Late last month, multiple news outlets reported that unspecified law enforcement officials had seized the servers for Leakedsource.com, perhaps the largest online collection of usernames and passwords leaked or stolen in some of the worst data breaches — including billions of credentials for accounts at top sites like LinkedIn and Myspace.
In a development that could turn out to be deeply ironic, it seems that the real-life identity of LeakedSource’s principal owner may have been exposed by many of the same stolen databases he’s been peddling.
LeakedSource in October 2015 began selling access to passwords stolen in high-profile breaches. Enter any email address on the site’s search page and it would tell you if it had a password corresponding to that address. However, users had to select a payment plan before viewing any passwords.
LeakedSource was a curiosity to many, and for some journalists a potential source of news about new breaches. But unlike services such as BreachAlarm and HaveIBeenPwned.com — which force users to verify that they can access a given account or inbox before the site displays whether it has found a password associated with the account in question — LeakedSource did nothing to validate users. This fact, critics charged, showed that the proprietors of LeakedSource were purely interested in making money and helping others pillage accounts.
I also was curious about LeakedSource, but for a different reason. I wanted to chase down something I’d heard from multiple sources: That one of the administrators of LeakedSource also was the admin of abusewith[dot]us, a site unabashedly dedicated to helping people hack email and online gaming accounts.
Abusewith[dot]us began in September 2013 as a forum for learning and teaching how to hack accounts at Runescape, a massively multiplayer online role-playing game (MMORPG) set in a medieval fantasy realm where players battle for kingdoms and riches.

The currency with which Runescape players buy and sell weapons, potions and other in-game items are virtual gold coins, and many of Abusewith[dot]us’s early members traded in a handful of commodities: Phishing kits and exploits that could be used to steal Runescape usernames and passwords from fellow players; virtual gold plundered from hacked accounts; and databases from hacked forums and Web sites related to Runescape and other online games.
The administrator of Abusewith[dot]us is a hacker who uses the nickname “Xerx3s.” The avatar attached to Xerx3s’s account suggests the name is taken from Xerxes the Great, a Persian king who lived during the fifth century BC.
Xerx3s the hacker appears to be especially good at breaking into discussion forums and accounts dedicated to Runescape and online gaming. Xerx3s also is a major seller of Runescape gold — often sold to other players at steep discounts and presumably harvested from hacked accounts.
I didn’t start looking into who might be responsible for LeakedSource until July 2016, when I sought an interview by reaching out to the email listed on the site (leakedsourceonline@gmail.com). Soon after, I received a Jabber chat invite from the address “leakedsource@chatme.im.”
The entirety of that brief interview is archived here. I wanted to know whether the proprietors of the service believed they were doing anything wrong (we’ll explore more about the legal aspects of LeakedSource’s offerings later in this piece). Also, I wanted to learn whether the rumors of LeakedSource arising out of Abusewith[us] were true.
“After many of the big breaches of 2015, we noticed a common public trend…’Where can I search it to see if I was affected?’,” wrote the anonymous person hiding behind the leakedsource@chatme.im account. “And thus, the idea was born to fill that need, not rising out of anything. We are however going to terminate the interview as it does seem to be more of a witch hunt instead of journalism. Thank you for your time.”
Nearly two weeks after that chat with the LeakedSource administrator, I got a note from a source who keeps fairly close tabs on the major players in the English-speaking cybercrime underground. My source told me he’d recently chatted with Xerx3s using the Jabber address Xerx3s has long used prior to the creation of LeakedSource — xerx3s@chatme.im.
Xerx3s told my source in great detail about my conversation with the Leakedsource administrator, suggesting that either Xerx3s was the same person I spoke with in my brief interview with LeakedSource, or that the LeakedSource admin had shared a transcript of our chat with Xerx3s.
Although his username on Abusewith[dot]us was Xerx3s, many of Xerx3s’s closest associates on the forum referred to him as “Wade” in their forum postings. This is in reference to a pseudonym Xerx3s frequently used, “Jeremy Wade.”
![An associate of Xerx3s tells another abusewith[dot]us user that Xerx3s is the owner of LeakedSource. That comment was later deleted from the discussion thread pictured here.](https://krebsonsecurity.com/wp-content/uploads/2017/02/xerownsit-580x252.png)
An associate of Xerx3s tells another abusewith[dot]us user that Xerx3s is the owner of LeakedSource. That comment was later deleted from the discussion thread pictured here.
