Skimming devices that crooks install inside fuel station gas pumps frequently rely on an embedded Bluetooth component allowing thieves to collect stolen credit card data from the pumps wirelessly with any mobile device. The downside of this approach is that Bluetooth-based skimmers can be detected by anyone else with a mobile device. Now, investigators in the New York say they are starting to see pump skimmers that use cannibalized cell phone components to send stolen card data via text message.
Skimmers that transmit stolen card data wirelessly via GSM text messages and other mobile-based communications methods are not new; they have been present — if not prevalent — in ATM skimming devices for ages.
But this is the first instance KrebsOnSecurity is aware of in which such SMS skimmers have been found inside gas pumps, and that matches the experience of several states hardest hit by pump skimming activity.
The beauty of the GSM-based skimmer is that it can transmit stolen card data wirelessly via text message, meaning thieves can receive real-time transmissions of the card data anywhere in the world — never needing to return to the scene of the crime. That data can then be turned into counterfeit physical copies of the cards.
Here’s a look at a new skimmer pulled from compromised gas pumps at three different filling stations in New York this month. Like other pump skimmers, this device was hooked up to the pump’s internal power, allowing it to operate indefinitely without relying on batteries.

A GSM-based card skimmer found embedded in a gas pump in the northeastern United States.
It may be difficult to see from the picture above, but the skimmer includes a GSM-based device with a SIM card produced by cellular operator T-Mobile. The image below shows the other side of the pump skimmer, with the SIM card visible in the upper right corner of the circuitboard:
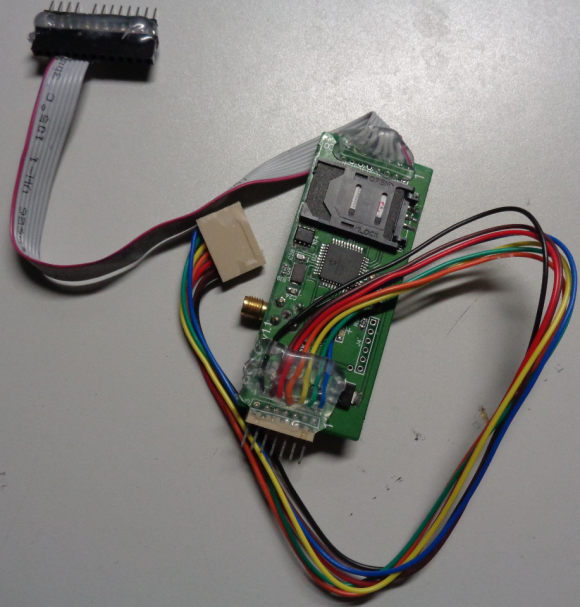
The reverse side of this GSM-based pump skimmer shows a SIM card from T-Mobile.
It’s not clear what type of mobile device was used in this skimmer, and the police officer who shared these images with KrebsOnSecurity said the forensic analysis of the device was ongoing.
Here’s a close-up of the area around the SIM card:
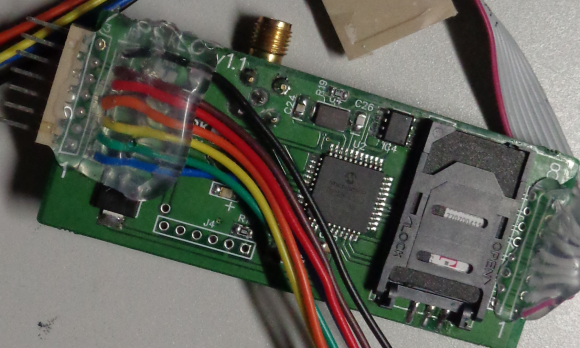
The officer, who shared these photos on condition of anonymity, said this was thought to be the first time fraud investigators in New York had ever encountered a GSM-based pump skimmer.
Skimmers used at all three New York filling stations impacted by the scheme included T-Mobile SIM cards, but the investigator said analysis so far showed the cards held no other data other than the SIM’s card’s unique serial number (ICCID).
KrebsOnSecurity reached out to weights and measures officials in several states most heavily hit by pump skimming activity, including Arizona, California and Florida.
Officials in all three states said they’ve yet to find a GSM-based skimmer attached to any of their pumps.
Skimmers at the pump are most often the work of organized crime rings that traffic in everything from stolen credit and debit cards to the wholesale theft and commercial resale of fuel — in some cases from (and back to) the very fuel stations that have been compromised with the gang’s skimming devices.
