Cloud hosting provider Dataresolution.net is struggling to bring its systems back online after suffering a ransomware infestation on Christmas Eve, KrebsOnSecurity has learned. The company says its systems were hit by the Ryuk ransomware, the same malware strain that crippled printing and delivery operations for multiple major U.S. newspapers over the weekend.
San Juan Capistrano, Calif. based Data Resolution LLC serves some 30,000 businesses worldwide, offering software hosting, business continuity systems, cloud computing and data center services.
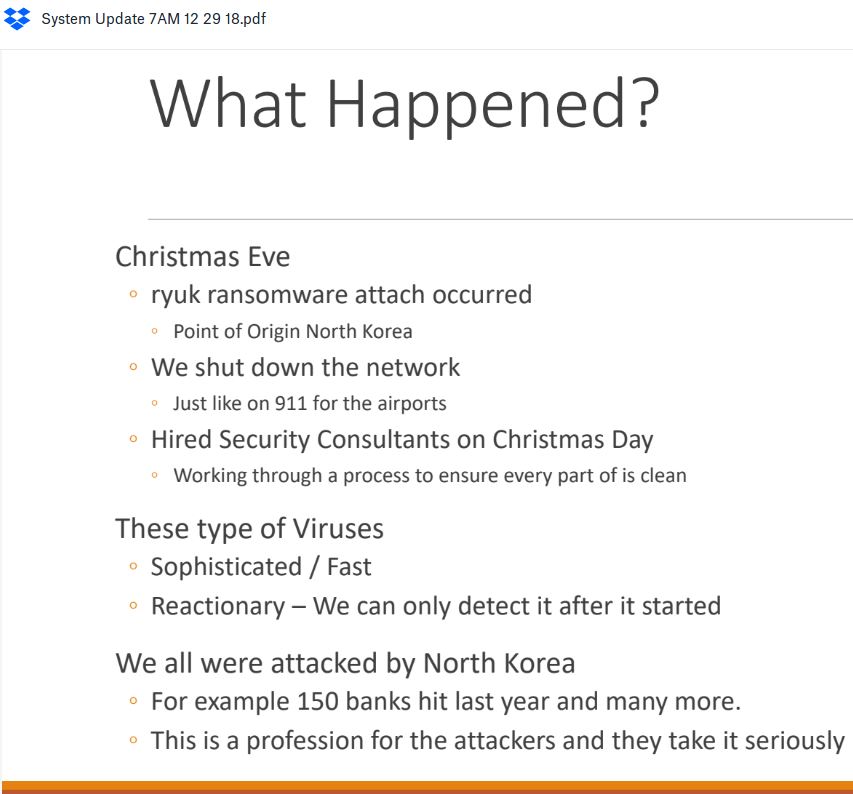
The company has not yet responded to requests for comment. But according to a status update shared by Data Resolution with affected customers on Dec. 29, 2018, the attackers broke in through a compromised login account on Christmas Eve and quickly began infecting servers with the Ryuk ransomware strain.
Part of an update on the outage shared with Data Resolution customers via Dropbox on Dec. 29, 2018.
The intrusion gave the attackers control of Data Resolution’s data center domain, briefly locking the company out of its own systems. The update sent to customers states that Data Resolution shut down its network to halt the spread of the infection and to work through the process of cleaning and restoring infected systems.
Data Resolution is assuring customers that there is no indication any data was stolen, and that the purpose of the attack was to extract payment from the company in exchange for a digital key that could be used to quickly unlock access to servers seized by the ransomware.

A snippet of an update that Data Resolution shared with affected customers on Dec. 31, 2018.
The Ryuk ransomware strain was first detailed in an August 2018 report by security firm CheckPoint, which says the malware may be tied to a sophisticated North Korean hacking team known as the Lazarus Group.
Ryuk reportedly was the same malware that infected the Los Angeles Times‘ Olympic printing plant over the weekend, an attack that led to the disruption of newspaper printing and delivery services for a number of publications that rely on the plant — including the Los Angeles Times and the San Diego Union Tribune.
A status update shared by Data Resolution with affected customers earlier today indicates the cloud hosting provider is still working to restore email access and multiple databases for clients. The update also said Data Resolution is in the process of restoring service for companies relying on it to host installations of Dynamics GP, a popular software package that many organizations use for accounting and payroll services.

