You may have heard that today’s phone fraudsters like to use caller ID spoofing services to make their scam calls seem more believable. But you probably didn’t know that these fraudsters also can use caller ID spoofing to trick your bank into giving up information about recent transactions on your account — data that can then be abused to make their phone scams more believable and expose you to additional forms of identity theft.
Last week, KrebsOnSecurity told the harrowing tale of a reader (a security expert, no less) who tried to turn the tables on his telephonic tormentors and failed spectacularly. In that episode, the people impersonating his bank not only spoofed the bank’s real phone number, but they were also pretending to be him on a separate call at the same time with his bank.
This foiled his efforts to make sure it was really his bank that called him, because he called his bank with another phone and the bank confirmed they currently were in a separate call with him discussing fraud on his account (however, the other call was the fraudster pretending to be him).
Shortly after that story ran, I heard from another reader — we’ll call him “Jim” since he didn’t want his real name used for this story — whose wife was the target of a similar scam, albeit with an important twist: The scammers were armed with information about a number of her recent financial transactions, which he claims they got from the bank’s own automated phone system just by spoofing her phone number.
“When they originally called my wife, there were no fraudulent transactions on her account, but they were able to specify the last three transactions she had made, which combined with the caller-ID had mistakenly earned her trust,” Jim explained. “After we figured out what was going on, we were left asking ourselves how the crooks had obtained her last three transactions without breaking into her account online. As it turned out, calling the phone number on the back of the credit card from the phone number linked with the card provided the most recent transactions without providing any form of authentication.”
Jim said he was so aghast at this realization that he called the same number from his phone and tried accessing his account, which is also at Citi but wholly separate from his spouse’s. Sure enough, he said, as long as he was calling from the number on file for his account, the automated system let him review recent transactions without any further authentication.
“I confirmed on my separate Citi card that they often (but not quite always) were providing the transaction details,” Jim said. “I was appalled that Citi would do that. So, it seemed the crooks would spoof caller ID when calling Citibank, as well as when calling the target/victim.”
The incident Jim described happened in late January 2020, and Citi may have changed its procedures since then. But in a phone interview with KrebsOnSecurity earlier this week, Jim made a call to Citi’s automated system from his mobile phone on file with the bank, and I could hear Citi’s systems asking him to enter the last four digits of his credit card number before he could review recent transactions.
The request for the last four of the customer’s credit card number was consistent with my own testing, which relied on a caller ID spoofing service advertised in the cybercrime underground and aimed at a Citi account controlled by this author.
In one test, the spoofed call let KrebsOnSecurity hear recent transaction data — where and when the transaction was made, and how much was spent — after providing the automated system the last four digits of the account’s credit card number. In another test, the automated system asked for the account holder’s full Social Security number.
Citi declined to discuss specific actions it takes to detect and prevent fraud. But in a written statement provided to this author it said the company continuously monitors and analyzes threats and looks for opportunities to strengthen its controls.
“We see regular attempts by fraudsters to gain access to information and we are constantly monitoring for emerging threats and taking preventive action for our clients’ protection,” the statement reads. “For inbound calls to call centers, we continue to adapt and implement detection capabilities to identify suspicious or spoofed phone numbers. We also encourage clients to install and use our mobile app and sign up for push notifications and alerts in the mobile app.”
PREGNANT PAUSES AND BULGING EMAIL BOMBS
Jim said the fraudster who called his wife clearly already knew her mailing and email addresses, her mobile number and the fact that her card was an American Airlines-branded Citi card. The caller said there had been a series of suspicious transactions, and proceeded to read back details of several recent transactions to verify if those were purchases she’d authorized.
A list of services offered by one of several underground stores that sell caller ID spoofing and email bombing services.
Jim’s wife quickly logged on to her Citi account and saw that the amounts, dates and places of the transactions referenced by the caller indeed corresponded to recent legitimate transactions. But she didn’t see any signs of unauthorized charges.
After verifying the recent legitimate transactions with the caller, the person on the phone asked for her security word. When she provided it, there was a long hold before the caller came back and said she’d provided the wrong answer.
When she corrected herself and provided a different security word, there was another long pause before the caller said the second answer she provided was correct. At that point, the caller said Citi would be sending her a new card and that it had prevented several phony charges from even posting to her account.
She didn’t understand until later that the pauses were points at which the fraudsters had to put her on hold to relay her answers in their own call posing as her to Citi’s customer service department.
Not long after Jim’s spouse hung up with the caller, her inbox quickly began filling up with hundreds of automated messages from various websites trying to confirm an email newsletter subscription she’d supposedly requested.
