The U.S. Secret Service is warning financial institutions about a recent uptick in a form of ATM skimming that involves cutting cupcake-sized holes in a cash machine and then using a combination of magnets and medical devices to siphon customer account data directly from the card reader inside the ATM.
According to a non-public alert distributed to banks this week and shared with KrebsOnSecurity by a financial industry source, the Secret Service has received multiple reports about a complex form of skimming that often takes thieves days to implement.
This type of attack, sometimes called ATM “wiretapping” or “eavesdropping,” starts when thieves use a drill to make a relatively large hole in the front of a cash machine. The hole is then concealed by a metal faceplate, or perhaps a decal featuring the bank’s logo or boilerplate instructions on how to use the ATM.

A thin metal faceplate is often used to conceal the hole drilled into the front of the ATM. The PIN pad shield pictured here is equipped with a hidden spy camera.
Skimmer thieves will fish the card skimming device through the hole and attach it to the internal card reader via a magnet.
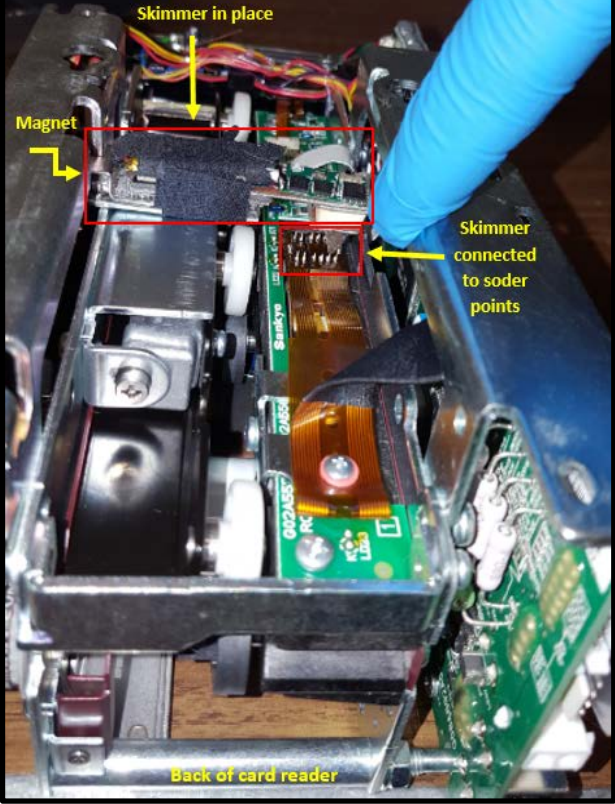
Thieves often use a magnet to secure their card skimmer in place above the ATM’s internal card reader. Image: U.S. Secret Service.
Very often the fraudsters will be assisted in the skimmer installation by an endoscope, a slender, flexible instrument traditionally used in medicine to give physicians a look inside the human body. By connecting a USB-based endoscope to his smart phone, the intruder can then peek inside the ATM and ensure that his skimmer is correctly attached to the card reader.

The Secret Service says once the skimmer is in place and the hole patched by a metal plate or plastic decal, the skimmer thieves often will wait a day or so to attach the pinhole camera. “The delay is believed to take place to ensure that vibrations from the drilling didn’t trigger an alarm from anti-skimming technology,” the alert reads.
When the suspect is satisfied that his drilling and mucking around inside the cash machine hasn’t set off any internal alarms, he returns to finish the job by retrofitting the ATM with a hidden camera. Often this is a false fascia directly in front of or above the PIN pad, recording each victim entering his or her PIN in a time-stamped video.
In other cases, the thieves may replace the PIN pad security shield on the ATM with a replica that includes a hidden pinhole camera, tucking the camera components behind the cut hole and fishing the camera wiring and battery through the hole drilled in the front of the machine.

The image on the left shows the spy camera guts and battery hidden behind the hole (this view is from the inside of the ATM, and the card reader is on the left). The image on the right shows a counterfeit PIN pad shield equipped with a hidden camera that is wired to the taped components pictured in the left image.
It’s difficult to cite all of the Secret Service’s report without giving thieves a precise blueprint on how to conduct these attacks. But I will say that several sources who spend a great deal of time monitoring cybercrime forums and communications have recently shared multiple how-to documents apparently making the rounds that lay out in painstaking detail how to execute these wiretapping attacks. So that knowledge is definitely being shared more widely in the criminal community now.