Investigators say skimming gangs typically gain access to station pumps by using a handful of master keys that still open a great many pumps in use today. In a common scenario, one person will distract the station attendant as fuel thieves pull up alongside the pump in a van with doors that obscure the machine on both sides. For an in-depth look at the work on one fuel-theft gang working out of San Diego, check out this piece.
There are generally no outward signs when a pump has been compromised by a skimmer, but a study KrebsOnSecurity published last year about a surge in pump skimming activity in Arizona suggests that skimmer gangs can spot the signs of a good mark.
Fraud patterns show fuel theft gangs tend to target stations that are close to major highway arteries; those with older pumps; and those without security cameras, and/or a regular schedule for inspecting security tape placed on the pumps.
Many filling stations are upgrading their pumps to include more physical security — such as custom locks and security cameras. In addition, newer pumps can accommodate more secure chip-based payment cards that are already in use by all other G20 nations.
But these upgrades are disruptive and expensive, and some stations are taking advantage of recent moves by Visa to delay adding much-needed security improvements, such as chip-capable readers.
Until late 2016, fuel station owners in the United States had until October 1, 2017 to install chip-capable readers at their pumps. Under previous Visa rules, station owners that didn’t have chip-ready readers in place by then would have been on the hook to absorb 100 percent of the costs of fraud associated with transactions in which the customer presented a chip-based card yet was not asked or able to dip the chip (currently, card-issuing banks and consumers eat most of the fraud costs from fuel skimming).
But in December 2016, Visa delayed the requirements, saying fuel station owners would now have until October 1, 2020 to meet the liability shift deadline.
The best advice one can give to avoid pump skimmers is to frequent stations that appear to place an emphasis on physical security. More importantly, some pump skimming devices are capable of stealing debit card PINs as well, so it’s good idea to avoid paying with a debit card at the pump.
Armed with your PIN and debit card data, thieves can clone the card and pull money out of your account at an ATM. Having your checking account emptied of cash while your bank sorts out the situation can be a huge hassle and create secondary problems (bounced checks, for instance).




Nice photos of the skimming device
“Make me happy I have an electric vehicle,” he said smugly.
So how do you pay for the quick-charge at an electric charging station when you’re on the road? Electric vehicles don’t avoid this problem and won’t in the future when there are more electric charging stations.
Also, it seems someone doesn’t like these articles being posted by Brian. There seems to be an attack in progress. I couldn’t post a comment for several minutes.
Would it be effective practice to pay only inside the station, and only at stations which will process chip credit cards? Which gas retail chains require chip readers?
Paying in cash avoids the problem in the first place plus you are not “tracked” with cash. Privacy and security are two sides of the same coin.
Gary
Yes…and at the same time we are admonished by various governments for using the “legal tender”. Curious, isn’t it?
And by paying with cash you are literally giving up security as there is no security in paying with cash. With cards you have it.
How is there no security paying with cash?
Did you ever bring gas back to a gas station? and even if you did, you have a receipt.
I’ve never been mugged, but I have had to replace a CC that was negated due to a business. I carry an average of $300 so I don’t run out during the week. It’s the same as carrying $40, 30 years ago lol :(….
“Did you ever bring gas back to a gas station?” this is gold
Because the person who holds the cash has the power. If there’s no record of the transaction, guess what, you’re SOL. It’s also up to the seller to give a refund, they’re under no legal obligation to do so here in the US. Remember, caveat emptor.
Getting your wallet stolen or lost has the same consequence.
Cards have fraud limits, so you’re out a small amount (typically none if it’s through no fault of your own).
This is an old, tired argument that has its roots from the early overly paranoid types.
Not good OpSec – you just told the Krebs readership that you normally carry $300 in cold hard cash. Tell me, are you on vacation right now?
There used to be a problem with petrol station attendants in the UK pocketing cash and claiming people had driven away without paying (bilking). Paying by card avoids that problem without having to demand a receipt.
So someone with a key, has to place this device? A thirty second job. But now, we don’t have to stay within the 600 foot range. Makes it more interesting. And with this circuitry, it will capture the pin. This appears to be a copy circuit, each tone associated with, a ascii, neat they copy the associated tones, music, and, create a card.
Police have to have a directed warrant to search, so, next complaint, they should leave the device, place a stingray nearby, and interrupt the transmission, and see who comes to repair the device? But after a week of letting it call, trace the call log. It’s got to be a system somewhere.
How do you know that the SIM card isn’t just a means to store the data and easily removed and replaced with a new card to allow offsite downloading without unintalling and reinstalling the skimmer? Do you have knowledge of fraud on the cards on the SIM card that was recovered? Because if not, then it’s highly likely SMS was not involved.