A status update shared by Data Resolution with affected customers on Jan. 2, 2018 shows the company is still struggling to restore services more than a week after the attack began.
Cloud hosting providers are often pitched as a way for companies to increase security and to better protect themselves from threats like ransomware, which scrambles data on infected systems and demands payment in exchange for a digital key needed to unlock affected systems.
At the same time, cloud providers represent an especially attractive target for ransomware attacks because they store vast amounts of data for other companies. In 2017, cloud hosting provider Cloudnine was hit by a ransomware attack, leading to an outage that lasted for several days.
Much depends on security practices maintained by each provider, according to an MIT Technology Review story last year that named cloud ransomware attacks as a top security concern for 2018.
“The biggest cloud operators, like Google, Amazon, and IBM, have hired some of the brightest minds in digital security, so they won’t be easy to crack,” wrote Martin Giles. “But smaller companies are likely to be more vulnerable, and even a modest breach could lead to a big payday for the hackers involved.”
A source at a company that uses Data Resolution to manage payroll payments told KrebsOnSecurity that the cloud hosting provider said it did not attempt to pay the requested ransom, preferring to restore systems from backups instead.




I can’t understand this. How can they claim the point of origin of a cyber attack in such a confident voice?
Is North Korean Cyber Force composed of secret agents of DataResolution.net ?
Yep. I can’t even see how they could say yet with confidence that data wasn’t taken, when they’re still focused on restoring service.
I was wondering the same thing Brian! And this begs the question how will they determine or conclude information was stolen or not!
Isnt it highly likely that ALL of their determinations are coming from a company like Mandiant or whatever IR team theyve hired? Perhaps their surety is based on the IR teams surety?
No way they can confirm it that fast. I have been doing IR for a long time and its just not possible to say nothing was exfilled in that short of time. Depending on the size of the cloud host or network it will take a few weeks to have moderate confidence at best.
In SQL Server, one thing that can be done to try to detect data extrusion is check the query plan cache for sql statements that look greedy, and/or are trying to enumerate assets.
Unfortunately, this cache is stored in RAM, and often a reboot or a service restart seems to be a common knee jerk reaction, thus wiping out useful forensic evidence.
If the plan cache is still intact, and not too old, one actually has a pretty decent chance of detecting data extrusion, though it tends to be a lot of work.
To be fair, if the host is virtualized its possible to checkpoint the state of the system at a point in time, then save that state to disk before shutting it down. As a result you can roll back to that saved state and view the current contents of RAM even though the system was subsequently shut down.
Of course if they compromised the virtualized host then it gets more complicated but access to virtualization hosts are normally tightly restricted.
“data extrusion”?
Related to data extraction?
Michael, check this site out,
https://whatis.techtarget.com/definition/data-exfiltration-data-extrusion
Because attribution creates a welcome distraction from the recovery and paints a clear picture of the ‘determined attacker’ as the bad guy (whilst we figure out what basic controls failed – or failed to exist- to facilitate this breach)
Interesting update from the company. Grammar off, mis-spelling. Reminds me of some of the spam emails I get in my inbox. Makes me wonder if the PDF is authentic?
Well, when I called the company they basically said everyone was too busy responding to the situation to take my call. So my guess is their response to customers has been pretty rushed
That’s just what I was thinking. Their message to customers would make me feel less secure and less sure that their whole communications mess has been taken over by a rogue – not necessarily the NORK.
I agree to this.
Most of the attacks like this is most likely can be attributed to a disgruntled employee. Think of the what they’re claiming “a compromised login account..”. No matter how excellent security is, the HUMAN factor is the weakest link.
I was wondering the same thing. Such mistakes would not instill confidence in me if I were their customer.
Also – what on earth is, “We shut down the network just like on 911 for the airports.”
Are they really comparing the grounding of all air traffic on 9/11/2001 to shutting down their network in response to a ransomware attack.
If so, that is disrespectful and despicable.
How many people were murdered as a result of in their ransomware attack?
Brian I’d agree wholeheartedly. On the healthcare side ransomware is just assumed as a breach pending a few technical get out of jail free specifics.
