Equifax, one of the “big-three” U.S. credit bureaus, said today a data breach at the company may have affected 143 million Americans, jeopardizing consumer Social Security numbers, birth dates, addresses and some driver’s license numbers.
In a press release today, Equifax [NYSE:EFX] said it discovered the “unauthorized access” on July 29, after which it hired an outside forensics firm to investigate. Equifax said the investigation is still ongoing, but that the breach also jeopardized credit card numbers for roughly 209,000 U.S. consumers and “certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers.”
In addition, the company said it identified unauthorized access to “limited personal information for certain UK and Canadian residents,” and that it would work with regulators in those countries to determine next steps.
“This is clearly a disappointing event for our company, and one that strikes at the heart of who we are and what we do. I apologize to consumers and our business customers for the concern and frustration this causes,” said Chairman and Chief Executive Officer Richard F. Smith in a statement released to the media, along with a video message. “We pride ourselves on being a leader in managing and protecting data, and we are conducting a thorough review of our overall security operations.”
Equifax said the attackers were able to break into the company’s systems by exploiting an application vulnerability to gain access to certain files. It did not say which application or which vulnerability was the source of the breach.
Equifax has set up a Web site — https://www.equifaxsecurity2017.com — that anyone concerned can visit to see if they may be impacted by the breach. The site also lets consumers enroll in TrustedID Premier, a 3-bureau credit monitoring service (Equifax, Experian and Trans Union) which also is operated by Equifax.
According to Equifax, when you begin, you will be asked to provide your last name and the last six digits of your Social Security number. Based on that information, you will receive a message indicating whether your personal information may have been impacted by this incident. Regardless of whether your information may have been impacted, the company says it will provide everyone the option to enroll in TrustedID Premier. The offer ends Nov. 21, 2017.
ANALYSIS
At time of publication, the Trustedid.com site Equifax is promoting for free credit monitoring services was only intermittently available, likely because of the high volume of traffic following today’s announcement.
As many readers here have shared in the comments already, the site Equifax has available for people to see whether they were impacted by the breach may not actually tell you whether you were affected. When I entered the last six digits of my SSN and my last name, the site threw a “system unavailable” page, asking me to try again later.
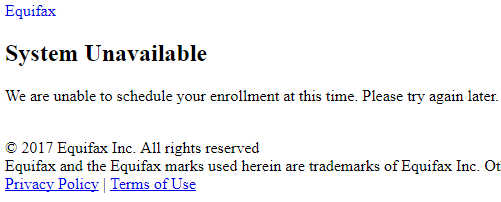
When I tried again later, I received a notice stating my enrollment date for TrustedID Premier is Sept. 13, 2017, but it asked me to return again on or after that date to enroll. The message implied but didn’t say I was impacted.
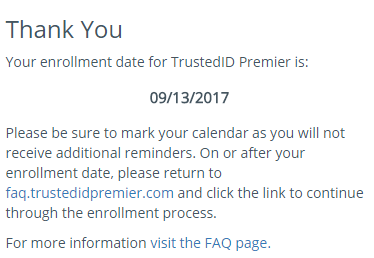
Maybe Equifax simply isn’t ready to handle everyone in America asking for credit protection all at once, but this could be seen as a ploy by the company assuming that many people simply won’t return again after news of the breach slips off of the front page.
Update, 11:40 p.m. ET: At a reader’s suggestion, I used a made-up last name and the last six digits of my Social Security number: The system returned the same response: Come back on Sept. 13. It’s difficult to tell if the site is just broken or if there is something more sinister going on here.
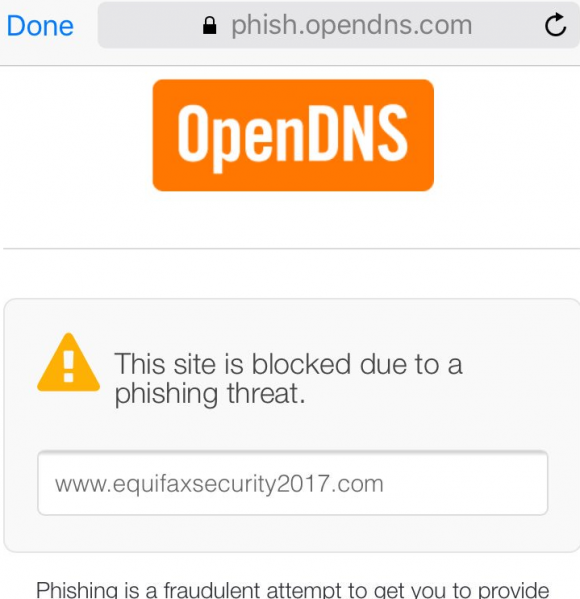
Also, perhaps because the site is so new and/or because there was a problem with one of the site’s SSL certificates, some browsers may be throwing a cert error when the site tries to load. This is the message that OpenDNS users are seeing right now if they try to visit www.equifaxsecurity2017.com:
Original story:
Several readers who have taken my advice and placed security freezes (also called a credit freeze) on their file with Equifax have written in asking whether this intrusion means cybercriminals could also be in possession of the unique PIN code needed to lift the freeze.
