Government Payment Service Inc. — a company used by thousands of U.S. state and local governments to accept online payments for everything from traffic citations and licensing fees to bail payments and court-ordered fines — has leaked more than 14 million customer records dating back at least six years, including names, addresses, phone numbers and the last four digits of the payer’s credit card.
Indianapolis-based GovPayNet, doing business online as GovPayNow.com, serves approximately 2,300 government agencies in 35 states. GovPayNow.com displays an online receipt when citizens use it to settle state and local government fees and fines via the site. Until this past weekend it was possible to view millions of customer records simply by altering digits in the Web address displayed by each receipt.
On Friday, Sept. 14, KrebsOnSecurity alerted GovPayNet that its site was exposing at least 14 million customer receipts dating back to 2012. Two days later, the company said it had addressed “a potential issue.”
“GovPayNet has addressed a potential issue with our online system that allows users to access copies of their receipts, but did not adequately restrict access only to authorized recipients,” the company said in a statement provided to KrebsOnSecurity.
The statement continues:
“The company has no indication that any improperly accessed information was used to harm any customer, and receipts do not contain information that can be used to initiate a financial transaction. Additionally, most information in the receipts is a matter of public record that may be accessed through other means. Nonetheless, out of an abundance of caution and to maximize security for users, GovPayNet has updated this system to ensure that only authorized users will be able to view their individual receipts. We will continue to evaluate security and access to all systems and customer records.”
In January 2018, GovPayNet was acquired by Securus Technologies, a Carrollton, Texas- based company that provides telecommunications services to prisons and helps law enforcement personnel keep tabs on mobile devices used by former inmates.
Although its name may suggest otherwise, Securus does not have a great track record in securing data. In May 2018, the New York Times broke the news that Securus’ service for tracking the cell phones of convicted felons was being abused by law enforcement agencies to track the real-time location of mobile devices used by people who had only been suspected of committing a crime. The story observed that authorities could use the service to track the real-time location of nearly any mobile phone in North America.
Just weeks later, Motherboard reported that hackers had broken into Securus’ systems and stolen the online credentials for multiple law enforcement officials who used the company’s systems to track the location of suspects via their mobile phone number.
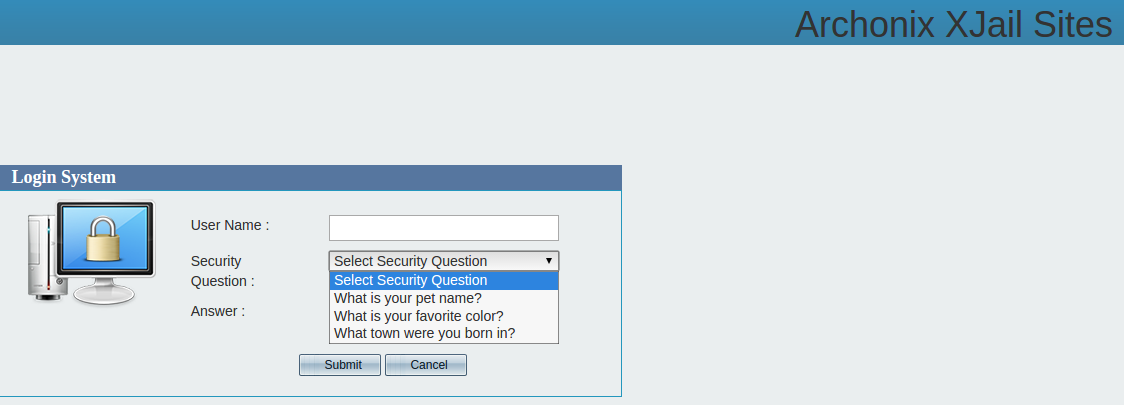
A story here on May 22 illustrated how Securus’ site appeared to allow anyone to reset the password of an authorized Securus user simply by guessing the answer to one of three pre-selected “security questions,” including “what is your pet name,” “what is your favorite color,” and “what town were you born in”. Much like GovPayNet, the Securus Web site seemed to have been erected sometime in the aughts and left to age ungracefully for years.
Data exposures like these are some of the most common but easily preventable forms of information leaks online. In this case, it was trivial to enumerate how many records were exposed because each record was sequential.
