Identity thieves have perfected a scam in which they impersonate existing customers at retail mobile phone stores, pay a small cash deposit on pricey new phones, and then charge the rest to the victim’s account. In most cases, switching on the new phones causes the victim account owner’s phone(s) to go dead. This is the story of a Pennsylvania man who allegedly died of a heart attack because his wife’s phone was switched off by ID thieves and she was temporarily unable to call for help.
 On Feb. 20, 2016, James William Schwartz, 84, was going about his daily routine, which mainly consisted of caring for his wife, MaryLou. Mrs. Schwartz was suffering from the end stages of endometrial cancer and wasn’t physically mobile without assistance. When Mr. Schwartz began having a heart attack that day, MaryLou went to use her phone to call for help and discovered it was completely shut off.
On Feb. 20, 2016, James William Schwartz, 84, was going about his daily routine, which mainly consisted of caring for his wife, MaryLou. Mrs. Schwartz was suffering from the end stages of endometrial cancer and wasn’t physically mobile without assistance. When Mr. Schwartz began having a heart attack that day, MaryLou went to use her phone to call for help and discovered it was completely shut off.
Little did MaryLou know, but identity thieves had the day before entered a “premium authorized Verizon dealer” store in Florida and impersonated the Schwartzes. The thieves paid a $150 cash deposit to “upgrade” the elderly couple’s simple mobiles to new iPhone 6s devices, with the balance to be placed on the Schwartz’s account.
“Despite her severely disabled and elderly condition, MaryLou Schwartz was finally able to retrieve her husband’s cellular telephone using a mechanical arm,” reads a lawsuit (PDF) filed in Beaver County, Penn. on behalf of the Schwartz’s two daughters, alleging negligence by the Florida mobile phone store. “This monumental, determined and desperate endeavor to reach her husband’s working telephone took Mrs. Schwartz approximately forty minutes to achieve due to her condition. This vital delay in reaching emergency help proved to be fatal.”
By the time paramedics arrived, Mr. Schwartz was pronounced dead. MaryLou Schwartz died seventeen days later, on March 8, 2016. Incredibly, identity thieves would continue robbing the Schwartzes even after they were both deceased: According to the lawsuit, on April 14, 2016 the account of MaryLou Schwartz was again compromised and a tablet device was also fraudulently acquired in MaryLou’s name.
The Schwartz’s daughters say they didn’t learn about the fraud until after both parents passed away. According to them, they heard about it from the guy at a local Verizon reseller that noticed his longtime customers’ phones had been deactivated. That’s when they discovered that while their mother’s phone was inactive at the time of her father’s death, their father’s mobile had inexplicably been able to make but not receive phone calls.
KNOW YOUR RIGHTS AND OPTIONS
Exactly what sort of identification was demanded of the thieves who impersonated the Schwartzes is in dispute at the moment. But it seems clear that this is a fairly successful and common scheme for thieves to steal (and, in all likelihood, resell) high-end phones.
Lorrie Cranor, chief technologist for the U.S. Federal Trade Commission, was similarly victimized this summer when someone walked into a mobile phone store, claimed to be her, asked to upgrade her phones and walked out with two brand new iPhones assigned to her telephone numbers.
“My phones immediately stopped receiving calls, and I was left with a large bill and the anxiety and fear of financial injury that spring from identity theft,” Cranor wrote in a blog on the FTC’s site. Cranor’s post is worth a read, as she uses the opportunity to explain how she recovered from the identity theft episode.
She also used her rights under the Fair Credit Reporting Act, which requires that companies provide business records related to identity theft to victims within 30 days of receiving a written request. Cranor said the mobile store took about twice that time to reply, but ultimately explained that the thief had used a fake ID with Cranor’s name but the impostor’s photo.
“She had acquired the iPhones at a retail store in Ohio, hundreds of miles from where I live, and charged them to my account on an installment plan,” Cranor wrote. “It appears she did not actually make use of either phone, suggesting her intention was to sell them for a quick profit. As far as I’m aware the thief has not been caught and could be targeting others with this crime.”
Cranor notes that records of identity thefts reported to the FTC provide some insight into how often thieves hijack a mobile phone account or open a new mobile phone account in a victim’s name.