As the recipient of several of these “email bombing” attacks, I can verify that crooks often will use services offered in the cybercrime underground to flood a target’s inbox with these junk newsletter subscriptions shortly after committing fraud in the target’s name when they wish to bury an email notification from a target’s bank.
‘OVERPAYMENT REIMBURSEMENT’
In the case of Jim’s wife, the inbox flood backfired, and only made her more suspicious about the true nature of the recent phone call. So she called the number on the back of her Citi card and was told that she had indeed just called Citi and requested what’s known as an “overpayment reimbursement.” The couple have long had their credit cards on auto-payment, and the most recent payment was especially high — nearly $4,000 — thanks to a flurry of Christmas present purchases for friends and family.
In an overpayment reimbursement, a customer can request that the bank refund any amount paid toward a previous bill that exceeds the minimum required monthly payment. Doing so causes any back-due interest on that unpaid amount to accrue to the account as well.
In this case, the caller posing as Jim’s wife requested an overpayment reimbursement to the tune of just under $4,000. It’s not clear how or where the fraudsters intended this payment to be sent, but for whatever reason Citi ended up saying they would cut a physical check and mail it to the address on file. Probably not what the fraudsters wanted, although since then Jim and his wife say they have been on alert for anyone suspicious lurking near their mailbox.
“The person we spoke with at Citi’s fraud department kept insisting that yes, it was my wife that called because the call came from her mobile number,” Jim said. “The Citi employee was alarmed because she didn’t understand the whole notion of caller ID spoofing. And we both found it kind of disturbing that someone in fraud at such a major bank didn’t even understand that such a thing was possible.”
SHOPPING FOR ‘CVVs’
Fraud experts say the scammers behind the types of calls that targeted Jim’s family are most likely fueled by the rampant sale of credit card records stolen from hacked online merchants. This data, known as “CVVs” in the cybercrime underground, is sold in packages for about $15 to $20 per record, and very often includes the customer’s name, address, phone number, email address and full credit or debit card number, expiration date, and card verification value (CVV) printed on the back of the card.
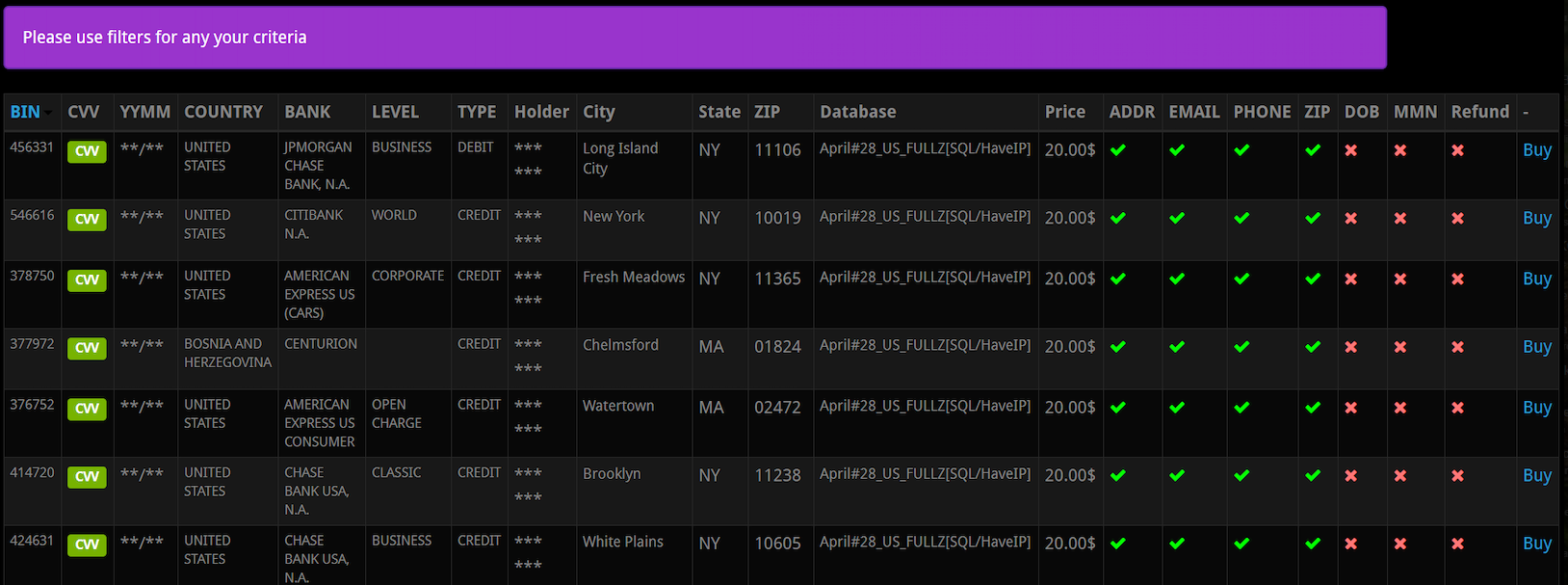
A screen shot from an underground store selling CVV records. Note that all of these records come with the cardholder’s address, email, phone number and zip code. Click to enlarge. Image: Gemini Advisory.