The “Jeremy Wade” pseudonym shows up in a number of hacked forum databases that were posted to both Abusewith[dot]us and LeakedSource, including several other sites related to hacking and password abuse.
For example, the user database stolen and leaked from the DDoS-for-hire service “panic-stresser[dot]xyz” shows that a PayPal account tied to the email address eadeh_andrew@yahoo.com paid $5 to cover a subscription for a user named “jeremywade;” The leaked Panicstresser database shows the Jeremywade account was tied to the email address xdavros@gmail.com, and that the account was created in July 2012.
The leaked Panicstresser database also showed that the first login for that Jeremywade account came from the Internet address 68.41.238.208, which is a dynamic Internet address assigned to residential customers of Comcast Communications in Michigan.
According to a large number of forum postings, it appears that whoever used the xdavros@gmail.com address also created several variations on that address, including alexdavros@gmail.com, davrosalex3@yahoo.com, davrosalex4@yahoo.com, as well as themarketsales@gmail.com.
The Gmail account xdavros@gmail.com was used to register at least four domain names almost six years ago in 2011. Two of those domains — daily-streaming.com and tiny-chats.com — were originally registered to a “Nick Davros” at 3757 Dunes Parkway, Muskegon, Mich. The other two were registered to a Nick or Alex Davros at 868 W. Hile Rd., Muskegon, Mich. All four domain registration records included the phone number +12313430295.
I took that 68.41.238.208 Internet address that the leaked Panicstresser database said was tied to the account xdavros@gmail.com and ran an Internet search on it. The address turned up in yet another compromised hacker forum database — this time in the leaked user database for sinister[dot]ly, ironically another site where users frequently post databases plundered from other sites and forums.
The leaked sinister[dot]ly forum database shows that a user by the name of “Jwade” who registered under the email address trpkisaiah@gmailcom first logged into the forum from the same Comcast Internet address tied to the xdavros@gmail.com account at Panicstresser.
I also checked that Michigan Comcast address with Farsight Security, a security firm which runs a paid service that tracks the historic linkages between Internet addresses and domain names. Farsight reported that between 2012 and 2014, the Internet address 68.41.238.208 was tied to no-ip.biz, popular “dynamic IP” service.
No-ip.biz and other dynamic IP address services are usually free services that allow users to have Web sites hosted on servers that frequently change their Internet addresses. This type of service is useful for people who want to host a Web site on a home-based Internet address that may change from time to time, because services like No-ip.biz can be used to easily map the domain name to the user’s new Internet address whenever it happens to change.
Unfortunately, these dynamic IP providers are extremely popular in the attacker community, because they allow bad guys to keep their malware and scam sites up even when researchers manage to track the attacking IP address and convince the ISP responsible for that address to disconnect the malefactor. In such cases, dynamic IP services allow the owner of the attacking domain to simply re-route the attack site to another Internet address that he controls.
Farsight reports that the address 68.41.238.208 maps back to three different dynamic IP domains, including “jwade69.no-ip.biz,” “wadewon.no-ip.biz,” and “jrat6969.zapto.org.” That first dynamic address — jwade69.no-ip.biz — was included among several hundred others in a list published by the Federal Bureau of Investigation as tied to the distribution of Blackshades, a popular malware strain that was used as a password-stealing trojan by hundreds of paying customers prior to May 2014.
XERX3S HACKED?
In January 2017, when news of the alleged raid on LeakedSource began circulating in the media, I began going through my notes and emails searching for key accounts known to be tied to Xerx3s and the administrator of Abusewith[dot]us.
Somehow, in the previous three months I’d managed to overlook an anonymous message I received in mid-September from a reader who claimed to have hacked the email account themarketsales@gmail.com, one of several addresses my research suggested was tied to Xerx3s.
The anonymous source didn’t say exactly how he hacked this account, but judging from the passwords tied to Xerx3s’s other known accounts that were included in the various forum database leaks listed above it may well have been because Xerx3s in some cases re-used the same password across multiple accounts.
My anonymous source shared almost a dozen screenshots of his access to themarketsales@gmail.com, which indicate the name attached to the account was “Alex Davros.” The screenshots also show this user received thousands of dollars in Paypal payments from Leakedsource.com over a fairly short period in 2015.
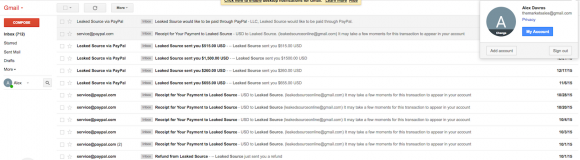
The screenshots also showed that themarketsales@gmail.com was tied to a PayPal account assigned to a Secured Gaming LLC. Recall that this is the same company name included in the Web site registration records back in 2011 for daily-streaming.com and tiny-chats.com.