Overall, it’s getting tougher to spot ATM skimming devices, many of which are designed to be embedded inside various ATM components (e.g., insert skimmers). It’s best to focus instead on protecting your own physical security while at the cash machine. If you visit an ATM that looks strange, tampered with, or out of place, try to find another machine. Use only ATMs in public, well-lit areas, and avoid those in secluded spots.
Most importantly, cover the PIN pad with your hand when entering your PIN: That way, even if the thieves somehow skim your card, there is less chance that they will be able to snag your PIN as well. You’d be amazed at how many people fail to take this basic precaution.
Sure, there is still a chance that thieves could use a PIN-pad overlay device to capture your PIN, but in my experience these are far less common than hidden cameras (and quite a bit more costly for thieves who aren’t making their own skimmers). Done properly, covering the PIN pad with your hand could even block hidden cameras like those embedded in the phony PIN pad security shield pictured above.




The other advice I would give, apart from using a different ATM, is to report it to the bank and/or the police. Surprised you didn’t mention this.
I am surprised that bothered to add that little twist of the knife at the end. “Surprised you didn’t mention .” Really? Why? Who cares what you are surprised about? Really. You might have said “Thank you for mentioning this latest scam. Now I can tell others.” Seems better that way.
Not surprised, I have found that Banks, unless it DIRECTLY affects them tend to appease customers while doing nothing. I lost a card, a long time ago, in a machine in a lobby of the bank to be told by a bank official that it was impossible and only after insisting on a higher level manger did they go into the back and found my card laying on the ground. Then they came out and insisted I had to perform some form of request to get it back and again, after insisting vehemently they looked at my license and the card then returned it too me. Sigh!
We could just use a real live bank teller.
That’s not gonna happen. It’s to easy…
Easy if you’re free to stop at the bank during bankers hours.
Some of us work before, during, and after those times.
… and pay a hefty over the counter transaction fee
Sounds like you need a new bank!
So it seems like machines need to be re engineered to cover all circuitry that contains un encrypted data with a tamper plate…
And perhaps maintaining positive pressure with the ATM by way of fan, and measuring that pressure and the power draw of the fan for sudden sustained changes?
… and an LDR or some other sort of sensor within the machine near sensitive components to detect persistent light where there should be dark during specific parts of transaction? .. crook needs to see what they’re doing.. does light in area match flashing of card acceptor for example?
… IR beams across empty spaces of internal ATM space?
… capacitance sensors around key areas of machine to detect changes in structure?
… Thin dual conductive layer mesh applied to inside of ATM that’s likely to short on breach by any tool?
… Vendor provided overlays designed to be test fitted over key ATM portions to quickly check if something is to spec?
There seems to be too much reliance on the idea that the ATM case is inviolable which is clearly not the case. Assuming folks ARE going to get in, need to detect when they do.. assume perimeter is crap and imolement security in depth.
… implement …
Technology isn’t the answer to every problem. Rather than getting into a constant arms race with thieves and replace every ATM twice a year with the latest short term countermeasures, some banks are taking the simple steps of accepting a certain level of fraud and the cost of reversing or simply reimbursing victims of minor cash theft. As long as that’s cheaper than constantly re-engineering ATMs, that’s a good business decision for everybody.
Technology isn’t always the answer. It’s a truism that once an attacker has physical access, the machine is theirs. The cost of re-engineering and refitting/replacing all the ATMs to resist the latest techniques repeatedly is probably quite high. Banks might find that transaction limits and fraud detection, along with simply repaying petty cash fraud to affected clients, might be much less expensive.
Executives at banks and businesses want bigger bonuses. They get bigger bonuses when they report that they saved money by eliminating employees. Bank Tellers, or store cashiers are the easiest and lowest level employees to dispose of. It is in the executives’ best personal interest and that is what is all about.
Interesting video. I noticed the criminals were not speaking English. Does anyone recognize the language or understand what they said? Me thinks it was Arabic or some Middle-eastern dialect. Anyone have a clue?
Idti cyuda (Come here)
Svyaz’ (something) Connection (XXX)
Mashina (Something)
It’s russian I believe….
it’s romanian
It’s not Romanian. It’s russian…
Awesome pictures even though one has a spelling mistake LOL
Yeah I noticed that too. Not my mistake though.