“In January 2013, there were 1,038 incidents of these types of identity theft reported, representing 3.2% of all identity theft incidents reported to the FTC that month,” she explained. “By January 2016, that number had increased to 2,658 such incidents, representing 6.3% of all identity thefts reported to the FTC that month. Such thefts involved all four of the major mobile carriers.”
The reality, Cranor said, is that identity theft reports to the FTC likely represent only the tip of a much larger iceberg. According to data from the Identity Theft Supplement to the 2014 National Crime Victimization Survey conducted by the U.S. Department of Justice, less than 1% of identity theft victims reported the theft to the FTC.
While dealing with diverted calls can be a hassle, having your phone calls and incoming text messages siphoned to another phone also can present new security problems, thanks to the growing use of text messages in authentication schemes for financial services and other accounts.
Perhaps the most helpful part of Cranor’s post is a section on the security options offered by the four major mobile providers in the U.S. For example, AT&T offers an “extra security” feature that requires customers to present a custom passcode when dealing with the wireless provider via phone or online.
“All of the carriers have slightly different procedures but seem to suffer from the same problem, which is that they’re relying on retail stores relying on store employee to look at the driver’s license,” Cranor told KrebsOnSecurity. “They don’t use services that will check the information on the drivers license, and so that [falls to] the store employee who has no training in spotting fake IDs.”
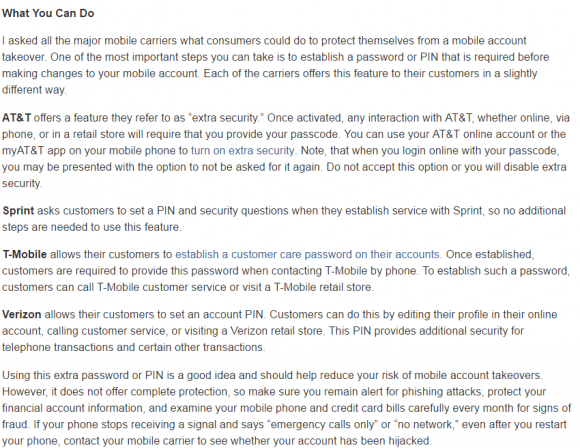
Some of the security options offered by the four major providers. Source: FTC.
It’s important to note that secret passcodes often can be bypassed by determined attackers or identity thieves who are adept at social engineering — that is, tricking people into helping them commit fraud.
I’ve used a six-digit passcode for more than two years on my account with AT&T, and last summer noticed that I’d stopped receiving voicemails. A call to AT&T’s customer service revealed that all voicemails were being forwarded to a number in Seattle that I did not recognized or authorize.
Since it’s unlikely that the attackers in this case guessed my six-digit PIN, they likely tricked a customer service representative at AT&T into “authenticating” me via other methods — probably by offering static data points about me such as my Social Security number, date of birth, and other information that is widely available for sale in the cybercrime underground on virtually all Americans over the age of 35. In any case, Cranor’s post has inspired me to exercise my rights under the FCRA and find out for certain.
Vineetha Paruchuri, a masters in computer science student at Dartmouth College, recently gave a talk at the Bsides security conference in Las Vegas on her research into security at the major U.S. mobile phone providers. Paruchuri said all of the major mobile providers suffer from a lack of strict protocols for authenticating customers, leaving customer service personnel exposed to social engineering.
“As a computer science student, my contention was that if we take away the control from the humans, we can actually make this process more secure,” Paruchuri said.
Paruchuri said perhaps the most dangerous threat is the smooth-talking social engineer who spends time collecting information about the verbal shorthand or mobile industry patois used by employees at these companies. The thief then simply phones up customer support and poses as a mobile store technician or employee trying to assist a customer. This was the exact approach used in 2014, when young hooligans tricked my then-ISP Cox Communications into resetting the password for my Cox email account.
I suppose one aspect of this problem that makes the lack of strong customer authentication measures by the mobile industry so frustrating is that it’s hard to imagine a device which holds more personal and intimate details about you than your wireless phone. After all, your phone likely knows where you were last night, when you last traveled, the phone number you last called and numbers you most frequently text.