So far, the answer seems to be “no.” Equifax was clear that its investigation is ongoing. However, in a FAQ about the breach, Equifax said it has found no evidence to date of any unauthorized activity on the company’s core consumer or commercial credit reporting databases.
I have long urged consumers to assume that all of the personal information jeopardized in this breach is already compromised and for sale many times over in the cybercrime underground (because it demonstrably is for a significant portion of Americans). One step in acting on that assumption is placing a credit freeze on one’s file with the three major credit bureaus and with Innovis — a fourth bureau which runs credit checks for many businesses but is not as widely known as the big three.
More information on the difference between credit monitoring and a security freeze (and why consumers should take full advantage of both) can be found in this story.
I have made no secret of my disdain for the practice of companies offering credit monitoring in the wake of a data breach — especially in cases where the breach only involves credit card accounts, since credit monitoring services typically only look for new account fraud and do little or nothing to prevent fraud on existing consumer credit accounts.
Credit monitoring services rarely prevent identity thieves from stealing your identity. The most you can hope for from these services is that they will alert you as soon as someone does steal your identity. Also, the services can be useful in helping victims recover from ID theft.
My advice: Sign up for credit monitoring if you can, and then freeze your credit files at the major credit bureaus (it is generally not possible to sign up for credit monitoring services after a freeze is in place). Again, advice for how to file a freeze is available here.
The fact that the breached entity (Equifax) is offering to sign consumers up for its own identity protection services strikes me as pretty rich. Typically, the way these arrangements work is the credit monitoring is free for a period of time, and then consumers are pitched on purchasing additional protection when their free coverage expires. In the case of this offering, consumers are eligible for the free service for one year.
That the intruders were able to access such a large amount of sensitive consumer data via a vulnerability in the company’s Web site suggests Equifax may have fallen behind in applying security updates to its Internet-facing Web applications. Although the attackers could have exploited an unknown flaw in those applications, I would fully expect Equifax to highlight this fact if it were true — if for no other reason than doing so might make them less culpable and appear as though this was a crime which could have been perpetrated against any company running said Web applications.
This is hardly the first time Equifax or another major credit bureau has experienced a breach impacting a significant number of Americans. In May, KrebsOnSecurity reported that fraudsters exploited lax security at Equifax’s TALX payroll division, which provides online payroll, HR and tax services.
In 2015, a breach at Experian jeopardized the personal data on at least 15 million consumers. Experian also for several months granted access to its databases to a Vietnamese man posing as a private investigator in the U.S. In reality, the guy was running an identity theft service that let cyber thieves look up personal and financial data on more than 200 million Americans.
My take on this: The credit bureaus — which make piles of money by compiling incredibly detailed dossiers on consumers and selling that information to marketers — have for the most part shown themselves to be terrible stewards of very sensitive data, and are long overdue for more oversight from regulators and lawmakers.
In a statement released this evening, Sen. Mark Warner (D-Va.) called the Equifax breach “profoundly troubling.”
“While many have perhaps become accustomed to hearing of a new data breach every few weeks, the scope of this breach – involving Social Security Numbers, birth dates, addresses, and credit card numbers of nearly half the U.S. population – raises serious questions about whether Congress should not only create a uniform data breach notification standard, but also whether Congress needs to rethink data protection policies, so that enterprises such as Equifax have fewer incentives to collect large, centralized sets of highly sensitive data like SSNs and credit card information on millions of Americans,” said Warner, who heads the bipartisan Senate Cybersecurity Caucus. “It is no exaggeration to suggest that a breach such as this – exposing highly sensitive personal and financial information central for identity management and access to credit– represents a real threat to the economic security of Americans.”
