Equifax, one of the “big-three” U.S. credit bureaus, said today a data breach at the company may have affected 143 million Americans, jeopardizing consumer Social Security numbers, birth dates, addresses and some driver’s license numbers.
In a press release today, Equifax [NYSE:EFX] said it discovered the “unauthorized access” on July 29, after which it hired an outside forensics firm to investigate. Equifax said the investigation is still ongoing, but that the breach also jeopardized credit card numbers for roughly 209,000 U.S. consumers and “certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers.”
In addition, the company said it identified unauthorized access to “limited personal information for certain UK and Canadian residents,” and that it would work with regulators in those countries to determine next steps.
“This is clearly a disappointing event for our company, and one that strikes at the heart of who we are and what we do. I apologize to consumers and our business customers for the concern and frustration this causes,” said Chairman and Chief Executive Officer Richard F. Smith in a statement released to the media, along with a video message. “We pride ourselves on being a leader in managing and protecting data, and we are conducting a thorough review of our overall security operations.”
Equifax said the attackers were able to break into the company’s systems by exploiting an application vulnerability to gain access to certain files. It did not say which application or which vulnerability was the source of the breach.
Equifax has set up a Web site — https://www.equifaxsecurity2017.com — that anyone concerned can visit to see if they may be impacted by the breach. The site also lets consumers enroll in TrustedID Premier, a 3-bureau credit monitoring service (Equifax, Experian and Trans Union) which also is operated by Equifax.
According to Equifax, when you begin, you will be asked to provide your last name and the last six digits of your Social Security number. Based on that information, you will receive a message indicating whether your personal information may have been impacted by this incident. Regardless of whether your information may have been impacted, the company says it will provide everyone the option to enroll in TrustedID Premier. The offer ends Nov. 21, 2017.
ANALYSIS
At time of publication, the Trustedid.com site Equifax is promoting for free credit monitoring services was only intermittently available, likely because of the high volume of traffic following today’s announcement.
As many readers here have shared in the comments already, the site Equifax has available for people to see whether they were impacted by the breach may not actually tell you whether you were affected. When I entered the last six digits of my SSN and my last name, the site threw a “system unavailable” page, asking me to try again later.
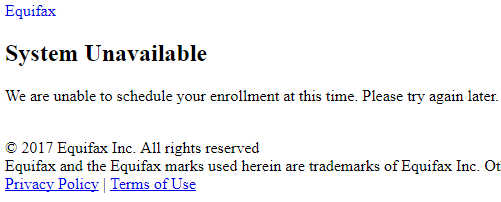
When I tried again later, I received a notice stating my enrollment date for TrustedID Premier is Sept. 13, 2017, but it asked me to return again on or after that date to enroll. The message implied but didn’t say I was impacted.
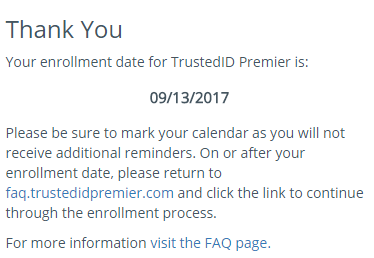
Maybe Equifax simply isn’t ready to handle everyone in America asking for credit protection all at once, but this could be seen as a ploy by the company assuming that many people simply won’t return again after news of the breach slips off of the front page.
Update, 11:40 p.m. ET: At a reader’s suggestion, I used a made-up last name and the last six digits of my Social Security number: The system returned the same response: Come back on Sept. 13. It’s difficult to tell if the site is just broken or if there is something more sinister going on here.
