Dec. 18 marked the fourth anniversary of this site breaking the news about a breach at Target involving some 40 million customer credit and debit cards. It has been fascinating in the years since that epic intrusion to see how organized cyber thieves have shifted from targeting big box retailers to hacking a broad swath of small to mid-sized merchants.
In many ways, not much has changed: The biggest underground shops that sell stolen cards still index most of their cards by ZIP code. Only, the ZIP code corresponds not to the legitimate cardholder’s billing address but to the address of the hacked store at which the card in question was physically swiped (the reason for this is that buyers of these cards tend to prefer cards used by people who live in their geographic area, as the subsequent fraudulent use of those cards tends to set off fewer alarm bells at the issuing bank).
Last week I was researching a story published here this week on how a steep increase in transaction fees associated with Bitcoin is causing many carding shops to recommend alternate virtual currencies like Litecoin. And I noticed that popular carding store Joker’s Stash had just posted a new batch of cards dubbed “Dynamittte,” which boasted some 7 million cards advertised as “100 percent” valid — meaning the cards were so fresh that even the major credit card issuers probably didn’t yet know which retail or restaurant breach caused this particular breach.
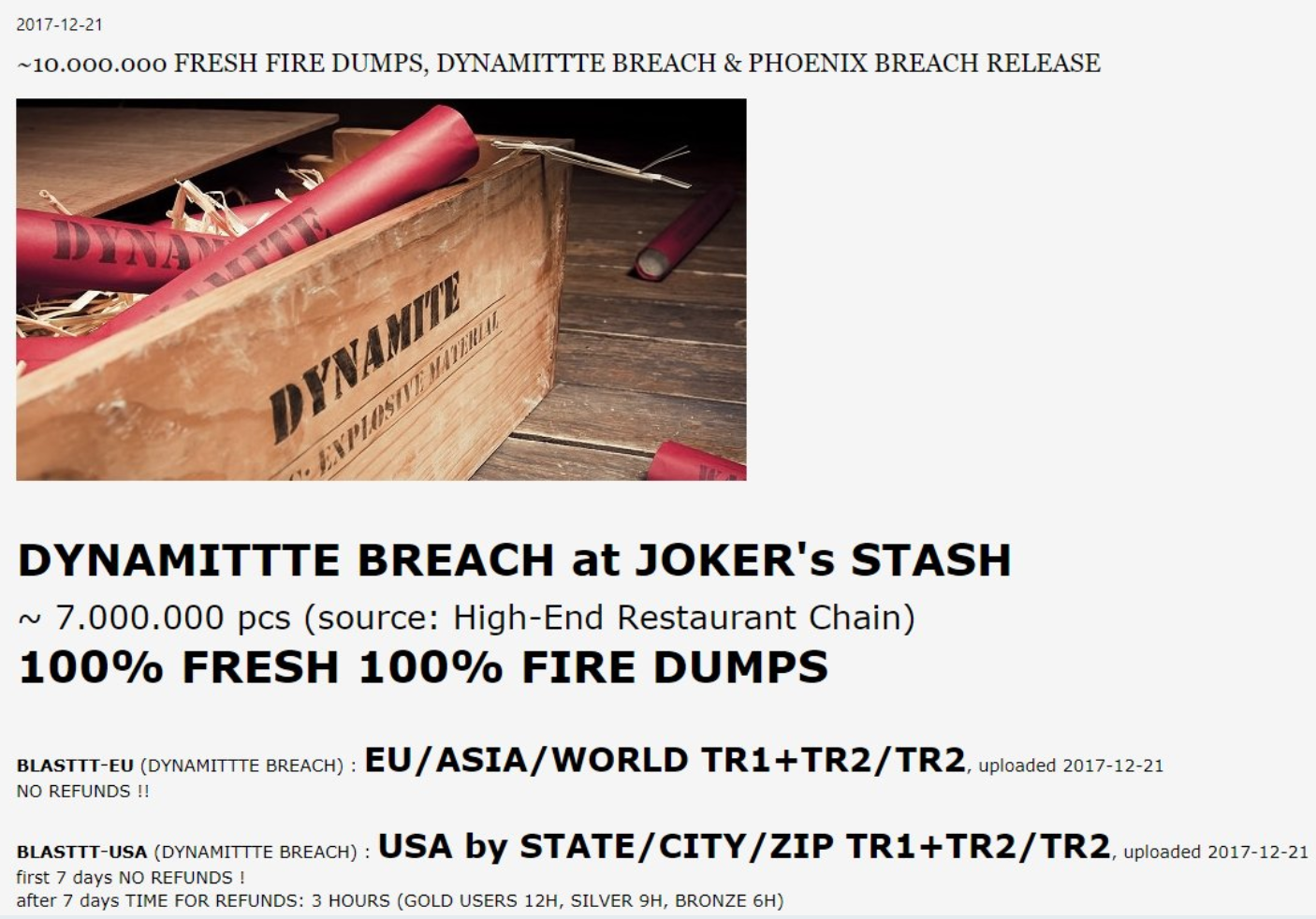
An advertisement for a large new batch of stolen credit card accounts for sale at the Joker’s Stash Dark Web market.