E-commerce sites can mitigate such leaks by using something other than easily-guessed or sequential record numbers, and/or encrypting unique portions of the URL displayed to customers upon payment.
Although fixing these information disclosure vulnerabilities is quite simple, it’s remarkable how many organizations that should know better don’t invest the resources needed to find and fix them. In August, KrebsOnSecurity disclosed a similar flaw at work across hundreds of small bank Web sites run by Fiserv, a major provider of technology services to financial institutions.
In July, identity theft protection service LifeLock fixed an information disclosure flaw that needlessly exposed the email address of millions of subscribers. And in April 2018, PaneraBread.com remedied a weakness that exposed millions of customer names, email and physical addresses, birthdays and partial credit card numbers.
Got a tip about a security vulnerability similar to those detailed above, or perhaps something more serious? Please drop me a note at krebsonsecurity @ gmail.com.




Brian wrote: “..it’s remarkable how many organizations that should know better don’t invest the resources needed to find and fix them.”
Well, if they don’t get hit with big fat lawsuits they will continue to favor the bottom line and to hell with the clients. It’s all in stock value.
and big govt wants to over regulate and control more and more of the internet. their health care websites in some states were also a disaster.
You may have missed the bit where GovPayNet was a private contractor.
And don’t forget the always inspiring, “We’re from the government and we’re here to help you.”
…said no one ever.
Ronald Reagan said it, it was in jest, but he did say it.
“Nonetheless, out of an abundance of caution and to maximize security for users, GovPayNet has updated this system to ensure that only authorized users will be able to view their individual receipts.”
Funny how that abundance of caution always follows a prior shortage of caution. And how they decide to maximize security because it was previously minimal.
OK, maybe not so funny.
We’re living in the age of the “non-apology”.
“We didn’t make a mistake, we’ve just suddenly and surreptitiously opted to be really, REALLY careful with your stuff. No particular reason. We’re just great people and you should love us.”
Love conquers all.
During the 2008 recession, my small drywall firm found itself with an unexpected surplus supply of topping (finishing) compound (“mud”). As part of our cost-cutting, downsizing strategy, we mixed it with on-hand rapid setting dry compound (“hot mud”), and used it to embed and attach fully code-compliant paper tape. Several years later, a significant portion of this “taping” experienced a totally unforeseen, and nearly inexplicable materials failure characterized by tape falling off of walls and ceilings, along with the finishing mud which covered it. We’re offering free mitigation: any former customer with a problem can receive an instruction video on embedding and finishing drywall paper tape. We are in close contact with local and state building officials, although our firm closed permanently in 2012.
Although we’re deeply sorry for our customers troubles, no one has yet died in a catastrophic fire enabled by the absence of passive fire containment–a by-product of the tape falling. Those authorities and so-called drywall experts who claim that the tape failure was inevitable, are the sort of pessimists and nay-sayers who try to stifle innovation at every turn of the road, no matter the situation.
Can’t wait to read what you posted about information leaks on the drywall message board!
You don’t need to wait. Companies like GovPayNow.com behave, in reality, with the same greed, incompetence, and insincerity as my imaginary company…and then BK reports on it. BTW the mistakes mentioned are based on 2 different actual errors I saw in my years in the mud trade.
So an instruction video is “mitigation”? Why didn’t Equifax think of that?
Good thought. Let’s hope they don’t read this!
This should shut down the naysayers who claim sarcasm can’t shine through in print!
@Bart, exactly right. Until we see some CEOs publicly cited and made felons, bank accounts zeroed, their houses foreclosed, sports cars confiscated etc this stuff is not going to stop. Spineless Congress hasn’t the courage to do what needs done.
Haha, “What is your pet name?” (vs. “What is your pet’s name?”)
mine is shnookums.
don’t hack me, bro!
Too late! I’ve got all your data!
Thanks, Shnookums!
I’m about ready to give up on governments or any other supposedly concerned business, and just let all our data be out there freely. Maybe we should concentrate more on who is using the data and less on securing it. We obviously can’t fix the problem, or at least no one seems to care, no matter what they say. Actions tell me they could care less. There must be a way to verify that you are you and not someone, or something else, that can’t be used by crooks to spoof who we are dealing with.
Is there any way to find out which government agencies are currently using “GovPayNow.com”? For instance, how can I find out if the Massachusetts Registry of Motor Vehicles (RMV) uses that as the innards of its “EZPass” toll payment responder’s account “re-filling”?