Also, perhaps because the site is so new and/or because there was a problem with one of the site’s SSL certificates, some browsers may be throwing a cert error when the site tries to load. This is the message that OpenDNS users are seeing right now if they try to visit www.equifaxsecurity2017.com:
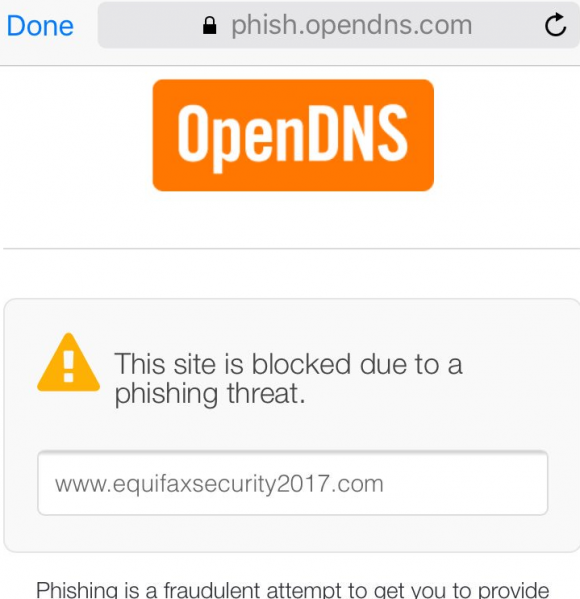
Original story:
Several readers who have taken my advice and placed security freezes (also called a credit freeze) on their file with Equifax have written in asking whether this intrusion means cybercriminals could also be in possession of the unique PIN code needed to lift the freeze.
So far, the answer seems to be “no.” Equifax was clear that its investigation is ongoing. However, in a FAQ about the breach, Equifax said it has found no evidence to date of any unauthorized activity on the company’s core consumer or commercial credit reporting databases.
I have long urged consumers to assume that all of the personal information jeopardized in this breach is already compromised and for sale many times over in the cybercrime underground (because it demonstrably is for a significant portion of Americans). One step in acting on that assumption is placing a credit freeze on one’s file with the three major credit bureaus and with Innovis — a fourth bureau which runs credit checks for many businesses but is not as widely known as the big three.
More information on the difference between credit monitoring and a security freeze (and why consumers should take full advantage of both) can be found in this story.
I have made no secret of my disdain for the practice of companies offering credit monitoring in the wake of a data breach — especially in cases where the breach only involves credit card accounts, since credit monitoring services typically only look for new account fraud and do little or nothing to prevent fraud on existing consumer credit accounts.
Credit monitoring services rarely prevent identity thieves from stealing your identity. The most you can hope for from these services is that they will alert you as soon as someone does steal your identity. Also, the services can be useful in helping victims recover from ID theft.
My advice: Sign up for credit monitoring if you can, and then freeze your credit files at the major credit bureaus (it is generally not possible to sign up for credit monitoring services after a freeze is in place). Again, advice for how to file a freeze is available here.
The fact that the breached entity (Equifax) is offering to sign consumers up for its own identity protection services strikes me as pretty rich. Typically, the way these arrangements work is the credit monitoring is free for a period of time, and then consumers are pitched on purchasing additional protection when their free coverage expires. In the case of this offering, consumers are eligible for the free service for one year.
That the intruders were able to access such a large amount of sensitive consumer data via a vulnerability in the company’s Web site suggests Equifax may have fallen behind in applying security updates to its Internet-facing Web applications. Although the attackers could have exploited an unknown flaw in those applications, I would fully expect Equifax to highlight this fact if it were true — if for no other reason than doing so might make them less culpable and appear as though this was a crime which could have been perpetrated against any company running said Web applications.
This is hardly the first time Equifax or another major credit bureau has experienced a breach impacting a significant number of Americans. In May, KrebsOnSecurity reported that fraudsters exploited lax security at Equifax’s TALX payroll division, which provides online payroll, HR and tax services.
In 2015, a breach at Experian jeopardized the personal data on at least 15 million consumers. Experian also for several months granted access to its databases to a Vietnamese man posing as a private investigator in the U.S. In reality, the guy was running an identity theft service that let cyber thieves look up personal and financial data on more than 200 million Americans.