Translation: These stolen cards were far more likely to still be active and useable after fraudsters encode the account numbers onto fake plastic and use the counterfeits to go shopping in big box stores.
I pinged a couple of sources who track when huge new batches of stolen cards hit the market, and both said the test cards they’d purchased from the Joker’s Stash Dynamittte batch mapped back to customers who all had one thing in common: They’d all recently eaten at a Jason’s Deli location.
Jason’s Deli is a fast casual restaurant chain based in Beaumont, Texas, with approximately 266 locations in 28 states. Seeking additional evidence as to the source of the breach, I turned to the Jason’s Deli Web site and scraped the ZIP codes for their various stores across the country. Then I began comparing those ZIPs with the ZIPs tied to this new Dynamittte batch of cards at Joker’s Stash.
Checking my work were the folks at Mindwise.io, a threat intelligence startup in California that monitors Dark Web marketplaces and tries to extract useful information from them. Mindwise found a nearly 100 percent overlap between the ZIP codes on the “Blasttt-US” unit of the Dynamittte cards for sale and the ZIP codes for Jason’s Deli locations.
Reached for comment, Jason’s Deli released the following statement:
“On Friday, Dec. 22, 2017, our company was notified by payment processors – the organizations that manage the electronic connections between Jason’s Deli locations and payment card issuers – that MasterCard security personnel had informed it that a large quantity of payment card information had appeared for sale on the ‘dark web,’ and that an analysis of the data indicated that at least a portion of the data may have come from various Jason’s Deli locations.”
“Jason’s Deli’s management immediately activated our response plan, including engagement of a leading threat response team, involvement of other forensic experts, and cooperation with law enforcement. Among the questions that investigators are working to determine is whether in fact a breach took place, and if so, to determine its scope, the method employed, and whether there is any continuing breach or vulnerability.”
“The investigation is in its early stages and, as is typical in such situations, we expect it will take some time to determine exactly what happened. Jason’s Deli will provide as much information as possible as the inquiry progresses, bearing in mind that security and law enforcement considerations may limit the amount of detail we can provide.”
It’s important to note that the apparent breach at Jason’s Deli almost certainly does not correspond to 7 million cards; typically, carding shop owners will mix cards stolen from multiple breaches into one much larger batch (Dynamittte), and often further subdivide the cards by region (US vs. European cards).
As run-of-the-mill as these card breaches have become, it’s still remarkable even in smaller batches of cards like those apparently stolen from Jason’s Deli customers just how many financial institutions are impacted with each breach.