And yet, the best the mobile providers and their fleet of reseller stores can do to tell you apart from an ID thief is to store a PIN that could be bypassed by clever social engineers (who may or may not be shaving yet).
A NOTE FOR AT&T READERS
By the way, readers with AT&T phones may have received a notice this week that AT&T is making some changes to “authorized users” allowed on accounts. The notice advised that starting Sept. 1, 2016, customers can designate up to 10 authorized users per account.
“If your Authorized User does not know your account passcode or extra security passcode, your Authorized User may still access your account in a retail store using a Forgotten Passcode process. Effective Nov. 5, 2016, Authorized Users and those persons who call into Customer Service and provide sufficient account information (“Authenticated Callers”) Will have the ability to add a new line of service to your account. Such requests, whether made by you, an Authorized User, an Authenticated Caller or someone with online access to your account, will trigger a credit check on you.”

AT&T’s message this week about upcoming account changes.
I asked AT&T about what need this new policy was designed to address, and the company responded that AT&T has made no changes to how an authorized user can be added to an account. AT&T spokesman Jim Greer sent me the following:
“With this notice, we are simply increasing the number of authorized users you may add to your account and giving them the ability to add a line in stores or over the phone. We made this change since more customers have multiple lines for multiple people. Authorized users still cannot access the account holder’s sensitive personal information.”
“Over the past several years, the authentication process has been strengthened. In stores, we’re safeguarding customers through driver’s license or other government issued ID authentication. We use a two-factor authentication when you contact us online or by phone that requires a one-time PIN. We’re continuing our efforts to better protect customers, with additional improvements on the horizon.”
“You don’t have to designate anyone to become an authorized user on your account. You will be notified if any significant changes are made to your account by an authorized user, and you can remove any person as an authorized user at any time.”
The rub is what AT&T does — or more specifically, what the AT&T customer representative does — to verify your identity when the caller says he doesn’t remember his PIN or passcode. If they allow PIN-less authentication by asking for your Social Security number, date of birth and other static information about you, ID thieves can defeat that easily.
Has someone fraudulently ordered phone service or phones in your name? Sound off in the comments below.
If you’re wondering what you can do to shield yourself and your family against identity theft, check out these primers:
How I Learned to Stop Worrying and Embrace the Security Freeze (this primer goes well beyond security freezes and includes a detailed Q&A as well as other tips to help prevent and recover from ID theft).




What doesn’t compute is even a cell phone without provisioned service should still be able to call 911.
If it was not as Rick said, what are the various shelters truly doing with the donated cell phones? (He is correct.)
That was my first thought as well. You should always be able to dial 911, even if the cell phone does not currently have a service agreement attached to it.
In many countries you are always able to call 112. Except I guess in America it would rob the MSP from vital cashflow.
Actually, landlines in many states, and mobile phones across the US and Canada, are required to be able to call 911 as long as there’s a signal (that is, as long as a connection is technically possible), even if there’s no service plan, even if previous service was terminated for non-payment: https://en.wikipedia.org/wiki/9-1-1#Inactive_telephones
(Curiously, I also read that AT&T maps 112 to 911, for the benefit of visitors from Europe or the many non-EU countries that have adopted this emergency number, and similarly, some phone providers in other countries map 112 and 911, if otherwise unused, to whatever emergency number is used locally; relatedly, the ITU recommends one of those two numbers for places that don’t yet have emergency numbers.)
What other commenters have said, that she hadn’t actually tried to call 911 but instead tried calling friends and relatives, sounds more reasonable.
This happened to my coworker a couple weeks ago. Someone walked into a Sprint store in Michigan (we are in Texas) and added 4 lines to her account, all iPhones. In her case, the scammers were also able to get into her online Sprint account, and initiate several payments from her bank account. So her phone didn’t get turned off, but she had TWO big messes to sort out!
I have Verizon Wireless as my provider and I am charged a “911” fee on every invoice. My understanding was that all carriers were required to collect this fee and that the purpose of this fee was to keep 911 accessible on ALL mobile phones!
1) Mrs. Schwartz didn’t try to call 911.