My take on this: The credit bureaus — which make piles of money by compiling incredibly detailed dossiers on consumers and selling that information to marketers — have for the most part shown themselves to be terrible stewards of very sensitive data, and are long overdue for more oversight from regulators and lawmakers.
In a statement released this evening, Sen. Mark Warner (D-Va.) called the Equifax breach “profoundly troubling.”
“While many have perhaps become accustomed to hearing of a new data breach every few weeks, the scope of this breach – involving Social Security Numbers, birth dates, addresses, and credit card numbers of nearly half the U.S. population – raises serious questions about whether Congress should not only create a uniform data breach notification standard, but also whether Congress needs to rethink data protection policies, so that enterprises such as Equifax have fewer incentives to collect large, centralized sets of highly sensitive data like SSNs and credit card information on millions of Americans,” said Warner, who heads the bipartisan Senate Cybersecurity Caucus. “It is no exaggeration to suggest that a breach such as this – exposing highly sensitive personal and financial information central for identity management and access to credit– represents a real threat to the economic security of Americans.”
It’s unclear why Web applications tied to so much sensitive consumer data were left unpatched, but a lack of security leadership at Equifax may have been a contributing factor. Until very recently, the company was searching for someone to fill the role of vice president of cybersecurity, which according to Equifax is akin to the role of a chief information security officer (CISO).
The company appears to have announced the breach after the close of the stock market on Thursday. Shares of Equifax closed trading on the NSYE at $142.72, up almost one percent over Wednesday’s price.
This is a developing story. Updates will be added as needed.
Further reading:
Are Credit Monitoring Services Really Worth It?
Report: Everyone Should Get a Security Freeze
How I Learned to Stop Worrying and Embrace the Security Freeze
Update: 8:38 p.m. ET: Added description of my experience trying to sign up for Equifax’s credit monitoring offer (it didn’t work and it may be completely broken).




Hi Brian. Do you have a source for the “143M *Americans*” claim in the title? The Equifax release just mentions US consumers, but your post seems to suggest tue breach affects US *citizens* only.
Plenty of other news sources seem to have taken a similar shortcut (WaPo, NY Times to a lesser extent, etc) from “US Consumer” to “American”, but I can’t seem to find an actual statement from Equifax to justify it.
Are foreigners with SSNs really not affected by the breach, or did you just forget about them? (Foreigners need an SSN to get paid, just like Americans, so many students and most green card holders have one; I can’t find precise figures, but estimates are in the 20-30M people range)
It’s not just amercian’s as I’m British, living in the US and my wife and I both got ” you may be affected” notifications when checking.
It’s kind of weird that you need the 6 digits rather than the last 4 numbers to check.
My wife’s check back and notify date was 9/13 and mine was 9/14 so it looks like they are just spreading the signups randomly.
Its stupid that the company can get away with just offering credit monitoring services that they already provide (and this is not the first time that this has happened).
Maybe a better solution would be for the company to be forced to provide credit monitoring provided by the *other* credit monitoring services so they take the financial hit and their competitors gain. This may provide a bit more incentive to look after our data properly.
Interestingly I have always received notifications from Lastpass that my data has been leaked at least a day before I get information from the credit monitoring services do (that were provided to me by previous breach problems).
From their FAQ’s
“We identified a cybersecurity incident potentially impacting approximately 143 million U.S. consumers. Criminals exploited a U.S. website application vulnerability to gain access to certain files. We discovered the unauthorized access and acted immediately to stop the intrusion. We promptly engaged a leading, independent cybersecurity firm that has been conducting a comprehensive forensic review to determine the scope of the intrusion, including the specific data impacted. We also reported the criminal access to law enforcement and continue to work with authorities.”
Shawn: Yes, US Consumers. That includes visa holders and legal residents with green cards, who have SSNs and use credit card like everyone else. This article is just sloppily equating US Consumers and Americans.
In other words, I was criticizing Brian’s reporting. The release doesn’t say Americans, but his article does – it’s not just him, of course (WaPo did the same), but it’s not up to the strict standards that we’ve come to expect and love for his reporting.