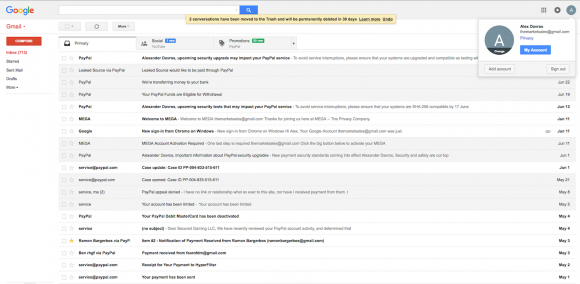
A screenshot shared with me in Sept. 2016 by an anonymous source who said he’d hacked the Gmail address “themarketsales@gmail.com”.
In addition, the screenshot above and others shared by my source indicate that the same Paypal account tied to themarketsales@gmail.com was habitually used to pay a monthly bill from Hyperfilter.com, a company that provides DDoS protection and hosting and which has long been the provider used by Abusewith[dot]us.
Finally, the anonymous hacker shared screenshots suggesting he had also hacked into the email account desiparker18@gmail.com, an account apparently connected to a young lady in Michigan named Desi Parker. The screenshots for Ms. Parker suggest her hacked Gmail account was tied to an Apple iTunes account billed to a MasterCard ending in 7055 and issued to an Alexander Davros at 868 W. Hile, Muskegon, Mich.
The screenshots show the desiparker18@gmail.com address is associated with an Instagram account for a woman by the same name from Muskegon, Mich. (note that the address given in the WHOIS records for Alex Davros’s daily-streaming.com and tiny-chats.com also was Muskegon, Mich).
Desi Parker’s Instagram lists her “spouse” as Alex Davros, and says her phone number is 231-343-0295. Recall that this is the same phone number included in the Alex Davros domain registration records for daily-streaming.com and tiny-chats.com. That phone number is currently not in service.
Desi Parker’s Facebook account indeed says she is currently in a relationship with Alexander Marcus Davros, and the page links to this Facebook account for Alex Davros.
Alex’s Facebook profile is fairly sparse (at least the public version of it), but there is a singular notation in his entire profile that stands out: Beneath the “Other Names” heading under the “Details about Alexander” tab, Alex lists “TheKing.” Parker’s Instagram account includes a photo of an illustration she made including her beau’s first name with a crown on top.
Interestingly, two email addresses connected to domains associated with the Jeremy Wade alias — matt96sk@yahoo.com and skythekiddy@yahoo.com — are tied to Facebook accounts for Michigan residents who both list Alex Davros among their Facebook friends.
Below is a rough mind map I created which attempts to show the connections between the various aliases, email addresses, phone numbers and Internet addresses mentioned above. At a minimum, they strongly indicate that Xerx3s is indeed an administrator of LeakedSource.
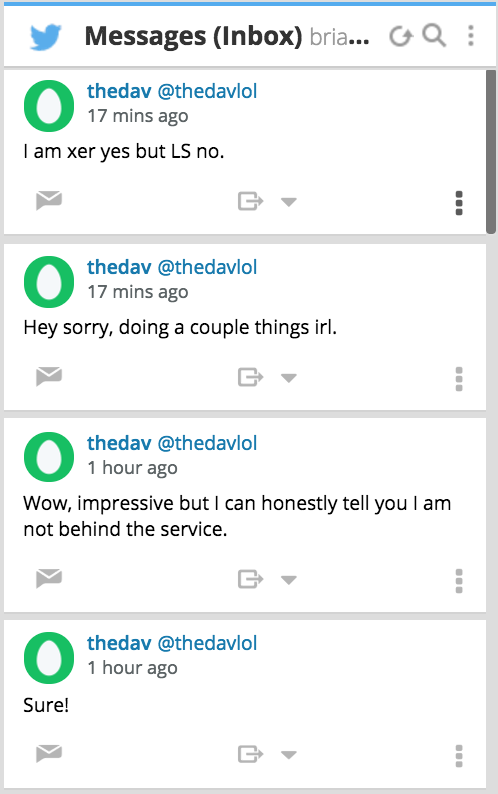 I managed to reach Davros through Twitter, and asked him to follow me so that we could exchange direct messages. Within maybe 60 seconds of my sending that tweet, Davros followed me on Twitter and politely requested via direct message that I remove my public Twitter messages asking him to follow me.
