“He built a piece of software. That tool was pirated and abused by hackers. Now the feds want him to pay for the computer crooks’ crimes.”
The above snippet is the subhead of a story published last month by the The Daily Beast titled, “FBI Arrests Hacker Who Hacked No One.” The subject of that piece — a 26-year-old American named Taylor Huddleston — faces felony hacking charges connected to two computer programs he authored and sold: An anti-piracy product called Net Seal, and a Remote Administration Tool (RAT) called NanoCore that he says was a benign program designed to help users remotely administer their computers.

Photo illustration by Lyne Lucien/The Daily Beast
The author of the Daily Beast story, former black hat hacker and Wired.com editor Kevin Poulsen, argues that Huddleston’s case raises a novel question: When is a programmer criminally responsible for the actions of his users?
“Some experts say [the case] could have far reaching implications for developers, particularly those working on new technologies that criminals might adopt in unforeseeable ways,” Poulsen wrote.
But a closer look at the government’s side of the story — as well as public postings left behind by the accused and his alleged accomplices — paints a more complex and nuanced picture that suggests this may not be the case to raise that specific legal question in any meaningful way.
Mark Rumold, senior staff attorney at the Electronic Frontier Foundation (EFF), said cases like these are not so cut-and-dry because they hinge on intent, and determining who knew what and when.
“I don’t read the government’s complaint as making the case that selling some type of RAT is illegal, and if that were the case I think we would be very interested in this,” Rumold said. “Whether or not [the government’s] claims are valid is going to be extraordinarily fact-specific, but unfortunately there is not a precise set of facts that would push this case from being about the valid reselling of a tool that no one questions can be done legally to crossing that threshold of engaging in a criminal conspiracy.”
Citing group chat logs and other evidence that hasn’t yet been made public, U.S. prosecutors say Huddleston intended NanoCore to function more like a Remote Access Trojan used to remotely control compromised PCs, and they’ve indicted Huddleston on criminal charges of conspiracy as well as aiding and abetting computer intrusions.
Poulsen depicts Huddleston as an ambitious — if extremely naive — programmer struggling to make an honest living selling what is essentially a dual-use software product. Using the nickname “Aeonhack,” Huddleston marketed his NanoCore RAT on Hackforums[dot]net, an English-language hacking forum that is overrun with young, impressionable but otherwise low-skilled hackers who are constantly looking for point-and-click tools and services that can help them demonstrate their supposed hacking prowess.
Yet we’re told that Huddleston was positively shocked to discover that many buyers on the forum were using his tools in a less-than-legal manner, and that in response he chastised and even penalized customers who did so. By way of example, Poulsen writes that Huddleston routinely used his Net Seal program to revoke the software licenses for customers who boasted online about using his NanoCore RAT illegally.
We later learn that — despite Net Seal’s copy protection abilities — denizens of Hackforums were able to pirate copies of NanoCore and spread it far and wide in malware and phishing campaigns. Eventually, Huddleston said he grew weary of all the drama and sold both programs to another Hackforums member, using the $60,000 or so in proceeds to move out of the rusty trailer he and his girlfriend shared and buy a house in a low-income corner of Hot Springs, Arkansas.
From the story:
“Now even Huddleston’s modest home is in jeopardy,” Poulsen writes. “As part of their case, prosecutors are seeking forfeiture of any property derived from the proceeds of NanoCore, as well as from Huddleston’s anti piracy system, which is also featured in the indictment. ‘Net Seal licensing software is licensing software for cybercriminals,’ the indictment declares.
“For this surprising charge—remember, Huddleston use the licenses to fight crooks and pirates—the government leans on the conviction of a Virginia college student named Zachary Shames, who pleaded guilty in January to selling hackers a keystroke logging program called Limitless. Unlike Huddleston, Shames embraced malicious use of his code. And he used Net Seal to protect and distribute it.