It’s unclear why Web applications tied to so much sensitive consumer data were left unpatched, but a lack of security leadership at Equifax may have been a contributing factor. Until very recently, the company was searching for someone to fill the role of vice president of cybersecurity, which according to Equifax is akin to the role of a chief information security officer (CISO).
The company appears to have announced the breach after the close of the stock market on Thursday. Shares of Equifax closed trading on the NSYE at $142.72, up almost one percent over Wednesday’s price.
This is a developing story. Updates will be added as needed.
Further reading:
Are Credit Monitoring Services Really Worth It?
Report: Everyone Should Get a Security Freeze
How I Learned to Stop Worrying and Embrace the Security Freeze
Update: 8:38 p.m. ET: Added description of my experience trying to sign up for Equifax’s credit monitoring offer (it didn’t work and it may be completely broken).




I got the deferred message earlier, then I went back just now and got a message saying I was impacted.
For those that got a date to come back and check, I would check again, my message changed to impacted after a couple of hours.
This data breach is an outrage! Somebody at Equifax needs to be criminally prosecuted for gross negligence. If there is a class action lawsuit in the works, please post details here.
Get this, in CA we have to pay $10 to each company to put a freeze on our accts. Equifax waved this. But with Transunion and Experian, I have to pay them to freeze the files they’ve accumulated on me without my consent. Seems like the biggest scam perpetrated on the American people in a long time.
Clas-action lawsuit anyone?
I’ve always thought credit bureaus were a scam!! They get all our info without our consent!
Rick Smith should be booted without any compensation!!
Equifax has had a revolving door in their information security team for the past 5 years and have seen many of their long-time best and brightest leave. It’s been long whispered how bad information security has become there and now we all see just how bad it is.
The site claimed to be where one would check to see if one’s private info has been breached has ssl security with NO OWNERSHIP INFORMATION. One would think that its sucky security would make it learn a lesson. Please check on the sucureness of this site, Brian!
This is like a sick joke to see if the panicking populace will run and put in their secret information to a company already proven not to be trusted.
A sad twist of ongoing mistrust:
The so-called website to check to see if one’s secure info has leaked is itself shown to have an ssl padlock providing zero identity information! Freakin’ unbelievable.
Equifax has already shown itself to be incompetent bumblers, but this takes the cake. Please investigate the ongoing incompetence, Brian. This is just the tip of the iceburg.
Dealing with the small business division makes one feel like competence would be an unreachable dream.
I checked a few minutes ago and they said I was not impacted. But…do I believe them? Not so sure. Most businesses around here use Experion so maybe I will luck out.
I agree with everything said here. We did not give them permission to gather this information even that was a dupe. and now the personal information has been given away by what seems like a careless no money invested in security on their part.
I went to the site followed all sign ups and I too was given a date to return? They are not even sending emails to the people they have impacted! Ok Now what happens if my ssn falls in the hands of s terrorist? Now he or she has become me! I am all for a lawsuit. We should be compensated new cards,new scores,new ssn.
I to am very angry and a free monitor for the future is not enough!
just entered dummy information into the sham equifaxsecurity2017.com website. It put a check next to each, the last name and the six digits…
Then it returned that:
Thank You
Your enrollment date for TrustedID Premier is:
09/13/2017
Please be sure to mark your calendar as you will not receive additional reminders. On or after your enrollment date, please return to faq.trustedidpremier.com and click the link to continue through the enrollment process.
I’m so comforted!
Thank you. I found the same thing after reading your comment. I just updated the story with that observation.
So the site was hacked in May, they discovered at the end of July, and I am not notified until I read about it here, 5 months later.
I am angry that these companies are storing and profiting from data I did not share with them or give them permission to use. Now I am placed at risk and all they want to do is offer free credit monitoring for which I suspect they have struck a deal and pay little or nothing to provide.
I do not have formal education in computer security, but even I can come up with several ways that a company can safeguard and/or be alerted to a breech or unauthorized use of data. Companies think they are smart, but the continued number of breeches confirms my feelings that most companies are stupid. And don’t get me started on all the breeches that are never detected…
This stinks. 3 top Equifax executives sold shares of the company days after July 29 cyber breach was discovered by the company, per SEC filings https://www.cnbc.com/2017/09/07/equifax-cyberattack-three-executives-sold-shares-worth-nearly-2-million-days-after-data-breach.html
Perhaps Equifax et al should be required to provide LIFETIME credit monitoring since this may affect consumers for a lifetime. Somehow it has to be made so expensive and onerous for these companies to get hacked, that they will finally take security than they obviously don’t. Read the clueless statement by Equifax’s CEO – really?!
many sources are now pointing out potential insider trading related to the breach
http://www.marketwatch.com/story/equifax-executives-sold-stock-after-data-breach-before-informing-public-2017-09-07
https://seekingalpha.com/article/4105152-equifax-sell-worsens
Brian, Thanks for this alert, may not have seen otherwise. Your emails are invaluable – thanks for all you do!