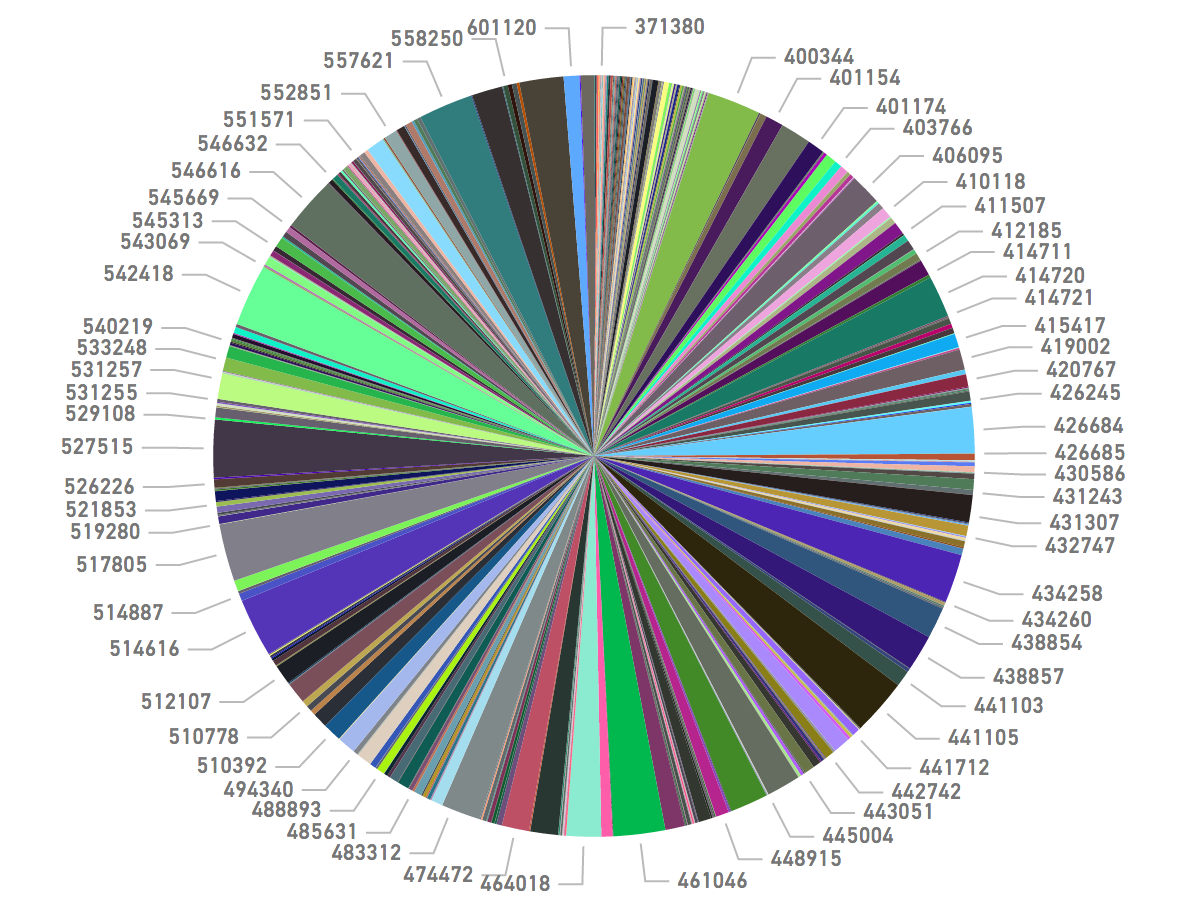
Banks impacted by the apparent breach at Jason’s Deli, sorted by Bank ID Number (BIN) — i.e. the issuer identified by the first six digits in the card number.
Mindwise said it was comfortable concluding that at least 170,000 of the cards put up for sale this past week on Joker’s Stash map back to Jason’s Deli locations. That may seem like a drop in the bucket compared to the 40 million cards that thieves hauled away from Target four years ago, but the cards stolen from Jason’s Deli customers were issued by more than 250 banks and credit unions, most of which will adopt differing strategies on how to manage fraud on those cards.