I just have a hard time taking your information at face value, personally knowing first hand that an Oklahoma Officer was misquoted 2 weeks ago in regards to the use of infrared technology on ATM skimmers.
Hello ??
Dont confuse a SIM card with a memory card – the two are totally different.
It is BLATANTLY obvious to anyone with half a brain that you are looking at a cellular device – right down the the gold threaded SMA connector for the antenna. Why would a TECH savvy crook conceal a cellular device inside a pump and then use its SIM card to store data ?
Jeeeez……….
SIM cards can store data such as contacts. Imagine the break in the case because some idiot criminal used his moms old SIM card with his contact info saved to SIM!
While that is certainly a requirement on the checklist for these investigations, it didn’t hold anything in this case: “the investigator said analysis so far showed the cards held no other data other than the SIM’s card’s unique serial number “
SIM cards also only have a storage capacity of maybe half a meg. They only store brief strings of text. As far as using it as a storage medium, that would be highly impractical considering the cost and severe lack of storage.
As much an improvement as chip-reading pumps would be, part of me dreads it if the implementation is as terrible as some of the units I’ve seen in stores. Every now and then I use one that’s so fast as to be almost instantaneous. On the other hand, at a major grocery store chain around here, not only is the machine’s UI itself annoying but the entire process is almost ludicrously slow.
Yes, I noticed that at CostCo the Chip transaction is almost instant and at Stater Bros Market it is very slow.
Really? The US is the ONLY G20 nation to NOT have fully implemented chip cards, everywhere else hasnt really had any major problems. And, the performance of the debit machine etc, is not related to chip or no chip. Its related to the internet connection of the business using it. Fast connection = fast transactions. There is nothing to “dread” about chip cards.
I’m in the weights & measures field and what I tell people to do is pay inside with cash. Even paying inside with a card is risky because those customer credit card readers have had skimmers put on them as well.
Thanks Brian for keeping us up to date on the latest threats. I use a credit card at the pump that sends me a text message for every transaction. Plus following your advice for only using stations that appear to emphasize security.
So? Steal my CC. I’m not liable. Not even for the $50 anymore.
Its not my problem, its the card issuer’s and possibly the vendor’s.
And don’t gimmie that utter BS of “thats what keeps the rates up”. They aren’t going to lower them because of chips. Gonna stay high to pay off all those new readers.
We should have NEVER gone to chip readers. We should have leap frogged the over a decade old technology.
It just moved the fraud from card present to card not present.
I guess you’ve never been on vacation when fraud charges start showing up? Typically that means you need to wait a day or two for a new card to be overnight or 2-Day mailed to you. Not at all convenient if you are on a road trip or traveling vacation.
Of course, following the one-is-none and two-is-one rule, you’d have a backup CC with you just in case.
It’s still a hassle to deal with and itemize all the fraud charges on the statement. Worse still if you have a bunch of accounts tied to that CC number that you now have to update.
I don’t do that. I have a dedicated card for reoccuring CC charges, a few for in person, and one (with BofA ShopSafe) for online purchases. I have a list of where the reoccurring charges at set up at, so if somehow that card did get compromised, I know where to update them. But, the risk of compromise is very low as it doesn’t get used “out and about”.
At BOA’s site: Please note that ShopSafe requires you to have Adobe Flash installed on your computer. Download Adobe Flash
Ugh. Nevermind, then.
This one appears to be created to be used internal to the pump so even if you take the common step of pulling on the credit card scanner you won’t discover the scanner.
I had this happen to me so many times that I stopped paying for gas at any pump. I started going inside the store and giving them the card I wanted to use to pay for gas. It resolved the issue. Yes, it is inconvenience but it worked.
You are correct and I must say we have solved the problem the same way. Concerning inconvenience, there is any when consumers stop to think about it methodically. What is an inconvenience is having to stop and replace cards regularly. Cash is always better in my opinion but when you live in high in the mountains, cash isn’t always accessible.
Oops I meant to say, “there isn’t any inconvenience when consumers stop and think about it…”
thanks
Any details available concerning what type of antenna was used with the devices, and whether it was visible externally? I’m guessing an antenna inside of a sheet metal box wouldn’t work very well.
I’ve started using the Exxon-Mobil Speedpass app to pay at the pump. Along with Samsung Pay, I’m not communicating directly with the pump itself, plus using a tokenized version of my credit card for the payment.
Yep, I use the ExxonMobil Speedpass as well. As the crooks get smarter with technology, we need to use better technology to stay ahead of them. Current phone does not support the Samsung Pay, but I want that next time I upgrade.