It was a family member she reached on her husband’s cellphone who did.
This isn’t uncommon for folks in a stressed situation to call a friend or relative instead of 911.
I have no doubt if she had dialed 911 from her de-activated phone it would have worked.
2) The 911 fee isn’t to provide 911 service to the subscriber. That cost is essentially zero Verizon.
The 911 fees go to support the hardware and software used to route the calls to the appropriate dispatch centers, to show the location information about the phone (easier back in the days they were mostly wired to a physical location), and display that information to the 911 call takers.
It’s that infrastructure that the fee pays, it doesn’t pay to provide “service” to phones so they can call 911.
(For those wondering how I can conclude Mrs. Schwartz didn’t call 911, read the lawsuit in the link.
Had she tried to call and that call failed, the attorneys would’ve mentioned it in the legal equivalent of asterisked, bold, italicized, blinky text.
Instead they have to make a case that a reasonable person in Mrs. Schwartz’s age, condition, and mental state of mind wouldn’t have considered calling 911 but would instead repeatedly try to call different friends and relatives)
There was a time I would’ve said that the notion of an adult, even an elderly one calling relatives/friends for medical emergencies is dumb and all their fault. Thing is, I’ve been the recipient of those calls, with me practically yelling into the phone “CALL 911!!!”, then having to call that locality’s police and ambulance service myselfto get them out to those elderly relatives’ homes.
It does happen. And happens to people who are otherwise rational when there’s no emergency.
So yes, the harsh reality is that in emergencies, some people don’t necessarily think straight. And in regards to 911, this especially includes people who are old enough to remember the pre-911 days (and yes, for people old enough, the 80s and 90s can count as “recent”, and Google says that 911 service still only covered around half the country by 1987).
I know that it seems silly to not immediately think “911” for an ambulance when a medical emergency happens, but I grew up with it. A lot of older people have not. And they’ll think family and friends first before paramedics. I know “anecdote” isn’t “data”, but the point stands that it’s not unreasonable to predict older people reacting this way.
This. I’ve seen that with elderly (my mother, who called my brother instead of the emergency number in her home country, 112.)
I’ve also seen it here with a young person, 20-something. The apartment building I lived in caught on fire, and the neighbor who saw the smoke called the apartment management, who then told her to call 911…
You didnt get the point!!! She was able to call 911 later, but it was too late. When you are 84 and weird messages pop on screen and you are having heart attack, you wouldnt find a way to go through steps required… Very sad…
Most of cybercrime tax fraud identy fraud and so on starting from ukraine money aswell goes to ukraine. So from ukraine the money goes to isis. And russia. Money incirulation
Similar problems here (in Australia) – always stemming from mobile providers making everything as low-friction as possible at the expense of proper security verification. With the most basic degree of identity theft, it’s laughably easy to have numbers ported (through a nice anonymous phone call), move accounts between providers and devices, and upgrade or add devices to an account. The mobile market is such a booming business that consumer identification and protection is currently an afterthought (understandable perhaps, but also unforgivable). Something really has to give – looking forward to some legislated standards for KYC, as in the financial sector.
This is unacceptable, on two fronts.
1. 911 service is supposed to be always available, no matter what. Deactivating even the 911 service on the Schwartz’s phone was an act of criminal negligence on the part of Verizon.
2. There’s a bleeding obvious 2FA solution here, which is that to deactivate, forward, or otherwise change a phone’s plan for any reason should require receiving a code in an SMS at the phone that is to be deactivated or otherwise affected, then relay that code to the phone company employee to prove that you actually possess the phone in question. The only exception should be for deactivating or replacing a lost or stolen phone, in which case yes, 911 service should remain available from the old phone, and other methods of authentication should be used, such as bringing to them the last utility bill they’d mailed you for the phone in question. Nobody but the phone’s rightful owner is likely to possess that. So, they should require you to have either the phone itself or paperwork proving it’s yours, either a bill they’ve sent you or whatever documentation they gave you when you originally activated it.
There’s a basic authentication problem that should take things such as stolen phones, house burning down which destroys all phones and password records.
Without a robust and simple procedure such as fingerprints, iris scans, etc, the mobile provider must be prepared to walk away from a significant number of customers who have forgotten PINs, or whatever.