Down here in God’s Country we pronounce it roughly that way, though we all (or most!) know there’s an “l”
It’s not “wiretapping” in the same way a Man-In-The-Middle-Attack would be, or a network sniffer. This is still -just- skimming, evolved to the card reader, and with more vandalism to the ATM. The headline is salacious and designed for click-bait-ish site traffic. InfoSec folks all over are going to trip over themselves spraining their necks to attack their ATM Operations folks and Fraud divisions freaking out over this “threat” when it’s just an evolution of skimming – being performed by the same idjits pushing insert-skimmers down card reader throats.
Is it worth sharing and educating the marketplace and customers – sure. Is it worth kicking up dust and using buzzwords like “wiretapping”? Nope.
Disagree. This is not “buzzword” usage. You might not be old enough to have hooked Beige Boxes up to hard phone lines, but skimmers like this, that attach to solder joints (wires), would pretty much be the *definition* of “wire tapping”. I could wire tap your phone hard line doing a MitM attack as you suggested, but it would be easier to just clip into the wires outside of your house. Or similar to this attack, tap the wires leading to your phone’s microphone inside of your home telephone. Traditional ATM skimmers don’t touch the wires at all usually. I think the word wiretap was used appropriately here. You just seem to presume it means tapping different wires.
Excellent response, Matt. I agree. Bottom line is this: Mr. Krebs does not need clickbait headlines; anybody who knows anything knows where to find the best blogs on infosec… right here.
Agree Steve. Keep up the great work, Brian! The security industry has nothing but respect for you. Ignore the n00bs 😉
I have indeed been delivered a drop-shipment of grey boxes and hardwired everything together (and I know what a Token Ring is, thank-you-very-much). I even got me some suspenders and a plaid shirt in the closet with moth-holes in ’em.
This is more accurately called an Eavesdropper because the “only thing wired” is the pin-hole camera synced to the mag-stripe reader. Usually there are two non-connected devices. It is still a mag-stripe reader (usually on a motorized reader & not dip). There is -no- wire on the card reader that is stripped and tapped. There’s no listening or sniffing of data over a wire of any kind. Therefore – there’s no wiretap. Period. I’ve removed them, recently. Hands-on. I know of what I speak. I can send you photos from my phone.
The more shocking/amazing development is the sophistication of these overlay stickers, and the hollowing out of PIN Shields to hide the cameras in. That’s taken us all aback – because the shields are being weaponized against us. I mean, our first inclination when we saw 1.5″ to 3″ holes drilled into the ATM was an Endoscope attack for Jackpotting. That made sense. Except the location for this stuff was next to the card reader. This is just – skimming. Data theft – one card at a time.
We got that alert – directly from the sender with the SS. Long-standing relationship there (and the Task Force). Whether the DoHS used that language or not – it’s still overt. We forwarded the original alert to all of our affected departments, with reasonable expectations. Today – some of those same people sent knee-jerk “OMG!!! SKY FALLING” requests for “what the hell are we gonna do about this? – AHHH!” – just because of this very article – and the headline. The shock factor from something called “wiretapping” is certainly greater than “eavesdropping” or “crooks get more crooked”.
Clickbaitish? Do you think the term wiretapping in this context was something I came up with? It’s straight from the Secret Service’s own advisory. What’s more, it’s a quite accurate description of what’s going on.
I know the Secret Service has its hands in a pretty diverse batch of stuff. I guess they’re publishing Listicles now?
You won’t believe what scammers are doing now!
Defending the President from bodily harm and investigating counterfeit money… I guess?
It amazes me that someone could actually drill a 2″ – 4″ hole in an ATM without attracting attention. This could take many minutes to do and if the drilling is through steel or aluminum, it would be very noisy.
A hole cutter saw bit and a powerful battery powered drill can make quick work of any metal (short of armor) – even the armor on some ATMS isn’t thick enough to keep them from drilling through in seconds. The sound might even be just a short squeaking noise.
A companion problem would be keeping the filings from messing up the electronics inside. Vacuums help — but that’s even more noise. Moreover, I have trouble imagining that just a short squeaking noise would describe drilling through something even as thin as a computer cabinet.
Sean,
My thoughts too after reading about this “procedure”. As a retired construction foreman, there is going to be aluminum/iron filings/dust and residue at the entry point. Very find dust that adheres to everything.
Since these bums are not cabinetmakers, it behooves the ATM user to become v-e-r-y circumspect at the area[s] mentioned in the article. Move the face plate and PIN pad shield a bit.
The holes are smooth-edged and no bits or scrap is around them. All of our drilling attacks have been on the plastic only (and the vaults are pretty damn thick – so there’s no getting in there).
