A spear-phishing attack this week hooked a customer service employee at GoDaddy.com, the world’s largest domain name registrar, KrebsOnSecurity has learned. The incident gave the phisher the ability to view and modify key customer records, access that was used to change domain settings for a half-dozen GoDaddy customers, including transaction brokering site escrow.com.
Escrow.com helps people safely broker all sorts of transactions online (ironically enough, brokering domain sales is a big part of its business). For about two hours starting around 5 p.m. PT Monday evening, Escrow.com’s website looked radically different: Its homepage was replaced with a crude message in plain text:
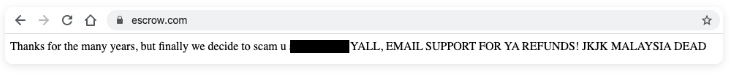
The profanity-laced message left behind by whoever briefly hijacked the DNS records for escrow.com. Image: Escrow.com
DomainInvesting.com’s Elliot Silver picked up on the change and got a statement from Matt Barrie, the CEO of freelancer.com, which owns escrow.com.
“During the incident, the hackers changed the DNS records for Escrow.com to point to to a third party web server,” Barrie wrote, noting that his security team managed to talk to the hacker responsible for the hijack via telephone.
Barrie said escrow.com would be sharing more details about the incident in the coming days, but he emphasized that no escrow.com systems were compromised, and no customer data, funds or domains were compromised.
KrebsOnSecurity reached out to Barrie and escrow.com with some follow-up questions, and immediately after that pinged Chris Ueland, CEO of SecurityTrails, a company that helps customers keep track of their digital assets.
Ueland said after hearing about the escrow.com hack Monday evening he pulled the domain name system (DNS) records for escrow.com and saw they were pointing to an Internet address in Malaysia — 111.90.149[.]49 (that address is hobbled here because it is currently flagged as hosting a phishing site). The attacker also obtained free encryption certificates for escrow.com from Let’s Encrypt.
Running a reverse DNS lookup on this 111.90.149[.]49 address shows it is tied to fewer than a dozen domains, including a 12-day-old domain that invokes the name of escrow.com’s registrar — servicenow-godaddy[.]com. Sure enough, loading that domain in a browser reveals the same text that appeared Monday night on escrow.com, minus the redaction above.
The message at servicenow-godaddy[.]com was identical to the one displayed by escrow.com while the site’s DNS records were hacked.
Barrie said one of those notes stated that certain key changes for escrow.com could only be made after calling a specific phone number and receiving verbal authorization. As it happened, the attacker went ahead and called that number, evidently assuming he was calling someone at GoDaddy.
In fact, the name and number belonged to escrow.com’s general manager, who played along for more than an hour talking to the attacker while recording the call and coaxing information out of him.
“This guy had access to the notes, and knew the number to call,” to make changes to the account, Barrie said. “He was literally reading off the tickets to the notes of the admin panel inside GoDaddy.”
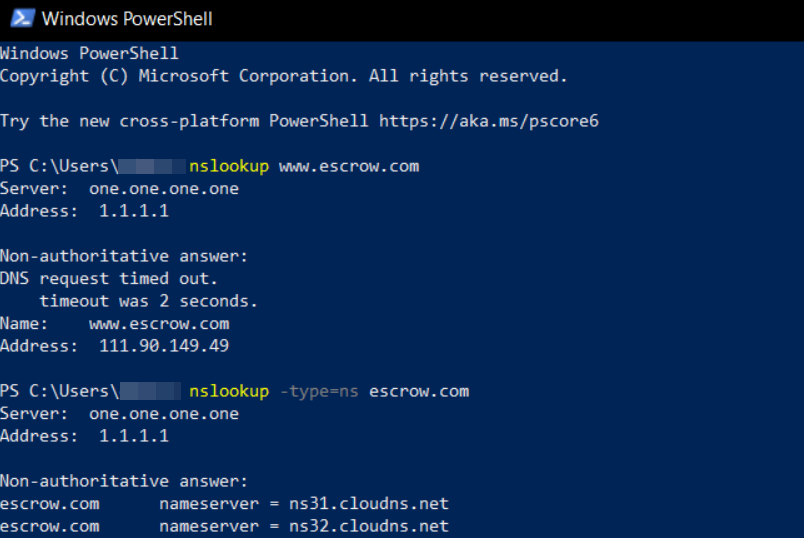
A DNS lookup on escrow.com Monday evening via the Windows PowerShell built into Windows 10. Image: SecurityTrails
In a statement shared with KrebsOnSecurity, GoDaddy acknowledged that on March 30 the company was alerted to a security incident involving a customer’s domain name. An investigation revealed a GoDaddy employee had fallen victim to a spear-phishing attack, and that five other customer accounts were “potentially” affected — although GoDaddy wouldn’t say which or how many domains those customer accounts may have with GoDaddy.