We can’t stop criminals from installing skimmers on gas pumps. Not knowing when a skimmer is installed or how long it has been stealing credit/debit card numbers is the real problem. It shouldn’t be the responsibility of the consumer to try to keep their information secure – the gas station owner should be doing everything in their power to protect the financial information of their customers. Unfortunately, gas stations are not held responsible when a skimmer is found on one of their pumps – it should be treated like any other data breach.
Gas Pump Sentry fixes this by immediately alerting the gas station owner, manager and/or employees when a pump is opened so it can be shutdown, inspected and the skimmer removed before it steals a single credit/debit card number.
http://www.GasPumpSentry.com
One of these would be a good starting point for building a device like this: https://www.adafruit.com/product/2637
I’m not suggesting this is where they bought it – they probably have better sources. As a hobbyist, this is one of the places I’d go to build a GMS device like this skimmer.
When a crook installs a skimmer and get credit/debit card data, banks should refund victims, right? That’s what the emv deadline is about, after the deadline, the store where skimmer was found will be responsible for this refund. When cyber crooks install trojans like Citadel on business, banks still responsible to refund the victims?
There is a very low tech solution: pay with cash.
Agreed for home/local use. Taking it one step further, I have an ATM card with a Savings-only Credit Union account. It has typically $40-100 in it, and I can use it at any 7-11 gas station (or any Credit Union) ATM to get cash out for free.
I do that, and then pay with cash. Where I live, paying with cash is cheaper than paying with CC. They offer a “cash discount” that is lower than the CC price of gas.
While I’m pumping gas, I jump on my smartphone and log into my Credit Union website for my normal Checking account and transfer over whatever amount I just pulled out. My accounts are set up such that my Savings-only account is not linked to my normal Checking/Savings account, but my normal Checking/Savings account can transfer funds to it (I can transfer funds to any other account at my Credit Union this way, and do so for my kids, but they can’t take funds).
While I do practice a good check on the ATM and cover my hand when I do the pin, worst case I am out $40-100 in cash from the account, but more importantly my normal Checking account that pays all my bills is never in danger.
However, this is a hassle for road trips. While we try to hit all the Costco gas stations along the way, there are very few on the east side of Oregon that have gas. But when we can’t, we just hit the best stop to maximize are travel:stops ratio and use a “traveling” CC which is used only for trips like this.
T-Mo is pretty much the only way to go in the US for one of those embedded GSM boards. They’ve promised to keep 2G GSM working for data devices till 2020, IIRC, whereas AT&T turned that off everywhere at the end of 2016. I don’t recognize the devices, but I suppose it could have been bought outright or scavenged from a scale, utility meter or even burglar alarm or lo-jack. Someone will certainly have seen one before.
Also, it’s pretty amazing how many industrial devices with locks on them actually use a one-key-fits-all scheme. It seems careless at first, but it is a lot easier to do maintenance when the tech already has the key rather than hoping for the clerk to know where the manager stashed it. If you’re running a business and your mission-critical hardware isn’t working and can’t be fixed because you don’t know where you left the key, you’re gonna call your vendor and yell at them, and vendors don’t like being yelled at.
According to a quick google search both the track 1 and track 2 data is combined less than 130 characters. I also did some research into the availability of LTE chips for this type of platform. While there is an increase in both hardware price and software development cost, the API for SMS appears to be very similar between the 2G and LTE. So I expect this type of fraud execution to become very common in the future.
Looks like just a generic Arduino GSM shield. – https://www.google.ca/search?q=arduino+gsm+shield&oq=arduina+gsm&aqs=chrome.1.69i57j0l5.5215j0j7&sourceid=chrome&ie=UTF-8
Also, theres no reason the techs cant have multiple if not MANY different keys. At install they just have to issue one key to the retailer and one to themselves.
In the photos what is the purpose of the threaded brass fitting attached to the circuit board?Possibly an external antenna connection?Not needed in this scenario? Just curious Read your articles all the time.Thanks
Its just the Antenna connector. Google Arduino GSM shield. They all have one.
“I’m guessing an antenna inside of a sheet metal box wouldn’t work very well.”
A GSM antenna is perfectly working inside a gas pump made of iron. The iron is transparent at the micro-wave frenquencies used for GSM (1.8-1.9 MHz). This is the reason why you can perfectly use a GSM within the cabin of a lift which is usually mainly made of iron or steel (as long as the concrete traversal path isn’t too long).
MHz? I think you meant GHz.
“A GSM antenna is perfectly working inside a gas pump made of iron. The iron is transparent at the micro-wave frenquencies used for GSM (1.8-1.9 MHz).”
As _Dave_ noticed it, I meant 1.8 – 1.9 _GHz_.