When they lay the overlay sticker over the hole or re-cover the card-insert display – you cannot tell anything has been damaged. The overlays are so good they fool seasoned techs – until they notice the extra framing/edging around the receipt printer area. On the insert-display, unless there is damage to the plastic cover itself (stress fractures or web fractures in the corners) it is very hard to tell.
We’ve watched our DVR footage to observe these guys (usually two people per install) post-event and we cannot see everything for sure. But, they bring a tool bag or kit with them and it’s almost scary how professional they are about smoothing the holes out and inserting the devices onto the card reader. One of my guys who removed one a couple of months ago couldn’t stop bragging on these installer’s ingenuity and craftsmanship. He’s young but still.
Imagine a privately owned store with an ATM. Store closes, owner drills hole, sets up skimmer and voila. Or, maybe its a trusted employee. Perhaps its at 3am on a Sun in a small town, remote gas station, dead part of town etc. Perhaps its done in broad daylight in a busy area with 5 or 10 people running interference. Perhaps they were dressed up as ATM techs. There’s a 1001 ways this could be accomplished.
Secret Service needs to learn that solder is spelled with an L.
It’s hard to cover your hand entering the PIN when you are in a car. You’re using your left hand to enter the number while your right hand is inconveniently located inside the vehicle. Seriously though, you would need some sort of wearable cover for your left hand. Might try to make one.
Drive thru ATMs… an example of convenience trumping security it seems.
I can two-hand drive-up ATMs without issues, but I also refuse to get an SUV so maybe some common sense is in order. If the problem is caused by a cartoonishly oversized vehicle, try getting something practical.
Practicality is relative. Your tiny Chevy Spark may be wonderful for you and your three cats but it won’t do a hell of a lot of good for the family of six and their Malamute.
Why didn’t the fbi put something out? Seems suspicious.
Because financial and electronic-based crimes involving financial institutions falls under the jurisdiction of the Secret Service.
Why didn’t the fbi put something out? Seems suspicious
REPEAT: Because financial and electronic-based crimes involving financial institutions falls under the jurisdiction of the Secret Service. duh!
Just a question: Why don’t the owners of ATM surround their machines with lots of cameras? Wireless, or even wired cameras are very inexpensive these days.
Say, you got 1,500 ATMs, need ~3,000 cameras, a network with the bandwidth and DVRs/camera system manager. So then what? Going to hire 1,500 people to sit around and watch cameras 24/7? At the rate of fraud, a bank would need to lose what … ($15/h*24*365*1500) dollars a year to justify avoiding it? It ain’t the price of the cameras.
As others already posted, extra camera require more people to monitor them. The entire purpose of ATMS is to reduce the number of people on the payroll.
I am not surprised… it seems like these guys get more efficient at finding ways to siphon siphon siphon…
This year alone I have came across two Bank of America Arms that were certainly tampered with. One had a very loose pin pad and another one’s card slot was literally…. missing. I would have uploaded photos but no option. I called the diebold tech number and they fixed both in a jiff.
This is a track data skimmer and they use magnets to attach to ATM?
Good luck to them!
Does this mean it’s safer to use a phone with NFC to access bank services at an ATM than a physical card? Of course I suspect increased usage like that would lead to cloning NFC credentials too.
Short answer: yes. Contactless/cardless is far more secure. Tokenization gets us about as close to foolproof (for 2018) as you can.
Best ATM solution – don’t use them. Although I am partially responsible for our FI’s ATMs, I have not used an ATM myself for over 20 years. It’s a profitable scam. If you can’t keep enough cash on you for your weekly cash expenses, you need budgeting lessons, not a machine to skim your funds.
This, 1000%!
The endoscope is the inexpensive type used by car mechanics that just attaches to your phone, tablet or laptop. Not medical endoscopes, though the reference gives the reader an understanding of the concept. They’re only about $25 online and used by most mechanics to look inside engines and transmissions to check for wear and to help troubleshoot issues.
Interesting, thanks for the good read. Just one comment. Is the new overlay optically clear? Polarized? And visable to the keyboard? Or the camera? New vectors?
Here in Brazil we use fingerprint scanners at ATM´s (wipe after use to prevent fraude) and control questions that change place and to answer you do not use the numpad, but the buttons on the side of the screen or the touch screen.
Why do they not have this in the USA ?
Those seem like security theater to me. Fingerprint and other biometric scanners are almost always easy to defeat with a replay attack, unless the scanner is constantly being watched for tampering. Plus, once your info is out there, there’s no way to change your credentials! Control questions can easily be read with a camera or via MITM.