Dozens of cybercrime shops traffic in this stolen data, which is more traditionally used to defraud online merchants. But such records are ideally suited for criminals engaged in the type of phone scams that are the subject of this article.
That’s according to Andrei Barysevich, CEO and co-founder of Gemini Advisory, a New York-based company that monitors dozens of underground shops selling stolen card data.
“If the fraudsters already have the target’s cell phone number, in many cases they already have the target’s credit card information as well,” Barysevich said.
Gemini estimates there are currently some 13 million CVV records for sale across the dark web, and that more than 40 percent of these records put up for sale over the past year included the cardholder’s phone number.
Data from recent financial transactions can not only help fraudsters better impersonate your bank, it can also be useful in linking a customer’s account to another account the fraudsters control. That’s because PayPal and a number of other pure-play online financial institutions allow customers to link accounts by verifying the value of microdeposits.
For example, if you wish to be able to transfer funds between PayPal and a bank account, the company will first send a couple of tiny deposits — a few cents, usually — to the account you wish to link. Only after verifying those exact amounts will the account-linking request be granted.
JUST HANG UP
Both this and last week’s story illustrate why the only sane response to a call purporting to be from your bank is to hang up, look up your bank’s customer service number from their Web site or from the back of your card, and call them back yourself.
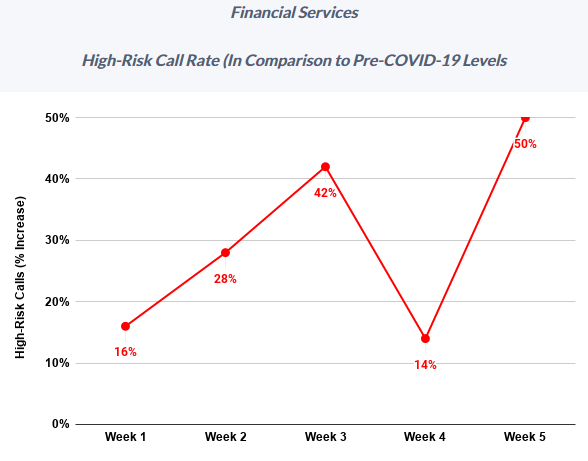
Meanwhile, fraudsters who hack peoples’ finances with nothing more than a telephone have been significantly upping the volume of attacks in recent months, new research suggests. Fraud prevention company Next Caller said this week it has tracked “massive increases in call volumes and high-risk calls across Fortune 500 companies as a result of COVID-19.”
“After a brief reprieve in Week 4 (April 6-12), Week 5 (April 13-19) saw call volume across Next Caller’s clients in the telecom and financial services sectors spike 40% above previous highs,” the company found. “Particularly worrisome is the activity taking place in the financial services sector, where call traffic topped previous highs by 800%.”
Next Caller said it’s likely some of that increase was due to numerous online and mobile app outages for many major financial institutions at a time when more than 80 million Americans were simultaneously trying to track the status of their stimulus deposits. But it said that surge also brought with it an influx of fraudsters looking to capitalize on all the chaos.
“High-risk calls to financial services surged to 50% above pre-COVID levels, with one Fortune 100 bank suffering a high-risk increase of 60% during Week 5,” the company wrote in a recent report.




…hang up and call the number for fraud…
…repeat…hang up!…
I never answer a number I don’t recognize. Period. If it is important, they will leave a message. I have a cell phone from another state. I get calls regularly from the area code that matches my old state, where I haven’t lived for eight years! They never leave a message. Callers from other states can disguise their numbers to look like they are coming from your own area code. So I just don’t engage. I have two cards, both of which are set up to send me a text any time there is a transaction. I handle everything, address changes, etc. on-line. No reason to talk to anyone in this day and age.
