seems like it gives us a rock-solid decentralized cryptographic framework to authenticate. It doesn’t do real-person authentication, but it’s interesting to consider how SSL certifications work, like the EV cert, domain authentication, etc. https://www.grc.com/sqrl/sqrl.htm
Companies like Verisign, Digicert, Symantec, etc, sign and certify the truthfulness/identity of EV certs, and these can also be revoked and reissued.
So, what I’m suggesting is that we treat real-world identity authentication like SSL Certs…
IMO, John’s comment moves us toward a solution. ISTM, that if the PII can’t be shared, then canaries can sing (or, well, stop singing, as the metaphor suggests).
Also, I’d like to respond to those suggesting regulation. I work in a VERY highly regulated industry. Trust me. Regulation will only add expense.
Regulation seeks to solve the security problem via Policy and Monitoring. Policy is an extremely weak form of security and is completely unusable against the criminal element. Monitoring is inherently reactive. It is not protective (unless coupled with very steep fines). And, things like the Sony break-in work quite effectively well as a surragate for the threat of expensive fines (thank you very much). So, regulation isn’t really all that helpful.
Having said that, regulation appears to help set the low bar; but, even then, it’s a very expensive low bar.
Regulation may well add expense, but no new regulation virtually guarantees that the status quo continues. Yes, they will probably patch their systems as vendors release patches, but that’s about it.
The incentives for industry are to not spend money unless it is in the hopes of increasing revenue, and the data brokers have no such incentive. It is the end users who care when their information gets leaked out, and the end users are not the ones who are directly paying the data brokers.
Brian, how do I report illegal copies of your book being offered online?
First of all, great show on 60 Minutes! Very well done.
Ok now about this topic, yes it’s a huge problem and I blogged it when you wrote the original post. This is huge and I’ve had as a hobby my little campaign as yet one more alternative to get a law passed that would require “all” data sellers to be indexed, in other words buy a license and disclosed what kind of data they sell and to what type of companies they sell too. This goes beyond the Data brokers and granted they are the biggest part of the problem.
I’ll give a link to my campaign at the end here where I’m not trying to get rich as you will see but just a little donation for my time. Like I said I’ve been working on it with my own time for 3 years which includes corresponding with lawyers at the FTC and members of Congress. Now that Rockefeller is retiring I’ll remove him:) He didn’t do much anyway other than hold hearings and write a couple letters.
Recently I also had a discussion with the World Privacy Forum and the idea of a license was certainly met with approval as a good start, which is what I intend by all means. You bet it’s an uphill battle and needs an act of Congress as the FTC is dead in the water. On 60 minutes a while back, the head of the FTC admitted they were helpless.
I had to laugh in your example with Richard Cordray as I have blogged many times how useless he is, nothing personal but a lawyer in the wrong job and even the White House earlier this year said he’s got more to learn. He’s not very sharp at all and is limited to going after low hanging fruit. While I’m on the topic, here’s a link of interest with a company you probably know called Argus who buys credit card transactions, scores you and then sells that data and the scores to banks and insurers.
Richard Cordray, what’s he doing, buying consumer data from Argus and making a data base of his own, so as I said not too smart. He must drive the Treasury Department nuts as every time I have written about him, they are all over the posts:) I’m pretty out there with my comments and was from the day he was appointed when I said we have another one suffering from the “Sebelius Syndrome”, my name for this affliction of data mechanics ignorance. Mary Jo White and Eric Holder I feel too are also afflicted as they don’t have a clue about computer code or what it does and how fraud code works.
http://ducknetweb.blogspot.com/2014/08/argus-analytics-produces-share-of.html
I think everyone knows by now I’m the accidental consumer advocate as others in this area have failed as we need that law to license data sellers so we know they all are. It was funny on Twitter a short while back too as out of the blue the chief of police in San Francisco jumped right in there too and liked the idea. It comes down to this, you can’t regulate or create rules without knowing who the players are. What kind of world would it be if stock brokers as an example where not licensed? I use that to make my case and the fact that I have to buy a license to go fishing, again something with very little risk and exposure:)
I just added a page to my campaign about a medical billing company who’s privacy statement duped patients in and the FTC caught them creating medical records with information from billing information and with other data from the web. It’s a good read. PaymentsMD was the name of the company.
Every week I’m in the face of the FTC or members of Congress with emails and I get them on my site reading do that’s a start, Warren, Schumer and a few others, so they are reading.
If you didn’t see this, look at what this hospital is doing, getting Acxiom records on patients along with their credit card transactions. Who knows how flawed this is. One day it was funny Acxiom decided to talk to me on Twitter and they never crawl out of their shell but I gave them loaded links to read and checked my stats and they went there:) I’ve been all over MasterCard too and they know who I am as they sell your records all over the place as well.
The problem is the repackaging that’s going on and I’ve had that issue myself with 2 aliases that keep showing up and I’ve never used an alias. Here’s the link to my campaign and if anyone feels generous, so be it and that makes me happy but if not, read the material anyway as it’s good stuff to know.
http://www.youcaring.com/other/help-preserve-our-privacy-/258776
I also made page of videos that I call the Attack of the Killer Algorithms that covers every day code hosing of consumers where you get duped and there’s a lot of Wall Street information and it’s at layman level for most of it. This is how inequality grows with math that move money if you want see what goes on behind the scenes. The first video is one my favorites, Charlie Siefe, NYU and his video about “Context”. See how you get duped with stats and stuff on the web.
http://www.ducknet.net/attack-of-the-killer-algorithms/
Maybe my license campaign will make it, who knows but I’m pushing it as step one.