“Our team investigated and found an internal employee account triggered the change,” the statement reads. “We conducted a thorough audit on that employee account and confirmed there were five other customer accounts potentially impacted.”
The statement continues:
“We immediately locked down the impacted accounts involved in this incident to prevent further changes. Any actions done by the threat actor have been reverted and the impacted customers have been notified. The employee involved in this incident fell victim to a spear-phishing or social engineering attack. We have taken steps across our technology, processes and employee education, to help prevent these types of attacks in the future.”
There are many things domain owners can and should do to minimize the chances that domain thieves can wrest control over a business-critical domain, but much of that matters little if and when someone at your domain name registrar gets phished or hacked.
But increasingly, savvy attackers are focusing their attention on targeting people at domain registrars and their support personnel. In January, KrebsOnSecurity told the harrowing story of e-hawk.net, an online fraud prevention and scoring service that had its domain name fraudulently transferred to another provider after someone social engineered a customer service representative at e-hawk’s registrar.
Nation-state level attackers also are taking a similar approach. A massive cyber espionage campaign targeting a slew of domains for government agencies across the Middle East region between 2018 and 2019 was preceded by a series of targeted attacks on domain registrars and Internet infrastructure firms that served those countries.
While there is very little you can do to prevent your domain registrar from getting phished or tricked by scammers, there are several precautions that you can control. For maximum security on your domains, consider adopting some or all of the following best practices:
-Use 2-factor authentication, and require it to be used by all relevant users and subcontractors.
-In cases where passwords are used, pick unique passwords and consider password managers.
-Review the security of existing accounts with registrars and other providers, and make sure you have multiple notifications in place when and if a domain you own is about to expire.
-Use registration features like Registry Lock that can help protect domain name records from being changed. Note that this may increase the amount of time it takes going forward to make key changes to the locked domain (such as DNS changes).
-Use DNSSEC (both signing zones and validating responses).
-Use access control lists for applications, Internet traffic and monitoring.
-Monitor the issuance of new SSL certificates for your domains by monitoring, for example, Certificate Transparency Logs.




I hope someone is going to revoke the LetsEncrypt cert! Certainly a novel way to allow you to generate ‘genuine’ certs that could later be used for bad things…
LetsEncrypt didn’t do anything wrong. This was entirely GoDaddy’s fault.
Let’s encrypt recently celebrated their 1 billionth free tls ssl cert issued out on Feb 27, 2020.
I am guessing a fair chunk of those issued out by their certBot are abused for fraudulent purposes, due to the 0 pricetag and organisations preaching about the padlock in the URL bar to be ‘panacea’.
From the paid options looks like Sectigo (ex Comodo) have the most in fraudulent activities (via cPanel AutoSSL), but they revoke them quickly, once alerted.
I am yet to see a revoked let’s encrypt cert.
Let’s Encrypt issues only 90-day certs. They figure the bad certs are valid for so short a time, it’s not worth revoking. (I do not agree.)
They revoked a whole bunch: https://community.letsencrypt.org/t/revoking-certain-certificates-on-march-4/114864
… due to a bug in their software.
The certificate holders can revoke their own certs at any time. Doesn’t really help in this case, though.
I’m glad I gave up the whole dream of ever owning a domain name; this just let me know I was right in abandoning the whole thought.
I wouldn’t let this discourage you from owning a domain name. I have a few. I think it is less likely the underworld would go after us — there are bigger fish. I used Escrow.com a few years ago to help purchase a domain, was highly skeptical at first but was ultimately impressed with its service.
That is a very odd statement. A registrar got compromised so you are giving up on ever owning a domain??? I think you are reading a little too much into this story.
When it comes to subjects like this, it doesn’t take much for me to wash my hands of the whole mess, no matter how fractured the information dependencies are. I’m just tired of the whole thing, and how a company can have a perfectly good system, and one phishing email destroys it all. 🙁
This is the world we live in. There will always be bad players. Either we observe best practices and be prepared for the worst, or we let them defeat us completely. I’d say the article outlines best practices pretty well.