You’ll recognize the number calling you, they’re spoofing the number of your bank.
That is a really, really lame cop-out, stupid, rude, destructive, expensive, hurtful, and counter-productive reaction.
What if I found your wallet? (real happening, I used their driver’s license to return it to their home address).
What if the police found your elderly mother with severe dementia at a bank about a mile away from home; she was walking on autopilot across busy streets from distant memory to get there? In the middle of winter? with no coat? And you lived 2,000 miles away? (real occurance. I HATE their daughter now..
What if your house is being broken into? Your house is on fire?
You want to talk to somebody because you just got raped (and when I see John Q, I assume male-on-male rape) but for whatever reason were uncomfortable calling the police?
What if this happened to your daughter or son, and the rapist stole their purse/pants/whatever-including-phone, so they are naked on the street, calling from my phone because I saw them bloody and needing help?
Answer your goddamn phone!!!
Disagree. I stopped answering spam calls years ago. People that know me can ring my phone, 99% others can’t. People/organizations I know have other ways than the antiquated spam call system to reach me, reliably.
Many banks including TD Bank on the East Coast of The US, and throughout Canada are now using voice recognition technology for their telephone banking.
You can only imagine how easily that is spoofed as well.
Stay healthy!
It would appear that voice recognition security systems can be defeated by voice impersonators. See the study done by the University of Eastern Finland.
https://www.uef.fi/-/voice-impersonators-can-fool-speaker-recognition-systems
It is possible that voice recognition systems may not be foolproof. Here is a a study done in late 2017 (there may have improvements since then) by the University of Eastern Finland demonstrating that such systems can be defeated by voice impersonators.
The corrected link to the study is:
https://news.cision.com/university-of-eastern-finland/r/voice-impersonators-can-fool-speaker-recognition-systems,c2391188
Good information! Thanks for all you do. I’ll be using this for our anti fraud information that we share with my employees.
The banks should implement, a “two factor text” to your cell phone which you have to enter, before your recent transactions are given to you.
Getting a duplicate SIM card as the one in your phone (yes, it’s possible), can intercept that verification text to your phone.
As a long-time member of credit unions rather than banks, I often wonder if the risk for credit unions is less, more, or about the same as for the big banks. On the one hand, the target size is too small to blanket a large set of email addresses or phone numbers with fraud attempts. Yet I feel like that may make the credit union customers easier prey if the criminal enterprise is able to do a targeted attack.
Due to their smaller size, credit unions provide lower attack volumes and so can be less attractive to ‘professional’ fraudsters (the ‘amateur’ fraudsters who buy financial details are a different story). They also tend to provide a great staff / manual review : customers / cards / transactions ratio, and quicker internal communication which may limit the effectiveness of fraud MOs. This does not by any means translate into ‘credit unions are safer’ however – they can certainly still be successfully targeted by fraudsters because there are no hard-and-fast rules in this game.
Fortunately I live in a small community where everyone knows each other and can even recognize by voice. However our Credit Union was pretty vulnerable a few years ago, but hired a really good IT person whom I know, that instituted some very good practices and standards for the CU. They were even better locked down than most of the banks in the area. But the banks are playing catch-up now!
Keith,
It depends on the credit union. There are some credit unions that are larger than some banks. And mine has a good fraud detection system. At least twice they have called us when they noticed what they thought were fraudulent charges. And both times, they were right.
Fraud detection is great; but the only problem is now that Chip-n-pin is here, the bank just shuts the card down completely with each detection, and it takes longer now to clear it up. It used to be, the cashier would get a block in the POS device and a quick call to the bank would clear it up. But, let’s face it, the more secure it is the better. I’d rather be inconvenienced, that robbed blind any day!
Keith, we are and have been with a credit union for a long time. My wife got one of those calls she was smart enough to hang up. She called the credit union and found out there were no fraudulent charges. She told the person at the credit union she hung up on the fraud call and they said that was the best thing to do. Just don’t tell my wife she is smarter than me I will never live it down.
I won’t tell, but she probably already knows doesn’t she? I’m not married sorry to say, so I could be wrong on this.
“if the risk for credit unions is less, more, or about the same as for the big banks”
One significant risk that credit unions and community banks face is that their online presence is often completely outsourced to one of a small number of companies. So if, say, Credit Union A is phished and its online banking provider is compromised as a result, many, many other credit unions and banks will be affected as well.
The bottom line, unfortunately, is that financial service security is highly dependent on individual measures taken by *customers*. We cannot rely on aspects or actions of these companies for protection.