In other words, by moving down the food chain to smaller but far more plentiful and probably less secure merchants (either by choice or because the larger stores became a harder target) — and by mixing cards stolen from multiple breaches — the fraudsters have made it less likely that breaches at chain stores will be detected and remediated quickly, thereby prolonging the value and use of the stolen cards put up for sale in underground marketplaces.
All that said, it’s really not worth it to spend time worrying about where your card number may have been breached, since it’s almost always impossible to say for sure and because it’s common for the same card to be breached at multiple establishments during the same time period.
Just remember that although consumers are not liable for fraudulent charges, it may still fall to you the consumer to spot and report any suspicious charges. So keep a close eye on your statements, and consider signing up for text message notifications of new charges if your card issuer offers this service. Most of these services also can be set to alert you if you’re about to miss an upcoming payment, so they can also be handy for avoiding late fees and other costly charges.
Related reading (i.e., other breach stories confirmed with ZIP code analysis):
Breach at Sonic Drive-in May Have Impacted Millions of Credit, Debit Cards
Zip Codes Show Extent of Sally Beauty Breach




I’m glad to finally see a breach announcement without “we take your privacy and security very seariously” in it.
This is some DAMN fine investigative work, Brian. I’ve had individual cards caught in multiple breaches in the past, and I’m wondering how long it’ll be before issuing banks just start sending new cards every month. I feel like it would be the most effective way to deal with the constant hacks…
Along the lines of a regular periodic re-issuing of cards would be to consider issuing consumer security tokens that generate one-time random PINs for transactions.
Yes, many will consider this an inconvenience and card issuers would likely worry about consumer resistance to an added device. And of course there is always the possibility of the security token company itself being hacked, a la the RSA Security debacle, but that, one would imagine, is a lower probability event.
>generate one-time random PINs for transactions.
This pretty much describes Android / Apple pay via an NFC reader
New cards every month? Really? Considering cards cost at least $2 to reissue (plastic expense, emboss expense, postage expense plus processor fees for things like card activation, account on file, etc.) and the Fed reported that debit interchange rates for signature transactions are 1.07%, there is no way that card issuers would profit with monthly reissues.
Maybe Krebs could have called it the “JJ Evans” breach because the card holders not going to have Good Times ! Laugh it up !
So I take this to mean that Jasons does not have EMV capable POS systems?
According to Jason’s Deli, none of their stores have chip-enabled readers.
Sure they do.. but like 98% of other vendors, they’re still allowing non-token based swipe transactions. Until this loophole is fixed (vendors forced to enable chip-only based transactions), this scale of card theft will continue.
The biggest/last holdout are PoS side swipe terminals. These vendors either need to be forced to chip (if not chip+PIN) transactions or held financially liable for being the weakest link (now that everyone has the equipment to secure the PoS vector).
Tweeks
Chip capable is not the same thing as chip-ready or chip-enabled. Yes, most retailers have chip capable readers installed, but most also don’t have the chip capability turned on, for a number of reasons.
Jason’s uses an swipe slot attached to the cash register. The customer is not presented with a swipe/chip option.
For a credit card transaction, you hand your credit card to the cashier. The cashier swipes the card. You’re asked if you need a receipt. If not, the cashier hands back your card and you’re done.
> …most also don’t have the chip capability turned on, for a number of reasons.
I’d bet the “number of reasons” is $$$, not technical. What would be a good read is seeing if the banks go after the breached merchant to recoup their costs. They start doing that, the merchants would tighten security. A few might try to do away with cards, but that will likely cost them too much business, and they quit that quickly.
The problem with that though is businesses, particularly the insurance companies, think short term, not long term. Sure the first suit might cost more than they get back, but next time the breached merchant will be more willing to settle.
One of the impediments to ‘chip only’ are 3rd party processors and large issuers which provide swipe PoS devices as part of their services. There are still many, many small businesses which only have dedicated swipe readers.
In other words, 3rd party processors need to make the investment to replace all those swipe devices as well as upgraded software to securely work with chip transactions.
Ain’t happening any time soon.
And yet, it already has happened in Canada and most of Europe.