“Huddleston admits an acquaintanceship with Shames, who was known on HackForums as ‘Mephobia,’ but bristles at the accusation that Net Seal was built for crime. ‘Net Seal is literally the exact opposite of aiding and abetting’ criminals, he says. ‘It logs their IP addresses, it block their access to the software, it stops them from sharing it with other cyber criminals. I mean, every aspect of it fundamentally prevents cybercrime. For them to say that [crime] is its intention is just ridiculous.’”
Poulsen does note that Shames pleaded guilty in January to selling his Limitless keystroke logging program, which relied on Huddleston’s Net Seal program for distribution and copy protection.
Otherwise, The Daily Beast story seems to breeze over relationship between Huddleston and Shames as almost incidental. But according to the government it is at the crux of the case, and a review of the indictment against Huddleston suggests the two’s fortunes were intimately intertwined.
From the government’s indictment:
“During the course of the conspiracy, Huddleston received over 25,000 payments via PayPal from Net Seal customers. As part of the conspiracy, Huddleston provided Shames with access to his Net Seal licensing software in order to assist Shames in the distribution of his Limitless keylogger. In exchange, Shames made at least one thousand payments via PayPal to Huddleston.”
“As part of the conspiracy, Huddleston and Shames distributed the Limitless keylogger to over 3,000 people who used it to access over 16,000 computers without authorization with the goal and frequently with the result of stealing sensitive information from those computers. As part of the conspiracy, Huddleston provided Net Seal to several other co-conspirators to assist in the profitable distribution of the malicious software they developed, including prolific malware that has repeatedly been used to conduct unlawful and unauthorized computer intrusions.”
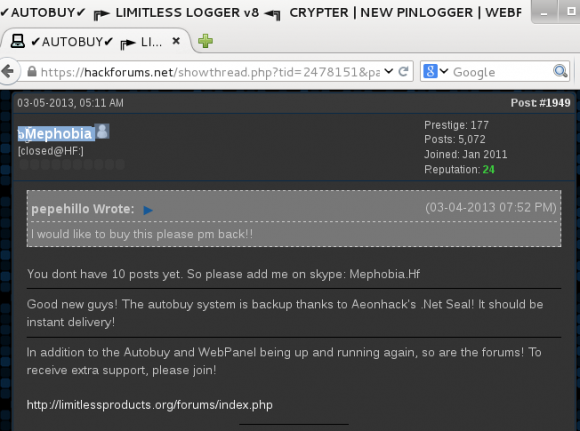
A screen shot of Zach “Mephobia” Shames on Hackforums discussing the relationship between his Limitless keylogger and Huddleston’s (Aeonhack) Net Seal anti-piracy and payment platform.
Allison Nixon, director of security research for New York City-based security firm Flashpoint, observed that in the context of Hackforums, payment processing through Paypal is a significant problem for forum members trying to sell dual-use software and services on the forum.
“Most of their potential customer base uses PayPal, but their vendor accounts keep getting suspended for being associated with crime, so people who can successfully get payments through are prized,” Nixon said. “Net Seal can revoke access to a program that uses it, but it is a payment processing and digital rights management (DRM) system. Huddleston can claim the DRM is to prevent cybercrime, but realistically speaking the DRM is part of the payment system — to prevent people from pirating the software or initiating a Paypal chargeback. Just because he says that he blocked someone’s license due to an admission of crime does not mean that was the original purpose of the software.”
Nixon, a researcher who has spent countless hours profiling hackers and activities on Hackforums, said selling the NanoCore RAT on Hackforums and simultaneously scolding people for using it to illegally spy on people “could at best be seen as the actions of the most naive software developer on the Earth.”
“In the greater context of his role as the money man for Limitless Keylogger, it does raise questions about how sincere his anti-cybercrime stance really is,” Nixon said. “Considering that he bought a house from this, he has a significant financial incentive to play ignorant while simultaneously operating a business that can’t make nearly as much money if it was operated on a forum that wasn’t infested with criminals.”
Huddleston makes the case in Poulsen’s story that there’s a corporate-friendly double standard at work in the government’s charges, noting that malicious hackers have used commercial remote administration tools like TeamViewer and VNC for years, but the FBI doesn’t show up at their corporate headquarters with guns drawn.