I tried using the following in a google search, it looks like most agencies that used it offer it as a direct link:
link:govpaynet MyTownName
Thanks for the suggestion. I did the Google search you suggested:
link:govpaynet MyTownName
using various “towns” (including “Massachusetts”) but that didn’t
do much for me. When I went to http:govpaynow.com it redirected
to:
https://www.govpaynow.com/gps/user/
which has an interface for finding particular “agencies” and making
particular kinds of payments. That interface has pop-down buttons that
display many individual using-agencies of “GovPayNet” and “GovPayNow”.
I partially answered my own question in that there were very few
Massachusetts “users”, and definitely not the Registrar of Motor
Vehicles.
And there is not a recall on this?…..i deal in bicycles and so sick of the cn/jpn game
Systems like these are designed and coded by the graduates of “code camps.” They know how to put a pretty face on a web site with the latest toolkit, but they don’t have a clue that security must be designed in, nor how to go about it.
On top of that, the security requirement specification in a majority of cases is entirely absent or is, “make it secure.”
Alt Headline: Criminal tracking company that supported criminal activity hacked by criminals.
Seams to be a theme.
I believe accountability is the solution. The terms “Due Care” and “Due Diligence” come to mind. If a company wants to deal in personal information then they need to be accountable. Large enough fines to make it really hurt or ban from doing business until they take security for others information more seriously.
This is exactly what GDPR does
I’m thinking about becoming an estonian e-resident and claiming GDPR protection
Applying for Estonian e-residency is cheap and amazingly simple. It’s a pity that the scheme has been so popular with certain Russian miscreants – a €200bn (yes *billion*, that’s an awful lot of dirty Russian money) money-laundering racket has been rumbled and the head of Danske Bank has fallen on his sword (metaphorically speaking, no CEO has been impaled afaik). There may be a story in there somewhere for Brian to find …
More “headslap”….
Our county allows anyone to view property tax details by only requiring name and address – i.e. one can use White Pages and access property tax records of strangers.
Unfortunately tax records are public.
I worked for a municipality for 19 years. This topic came up quite a bit. The law says those records must be available to anyone who asks for them. Does that mean we have to expose them on the web? It always seemed to me that making someone request them would be a better idea.
Not unfortunate property tax records are public. Sunshine is a powerful antidote to corruption, fraud, and injustice. That’s why so many folks value their privacy while wanting full visibility into everyone else’s affairs.
I think the key piece of that edict is the “to anyone who asks” bit.
If you’re passively snarfing them up, there’s no asking, no exchange, and no real opportunity to record who’s asking, therefore.
Property tax records are public records. Anyone can walk into the tax collector’s office and view them all without restrictions. So the unrestricted web access for anyone is proper function.
As a former municipal official I can attest this “complaint” is typical of citizens’ conflicted view about information: they want privacy and transparency, at the same time for the same information. For example, they want privacy of their own tax records but want to be able to audit the tax rolls for under assessments or outright fraud. You can’t have it both ways folks, it’s either transparent or it’s protected as private.
One bullet point only on “security”. https://www.govpaynet.com/faq.php#anchor-g37
“How do I know my customers’ card information is secure?
GovPayNet is independently certified as complying with the highest level of card security available. You can confirm this by clicking on the Trustwave® logo at the lower right-hand corner of our corporate web site, http://www.govpaynet.com or our payment web site, http://www.govpaynow.com.”
Interesting they flaunt a “PCI DSS I Comply Compliance Point” logo on their website. The myth of compliance and certification is that you can trust it beyond the actual time the snapshot occurred, coupled with the fact that not all reviews get deep enough at times. So I have yet another possible exposure of my information.
“Big business” buddies that Congress is they can’t yet get to enact law on this. But they should just assign a simple fine, per item leaked.
$100 per name/data element payable 50% to the owner of the name/element, 25% to the bank if it is a banking related item and 25% to the state government where the owner resides. Why these breakdowns? Because it is doubtful that an offender will act correctly in compensating the owner but banks and state governments are always needing cash and will spend sizable effort to track down their portion of these funds. It will really only take about 10 enforced penalties before everyone will be throwing serious resources at avoiding the fine and the source of the fine (security). And simply leaving it up to the legal resources of the common victim is again mostly toothless. A specific and declared fine that isn’t sizable unless the number of data elements is large would have a very direct impact. Verizon leaks all your PINS on AWS? Imagine if they had to pay every account listed (more than one if there was more than one listing of the same account such as a separate phone #) a fine based on this set fee structure.