EMV has nothing to do with securing payment transactions. In fact, EMV as it is implemented today in the US is no more secure than the mag stripe. The EMV standard does have the capabilities for further securing transactions (e.g., dynamic PAN and dynamic PIN), but those are not enabled even in Europe and Canada where EMV have been in use for a while. What makes EMV more secure in Europe and Canada is the requirement to enter a PIN when using a card. However, the PIN requirement can be bypassed by the merchant.
What makes payments truly secure is end-to-end encryption (E2EE) and tokenization of the PAN. Using those technologies makes either the mag stripe or EMV secure. Most merchants have implemented or are in the process of implementing these technologies which effectively takes them out as targets for a breach. Once all merchants implement these technologies, only the processors, banks and card brands will be the source for such data.
EMV is not the weak link in the implementations you’re describing of course; it’s the low-tech signature and mag stripe that are the problem – that’s why EMV is working fine everywhere else in the world where these are (fairly consistently) no longer accepted. Heck, some capabilities the standard supports haven’t been rolled out anywhere yet afaik because they’re simply not needed yet.
You’re 100% correct.. Now ask yourself why Visa and MasterCard have pushed EMV and yet could care less if a retailer deploys E2EE.
4 years later and what has changed? Perhaps some of the larger companies are more secure, or maybe it’s just a matter of time before new breeches are reported to the public?
Get a clue, IT people! There are lots of ways to obfuscate important data to make it nearly impossible for someone to figure out how to put the pieces back together, should they get access to it. Take the time to not only encrypt, but also scatter the data and stories like this won’t be so commonplace. And don’t encrypt with common methods, make up your own!
As one of these “IT People”, tell me: How would scattering this data work/help?
What it sounds like you are advocating for is security through obscurity, which is not security at all.
I don’t know if this post is sincere or not but it’s a cardinal rule that you do not create your own encryption.
https://www.google.com/search?q=roll+your+own+encryption
Try bit shifting. That should suffice.
Do what… “make up your own”?? Do you even know what on earth you are talking about? Since when was it ever recommended that one roll their own encryption? SMH…
Oh, if we only had a clue…all problems would be solved…
I myself am working on my own mashed banana crypto scheme. The encrypting works great but I haven’t been able to decrypt it yet.
I use Double ROT-13. Sometimes, when I’m feeling extra paranoid, I’ll double that to Quad ROT-13 for extra strength!!
“And don’t encrypt with common methods, make up your own!”
Please don’t anyone follow this person’s advise. FOr his previous comments, obfuscation is not security. It gives the appearance of security to those that do not know better and actually makes it easier to break into systems.
As for the above-quoted statement, a thousand times no. History has shown it is always a disaster to have a programmer design a cipher. Leave cryptography to the experts who actually know what they are doing. Amateurs, historically, have failed miserably
Wondering who at Mastercard is leaking CPP data to you.
Banks and other issuing organizations are all doing their own data analytics at this point and share information in various forums and user groups.
Mastercard will never disclose any merchant names to anyone – officially or unofficially. Even after the merchant’s themselves acknowledge the breach.
Visa and MasterCard have set up their systems so that it’s not their job to do this kind of analysis. Not saying they don’t, but if they do they rarely share it with the card-issuing institutions. At least not in any timeframe that’s useful to most financial institutions.
Usually, it is the other way around: A bunch of banks report the same thing and Visa and MC then start their own investigation.
In short, I would never count on someone from the card brands to be a source on stuff like this, because the only time they’d know about it is if it was a really big event, in my experience.
We had a MasterCard compromised. Our bank sent me an alert and I declined the charge. I called my wife who was able to get online, find other pending fraudulent charges and then call the bank to get them removed and re-issue a new card. One of the fraudulent changes was on a Redbox machine. A few weeks later, after the new cards were issued, we saw a new charge from Redbox for $110. It turns out MasterCard gave Redbox the new card number because, “they’re required by law” to do so. Lesson learned: you can never assume issuing a new card will end fraudulent charges.