But Nixon notes that RATs sold on Hackforums are extremely dangerous for the average person to use on his personal computer because there are past cases when RAT authors divert infected machines to their own botnet.
Case in point: The author of the Blackshades Trojan — once a wildly popular RAT sold principally on Hackforums before its author and hundreds of its paying customers were arrested in a global law enforcement sweep — wasn’t content to simply rake in money from the sale of each Blackshades license: He also included a backdoor that let him secretly commandeer machines running the software.
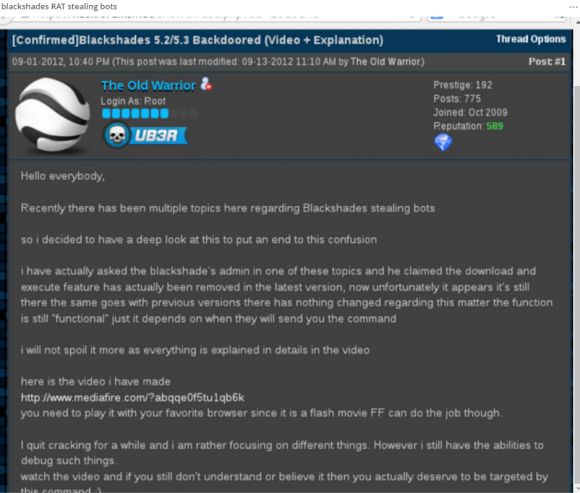
A Hackforums user details how the Blackshades RAT included a backdoor that let the RAT’s original author secretly access systems infected with the RAT.
“If a person is using RAT software on their personal machine that they purchased from Hackforums, they are taking this risk,” Nixon said. “Programs like VNC and Teamviewer are much safer for legitimate use, because they are actual companies, not programs produced by teenagers in a criminogenic environment.”
All of this may be moot if the government can’t win its case against Huddleston. The EFF’s Rumold said while prosecutors may have leverage in Shames’s conviction, the government probably doesn’t want to take the case to trial.
“My guess is if they want a conviction, they’re going to have to go to trial or offer him some type of very favorable plea,” Rumold said. “Just the fact that Huddleston was able to tell his story in a way that makes him come off as a very sympathetic character sounds like the government may have a difficult time prosecuting him.”
A copy of the indictment against Huddleston is available here (PDF).
If you enjoyed this story, take a look at a related piece published here last year about a different RAT proprietor selling his product on Hackforums who similarly claimed the software was just a security tool designed for system administrators, despite features of the program and related services that strongly suggested otherwise.




Do you suppose the providers of the software that allowed him to program something “illegal” will be prosecuted?
Two things:
1. By advertising his software on hackerforums, it shows intent – malicious intent. Team Viewer and VNC aren’t advertising in hackerforums. That’s probably why the feds aren’t beating their door down.
2. Huddleston knowingly profited from Shames sale of Limitless. I’m sure Huddleston was more than happy to provide Shames access to Net Seal for that specific purpose.
I’m not a lawyer, and I may be missing several facts, but the language in the indictment doesn’t seem to be covered by the sections referred to in it:
– 18 U.S.C. § 371 – Conspiracy to Defraud the United States
– 18 U.S.C. § 1030 – Fraud and related activity in connection with computers
– 18 U.S.C. § 2 – Principals
I’m not sure I’m sold on any intent to defraud the United States – directly or indirectly by the defendant (18 U.S.C. § 371).
I’m also not sold that there is enough evidence to prove intentionally causing damage to computer systems by transmitting a program, information, code, or command (18 U.S.C. § 1030 (a)(5)(A) and (B)).
The last code referred to, that is fairly vague and ties the previously mentioned codes to the defendant, is 18 U.S.C. § 2:
A – “Whoever commits an offense against the United States or aids, abets, counsels, commands, induces or procures its commission, is punishable as a principal.”