I managed to reach Davros through Twitter, and asked him to follow me so that we could exchange direct messages. Within maybe 60 seconds of my sending that tweet, Davros followed me on Twitter and politely requested via direct message that I remove my public Twitter messages asking him to follow me.
After I did as requested, Davros’s only response initially was, “Wow, impressive but I can honestly tell you I am not behind the service.” However, when pressed to be more specific, he admitted to being Xerx3s but claimed he had no involvement in LeakedSource.
“I am xer yes but LS no,” Davros said. He stopped answering my questions after that, saying he was busy “doing a couple things IRL.” IRL is Internet slang for “in real life.” Presumably these other things he was doing while I was firing off more questions had nothing to do with activities like deleting profiles or contacting an attorney.
Even if Davros is telling the truth, the preponderance of clues here and the myriad connections between them suggest that he at least has close ties to some of those who are involved in running LeakedSource.
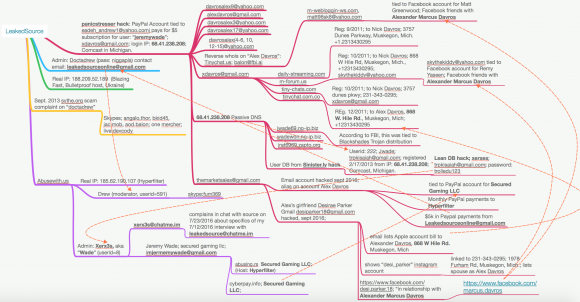
A “mind map” I created to illustrate the apparent relationships between various addresses and pseudonyms referenced in this story.
THE LEGALITY OF LEAKEDSOURCE
On the surface, the rationale that LeakedSource’s proprietors have used to justify their service may seem somewhat reasonable: The service merely catalogs information that is already stolen from companies and that has been leaked in some form online.
But legal experts I spoke with saw things differently, saying LeakedSource’s owners could face criminal charges if prosecutors could show LeakedSource intended for the passwords that are for sale on the site to be used in the furtherance of a crime.
Orin Kerr, director of the Cybersecurity Law Initiative at The George Washington University, said trafficking in passwords is clearly a crime under the Computer Fraud and Abuse Act (CFAA).
Specifically, Section A6 of the CFAA, which makes it a crime to “knowingly and with intent to defraud traffic in any password or similar information through which a computer may be accessed without authorization, if…such trafficking affects interstate or foreign commerce.”
“CFAA quite clearly punishes password trafficking,” Kerr said. “The statute says the [accused] must be trafficking in passwords knowingly and with intent to defraud, or trying to further unauthorized access.”
Judith Germano, a senior fellow at the Center on Law and Security at New York University’s School of Law, said LeakedSource might have a veneer of legitimacy if it made an effort to check whether users already have access to the accounts for which they’re seeking passwords.
“If they’re not properly verifying that when the user goes to the site to get passwords then I think that’s where their mask of credibility falls,” Germano said.
LeakedSource may be culpable also because at one point the site offered to crack hashed or encrypted passwords for a fee. In addition, it seems clear that the people who ran the service also advocated the use of stolen passwords for financial gain.





Nice job, Brian!
Yeah, it must be nice to have criminal friends who submit evidence of their crimes that you then use to write about their victims.
Yet again it shows that for all their supposed technical mastery it’s the basics that let them down and lead to their unveiling. No different to the corporate world where you can have the best firewalls and IPS in the world but if some numpty admin responds to a phishing email with their uid and password you’re screwed.
Too much focus on the sexy stuff and not enough on the basics.
It also shows that how ever hard you try to remove it, once stuff is on the internet it’s going to stay there for ever.
“Too much focus on the sexy stuff and not enough on the basics”.
That sums up life in 2017, irregardless of whether you are talking about internet security, running the country or anything else.
Hi Brian
You can check more of his FB details via hxxxs://stalkscan.com/
A site from an ethic hacker that only grabs data in a legal manner.
Something is wrong with your post dates. All of them are showing as published on 17th Feb.
The big number is the day.
Would be helpful if it used a four-digit year (YYYY MMM) instead of the confusion two digits (YY MMM). I know this has bit me a number of times, and then I remember, “Oh, yeah Krebs’ site shows the date format odd.”
This is why we have ISO 8601.
https://en.wikipedia.org/wiki/ISO_8601
You really could solve this by prefixing the 2 digit year w/ an apostrophe (’17) ..