My only direct knowledge of cloud services is with VPSes. But aren’t all the customers in virtualized machines? So somehow the virus gets on the hypervisor? How much outside access would that machine get? It should have internal access only.
I’m not sure from an implementation perspective, but technically, the hosting side is software that gets updates, and something always has a key to perform those updates.
So, it’s generally possible to infect.
Previous Ryuk infections have been preceded by Emotet and/or TrickBot infections. See last year’s incidents at the North Carolina water utility ONWASA and the Alaskan town of Valdez: https://blog.barkly.com/north-carolina-water-utility-ransomware-emotet
Emotet and TrickBot were two of the most active trojans of 2018 and the amount of infected computers out there is huge. Ryuk (and other ransomware) operators may be combing through these bothers and purchasing access to target networks they consider promising.
Here’s a good CheckPoint blog on the trend: https://blog.checkpoint.com/2018/10/23/ransomware-stopped-working-harder-started-working-smarter-botnets-phishing/
Appears to be on the rise. Orgs that have been shrugging off Emotet/TrickBot infections as minor should definitely be taking notice.
Thank you Jonathan for those links:
I notice CheckPoint indicates that the bots that take over the enterprise take advantage of ‘misconfigured’ Active Directory and Group Policy. So I assume if those two are properly hardened, these bots cannot gain control.
The only problem with that, is if the attackers are using RDP and are not stopped by firewalls or gateway blocking, then the attacker could probably gain permissions to modify both of those and configure them toward his bad ends anyway.
Do you, or anyone else here agree? Maybe the old Microsoft way of hardening the system are no longer valid?!
One of the advisories released to clients indicated that the company would no longer allow RDP connections, so your hunch may be correct.
Bad guys brute-forcing RDP or purchasing access to compromised RDP accounts is certainly a big, hairy problem. This post from UC Berkeley has some good suggestions for securing RDP: https://security.berkeley.edu/resources/best-practices-how-articles/system-application-security/securing-remote-desktop-rdp-system
TrickBot has a bunch of modules it uses to harvest credentials from various sources (email, browser, LSASS, etc.). It then sees what it can access with those credentials and harvests more, attempting to escalate its way up to domain admin creds. Sean Metcalf has a very good, meaty post on “Attack Methods for Gaining Domain Admin Rights in Active Directory” worth checking out that also includes mitigations: https://adsecurity.org/?p=2362
Thanks to both of you!
Attribution is hard and for them to say it’s North Korea is comical right now. I firmly believe that more than 60% of the so called state sponsored attacks are not state sponsored at all. With modern tools like metasploit and others it is not hard to launch a ransomware attack and it is trivially easy to launch said attack from servers in other countries as well.
Exactly. Data breach response playbook, rule #1: Blame the breach on advanced persistent threat actor whose capabilities were far and away above most security systems ability to prevent or detect.
Not necessarily true. Many SMB’s rely on the IR team they hire to do their incident response. Ive read about a few SMB’s in Canada and they didnt blame the breaches on an APT, they simply trusted what the IR company told them.
I would hit the roof if I was their customer. I wonder if their business will be able to recover. I also think blaming North Korea is somewhat premature !
Sure, let’s blame it on North Korea. Because blaming parties that would not defend themselves is such a high class act.
It is not a good sign when your first move is to pass blame and involve other parties.
I disagree with this article regarding the ransomware coming directly from North Korea with it’s 1024 IP number range(s) So much malicious spam and or abuse is coming from mainland China’s IP numbers that it’s becoming down right ridiculous.
More then likely North Korea is using China’s ISP’s to do it’s evil bidding for them . That’s if you can 100 percent prove that the ransomware is coming from
the government or hackers in North Korea.
Check out the stats here to see what I mean.
https://(www)(dot)abuseipdb.com/statistics/
Does anybody know if the settings in the Microsoft Management Control (MMC) can still prevent such takeovers with the newest Ransomware? I’ve been using the free version from the former Foolish IT for quite a while on my honeypot, and although the malware was able to turn the screen black – eventually a Windows error tag appears saying that permissions are rejected for this operation ( or similar error message), and the PC recovers easily on Ctrl-Alt-delete, so you can run CCleaner to remove the malware from the temp files. I always reboot just to see if the malware is still active. I also do an extensive rescue scan to make sure it is gone.