B – “Whoever willfully causes an act to be done which if directly performed by him or another would be an offense against the United States, is punishable as a principal.”
If the last section can be used to tie the previous sections in the indictment to the defendant, why isn’t there an indictment towards the developers of Skype? While it wasn’t being advertised directly by the company on Hackforums[dot]net, it is obviously being used by attackers to commit fraud. Doesn’t the language apply to them as well?
While I do not condone the actions of the defendant, I make tools (for research and interest) that could be used by attackers that would constitute fraud and abuse. Should I be concerned?
A few things:
1. Where Huddleston advertised should be immaterial. If determining criminal intent is down only to the forum you’ve posted it on, we’ll have some very dangerous squinting on our hands.
2. Knowingly profiting from the sale of a tool should also be irrelevant to intent, because it’s not the tool that should be issue but the intent to use it for criminal purposes, which is what’s essential to demonstrate.
3. A read of the indictment would seem to show that the government is not leaning heavily (or solely at any rate) on where Huddleston advertised and whether he profited. They quote communication between himself and others that strongly suggest that he was aware of criminal usage and collaborated by failing to stop or report it.
If he is indicted and convicted, I only hope it’s on the correct grounds–criminal collaboration–and not for advertising on the wrong forum and making money from his work.
It seems to me that convicting for any other reason that I’ve named could slide very easily into people being convicted for trying to hold software companies responsible–by posting details of a vulnerability if/when the company refuses to respond in a timely matter and issue a patch.
Read the indictment. The case hinges on the contents of the unreleased Skype chatlogs. It’s not a case of “you posted an ad on the wrong forum, now you go to jail”. It’s a case of “someone admitted to crimes and asked for help and you gave it to them”.
I agree with Mike & John.
If they convict this guy for the wrong reasons, that could be a precedent that kitchen knife manufacturers would be responsible for knives used in a murder. I hope the prosecutors aren’t so myopic to miss that. They’ve have to demonstrate either deliberate collaboration or a deliberate blind eye, as John said, and not merely “advertising on the wrong forum.”
If a knife manufacturer advertises on a “how-to-murder” website, they should absolutely be worried. Making a dual-purpose thing is not the issue – promoting the illegal side of the dual-purpose thing is the problem.
This issues proves how little our government knows about cybersecurity. It is true that hacking tools can be used for nefarious purposes, but it is also true that the same tools can be used for penetration testing to help identify vulnerabilities before the bad guys find them. So why hasn’t the government gone after HD Moore, author of Metasploit, or Rapid7, who now markets Metasploit commercially? Seems to me that if we are having such a hard time finding good cybersecurity talent that our government would be working to employ Mr. Huddleston and allow the country to benefit from his obvious skills. Also worth noting…historically it has not worked to go after gun manufacturers when users of those guns kill people, and the same should be the case here.
Wow, it only took 3 comments for the gun analogy to come out. The point of the story is that there’s no cause for such strained analogies in a case like this.
“Hacking programs don’t hack people, people hack people”
Heh! Heh! 🙂
Brian – guns are a good analogy: in both cases, you have things that are inherently neutral, but can be used for good and bad. Huddleston wrote something and sold it on a bad place, frequented by bad people, doing bad things. His alleged shock and outrage about people misusing his software is absurd.
Mr. Huddleston would be of no use to the NSA or any other Government org… there is far greater talent already employed there.
A large part of the reason they have such a hard time finding people is their requirements… specifically their drug use policy. They would have thousands more candidates if not for that. Either way, though, they have a ton of talented people working for them. It is naive to believe otherwise.
Kevin Poulson, who helped WIRED and Adrian Lamo rat out Bradley (nee Chelsea) Manning to the feds?
I’ll pass…
Since when was VNC, as Nixon claims, a company?
Since 2002. Andy Harter (CEO of RealVNC Limited) and other members of the original VNC team at AT&T founded RealVNC Limited in 2002. https://en.wikipedia.org/wiki/RealVNC
https://www.realvnc.com/company-profile/
expect hes talking about realvnc which is paid for non-home versions.