If you did decide to make a change to the date format (and I hope you do not) I would suggest using the ordinal date, as that both conforms to the related ISO standard and would be even more opaque than your current format, to the uninitiated.
All the posts do say “Feb 17 ” . I tried Chrome and IE and Edge.
the big number is the day.
Brian you could make it easier for everyone just use Roman numerals 😉
XV
II
XVII
Looking good!
No, 17 is the year. The large 15 above the “Feb” is the date.
Krebs you’ve really did an impressive work !
As we can see in the alex’s gf insta :
https://www.instagram.com/desi_parker/
it was his birthday 3 days ago , so this is the best GIFT from you for him .
Keep the good work krebs .
Great article and great research Brian, thanks! Regarding the legality, well, I think it is in fact not that easy. If they really cracked or even offered to crack passwords, then it probably was illegal to provide such services, but if they just aggregated and mirrored already public info, well then it could be difficult. But if a court decides it’s illegal, how do we for example categorize cloud-based hash cracking services like hashkiller, etc. then, which basically offer a similiar service? I guess it’s a quite difficult topic.
Any decent prosecutor would annihilate any argument that this was done for the common good. All they have to prove is you were in possession of this stolen info, and made it available to the general public with no attempt to protect the people listed. They can argue that protecting those people isn’t their job, to which the reply is that neither was it their job to release the list. Let’s face it, once the FBI had ahold of him, he is boned. They’d have a judge carpet bombing LE with warrants, seizures and freezes as fast as they could sign them. Once it went bad, it would go bad fast and hard.
https://ghostbin.com/paste/kzfft
mirror https://0bin.net/paste/6-vehKz15LdB2Y0+#Xln0ek4eN-tjc0CVCuPe6TM9G4yIle6mdZbjyk94dvB
“Art enables us to find ourselves and loose ourselves at the same time.”
Wow Davros sucks at everything.
There are so many facepalms there that I guarantee he will always be caught if he tries cybercrime again. There’s just so many slips there that it would be impossible for him to pull off perfect crimes.
Brian,
Great piece of forensic journalism, once again. Keep up the great work.
HaveIbeenPwned? will let you check on any email address from the main page. You need to prove you own an email address to get notifications.
Great chunk of detective work Krebs, impressive in every aspect, hats off to you
I love what you do Brian.
Thanks, Chris. I hope they let me keep doing it. I don’t know how to do anything else 🙂
Brian,
I love what you do and agree with you about 99% of things. However, I’m not sure how I feel about bringing Ms. Parker into this post. I accept that it may be an important link that holds the chain of who LeakedSource is together, but I wouldn’t be thrilled about being dragged into this if I were her or her parents. I’m sure you considered this, and obviously felt it was too integral to omit, but I’m not where I come down on it.
Tough lesson for her, but basically, “Don’t date criminals mucking around in the mud, or you’ll get some on you.”
I agree, there is no need to name his girlfriend. I’m sure she got problems IRL cause of this.
“Walk with the wise and become wise, for a companion of fools suffers harm” Proverbs 13:20
Mr. Krebs, I revere your journalism, but it’s no wonder your Jabber chat was so short: you came across as a giant d*ck. Nobody appreciates being talked to like that. And if a reporter interviewed me in all lowercase with no punctuation, I’d laugh them off as well.
I thought you were shilling at first but then examined this “interview” myself.
While leaked source is obviously in the wrong overal, I was very surprised hostility and rudeness of krebs here. The guy from leaked source was trying to be civil and seemed far more professional for far longer than I would have.
Perhaps this is some tactic the might Krebs has learned works well against cyber criminals, but I doubt that’s the case. Other than that another well put together story with brilliant research.
Jacob, you’re complaining about the treatment of a fraudster who makes money from account breaches.
Think about that. You’re more concerned with someone being handled gently than what they do.
What. The. Hell. Is. Wrong. With. You.
Can you explain why a criminal’s feelings matter? And better yet, what are you smoking that made you value etiquette with a crook over the harm they have done to the public.
I’d have to agree, much to my surprise.
Brian is an excellent resource and I’m in awe of his skills.
But should someone approach me in that somewhat illiterate manner (capitals exist for a reason, dammit), I’d be dismissive.
And this Xerx3s guy, he was surprisingly eloquent; it would have been appropriate to respond in kind.
All that said, really wish to reiterate how much I respect Mr Krebs.
I too respect Mr. Krebs especially after breaking free of sinking WaPo (Ignatius, Dep. AG “Sour Grapes” Yates and Intelligence abuses).