Do they still use Radiant POS? Is it too soon to tell if the breach occurred on the POS terminals or their self service Kiosks?
What your observing is breach reporting bias. Given that there is no equivalent to the “Fatality Analysis Reporting System” for cybersecurity hackers are seemingly more brazen and opportunistic. Everyone is a target. There is no discrimination based on size only imagination to capture data at any point it is undefended.
Being a bad guy on the internet is just great business today.
Didn’t Jason’s Deli have the same issue in 2010/2011?
Credit card and bank fraud is probably the “best” form of cybercrime from an ethical standpoint. It “steals” from the rich asshole bankers who pray on the middle class, while minimizing harm to the victims (they just report it and get their money back after a week). Yeah because Im so saddened and I sympathize so much with the rich if they can’t afford another private jet or yacht because of carding. It’s a good thing actually. The top 1% owns over 40% of the wealth. The rich are getting richer at the expense of everyone else. It’s no surprise that so many movies and tv shows are about the middle class doing something illegal to make ends meet.
The bank executives are not negatively impacted by these sorts of costs. They just list them as operating expenses on the ledgers and use it as an excuse to pay lower interest rates to the savings accounts and continue to pay small wages to the front-line staff that have no say into the decision making process that leads to these costs.
The executives will ensure that nothing gets in the way of the yearly bonuses they give to themselves.
Yes, so it actually IS the middle and lower income folks who pay the price, in the higher fees.
A common misconception is EMV (chip) protects from card number theft. It doesn’t. EMV in itself is not an encrypted communication, it just verifies the presence of a chip provided the retailer has an EMV reader. This technology only protects you from card duplication as long as the other retailer accepts EMV. Add to that in the US we don’t use pin like our international counterparts. So, if the retailer does not do P2PE (point-to-point encryption from card terminal to processor), the EMV card data can still be stolen and used at other retailers that don’t take EMV (i.e. online or gas stations).
This is a good point. EMV is there to protect the bank and the consumer, not the merchant themselves. Merchants are continuously being penalized for not having an EMV device just because “I didn’t dip” .. The implementation of the EMV solution can make it harder to suck the data out, mainly if the card data never touches a PC (RAM scraper), if on a dedicated hardware device that manages encryption and authorization result, the chances are much slimmer.
Also would be fair to point out in this article that this incident has only been tied back to corporate locations, _some_ franchisees have not reported any security incidents.
Krebs please look into this trend of stealing phone numbers that can then be used to drain bank accounts.
http://www.king5.com/article/news/thieves-are-stealing-your-cell-phone-number-to-take-your-money/281-501725049
It’s not a new problem or trend. Your mobile phone provider continues to be one of the weakest links in your security. And the big brands aren’t doing a lot about it.
https://krebsonsecurity.com/2017/08/is-your-mobile-carrier-your-weakest-link/
“Your mobile phone provider continues to be one of the weakest links in your security.”
How do you get around this, Brian? I’m just curious.
2-factor auth is not so high a bar if they’re able to get your SMS in realtime via cloning. What do you do beyond that? Recommend?
Here’s another loophole that I discovered by accident. I had a finicky Amex card for a bit that would get chip errors. Usually, after 3 errors, the terminal allows (and prompts for) a swipe.
Yup that’s chip fallback. That’s how fraudsters get around the EMV cards as well. They have a counterfeit chip card with a non working chip. After 3 failed dips, they are prompted to swipe. It comes through as a POS 80 chip fallback. We have tight restrictions for fallback transactions set up but a lot of times its not the issue of the card. Its a terminal implementation issue. Comes through as an EMV capable terminal but the software isn’t set up correctly so it wont let you dip. You are forced to swipe and it comes through as a POS 90 swipe. A POS 90 swipe at an “EMV capable” terminal results in no chargeback for the issuer. Merchant wins every time.
With the popularity of “pay with your phone” and “cashless only” transactions, the pressure on credit card companies and merchants to implement more secure transaction methods will only increase if more and more customers complain loudly and/or increased government pressure.