Another frightening example of lawyers and public officials gone bad. A while back Hilary Clinton proclaimed her intent to sue gun and ammunition manufacturers each and every time a hand gun or rifle was used in the commission of a crime!
Thank God for Trump! Let’s hope its not to late for Trump to restore balance to our society.
You just *had* to bring 45 into this, didn’t you?
I know right. That’s like the 4th time this week I’ve read that exact same comment.
“Hilary Clinton proclaimed her intent to sue gun and ammunition manufacturers”
Take your meds for f’s sake. You’re hallucinating.
Actually, that comment has some validity. Hillary wanted to take away protections so victims could sue.
http://www.bbc.com/news/world-us-canada-34447239
Now, what this all has to do with this story, is more nebulous.
This guy knew exactly what he did, his NetSeal was used to protect only more trojans and other malware and that was its purpose, it even supported some shady CC processor. You want real anti-piracy protections use real tools like PE-Lock and alike.
He sold the both tools only on HF, accepting bitcoins without any customers verification and now he want to play the innocent victim of the system. Are you taking us for fools Mr. Huddleston?
I’d love to see the pleadings. My personal opinion (not legal opinion) is that this is a show case, not a case the government intends to win. To prove any criminal liability the government will have to prove “mens rea” or intent. For an attenuated action (not direct hacking) but tool misuse I think that is hard. We have strong case law from the VHS/Betamax “time shifting” recordings provide precedent that a lawful use is strong evidence of non-infringement for copyright, and this line of reasoning should apply. Furthermore, the 1st amendment protects both source and object code as speech, so the government will have to overcome that defense as well. That said, I haven’t seen the evidence and if there is direct evidence of actual knowledge and profit from intentional hacking – then maybe.
CC- there is a link to the government’s complaint at the bottom of the story.
A very complicated case. Metasploit is an open-source exploit toolkit that can function very similar to some RAT’s, and yet you don’t see it’s developers being arrested.
People talk about how to use TeamViewer for unethical purposes all the time and TeamViewer bans their license, etc. Similar to this Net Seal DRM.
And I think one of the BlackShades creators was being prosecuted for credit card fraud he did as well (which I have no sympathy for) and they just decided to pile up charges on him.
Marketing on Hackforums isn’t the best idea though.
Allison’s comments/observations have a lot of merit and his association with Shames diminishes the idea Huddleston didn’t know what people might be using it for; however, I’m open to the idea he may not have intended for it to be weaponized at the rate it was because of the fact he tried to control its use with consumers. What’s interesting, though, is the fact he didn’t develop the software with triggers or something amounting to a killswitch.
Better yet, why didn’t he create auditing features to ensure data collection could occur in order to track the tool’s usage? I know this sets up issues concerning data privacy, but that could be spelled out to anyone prior to the sell which would make the data collection transparent. While it could be argued this would add time to software development and not worth the effort, he was familiar with a person (Shames) who knew how to develop those services and certainly could have found a number of tools, libraries or open source packages to integrate into his tool.
I’m inclined to believe he was ethically challenged (i.e., unconcerned with ensuring the software was being used in a legal manner) once the money came in. Furthermore, it’s hard to imagine someone selling their wares on a notorious hacker forum without considering the likelihood a consumer on that forum would use it differently than it was advertised.
Why didn’t he build certain things in? Well, knowing what needs to be built in comes with experience, and from the accounts here, he was relatively inexperienced. I see many more experienced developers not including fundamental things into what they build, so I wouldn’t expect someone with little experience to really think of a number of things.
Even if there was intent, the problem is proving it in the court of law. He must be considered innocent until proven guilty. There is a ton of circumstantial evidence against him, but it is just that. Where is the hard evidence? Any indictment that includes intent to perform an action is very difficult to get a conviction, without some sort of ‘smoking gun.’ And, for something like this, it comes down to intent.