I would say the interview was more like one by F. Chuck Todd or Sen. “Cigar Store” Warren. Seems like trying to get zingers in as opposed to answers out. I was surprised by the civility and grammar by the suspected fraudster. He or she may have a future in DC.
Brian,
You may have missed another possible connection: Davros is also the name of the original creator of Dr. Who’s arch-enemies, the Daleks.
https://www.facebook.com/marcus.davros a friend of my daughter
eadeh_andrew@yahoo.com should be eadeh_andrew1@yahoo.com
There are several way you can interview an informant. You probably have heard of good cop/ bad cop scenarios. Those people are usually handled with kid gloves as to not bruise their egos. But bad guy’s need their ego bruised. May be they would realize they are not doing good, and modify their behavior. A stern word from a security pro might have turned his averse to good. But then they have to be open, he wasn’t open.
Nice job as always, Brian!
I live within an hour of him. Check out the property records and whose name is listed: https://accessmygov.com/SiteSearch/SiteSearchDetails?SearchFocus=All+Records&SearchCategory=Address&SearchText=800-900+W.+Hile&uid=329&PageIndex=1&ReferenceKey=27-013-200-0053-00&ReferenceType=0&SortBy=&SearchOrigin=0&RecordKey=1%3d27-013-200-0053-00%3a%3a4%3d27-013-200-0053-00%3a%3a5%3d27-013-200-0053-00&RecordKeyType=1%3d0%3a%3a4%3d0%3a%3a5%3d0
I have nothing to back this up but I’m curious if the reason why Davros was receiving payments from LS was because we was selling/distributing DBs to them, not because he was an administrator or owner.
Please donate to Krebs so he can keep doing what he is doing. Digital criminals rely on the darkness that anonymity provides them and are embolden because they are not in the physical presence of their victims which makes them feel disconnected with the crimes they commit or the damage they do. It is not real for them until Krebs casts light into the shadows and suddenly everything collapses.
I believe the owner (He is at least affiliated with LeakedSource) is Paiman Wandy.
He also used to be an admin on AbuseWithUs
See what you can whip up with this info.
https://skidpaste.org/ZgeYFcNm
I made an attempt to look into this what happened with LS, though admittedly not nearly as thoroughly as yourself. There’s a post on AbuseWithUs where someone states they believed xer to be the owner of LS, to which he replies he isn’t but does know the owner and I believe he vouches for the service. The commented suggestion here from Chris that he may have received payment for database contributions sounds rather reasonable considering what we know. These are interesting theories nonetheless. I’m just hoping we eventually receive some evidence explaining what happened.
I’m quite surprised by how many connections you’ve made.. it’s almost unbelievable how easily different accounts/services/etc. can be tied together so elegantly. Thanks for sharing this!
Excellent sleuthing, Brian! What a tangled web you unraveled! Hopefully some in the intelligence community take some pointers from you. ;o)
It’s so good to see an article on Runescape. Thank you Krebs!
Nice work, author.
I’m really surprised. The lack of security this guy uses, especially for someone running a site like that.
And the fact that it’s all from his home IP address? I use a VPN literally 24/7. Not for anonymity but still, it would stop someone from finding my home IP like that. And the only time I use real location information is for things involving money where it’s absolutely required. Failing that, whois protection is like what? $7?
-Endless facepalming-
No offense to Orin Kerr, but I think the easier statute to use in this case is 18 U.S. Code § 1029 – Fraud and related activity in connection with access devices.
Back in the 1990s, when I was doing a lot of incident response surrounding sniffers, I learned from U.S. Attorneys that the evidentiary standards and provable damage limits (at the time, CFAA had a limit of something like $10,000 damage involving high hundreds or low thousands of compromised computers), and DDoS attacks were even harder to calculate damages and identify victims, while intrusions involving sniffers were much easier to prosecute because simple possession of stolen passwords (i.e, “access control devices”) with intent to use them for fraud was all that needed to be proved.
It would seem that in this case, simple possession with intent, due to the holding back of certain high-value passwords and selling them, would easily meet this low bar. I’ll bet you that is one of the primary charges if this does get pursued as a criminal offense.
Did you use a specific tool to create the mind map graphic in this article? It looks great.
Yes. Mindnode Pro for Mac.
Thanks Krebs. I’ll check it out. You da man keep on doxing.
Damn! You’re research is so good and juicy. 😀 Keep it up!
we are cool being lame. Hahaha xD
http://prntscr.com/eeh82v