I know John Nicholas Shaw used to offer an Enterprise version of his Cryptoprevent software, but I have no idea how it would apply to large data centers with SQL servers. The name has changed for the source of the freeware still offered on MajorGeeks, but many of the comments there don’t like the intrusive changes made to said MMC and recommend against it. However one could make the changes to the MMC themselves if they were highly educated in how to setup the Group Policies and/or snap-ins required to make it work, I wouldn’t doubt if those changes number in the 100s at least.
Minor correction – should be ‘Console’ instead of Control on MMC.
I suspect either the hired security company or FBI said to report it was NK. If there are any FW logs that say that, is only a guess. Which would also be the tool to decide if any data was exfiltrated, depending on how much access the haxorz had.
Personally I consider china and NK as one technically malicious pile. We should be putting sanctions on china, but we’ve let them have most of our manufacturing – so they have pretty much won the economic war they planned, all they have to do is stop shipping. I doubt the government would give a hoot about people there going without food.
If the attacker doesn’t get his ransom, perhaps he will then start looking at the encrypted data to see if he can at least get some revenue for it for his trouble. If they have access to news like this, they may already know they have some good information.
Regards,
Who wrote that last bullet about North Korea? It speaks like a 6th grader would talk. 150 banks got hit last year so 1) what does that have to do at all with this incident? 2) that means “All” were hit by North Korea? 3) Nice redirect. I’m sure customers rested easy by this keen damage control statement.
Jesus Christ.
He was the hacker?
How many ransomware attacks have been Mac- or Linux-based? I think zero.
Businesses need to rethink using Windows, which is only best for playing games nowadays. Even IBM corp uses over 200,000 Macs internally.
All these harrowing ransomware attacks against Mersk, Merck, FedEx, City of Atlanta, LATimes, etc etc etc have been Windows based.
M, The reasons attacks are on Windows is due to that fact that is where the money is for attackers. They are what runs “business” if mac or Linux had market share for these types of workloads, they would likely see large scale attacks as well. There is nothing inherently secure about Mac OS or Linux… in fact linux webservers are frequent attack targets.
I don’t think it’s as straightforward as that. What we need is for companies to stop allowing corporate computers to be used in a similar way to home computers, that includes internet and e-mail access.
Even in “locked down” environments your average Infosec will see breaches left, right and center within moments of walking in. Nobody is picked up for these and we treat breaches as run of the mill every day issues.
Janice has opened that e-mail and gotten a virus again.. ha bloody fool. When in fact if Janice had been found stealing $5 of paper it would have been treated more seriously but as it’s just a virus – IT can sort that, it only costs $100+ of time to re-image that PC right?
If we move to Linux or Mac we’d just find these issues following us.
It’s much greater than zero. Hoping bad guys won’t get you because your servers are Linux/Mac could be a costly delusion.
https://nakedsecurity.sophos.com/2017/06/15/more-mac-ransomware-666-and-7-days-to-pay/
https://www.bbc.com/news/technology-40261693
https://www.bankinfosecurity.com/linux-killdisk-ransomware-cant-decrypt-a-9619
https://www.carbonite.com/blog/article/2017/08/ransomware-threatens-linux-servers-especially-web-servers
Instead of thinking 0, you could do a quick search.
> Posted [1] on March 6th, 2016 by Graham Cluley
> Mac owners who use the open source Transmission BitTorrent client are being warned that a version of the installer was distributed via the app’s official website, infected with a new family of ransomware.
> Posted [2] on February 23rd, 2017 by Jay Vrijenhoek
> Security researchers published details yesterday on a new ransomware for Mac, which calls itself “Patcher.” The file-encrypting ransomware program finds its way onto macOS systems through BitTorrent websites, masquerading as an Adobe Premiere CC or Office 2016 patcher. Intego’s malware research team has updated its VirusBarrier anti-virus definitions to detect all components of the ransomware, identified as OSX/Filecoder and OSX/Filecoder.fs.