Ken,
You make a good point on the author’s experience; however, if we assume the indictment has any merit, then the government’s case may be stronger than we know. For instance, the feds allege Huddleston had extensive Skype sessions with others about data exfiltration, including Mr Shames. By this time, the feds allege, Huddleston was well aware of how Shames was using his software to distribute his key logger and that there were emails between Shames and his customers indicating his tool was being used as a worm.
The version of the RAT I found in the wild supposedly was sold for $25. The gov’t alleges that Huddleston required 50 licenses of Net Seal per sale and implicitly allowed to use the code as they wish at that point. If the NanoCore RAT was part of the Net Seal code, then, this could suggest he was getting approximately $1250 per transaction. This brings up another point.
Net Seal was being sold exclusively to cyber criminals. For a person who spends a significant portion of his time online selling his software to these individuals (whom he had some degree of familiarity with), doesn’t strike you as suspicious that he wasn’t aware of that critical fact?
Good article though I wouldn’t trust a site like The Daily Beast, just my opinion here.
While the article was great in it’s entirety, this is by far my favorite sentence:
“Huddleston marketed his NanoCore RAT on Hackforums[dot]net, an English-language hacking forum that is overrun with young, impressionable but otherwise low-skilled hackers who are constantly looking for point-and-click tools and services that can help them demonstrate their supposed hacking prowess.”
Well done as always Brian, with both the story as well as calling out skids in a hilariously tasteful manner.
I remember when Wietse Venema released SATAN and there was the same sort-of hand-wringing about him being complicit in the misuse of the tool. Regardless of where Huddleston advertised, the slippery slope of one person being responsible for the acts of another is way too slippery of a slope to be going down.
“[O]ne person being responsible for the acts of another” has been part of our legal tradition going back thousands of years to Roman Law, that’s a large part of why the arguments about “criminal intent” are so ferocious. You can’t supply inherently dangerous instrumentalities to minors, for example, much less sell a stolen firearm to a perosn you know is on a crime spree — the examples are endless.
I didn’t read the government’s complaint, but I do think a jury will have a hard time with any case brought against him.
Not really. Any competent prosecutor will paint him in a negative light easily enough, associating him with hackers. Consider how technologically illiterate the average user is; those are the ones on a jury. Any decent prosecutor will make sure that the jury is full of ’em.
Always a slippery slope. One thing the feds need to make sure doesn’t happen is to scare off anyone who may develop a worthwhile tool for the good guys to find vulnerabilities in order to close them. Metasploit, nessus, and others are absolutely needed in the toolbox to help secure your environment.
So if I am permitted to extrapolate…. If a bank robber drives away with the loot… the car company becomes an accomplice….? How about the company that made his/ her clothes!!!? The companies facilitated this crime?!!
But the part about him advertising on hacker sites doesn’t do him any favors.
The bank robber’s getaway driver is an accomplice.
Even if it’s an Uber driver, that isn’t aware of the robbery?
Even if it’s a Taxi that wasn’t aware of the robbery?
Some of the car advertisements I have seen could be taken to imply that the car being advertised has the capacity to be used as a getaway car. 🙂
As an active member of HF i can say, He knew exactly what he was doing. There are a lot of busts going on right now for RAT and Botnet sellers, they all know what they are selling, thats why they are selling it.
Looking at the comments, I think half the people here didn’t read the article or even skim the indictment.
I think you’re right and that’s likely true of anyone here making analogies between software and cars and guns.
Some of us did read the indictment and aren’t necessarily disagreeing with it.
But we are disagreeing with people who seem to be suggesting that making a tool and/or advertising it even on hackerforums should be considered enough to establish criminal intent.
So yes, cite the indictment, so we can all be clear that Mark Russinovich shouldn’t go to prison if he posts psexec on hackerforums.
He’s not in trouble for posting on Hackforums.
He’s not in trouble for creating a RAT.
He’s in trouble for the contents of the unreleased Skype chats where he communicated and gave customer support to people actively engaging in theft and fraud.
He’s in far bigger trouble over his payment processor than anything relating to the RAT.
Unless Mark Russinovich is going on Hackforums and helping people who ask for assistance with fraud, then this analogy is 100% moronic.