DF wrote: “$100 per name/data element payable 50% to the owner of the name/element, 25% to the bank if it is a banking related item and 25% to the state government where the owner resides.”
A profoundly good idea. I plan to write my congress critters and demand they implement it. Between OPM, Equifax, various credit card compromises, govpay etc I would have been able to afford a vacation.
The nice thing it that the Government _ FEDERAL that is – will NOT accept a check as payment anymore for certain things. You must use there their -so called_ secure “Lockboxes” to make payments… Talking to you BLM….
“In May 2018, the New York Times broke the news that Securus’ service for tracking the cell phones of convicted felons was being abused by law enforcement agencies to track the real-time location of mobile devices used by people who had only been suspected of committing a crime.”
“Law enforcement” has always thought themselves above the law. At one time I oversaw E-911 system conversions. Laws very from state to state on the legality of a dispatcher to reverse a caller ID lookup through the 911 system. Many sites where it is legal they use the system to lookup address information for illegal purposes. At one site where it was not legal to do this, I had the 911 director threaten me if I didn’t authorize enabling the feature. His excuse: ” WE ARE THE LAW! WE NEED IT TO ENFORCE THE LAW.”
Now you have the FBI being exposed in Washington DC for breaking the law in order to impeach a president. So much for the integrity of law enforcement…
The FBI did no such thing. Keep the BS political conspiracy theories off the comments section of a Security blog.
READ the unredacted emails and tweets that the president just authorized the Justice department to release UNREDACTED. Also read what Judicial Watch has uncovered through the FOIA and then lawsuits despite FBI redacting almost anything they released. Only dimwitted twits support allowing government to run amuck and illegally harass innocent citizens.
No conspiracy BS, just facts slowly pried out of the criminals that run the FBI. Stay tuned, all hell is about to break loose…
If you’ve ever seen the documentary “Startup.com” about govWorks.com, you’ll understand that quality crafted and secure software was never the goal of a company of this type.
As others have pointed out, there is no positive financial reward for producing a secure website. And there is no negative financial punishment for producing an insecure website. There are very few exceptions to that rule.
This is what happens when individuals decide they want to pay less taxes and then look for and even create new loopholes to cut their tax payments. Less taxes means less government services and cheaper contractors.
Be careful what you ask for ; and before it’s to late crack open a bible; the world is going to hell fast and it seems the only way to fix it is to kill the internet, crush cell phones and go back to the old ways ; maybe the preppers are onto something ; forget the zombie apocalypse big brother is going to be our undoing
I agree with Bart.
The companies are obligues to their shareholders to NOT invest in security, unless there is a financially sound reason to do that.
If they get low fine, and don’t lose much money in case of a breach, it is really not in the interest of the shareholders to implement security.
No security is perfect, so it is always a cost/risk/benefit decision, like any other insurance.
ANON404, the people currently running the FBI are actively trying to impeach a duly elected president by manufacturing false information. They are criminals and are about to be exposed regardless of the media cover up going on.
Is it just me or _IS_ this “GovSwipe” dive, shown in the top screenshot, a bit venturesome?
I mean, it’s basically a USB numpad attached to a megnetic stripe reader.
Since it’s just reading the magnetic stripe (I hope) it’s not supposed to type in your credit card’s PIN number there.
But, nontheless, it’s pretty odd and looks like a nice try to steal both my credit card data and my PIN number 😉
What kind of sick PUN-of-a-Freudian-slip is “Gov$wipe”?
This country has managed to make people believe the victim is the criminal. All of you, if your house is broken into, it is not your fault for having cheap locks. It is the intruder’s fault and the government’s fault. The number 1 duty of government is protection of the people. This includes fighting crime. The government’s crime policies are weak. The criminal justice system encourages crimes such as this. In all but a few circumstances, businesses and individuals should not be held responsible for what criminals. Criminals are the criminals, not people trying to make honest profits.
I am disappointed to see that the device depicted on their site does not allow reading the chip on the card. You should really avoid swiping.