I have some domains, but, it turns out that I can’t protect my domains as well as Google can protect theirs (“Surprise!”). So it’s better for me to use Google for my email addresses than add more risk to my chain by using my vanity domains.
One thing that I’ve done to prevent anything like that happening to my domain (and maybe someone will correct me on this) — I transferred it to domains.google with all appropriately long over-35-character passwords, 2FA via OTP (via Authy or Google Authenticator), domain lock and notifications set up to my special email address (that goes right to my smartphone.)
My thinking was that Google is “notorious” for not providing “human” customer service, which is a BIG PLUS in this case. If there’s no humans involved, there’s no social engineering.
Additionally, in my case dumping Namecheap (or GoDaddy in this case) is worth the move on its own. Both are horrible services!
+1
We were looking into Gandi, but have selected Google domains for new domains.
This is a very impressive piece of reporting. I appreciate the best practices in this and other articles — I can’t be reminded too often.
I’m confused. It sounds like the attacker had access within GoDaddy and used that to change the DNS record. But why did he need to speak to someone at Escrow.com?
It looks like the attacker was trying to do more than just change the DNS settings (like move the domain somewhere else) but was prevented from doing so because instructions on the customer’s account specified that verbal permission had to be gotten from someone at a specific phone number, which the attacker then called.
I’m impressed with the quick wit of the general manager for escrow.com, who was able to keep the attacker talking for an hour and gain valuable information.
Matt Barrie is no fool. He has been involved in the IT security game for quite a while. He once had a company doing deep packet inspection at the hardware level!
Any GM he would hire would have to have their wits about them and know their stuff.
That phone conversation with the hacker must have been interesting, and perhaps somewhat bizarre for the participants.
If I called GoDaddy I’d be surprised if they picked up the phone much less helped me. And yet this guy manages to get them to presumably reset the password on a random domain’s control panel? Incredible.
In the irony department, though a signatory of the DNS Abuse Framework (http://dnsabuseframework.org/), GoDaddy demands a subpoena for the release of GDPR redacted domain registrant data related to brand/TM/IP abuse — though some other registrars do not. If I had to guess, a well-crafted spear-phishing attack on GoDaddy would have involved a branded domain name. I wonder if GoDaddy security investigators were able to find the registrant contact data from the source of the attack to aid their investigation? Statistically, that domain name registrant was likely redacted by GDPR or a privacy/proxy service. Based on GoDaddy’s relationships with other registrars did they receive cooperation from the registrar or from their own registrar operations as they tried to mitigate further abuse from the spear-phishing attack? In any case, GoDaddy has been a very active participant in the policy development process for the availability of Whois data and policy related to privacy and proxy services. Hopefully, this event will inform their participation and have a positive impact on their cooperation with security and others trying to mitigate such attacks. Perhaps GoDaddy could speak to their investigation and how they mitigated this attack to inform others on their best practices as a registrar?
This —> “…-Use registration features like Registry Lock that can help protect domain name records from being changed. Note that this may increase the amount of time it takes going forward to make key changes to the locked domain (such as DNS changes)…”
Try this
https://bitmitigate.com/
or try cloudflare
This seems little bit scary. Because godaddy hold most of the domains on the Internet.
Most do not realize that over 90% of all malware/ viruses are derived from email right now. The scope, scale, and sophistication of these phishing/ spoofing emails are incredible. I’m certainly not saying the GoDaddy employee couldn’t have done things differently, of course they could have. Be diligent. This instance certainly won’t prevent be from maintaining and buying new domains with GoDaddy. IMO they are one of the best companies it there. I get it they could be cheaper, but I’ve never had an issue that could not have been resolved with then in over 15 years of doing business with them.
in canada they had a 1cent .ca promo recently
nice post sir they write news titles to get viewers too open the links.
You might add a related video or a picture or twwo to get people sattadon
i am blogger and also a web designer i have created lot of website my website birthday wishes for bhabhi/
Wow, looks good, especially the conclusion. I was
looking for this particular topic for a couple of days throughout the nest,
but there was nothing precious, only discovered this http://www.onlinetutorforme.com/algebra-tutor/, but still so pleased to attain your post in the end.
I am keen on that theme, and I want to be always
conscious of the most recent news. That’s a pleasure to read your post and finally clarify
the issue myself.
It’s not the fault of Let’s Encrypt.