Merchants have pushed back for far too long on implementing secure transaction methods due to cost, lack of technology (gas pump readers), or simple laziness as shown in the Jason’ Deli example. Yeah we still swipe!
Credit card issuers are letting merchants get away with these delays while making their customers suffer the consequences.
Then there is the dilemma of deploying EMV. Why should merchants deploy EMV-capable terminals if credit card issuers don’t support it? Or, why should credit card issuers issue EMV-capable cards is merchants don’t have terminals that use it? I know that I had problems getting EMV-capable cards from my credit card issuers within the last 18 months.
I recently read an article saying parts of Manhattan (NYC) have merchants that are “cashless”, so I guess I will not be visiting there any time soon.
So imagine the hassle (cancelled cards, update recurring monthly transactions, wait for new cards, etc.) a customer will have to go through to constantly recycle credit card numbers because of poor merchant security, lack of secure transaction methods, and lack of pressure by credit card issuers & government.
I don’t have to imagine that hassle as I am going through it right now after going through it within the past 18 months.
Forgive me if I am missing the ambiance of your post; but EMV is everywhere here now, and I live in the desert back woods of America. Almost all the merchants I deal with have chip-N-pin readers now, and they funnel you into using it also. I’m sure there a quite a few merchants not tied to chains or national brands that probably don’t have them yet, but it is getting rare even out here in the sticks!
I HATE using a PIN to do store transactions, but I’m getting used to it!
I know at least 1 regional chain, Whataburger, that has local outlets that do not accept EMV; they paper over the “dip” slot with a sign that says “no chip”. I also have Jason’s Deli locations near me. So I agree with the premise of Brian’s article that hackers are moving down the “retail spectrum” to smaller outlets (compared to Target and Home Depot). I think hackers, card issuers, and merchants are in a form of “arms race” with hackers wanting to steal as much data as possible before it becomes more “secure” (EMV capable & enabled) or even “chip & PIN” enabled).
I live in the suburbs of a major metropolitan area comprising millions of residents., but I have yet to a single gas station around me that accepts EMV; all of them look like they use a form of “swipe” at the gas pumps, or the EMV function is “not visibly obvious”. If Brian has any thoughts or an article on current gas pump POS security design I would like to read it. FWIW I am wary of gas pumps that use any form of NFC function for “cashless” payment so I end up with “swipe” or cash, but I limit my gas purchases to 1 specific card (it’s EMV capable, but I have yet to see any proof on the receipt that EMV is being used) to limit my risk.
As for your “chip & PIN” comments, I have yet to encounter a “chip & pin” situation anywhere around where I live/ I only see “EMV dip” and I will “EMV dip” whenever I can. So I think EMV “penetration” into US markets varies by region. So a YMMV disclaimer is appropriate.
Repeated compromises, both physical and software/firmware, of POS terminals (Target, Home Depot, Barnes & Noble, Cici’s Pizza, etc.) have shown POS (along with 3rd party POS maintainers & 3rd party transaction processors) maybe the “weakest link” in the transaction chain. Getting infections into other parts of the transaction chain, like the Target breach, seems to be the second most effective way to compromise card info; just find some point in the chain where the data is not encrypted and grab it there. Lax or no implementation of commonly accepted security measures makes the hacker’s job easier, like Internet-accessible POS terminals in Brian’s story on the Cici’s Pizza breach, phishing emails that drop malware that can “open the door” for a further widening of a breach, or poorly designed transaction handling & processing networks within merchants & transaction processors.
My point is simple. To make a “cashless” transaction infrastructure work, aside from the challenges of online purchases and concerns over “pervasive government surveillance” of it’s citizens, card info has to be held reliably & securely “somewhere” to make a “cashless” system work and that data should be stored in an encrypted way that only card issuers can unencrypt when needed yet be straightforward for merchants and “datastores” to implement & update; merchants and datastores do not need to know your entire CC number and related info in “cleartext” (or do they? Anyone?). A PKI design on the “backend” might work and possibly limit data exposure to only the details in a poorly secured customer account. To me, the need for “end to end” encryption of card info seems mandatory, but it does not seem widely employed in the US relative to statements made by people living in Europe that swear by the “chip & PIN” setup.