I make up the answers to all “personal knowledge” questions. The last time I went into the store to upgrade a phone, I was asked my web password, which I don’t memorize anyway. Since I didn’t know it, the clerk just told me what it was and proceeded with the upgrade. I did present the old phone hardware as at least one level of identification though.
It’s already there. All phones have an ein. A number attached to the phone at manufacture. That’s how I tracked down a phone owner to return their dropped phone. Even thou it was not an art company phone, they located the owner, by address and their other phone number, on another companies account, and returned it.
But, the elder adult, is the bane of every phone company. And they prefer simple easy devices, a bane to the the smaller obscure devices that are so common today. Eye scanner? Mini strokes, change the flow patterns on people, fingerprint, too many pattern changes as you age, voice? Even worse, ever have a cold, stuffy nose? A phone is to use, a communication device, it’s not a security device, a personal tracker, or any of the things it could be, but, they now deliver ads? So someone’s is watching what generates money for them by your having it. Too bad it’s not us it’s worrying about.
I thought about that approach, but if the phone truly is lost or stolen, and the thief gets a text, isn’t he likely to say it’s my phone don’t trust the thieves trying to change/upgrade my phone?
So, there are two different components to a phone:
1. The phone (IMEI)
2. The SIM (IMSI)
The value of the SIM is in being able to hack 2FA systems.
The value of the phone is for pure resale.
If someone doesn’t know you, then stealing the phone is mostly for its resale value. If someone is trying to hack your life (@mat style), then the value is in the SIM because that enables them to capture 2FA responses.
Note: for a thief, there’s probably slightly more risk in the SIM, in that it enables police to find them. If you watch modern TV shows/Movies about people on the run, one thing the good shows will do is take out the SIM — because that’s what ties the phone to your account. While powered on phone not in airplane mode with your SIM in it is in an area with coverage anywhere in the world, its home operator (e.g. AT&T) effectively knows where it is and can be asked to track it (which is pretty much exactly what you want to do if you’re trying to find your thief) — not to GPS accuracy levels, but with triangulation, to reasonable levels.
Once that SIM is removed, the phone no longer talks to your home network, it can talk to no-network, or the network of whichever SIM is inserted, and that operator has no reason to believe it’s stolen. There is an IMEI blacklist [1] (but, do you know your IMEI? your carrier should be keeping logs of it, but…).
It’s pretty hard for me to imagine the thieves described in this article as being interested in attacking the potential value of an IMSI, I’d expect them to just try to convert the phone (without SIM) into cash by selling it (sans SIM).
I’m not sure how well the IMEI blacklisting process works. An interesting DoS attack would be to report someone else’s phone’s IMEI as stolen.
Remember that it’s legal for you to sell your phone to someone else, so effectively an IMEI is transferrable.
Similarly, it’s possible to change the name on an account and thus transfer the IMSI to another individual (or just add an “authorized user” or an “informally authorized user”).
* Verizon is/was special, in that while it runs a CDMA network, it has phones which don’t require SIMs, and instead it effectively binds the CDMA equivalent of the IMEI directly to your account.
[1] https://imeidata.net/blacklist/check
In the case of an @mat style hacker who is trying to take over your virtual life, yes, in order to gain time he would certainly claim that you’re the thief. — And he’d probably also set up forwarding to a couple of services so that the SIM isn’t physically anywhere near him, otherwise the police would be able to track him.
Also, if you allow this for a ‘lost’ or ‘stolen’ phone all the thief has to do is say it was lost. Then if asked to produce verification they would raise a stink about being a loyal customer, how dare you treat them this way, I’ll cancel my policy and sue you…blah,blah,blah..
Or they may have already redirected your sms to another phone so they would have the code that was sent.
Point is there is no really ‘secure’ way to do this. As Brian, and the security community at large, point out if you put a lock on something, someone somewhere will be figuring a way around that lock. Some for the fun of it, some to help you make a stronger lock, and other who feel if you put a lock on it it must be valuable so I want in.