I’m not a lawyer, but I did read the indictment. I don’t see that the case has much to do with the software. It has everything to do with what Huddleston did to aid and encourage others in using his software for illegal purposes. To use the dread gun analogy, it’s okay to manufacture and own a gun, but it’s not okay to knowingly supply the gun to a criminal who intends to use it in a crime. The case may be difficult or easy to prove. I have no idea. But the software itself does not appear to me to be under indictment.
I don’t think any software should be illegal.
Those who drafted and subscribe to the Wassenaar Arrangement would care to disagree – as do I.
Any tool can be used as a weapon.
Huddlestone knew that when he created his toolsets and so I do not buy his subsequent BS. He knew what he was unleashing and that it would inevitably be used by people with nefarious intent.
Having said that, the case against him looks tenuous at best and not likely to succeed in a court of law – as it should probably should not.
How many years have Adobe been enabling crooks. Oh sure they patch, but they (Flash and Reader) have been “the exploit” to breach systems, since Adobe keeps giving their app privileges to do so.
Intent will be a strong suit in this case, and since he did take actions on his own to revoke licenses of suspected criminals prior to being charged, he has that on his side.
It’s not like he’s hacking into millions of computers and stealing data like the *** and *** – which are not companies, with apparently no limits of any kind (financial, legal or moral).
If anybody is interested in additional court documents, I have been posting them on a tribute website: https://www.aeonhack.com
Interesting – Allison and I worked at a security company that shall be not named a couple years back. Very cool she’s quoted here.
Yup, interesting as usual. Interesting auto arguments. So a uber driver could be held for bank robbery? Or a taxi driver? If the crook, used them?
But the use of a tool is up to the owner, not the creator. Otherwise why is compact, not liable? Or the currant owner of assembly language? Both are way down the line but?
Still a lot of ifs. If he can’t show he marketed his software to anyone BUT hackers, that will be all your average juror will hear. If he can’t show that his software was in fact being purchased and used for legitimate reasons, he isn’t going to convince anyone. If I put a cigarette machine in a Jr High bathroom, I can’t really argue that they weren’t my intended target. (There Brian, now you have tobacco thrown into the mix)
The standard for guilt ought to be higher than reckless marketing.
The indictment cites specific conversations that Huddleston had, strongly suggesting (even establishing) that he was aware of criminal usage, and collaborated by failing to act. That would be a good standard of guilt.
But the functionality of the tool, where he advertised or posted, in and of themselves should be considered irrelevant. Otherwise, there’s a serious danger that criminal prosecution could spread to more innocuous, innocent and productive actors and activities.
If you only sell something to on a hacker forum, and no where else then you will have a hard time making a case that you aren’t complicit or innocent.
It’s like the guy got advice from some stoner buddy. “Yeah if you give the prostitute the money in a birthday card, they can’t arrest you. If you just sell but don’t use the tool, they won’t arrest you.”
I guess I’ve been in this business too long and seen way too many people get popped because they thought they were untouchable to believe this guys.
So, should we arrest MS devs for Powershell?
Yes, but only for making it slow to load.
There are two issues: speech (the software) and action (the conspiracy).
All the analogies to guns, cars, etc. are missing the second issue.
From what I see, the government is not going to win anything based on speech, but they have lot of evidence of action. I’m betting the government has a good chance of winning this conspiracy case.
its so complex story in juridical view point.
Will the prosecution begin its case with a clip of Claude Rains from ‘Casablanca?’
https://www.youtube.com/watch?v=SjbPi00k_ME
Will i be criminal if someone use my pc and ip adresss?
And did this guy left his passport beside his computer?
The question is how they proof it was him ??
To prosucute someone you need alot proof and evidence and you must be sure you can connect the person with internet activity.
no names on the internet,and did he let send funds directly to his
name ? If so then he can only blame himself coz of his stupidty !!
people get caught if they personalize themselfes with the crime.
i just dont undestood why his suspected just coz his ip adress been used – ? –