> List of Mac viruses, malware and security flaws [3]
> Wondering if it’s true that Macs are safe from viruses? Here are some of the recent malware attacks and security threats that Mac users have suffered
> By Karen Haslam | 25 Apr 18
[1] https://www.intego.com/mac-security-blog/mac-users-hit-by-rare-ransomware-attack-spread-via-transmission-bittorrent-app/
[2] https://www.intego.com/mac-security-blog/patcher-ransomware-attacks-macos-encrypts-files-permanently/
[3] https://www.macworld.co.uk/feature/mac-software/mac-viruses-malware-security-3668354/
Endpoint protection can be implemented to protect RDP so even if passwords have been passed on if user is not on same authorised subnet they will be blocked. (It won’t protect against a compromised remote access host eg keylogged, that is authorised to connect). One would hope if they are a commercial grade service provider they would at least implement endpoint protection on their own DC’s and that they implement correct user policies and password changes for staff changes so it may indicate they don’t really know how the network has been compromised and are stopping RDP services to try to stem the breach.
I totally agree.
The problem with clouds is that sometimes they rain
And when it rains, it pours…
Managed Service Provider (MSP) does not offer higher level of security, than the companies can provide for themselves. One could easily argue that the MSP provided security is even less than most companies. That’s the nature of shared networks, servers, etc.
It’s one of the reasons why APT targets MSPs, why target a single company when targeting an MSP results in access to multiple companies data? Ryuk, and other ransomware, can also be utilized by hackers against MSPs for monetary gain. The fringe benefit of doing so? Attributing the attack to a state actor allows the hackers to stay in the shadows.
Yeah, when it rains, it pours…
curious that they “hired security consultants on Christmas day”…does that mean they had none previously?, or that they contracted for additional resources from a 3rd party incident response firm?
Martin Giles is probably not a great source Brian. To list IBM as a company who has great security right after it was disclosed that they got hit with Cloud Hopper is idiotic. Just because a company is large means ZERO in terms of security. Amazon and Google did set their environments up well so they are able to isolate damage in an automated fashion so you won’t see massive breaches. Its all about an automated containment and segmentation strategy, some companies get it and 95% of companies don’t. The issue is not cost, all of the tools are available out of the box for these strategies, its all about getting the right talent and taking security seriously. But that takes competent management and we just don’t see that very often in companies.
So what’s the latest? Nothing on their company website about it, in fact I find it strange that this occurred on Christmas yet 3 days later on the 28th their Company News page has new article entitled “The Support You Need, When You Need It” – ironic?
…though perhaps not as ironic as the last item they posted before the event?
https://www.dataresolution.net/understanding-disaster-recovery-and-its-impact-on-your-business/
I WANT MY DATA!!!! Does anyone know why they cant give us the data and I put it into my own environment, even temporarily.? I have a bunch of clients who have not had access to their books and records since the 24th. It is now nearing the end of the day on the 3rd. I am not sure when this nightmare is going to end.
I would rather host this onsite while they take forever to rebuild what they neglected. They blamed North Korea day 1, and then the next meeting they wanted to state facts about how LA times got hit by this too… well the fact is that LA times got up and running the next day.. why couldnt they?
They mentioned on the phone call that they are restoring 40 companies in parallel and that it is taking 1-8 hours. If they have 800 servers or 30,000 clients… the math says thats going to take WAY TO LONG.
They also are saying they are going from tape to disc. Can anyone tell me more about this process and why they used tape? is that a good security measure?
Anyone have suggestions how I can make them give me my data?
WTF !? No Timeline, down for 10.5 days now. This is a mess.
We were not notified by them, and it took 2 days to even get through to find out about the compromise after Accounting realized they could not get in. We subscribed to and get “System Update” Emails, promised every 4 hours, which are identical with no actionable status updates. We had calls Mon, Wed and Fri (1/4), where all the chats asked the same questions:
* what is the schedule for recovery? They spout nonsense about not being able to predict, don’t want to be wrong, etc. They also have stated it will “take days, not weeks” IN EVERY CALL. It has been 12 days, so in 2 more, it WILL be weeks.
* Can I get my DB, so I can stage it myself? Here is a quote from a slide:
It must be cleaned for “liability reasons”. A few people asked today if they could get it after signing a liability waiver. The question was not addressed, after being asked a few times.
They seems to have relied heavily on Veeam, which had its data compromised and encrypted.
*
Dude,
You have your business records in a cloud, but had no local copy or backup to a different cloud? Why?