At a minimum, an employee could leave the counter to the back room and attempt to call the number in question. If no on answers and a fraudster is at the counter, then the employee tried. If someone answers on an actually stolen phone, the thief will probably say, “wrong number.” If the real owner is at the counter and no one answers, no biggie. The point is to try in a way that is meaningful. Your comment seems to assume that the thief stealing the original phone and the thief at the counter are the same person, which is not the situation presented in your article. It’s possible, but the point is to try. The situation being discussed in these comments is where the thief at the counter does not have the phone in his possession.
It’s never that simple.
1. Some people don’t have fixed addresses.
2. Some people have residences that suffer fires or floods (hi New Orleans).
3. Many vendors are trying to switch billing to “paperless” (hi annoying gas company).
This means that it’s pretty easy to argue “I don’t have the bill”.
Plus. Imagine you’re traveling to Florida on vacation, and a thief steals your phone. Do you go into a store and say “hi, I have here my copy of my last phone bill”? Of course not, no one goes on vacation taking a copy of all of their documentation for every purchase … that’s not a vacation.
OK, why the hell is this thing eating my comments?
The system sometimes will delay a comment. Some end up queued for moderation. And sometimes it’s just an odd caching thing.
FWIW, one of my earlier comments here got snagged by one of the systems, but it showed up by the time I made another comment.
Don’t worry too much about it. If you’re worried about comments getting eaten frequently, then I’d suggest you compose them in Notepad, and copy them over for submission. If a comment does appear to be eaten, wait an hour and repost (preferably from the same browser, otherwise you might not see a notice that your original comment has been placed in the moderation queue). Otherwise, if you just think it was eaten, and choose to post again, both comments will probably appear and make you look a bit silly.
Sounds like a good reason not to have a “plan” but to purchase the phone outright and buy call credit as required – preferably via a voucher bought at a supermarket so that the phone company never knows your credit card number.
If you expose here too much fbi together with fraudsters will come and arrest you!@
This article reminded me of similar issue that happened to Linus Media Group (a YouTube channel with millions of subscribers) where their phone was hijacked and the hackers were able to get access to the group’s Twitter and other accounts through the 2-factor authentication and password reset via SMS features.
https://youtu.be/LlcAHkjbARs (the description of the “hack” starts at 3:00)
This is another reason I’m glad that I use a pre-paid phone. There is no contract to upgrade and no free phone; all this equals no worries for this type of fraud!
I simply buy a phone that’s compatible with the provider I’ve chosen and pay for the service each month.
This is a terrible situation, but another reason that I’m glad I use a reliable landline for calls at home as well as an emergency button pendant for a loved one who has health problems.
I have been the victim of multiple attempts to order tablets and high end phones off my Wireless account. In all but one case did the attacker get away with it, despite me being on the phone with my carrier moments after the device purchase was texted to me. Some months later I was registering with Samsung for warranty service on an SSD and discovered a tablet registered in my name to an address in Florida that belongs to a woman. She was also getting warranty service on her tablet. So I changed the return address to reflect my current residence (so as to get my SSD back). For months, the tablet was in limbo as Samsung had no idea who to send it too. They finally called me with an “audit” and I told them, the tablet was stolen. They obviously couldn’t hold on to it without a written police report, and eventually the device disappeared from my registered devices list.
Commercial revenue beats commercial security 10 to 1.
Security is a cost center, never a profit center.
Security only comes about through regulation or after consumer/victim law suits.
Think about that, the next time a political dufus claims the country has to reduce regulations and cap lawsuit judgments.
Learned something new about the 43 year old FCRA; it grows in lustre.
Excellent, informative journalism.
How’s about the cell phone manufacturers enable “bricking” stolen phones? When you report your hijacked cell account, At&T (etc.) DISABLES the stolen phone.
Well reverse that, the thief comes in, reports the phone stolen (the one in your possession, remember they are now you to the person they are talking to), the transaction happens. Now you have a bricked phone and the thief has a brand new phone charged to your account, which they sell that night on Craigslist, they make pure profit. You have the mind numbing task of proving ‘you’ didn’t buy/order the new phone and you need yours turned back on, but anything you had on it is now gone.
Not pretty to think about but is potentially a very real scenario.