If companies were forced to pay each victim of a data breach $1 per day from the beginning of the breach until it was fixed and the victims notified, then companies would have an incentive to do security well and the victims get some concrete restitution.
Lifetime enrollment in identity theft service should be the result not 1 yr. My exposure to this problem is for a lifetime, not 1 year.
You are 100% correct. To the extent that criminals will set reminders for when to go back and use the data. They mine it now, set a timer for say 12-18 months, let it sit dormant, then start using it after the protection expires. Especially when companies like this announce publicly that it is for 1 year. They pretty much just told the criminals how long to wait before attempting to use the stolen data.
Good thing that you’ll probably be part of another breach for which you’re offered free credit monitoring in that time.
my thoughts exactly. coming off OPM breach right into this one.
Similar happened with Target a few years back… It’s as if there is no hope for a better way. In the Target scenario, they provided protection through Experian to those affected by the breach. Then, low and behold, 4-5 months later, Experian was breached!
Yup. A few days back I got an email saying that the Experian monitoring through ProtectMyID, which was the result of the Target breach, is ending…
I since then have put a freeze with all 4 agencies. Highly recommended. The only drawback is that if there is a legitimate credit check, you need to temporarily unfreeze. Had to do that with Experian when renting a new apartment, took a few minutes on the phone.
This breach was too big to risk, and I had a similar experience with Equifax’ “impact” site, so I went back to your prior posts recommending security freezes.
Using a Firefox browser, I was able to implement freezes online with Experian, TransUnion, and Innovis, though finding the correct landing page on TransUnion instead of a paid monitoring subscription required getting lucky.
Equifax was another matter. After entering id info and qualifying challenges, I ended up at “We are currently unable to service your request. Please try again later.” Three tries over 30 minutes, still nogo. I had tried this with Equifax in 2015 to the same end and gave up on all of them, but later received a letter from Equifax saying a freeze was in place which I had no PIN to manage. I had to cancel that freeze by letter.
This time, I decided to retry Equifax with my emergency-use-only Win 10 PC and its Edge browser. Equifax’ system processed the freeze and returned a PIN, though with instructions to use an Adobe Print button that wasn’t visible to print it. Perhaps lots of fancy HTML stuff that caused Firefox to choke? At least this time I have a PIN, though by having written it down and screen captured.
Little or no information services at Equifax? I can believe it.
I wonder if Mint aka intuit knew about the Equifax breach? On September 6th they announced they are switching to transunion. Starting October 2, we’ll get your credit score from TransUnion, one of the nation’s top credit bureaus.
For those complaining about the $10 fee to freeze your credit report – be happy it exists!
If it was free – those a$$holes that stole the info could easily freeze us all out…you know, for the lulz…
What truly sucks is that they appropriate PII from consumers but consumers can’t fire these guys. Only the businesses that use them can. One way around that would be to complain to your bank about their performance and ask they no longer use Experian. I am doing that today, right after I check my credit and debit bank balances.
GDPR is the answer.
Could you expand on this a little? It’s unclear how GDPR would have prevented or mitigated this…
The TrustID site is now triggering a “Deceptive Site” warning in Chrome and Firefox.
Their cyber insurance carrier should deny the claim. Managements all over the place think that insurance is cheaper than doing the right thing. That needs to flip, especially in this case. Negligence should not be insurable.
As head of the Identity Theft Council, I recommend freezing two of the three main bureaus, and monitoring the third. That will give you some sense if anyone is at least trying to compromise your identity. Not foolproof, but far better than monitoring. Freeze the third if you need to.
The same day Equifax announced their breach, we announced an initiative that for the very first time in history has law enforcement taking a lead in community education and victim support. Timing is everything.
Freezing all 3 would be substantially better than leaving one unfrozen and waiting until it’s compromised to be notified about it.