May I ask? Have we reached the point of absurdity yet?
Does there remain even the flimsiest sliver of credibility in corporate assurances that the public’s personal data is secure?
This may be a problem that requires some fresh thinking, as the game of cat and mouse between security measures and hacking counter-measures is obviously not going well.
I enrolled and it said i am not affected and gave me an enrollment date of 9/14. However, I also enrolled my husbands and his did noy specify it just gave him an enrollmebt date. Also, I enrolled before his and his date is earlier than mine which is 9/13
Ug.
I tried the link in this article to https:/equifaxsecurity2017.com it triggers firefox’s “Insecure Connection” page. Error is “SEC_ERROR_UNKNOWN_ISSUER”. So, bogus cert.
Next I went to the equifax site and tried the link in the red “Equifax Security Incident” alert near the top of the page. That points to unencrypted http://equifaxsecurity2017.com. THAT tripped my DNS service’s filtering and gave me a page alerting me that it’s blocking the site due to a phishing threat.
So, I can imagine what’s really going on if the (real) equifax equifaxsecurity2017.com site is actually offline…
I tried putting in dummy data (with a definitely fake last name), and it said I wasn’t affected, but could sign up for their credit monitoring service anyway. Depending on what name you put in, this could either indicate that their system is broken, OR that so many people are affected that randomly guessing details will result in a hit.
How about it Equifax has to pay for all 143 million to get new Social Security and driver’s license numbers?
I got notice to return back on the 13th and my wife on the 11th (I check hers after I checked mine).
Just had a friend check his and he got an update that he was not impacted.
I am guessing that if you did get a date you were impacted.
So am I supposed to believe that this highly sensitive data was unencrypted and was just sitting on a drive somewhere to be read and copied by anyone? This is incredible. This is the OPM hack all over again. Encrypt FFS!
“At time of publication, the Trustedid.com site Experian is promoting for free credit monitoring services”
s/Experian/Equifax/ here I think.
problem: equifax is hacked, revealing personal information of millions of people.
solution: ask millions of people to reveal personal information to equifax.
my better idea: every time someone pays equifax for my personal information, I get half the money…
that video is a joke. the guy knows he’s out of a job…
Here’s what I’ve concluded after trying earlier with both myself and my wife trying as well:
1. If you get ‘Thank You – Your enrollment date for TrustedID Premier is:… ‘ – then that must mean your data has been compromised. (What I received)
2. If you get ‘Thank You – Based on the information provided, we believe that your personal information was not impacted by this incident.’ (What my wife received) You’re in the clear — well, until they determine that the event was more significant or something.
Both of these answers return consistently for us.
+1 to the lifetime credit monitoring – more than that, lifetime free locking with secondary auth or something to unlock. Somehow I knew one of the credit bureaus was the big hit someone was waiting to score. I’m not sure I remember a time where CC + SSL + D/L + DOB + Address were all compromised in the same breach — and with even a subset of those items, someone can pull CCs in your name, auto credit, you name it.
I bet this causes serious changes in how companies check/authorize credit in the first place. The ‘credit check’ as we know it is now useless and will open up companies to serious liabilities.
Thank you for the good reporting! I love this blog!!!
This time the customary apologies and statements of earnest intent (“we take the security of your data very seriously”) are not enough. Heads should roll in Atlanta, starting with Smith at the top.
Agreed!
I imagine who ever has our personal information is calling all investment companies and getting access to retirement accounts. Even I have been given access to my account with my SSN and some other basic information by talking with an investment advisor who are always very helpful.
I just don’t get why companies don’t invest in competent security engineers? Yes we are expensive, and rightly so, but when you compare the cost of a breach against the cost of security org that knows WTF it is doing it seems to be a small price to pay.
BTW: Senior mgmt seldom knows how to evaluate the competency of a security engineer.
Why isn’t Equifax responsible for notifying those whose data was impacted by the breach? I’m not comfortable logging six SSN digits into a system that’s quite likely not as secure as it should be.
There doesn’t seem to be a way for a UK citizen (or Canadian?) to check if they are affected as we don’t have Social Security numbers.