All good, until someone calls your provider pretending to be you, tells them your phone was stolen, and your phone suddenly turns into a brick.
Until law enforcement treats these cases as aggravated identity theft, which it is, instead of just simple property crime, nothing will change and no one will investigate.
What makes it “aggravated?”
@Brian: re account protections.
1. I frequently get various American wireless accounts set up against my email address (unauthorized). It’s a painfully slow process to get enough information to be able to yell at the phone companies (AT&T, Verizon, Sprint, Cricket, others). The most recent one required me to wait for receive about 4 emails to collect enough “account information” for me to be able to identify an “account” to a CSR. And even once I have enough “information”, they’re really not very eager to “change the information, because it isn’t your account”.
2. When I set up my latest Pay-as-you-go T-Mobile subscription, they didn’t ask me about a PIN — just gave me the SIM and promised it would work. It didn’t (my phone never received the APN settings, meaning it could call but not use the Internet — and I had no one to call, I only wanted data service). T-Mobile had a provision for me to reset my PIN from the phone (really phone tied to SIM).
@Brian re PINs.
I’m very wary of any PIN based system. They have all sorts of flaws:
1. Who wants to carry hundreds of PINs?
* One per CC/ATM-card
* one per phone
* one per SIM-account, one per SIM-chip
* one per wired-internet, one for gas, one for water, one for power
* one per — well, basically every single account you have
* two per financial: bank account (in order to do transactions, esp wire transfers, I need to know my full account and routing information, and for this PIN nonsense, I’d need a PIN), retirement, investment, insurance. — For all of these you generally need to know your account number, which is often not written down often (to “protect” your account’s security).
* A handful of them for the IRS (2 or 3 at last count? one for filing, one for retrieving a copy of last year’s filing, one for something else??).
* One for each of the 4 major US credit bureaus to thaw my credit reports, and one for each of the major Canadian credit bureaus (currently 2) when they move into the present and support freezes…
* One per Domain Registrar account (or possibly per Domain or ccTLD?)
** I’m waiting for Republicans to require a PIN for voting…
2. Because there are way too many PINs for people to have, they either end up being all the same (which makes compromising additional systems easy), or…
3. People lose them and the service needs to offer a way to reset them.
There’s a reason that phone companies (and everyone else) have asked customers to use their SSN as an authenticator: it’s something everyone “remembers”, and it isn’t “a public record, like your DOB” ** — yes, it’s a public record, because for a while it was more or less calculatable based on your Birth-Record (place+DOB), and the fact that nearly every US person has probably had their SSN exposed to some sort of leak/theft.
There’s a reason that the modern world is moving away from static pins (e.g. magstripe CC) to dynamic pins (2FA whether via Chip+PIN, or SMS, or U2F).
This happened to me last year with ATT. I’m absolutely sick of this.
I’ve received three notices in the last two weeks from other entities indicating I have new accounts open which I didn’t open.
When can we start killing these idiots on a wholesale basis? I want heads on pikes.
On two separate occasions I’ve had this happen to me. Someone went into a Verizon Wireless store and upgraded two of our basic lines to high end smart phones.
The first there was no photo identification used. I was able to get the issue resolved and my service restored to the two lines in question.
On the second occasion I had someone use a fake ID. They had my name, address, etc. but the persons picture. I have no idea how my identification was stole or used or how they even knew I had a verizon wireless account. I saw the activity within minutes and was able to call that store and figure out what was going on. Again, all charges were reversed and I was not liable but it is very frustrating when this happens because it is my time that gets thrown away when dealing with everything. From what I can tell having my account locked down seems to have stopped the behavior but I’m still curious if it’ll happen again. I’m glad that at my age I knew how to fix it but I feel awful for that family for having this issue and someone losing their life over it.
If it wasn’t so scary, it would be hilarious. The notice Brian got from ATT was worded just as if it was designed by hackers/thieves, and would have instantly found its way into my spam file. Then ATT would have claimed they notified me while enabling fraud and theft in my name.
When I got that ‘cute’ little message from AT&T I read it 4 times and concluded that whoever wrote it was dumber than a rock.
And…
That I was going to close my AT&T account and move it to another carrier.