YMMV
My mom was at the local post office Friday and bought a birthday card. I had her FaceTime me the image of the pos device. It was a new verifone unit. It had a label over card slot saying the chip reader was coming soon. We asked the postal clerk when that would be and she said “it was already supposed to be last year.”
Excellent follow up to the continuing problem post-Target!
Well written, and good work Brian!!
It is still amazing how the threat scape is constantly evolving as the crooks wise up to changes in merchant security.
Allow me to use the tired old saying of “Keep up the good work”; because you do – and do it so well. Kudos to you Sir!!
Have an excellent and HAPPY NEW YEAR!!!
Excellent research and write up Brian…
IMHO there is no excuse for not implementing P2PE at this point. I watched it get rolled out to ~600 locations in < 6 months this year.
Not only will it help keep retailers out of these articles, but it makes getting that PCI ROC a lot easier. I wouldn't be shocked to see that become a PCI requirement in the next few years…
In your Sonic compromise column, did I miss a link to the locations affected?
O love a nice fresh waffle in the morning.
“Deli locations and payment card issuers – that MasterCard security personnel had informed it that a large quantity of payment card information had appeared for sale on the ‘dark web,’ and that an analysis of the data indicated that at least a portion of the data may have come from various Jason’s Deli locations.”
I love a nice fresh waffle in the morning.
“Deli locations and payment card issuers – that MasterCard security personnel had informed it that a large quantity of payment card information had appeared for sale on the ‘dark web,’ and that an analysis of the data indicated that at least a portion of the data may have come from various Jason’s Deli locations.”
Interesting arguements against the weaker link of the process. “Blame the vendor” , remember https is hacked, remember a typical computer laptop can decrypt most traffic within minutes, verses the hours as before, and the “cloud” is also hacked. Now, tell me there is secure communications, and my devices are safe. Will I believe you?
Don’t always blame the vendor for card device not reading your chip. Many times it is the network they have available. Not all networks are equal, remember, many places only get 14.4 speeds here in the US, paying Comcast rates. Not all services are equal, but they charge for top tier. Remember that chip reader has to connect real time not sometime later, sale, use or just a piece of plastic? That you use when it wants, not when you want to use it.
Looking at these breaches happen time and time again I’m starting to get to the feeling that PoS terminals sold to merchants in the U.S seem have fundamental level security problems.
As far as I understand the ones used here in Europe have the card reader as a physically separate unit that communicates with the card holders’ servers independently over a well encrypted link. Not only that, the card reader has it’s programming in mask ROM memory so any hack of it will be removed when the terminal is turned off at the end of the day with the PoS terminal it’s connected to.
why keep flaws and sex weak links? who to blame`?
hackers? if you have money in house would you leave house door open ?? offcourse no !! if someone telling to me that my money is stolen coz of the breaqch or flwas,i will make someone responsible for that.
A friend of mine recently was notified of fraud on her Chase card. She only used this card in stores, not online, and only used the card in a two locations in the past two month’s, Kohl’s and a local shop. I told her that I thought that it was probably the local business, since Kohl’s should have learned how to avoid a breach by now and local businesses usually have lax security.
Could the card be from an earlier breach? and just appeared for sale recently. It’s worth noting that the card was used for a free Netflix trial where the card was tested by charging and then refunding $1. That was enough to tip Chase off within minutes of use.
Yes, it could have been from a major breach 8 months ago or a single dishonest contact 8 days ago. It’s impossible to diagnose from limited data, especially where no one’s legally obligated to make an announcement.
It’s the New Year now, and people are discovering that their gift cards are of no use; they’ve been scanned, and as soon as they’re activated, the thieves use the balance. When are the stores going to put the gift cards in a locked spot?
http://190.115.24.126
http://185.61.137.164
joker public ips