Too bad the Secret Service doesn’t know how to spell “solder”.
too bad no one will want to spell your name
I have seen this attack before and it is quite devastating. There are a couple of things to note. They keep things as flush as possible and come in teams. The camera sometimes is inside the custom made to fit molex connector light. Just like gas station skimmers they can use the internal power of the ATM which can result in one hell of a cash out if not detected by an inspection.
This is not a “cash out” attack. This is a data collection attack.
I think Real McCoy was talking about the payout from all the counterfeit cards that could be made and used as a result instead of a cash out.
Alternatively use Bitcoin and be your own bank. Banks are so oldskool and unnecessarily in most cases.
Yes i use bitcoins because fraudsters use secure bitcoins too.
Fraudsters will not steal from fellow fraudster brothers.
Somewhere the fraudsters need to keep their wealth stored safe too so follow the criminals and you will be safe.
Btw… the secret service is big joke fbi is nothing more then just group of guys who waiting for pay checqe
They dont do much work otherwise no any fraud in usa.
Why you americanos pay for them ur tax money and u still get robbed daily i dont undestood.
And to read those articcles its look like usa is cartoon not even real country.
Looks like i should back my stuff and come to usa with friends and will find ways to make money there…since money is just everywhere just be man enough and take it.
No wonder why all eastern europeans and africans go to usa to make money.
Its such open country without any defence..looks like they can afford weak security in usa.
Fraud and losses not problem for usa goverment and people i guess they only know how to watch baseball on tv…
Funny life
BrianKrebs:
Thank you for your reporting on important life topics.
Do you know if this “only” impacts the old slider ATM cards or is it hitting the chip based ATM’s also?
Regards.
Brian, in an attack like this it doesn’t matter. Even newer chip-based cards store card data on the mag stripe. Skimmers target mag stripe data by including an extra mag stripe read head that records anything that passes by. So, yes, this impacts chip-based cards as well.
Maybe destroy the magnetic stripe and only use the chip then? I’m not sure if this would be feasible in the US but in Finland I dont remember the last time I needed the stripe since the chip or NFC can be used everywhere.
Then again when using the chip at ATMs, the card is not inserted all the way so maybe a skimmer can’t even read the stripe?
Agree with others that it is funny that the Secret Service cannot spell “solder.”
Does anyone know of a way to shield the mag stripe on a card?
I’m thinking of a removable lead strip or something similar that would prevent a thief from accessing this information, yet allow the consumer to peel off the strip if needed to performed swiped transactions.
Has anyone heard of such a device? Can’t seem to find anything like this on a cursory search of the internet.
Maybe something like 3M Foil Tape 3381 Silver, e.g. https://www.amazon.com/3M-Foil-Tape-3381-Silver/dp/B00A7I5L86/
but might be difficult to peel off.
If you are the victim of this kind of attack does the bank cover your losses?
If so, I’m not going to worry about it too much.
This would be difficult to do in countries like Singapore.
On another hand I’ve seen some recent ATM machine designs here, that if a person is a bit short and using the machine, the person in the que would just read their balances of the screen from 1-2 m away or even a passing by person.
what’s needed is to force this banks to update their ATM machines. many of them are still using XP to start with.
and why the banks don’t physical secure the ATM from drillings and such?
the blame is on the banks.
I recently visited my local bank about some fraud on my card. During this visit I found out that the gas station was aware that one or more of their pumps were compromised but did nothing to warn customers or to remediate the issue. Literally, when the bank called and said “Hey you might want to check your pumps because we have gotten a couple of reports of fraud from customers who have used your pumps” the reply was “yeah, we know.” And that was it. I guess when you are not being held responsible for the fraudulent charges, you have zero incentive to do anything about it. EMV at the pump can’t come soon enough. I know it isn’t bulletproof but at least they can’t just steal the magstrip information straight away.
Bank customers will continue to NOT cover their PIN hands as long as the banks are responsible for all monetary losses. The customers have no skin in the game. Customers who are shown to not cover their hands, should be held responsible for 40% or $500, which ever is less. Then, you’ll see a huge increase in the number of customers who cover their hand when entering the PIN.
Most devices have a cover built into it which people use. I use my phone to the point that my card never goes in to the ATM slot simply due the level of sophistication that evolves.
Those covers are gross and full of germs. The next time your hand touches one, think of the last nose-picker who had their fingers in there.
Carry disposable gloves, people.