I’m wondering how many of these frauds would exist if, when verifying the customer via drivers license, they were also required to use a fingerprint reader….not for verification but in the event of fraud the fingerprint would be given to the police.
At 84, it’s time. You cannot escape the reaper for much longer than that. Cell phone or not.
Phil,
One indicator of the demise of a society is how it treats the very young (the unborn) and the very old. My grandmother was spry at 84, as was my friend’s great-grandfather. Each of them did very well until only weeks before they passed.
If not 84, then what about 82? 79? 75? Where does it end. Go read some Sci-Fi about those utopian societies with the dark underbelly of killing off anyone over a certain age.
Likewise, at the other end of the age spectrum, the very young. As one guy put it, there’s no moral difference between a baby at one end of the birth canal versus the other end (pre-natal, post-natal). Since abortion is currently based on the “want” of the mother (and often the mother only, fathers having little or no say), then therefore, without a moral difference before and after birth and “want” as a subjective basis, he predicted that we will soon see infanticide. Again, until what age limit, 2 months, 5 months? Etc.
You may claim that when your time comes you won’t care or will see it as your duty to society, as the Nazi’s did. If we changed to a society where the cold-heartedness you expressed here is the rule, and they come to kill (stealing your life from you) you at an age that has been legislated but is ultimately arbitrary, you may realize the monstrosity of your attitude.
It’s one thing to simply call you a monster. Instead, let’s be clear that you have shown you utter lack of compassion and contempt for life. In my experience with people who hold the same maxim you’ve expressed, they are most often untrustworthy in a psychopathic sense.
It’s not that you should have kept your statement to yourself. No, we need to see that there are monsters among us. Thank you for speaking up.
Sorry for all the typo’s–the sentence fragment that should have ended with a comma and the apostrophe in the plural for Nazis, etc. I had to hurry while typing. Hurrying causes more errors.
Blaming the victim, is disturbing to me. She paid for a service that wasn’t available to her at her time in need. Obviously, the fraud on this death case was easily preventable and they should be held accountable for the negligence. According to the lawsuit, the new iPhone was purchased in a different state with no identification. It’s very sad and the family will never know if their loved one would have survived because Verizon allows fraud to occur. The company is not taking appropriate steps and security measures to prevent this fraud from occurring to others. Hope it doesn’t happen to anyone else. So sad.
is any having problems with the pictures showing up on google chrome?
It’s not a problem with Chrome. It happens very frequently. Others have said it’s a problem with how the blogging software is set up.
When I encounter the problem, I come in via HTTP instead of HTTPS and I can see the pictures on any browser.
That’s very naive approach. Big hit on the usability – people often forget answers and then you have to keep calling Customer Care. Also what if someone is using very old version of a browser that can lead to his/her session being hijacked.
My phone service is through a mobile virtual network operator (MVNO) called Ting. There is no such thing as a retail mobile phone store. There are no store customer service reps. If I want to activate a new phone, I do it myself on-line.
I trust my on-line account against hacking more than I trust a customer service reps against social engineering.
Identity thieves are only successful because they have the confidence in knowing that there are few resources being used to stop them. The FTC has stepped up and at a minimum provided us with resources to combat identity theft after it occurs. The identity thieves however will continue to cause havoc on a National basis until we have a program in place that requires that there be an Identity fraud investigation department in retail companies that will be required to thoroughly investigate a fraud claim. I take identity theft very seriously and have all the normal monitoring services subscribed to. I also get immediate alerts on my cell phone every time my card is used. The other day I was in a meeting and a text came through about a $300.00 charge at a local restaurant on my card. I immediately called the restaurant and informed them that it was fraudulent they knew the table that made the charge as they were still there, The police were called and 6 Identity theft thieves were arrested… I slept great that night :). .
I sort of understand this scam, but someone opened 5 “land line” accounts in southern CA and v**izon let them do it, then they were defaulted upon, and went into collection. How are utility companies allowed to do this?
I should have said opened these in my (and other) names, using my stolen credentials. Land lines? Weird.
Brian, does the ‘business records’ provision include security camera footage of the transaction? You should ask Lorrie if she recieved the video footage of the purchase.