OK Lets See Now Martha Stewart Goes to Prison For Talking on the Phone About Her Stock Trades, Now Watch These To See If These Guys Get Away With Selling After The Discovery BUT Before the announcement of the breach.
Great Work Thanks
What if they, by default, implemented the protections afforded under credit monitoring? Everybody would be covered if they have a credit record from day 1. Why gather the info, and whether breached or not, extort protection money when they hold the damn info!?
Please take money from me to protect me from a breach of your system?? From a certain perspective this makes no sense.
Is there an easy way to – confirm – that credit freezes already in place with the big three are still in place?
(I put a freeze on innovis this morning)
Thanks.
Mac
I don’t know about an instant confirmation, but apply for some sort of credit (credit card, in store finance purchase) and you find out pretty quickly that you are denied. Sometimes they don’t say why (but believe me it is because of the freeze.) We have had our credit frozen for years and every now and then I apply for something just to test it. Always get denied.
Not clean or easy but it does provide some ability to test.
Equifax seems to top it off with three executives selling shares a few days before the announcement of the breach. Reported by Bloomberg according to my local paper (Toronto Star) . This included CFO John Gamble!
Hope some commission looks into this – it seems a clear case of insider trading
I heard this from our VP of Investments this morning and agree that these guys need to be investigated and possibly (hopefully) charged. Greed blinds some to the fact that the truth will be discovered and hopefully dealt with.
“Based on the information provided, we believe that your personal information may have been impacted by this incident.”
I just tried the tool to see if I had been impacted and it said that it was likely I had and gave me the option to enroll immediately.
Also note the whois record for trustedidpremier uses a Whois Privacy Service. That is not re-assuring.
Raw WHOIS Record
Domain Name: trustedidpremier.com
Registry Domain ID: 2157515886_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.registrar.amazon.com
Registrar URL: https://registrar.amazon.com
Updated Date: 2017-08-29T04:59:17.034Z
Creation Date: 2017-08-28T17:25:35Z
Registrar Registration Expiration Date: 2018-08-28T17:25:35Z
Registrar: Amazon Registrar, Inc.
Registrar IANA ID: 468
Registrar Abuse Contact Email: registrar-abuse@amazon.com
Registrar Abuse Contact Phone: +1.2062661000
Reseller:
Domain Status: addPeriod https://icann.org/epp#addPeriod
Domain Status: ok https://icann.org/epp#ok
Registry Registrant ID:
Registrant Name: On behalf of trustedidpremier.com owner
Registrant Organization: Whois Privacy Service
Registrant Street: P.O. Box 81226
Registrant City: Seattle
Registrant State/Province: WA
Registrant Postal Code: 98108-1226
Registrant Country: US
Registrant Phone: +1.2065771368
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: owner-1508335@trustedidpremier.com.whoisprivacyservice.org
Registry Admin ID:
Admin Name: On behalf of trustedidpremier.com administrative contact
Admin Organization: Whois Privacy Service
Admin Street: P.O. Box 81226
Admin City: Seattle
Admin State/Province: WA
Admin Postal Code: 98108-1226
Admin Country: US
Admin Phone: +1.2065771368
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: admin-1508335@trustedidpremier.com.whoisprivacyservice.org
Registry Tech ID:
Tech Name: On behalf of trustedidpremier.com technical contact
Tech Organization: Whois Privacy Service
Tech Street: P.O. Box 81226
Tech City: Seattle
Tech State/Province: WA
Tech Postal Code: 98108-1226
Tech Country: US
Tech Phone: +1.2065771368
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: tech-1508335@trustedidpremier.com.whoisprivacyservice.org
Name Server: ns-1426.awsdns-50.org
Name Server: ns-1667.awsdns-16.co.uk
Name Server: ns-402.awsdns-50.com
Name Server: ns-934.awsdns-52.net
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2017-08-29T04:59:17.408Z <<<
For more information on Whois status codes, please visit https://www.icann.org/resources/pages/epp
By submitting a query to the Amazon Registrar, Inc. WHOIS database, you agree to abide by the following terms. The data in Amazon Registrar, Inc.'s WHOIS database is provided by Amazon Registrar, Inc. for the sole purpose of assisting you in obtaining information about domain name accuracy. You agree to use this data only for lawful purposes and further agree not to use this data for any unlawful purpose or to: (1) enable, allow, or otherwise support the transmission by email, telephone, or facsimile of commercial advertising or unsolicited bulk email, or (2) enable high volume, automated, electronic processes to collect or compile this data for any purpose, including mining this data for your own personal or commercial purposes. Amazon Registrar, Inc. reserves the right to restrict or terminate your access to the data if you fail to abide by these terms of use. Amazon Registrar, Inc. reserves the right to modify these terms at any time.