Tied to post this last night, but no joy. Trying again…
Ah, sorry, but no. Your understanding of physics and EM is WAY off the mark.
First, you have the units wrong. GSM uses 1.8 to 1.9 GHz (that’s GigaHertz, as in 10^9) or 1800-1900 MHz.
Second, conductive metals like iron and steel are NOT transparent to electromagnetic radiation IF the box is SOLID, i.e. has NO HOLES it its surface.
The reason a cellphone works inside a lift (elevator) is that most cars DO have holes in one or more surfaces, sufficiently large to let the microwaves pass in and out.
Holes don’t have to be very big. We’re talking about 6 inches (15 cm) at those frequencies. But there MUST be HOLES, or NO signal will get in or out of the box.
Seems unlikely that a gas pump housing would have holes that large, so an external antenna IS required. But it can be quite small: 2 to 3 inches (5 to 7 cm).
This “master key” scheme is everywhere. It is old school mentality. Each brand of whatever had one key. I replaced some gate control hardware myself to save some money. Buy one gate keypad box, you now have a key for every box from that manufacturer. It gets worse. To open the gate, you just jumper the right spot.
Regarding buying fuel, I make it a point to buy at Costco. It may be totally false security. My theory is Costco actually pays employees, so they are less likely to allow the pumps to he diddled. Now that I know about the master key, that blows my theory.
Well I still yank the reader to see if it is loose.
Yup, Costco for the gas station fill-up “win” when you can. They take things seriously and have serialize tamper tape and inspect them. I still pull on them anyway (anyone can buy serialized tamper tape, and all it takes is a hot chick to chat up the gas station attendant).
Gary said “This “master key” scheme is everywhere. It is old school mentality. Each brand of whatever had one key. ”
True. Motorola hasn’t changed their trunk-mounted radio key since 1959.
The liability shift does not effect the merchant who facilitate stolen credit cards, only the merchant who accepts stolen credit cards.
Gas stations have very little incentive to upgrade to newer pumps with better security. They will drag out the liability shift for as long as possible.
Under the new liability rules, an “ethically challenged” individual can easily dispute with his card issuer a transaction he made with a chip card at a POS terminal that was not EMV enabled. I work for an organization that is late in converting their POS terminals to chip readers. These kinds of chargebacks are finally spurring them on to complete this migration.
So, where is the “rest of the story”. Did they do one more transaction, find the receiving phone and arrest the criminals? That would end this practice faster than paying by cash.
Gas station pumps must be EMV compliant by October 2017.This is long overdue and will reduce if not eliminate this kind of theft. Better yet will be if chip and pin verification will be required to thwart the use of stolen chip cards. Chip and signature for verification is like what Samuel Goldwyn said about oral agreements – not worth the paper they were written on.
Please re-read the article, as it mentioned this:
“But in December 2016, Visa delayed the requirements, saying fuel station owners would now have until October 1, 2020 to meet the liability shift deadline”
““But in December 2016, Visa delayed the requirements, saying fuel station owners would now have until October 1, 2020 to meet the liability shift deadline””
Yeah, that’s what happened when they came to the realization that the vendors would stop accepting Visa before changing over their infrastructure.
Interesting thing about sim cards. The older csm cards were made from 8 gig cards. 4 gigs for the OS from the maker, and 4 gigs of extra storage. For your apps and photos. I would not doubt there are larger cards now. Autoruns at start are not that hard to cross relate.
Security reached out to weights and measures officials in several states.
Thank you !
I thought I saw a remark from Brian at one point that you’re more likely to get mugged at the ATM than come across a skimmer. Seems to be more risk in losing cash than being on the hook for card fraud. Leave the cash at home and carry some pepper spray, I guess.
With Bluetooth it’s next to impossible to figure out who and when they are getting the data, but they have to be within the vicinity. With text messaging, wouldn’t there be a trail of where the text messages are going? a cell #? Couldn’t authorities tell what cell towers the messages were received from?
I’ve been surprised that the use of SMS text messaging hadn’t already been going on for some time. If I was to be doing this, I don’t think I would want to every show back up at the scene of the crime I’ve been committing.
As for tracking down the receiving side, this could be more difficult that you would expect. First, you don’t need a cell phone to retrieve an SMS message. Also, you could change the SendTO on the fly by just texting the unit at the pump which you could easily spoof making it very difficult to track, if even possible.
Security was never implemented into SMS as it was originally a method to signal carrier equipment and provide metric information for cellular radios. As we have moved to digital signaling, carriers realized they could profit by allowing end-users access to this tiny bit of the constant communications of the device to send short text messages amongst themselves. By the time it took off, security was/is to late.