Dude, we pay a lot of money to have someone who is a expert in the cloud industry to provide these types of recommendations for us. They have failed as professionals.
Kids are taught to backup their data. Lesson plan below.
I don’t understand adults who don’t grasp the concept.
https://alex.state.al.us/lesson_view.php?id=24826
you are totally correct. Data resolutions clearly runs their business like a bunch of amateurs. They need to take this course. They can not offer such expensive services promising 99.9 up time and multiple back ups and redundancies and then fail on those promises. Customers shouldn’t be the ones having to figure out these technical processes when it is outside their expertise/knowledge. In other terms, I surely wouldn’t diagnose and treatment plan myself for a illness.. I would leave that up to the doctors.
I am sure many people will be leaving data resolutions.
What does your contract say? Whatever your contract says is what you do, is what you do.
Hey: the company I work for is also a client of Data Resolution, and it is now day 22 and we still don’t have our data back. I wanted to reach out to you to see if you were successful in retrieving yours ? We are beside ourselves as they keep telling us its coming. Thanks for getting back to me if you can.
Pretty audacious for them to compare themselves and their response to 9/11 response lol
The compromise sequence is well known…
1. user opens a phishing mail
2. user opens a malicious attached Word/Excel doc
3. user is tricked into enabling macros that executes compromise code
Most companies could disable macros without a problem. The company system administrator can go to the Trust Center settings and “Disable all macros without notification”.
Reading this post was a great pleasure, thanks for your efforts.
I didn’t go through all of the comments, so maybe this was covered already.
They rebooted to regain control. Once they did that, the cache was cleared, forensic evidence was compromised, timestamps were lost, entry points & IPs & who knows what else were lost.
As a result, they can’t claim to know much of anything that happened because they didn’t follow basic BCP, DRP, or IRP protocols. Disconnect from network, salvage the evidence.
Then again, it doesn’t sound like they followed basic protocols for anything they did pre- or post-attack.
Two incidents that I personally experienced (here in New Zealand) put me permanently off any form of cloud-based hosting solutions.
1/ Tracking the source of a probe/attack to a cloud infrastructure company in the USA.
2/ Having a cloud infrastructure company in NZ shut down without warning over a weekend, locking several businesses out of their payroll systems on Monday morning.
After those two incidents, I laugh at any business that does not have their own equipment in-house with a dedicated team. They are IMO not a business that I wish to be dealing with, especially if the beancounters in the biz are doing it only for monetary reasons.
Government departments using cloud-based systems? Yeah, that’s not an accident waiting to happen.
Got the phone number variant as well. Is this definitely fake? Sorry if I sound naïve, just kinda freaked out.
What does your contract say? Whatever your contract says is what you do, is what you do.
WE are really getting concerned over this issue now. as if it wasn’t bad enough…still waiting for Acctg access since 12-23 and now it’s 1-14. Today, the promised availability of our backups, guaranteed to be available on friday at noon PST, still has not happened. No one is answering the phone or emmails and the webinar, scheduled for evey mondaymorning since the attack, was eerily empty this morning, with no reps from Data Resolutions and only about 10 clients…all dazed and confused. Has anyone received their data?
The company I work for was also caught up in this mess. Did you get your data back? Its is day 22 and we still don’t have our data back, and are freaking that we will never get it.
The DNS is nothing but the distributed name resolution service that is used by the ISPs or the Internet Service Providers around the globe.
Microsoft is pushing all of their ERP customers to go this way, within a few years we won’t be allowed to buy/run on-site Microsoft ERP systems. Microsoft’s cry is now “Cloud or nothing!”. They’ve already hidden links to their different packages (SL, GP, AX, which are all decent ERPs) pointing you now to “Dynamics 365” unless you know the direct urls.
Microsoft is not alone. The big-data industry wants to “own” your data. That way they “own” you.
If my company lost it’s ERP for 3 weeks, we’d be out of business.
At least if it’s my system that gets compromised, it’s my problem/fault.
There needs to be some push-back by customers against this push to the cloud. Customers need to be able to “choose” how they wish to store their data.
It’s now January 22 and I still don’t have access to my Dynamics Great Plains software that was part of the Ransomware attack. I need to produce 1099’s and am being told I should get it back this week, so far nothing.