Visit Amazon Registrar, Inc. at https://registrar.amazon.com
Contact us at registrar@amazon.com or +1.2062661000
© 2017, Amazon.com, Inc., or its affiliates
Is there information on how to sue for Equifax not putting up protective firewalls?!
Equifax’s business model was to expand their services by purchasing other software companies such as Talx instead of just focusing on managing consumer credit information and focusing on protecting it.
This doesn’t surprise me at all.
The ONLY way to tighten security is to fine these corporations into non-existence. Also jail corporate officers where appropriate. There is absolutely no excuse to not secure the data. They do not take the time to secure the data because it costs money to do so. The solution is simple. Pass new laws and impose HUGE fines on every data leak. This is the ONLY way they will tighten security. They will only do so if it will cost them money. Lots of money. The fine has to be a magnitude more than the cost of securing the data. The government needs to step up and protect it’s citizens!
It will be interesting to see how Equifax pulls itself out of this one. No doubt many people will be losing jobs.
You are correct! It won’t be the people who are responsible though. It will be scapegoats, including the company that provided the software-in-question, patched or not.
Careful what you wish for – if they go bankrupt, they’ll need to sell assets. Guess what their #1 assets are…
You might want to check the terms of use before you sign up. Equifax sucks…for allowing this to happen and then to sneak an arbitration clause into the TOS.
The arbitration clause states that if you agree to use the service, then you can’t participate in a class action.
…
Thanks for pointing this out.
Wow, good catch there. I’ll stay away from the useless monitoring and go for a freeze instead!
Came here to say this. People should know about this before they use the “free” credit monitoring.
LOL know it is just the opposite, made up a fake name Wonka (willy Wonka) and six random num,bers and Now it says i could be a victim. LOL Total opposite of yesterday No wonder they got hacked into
As a note to anyone signing up for the Equifax protection being offered – read the agreement carefully. Evidently accepting the service will remove your ability to enter into a class action lawsuit later.
Equifax wants us to enter the last 6 of our social and our last name on a website whose certificates are issued outside the USA and which in now way mention Equifax as the owner of the certificate??? Is this a joke ? Can’t you get a certificate that clearly states it’s issued to Equifax ???
Yesterday got no message. Today got the message I am affected. I can enroll 9/12. So, I am unprotected until then?
Equifax wants us to enter the last 6 of our social and our last name on a website whose certificates are issued outside the USA and which in now way mention Equifax as the owner of the certificate??? Is this a joke ? Can’t you get a certificate that clearly states it’s issued to Equifax ???
TrustedID is owned by Equifax which is hilarious by itself, just as Brian stated. What should really piss you off are the terms and conditions of signing up for their service.
If you enroll in Equifax’s TrustedID from your data being leaked, you waive your rights to sue Equifax and TrustedID in court or be part of any class action. Check for yourself: trustedidpremier.com/static/terms
I’m not able to inspect the certificate of the potential impact checking website at work because my employer has the stupid ZScaler man-in-the-middle TLS inspection in place, so every secure site I visit only shows the ZScaler certificate. These “security” tools might be useful to IT in some ways, but for people who are accustomed to doing their own certificate inspection, it’s a real pain in the ass.