There has been lots of coverage of this risk here if you’re interested:
https://krebsonsecurity.com/tag/fiserv/
Correct me, if I am wrong…
The wife should have hung up, when the fraudster asked for the “security word”, instead of giving him/her a second one.
Most of the financial institutions don’t ask for the security word/code, or password, if they call you.
Not knowing my bank’s phone number is a good idea as well. My bank can call me and while the caller ID would show the number, it would be unknown for me…
After being on the phone for a few minutes, getting scared about fraud, and then being reassured with some trust (fraudster verified last transactions)…. it is easy to forget who called who.
A good social engineer knows how to play emotions.
Hanging up should have been done at the beginning. Or better, never pick up from an unsolicited call. Important calls will leave a voicemail. Banks can send an email or text that merely tell you to call them.
Personally, I would play along with a fraudulent call, and start giving wrong secret code words. And hope the relayed code words being wrong 3+ times… raises a red flag with the real bank support team.
I wish you were right @Otto, but here in the UK, I regularly get calls from [number withheld] “good morning Mr T, I just need to take you some security, whats the first letter of your password?”
Sometimes its genuine, and I take the time to explain why this is a bad idea, and the caller usually clicks the “awkward customer ” checkbox.
I even sent a flowchart to an insurance company, I can imagine that caused a few laughs at their lunchbreak.
I have so far never been hacked (knock on wood). But on a few occasions i have been involved with calls in hindsight i should never engaged. And after hanging up i have said to myself, “man, what were you thinking.” The obvious answer is, I wasn’t! It can be real easy to get sucked into these calls.
Agreed… “just hang up”. Better yet, don’t answer in the first place. My approach is typically to let voicemail pick up the call… then listen to the voicemail. If it was important enough, they’ll leave a message. This also permits one to listen to the message several times, and avoid the urgency-to-react factor. That’s a favorite social engineering tactic.
If from a financial institution… call the listed/trusted number, not anything from your phone, or anything someone left as a callback number in a voicemail. This approach should work to thwart most any social engineering attack. Also, one could consider placing a fraud alert on their account if it was thought to be more than just a social engineering attempt, and even then, something to consider.
Lastly… as always… freeze credit accounts on all of the bureaus!
Be mindful, and stay safe (health-wise and financially) out there people.
Cheers.
Exactly! Just as you, I will never pick up any number I don’t recognize, and even if it is one, I let my VM take the call. I will also log in to my account via the app or web and make my own inspection.
THEN I will decide what my next step will be!
Also too, iPhones have a setting that will only let through numbers in your contacts. All unknowns go directly to vm.
Android: Auto-reject calls. I added prefixes for 99% of phone numbers and spammiest local number prefixes to auto-reject–reject-listed calls don’t ring. And, I contacted phone company to turn off voicemail=I don’t care about vociemail anymore–not worth my time as most of those were spam voicemails.
you mean to tell me with all this marvelous technology that there is no way to track where the payments for the CVV files are going? Like the Bitcoin ransom payments, there shd be some way to follow an electronic trail. Shouldn’t there?
That is what my bank told me. The only action that can be taken is to reject the transaction and see if they can get the money back. I had a spoof PayPal incident lately, and apparently a crook can control his own PayPal account and make transfers just as if he were PayPal itself!! But I caught the “micro payment” early, and recovered it and blocked all PayPal XFERs from then on. I’m sure the crook got my banking account information from one of those data dumps Brian points out in his reporting. Once they automatically aggregate all the information, they probably know more about you that even you know!
Another great and useful article. And to answer the question, yes, I may well have been fooled.
Thanks for a great article. And, yes, I might have been fooled.
Brian, if someone we know gets a fishy call, is there someone we can call, or an anti-fraud business, that we can contact & describe the incident & ask for advice on whether it sounded legitimate and what to do? someone who would charge a small but reasonable fee, for giving such advice?
Not that I know of. I know so many people who can’t resist answering their phone when it rings, even when they have no idea who could be calling. I have just the opposite problem.
The best advice is to assume if your phone rings and it’s someone you don’t know, they’re probably getting ready to scam you. That’s how bad it’s gotten. I don’t even answer my phone anymore unless the call appears to come from someone I know. But even then…Anyone else — a bank, a business I patronize, whatever, they can leave a message. If I want to call them back, I will.
iOS 13 has a setting that allows one to automatically forward all numbers not on their contact list to voicemail, without the phone ever ringing. Accordingly, there can be no temptation or ability to reflexively answer such calls.
Ref: https://www.cnet.com/how-to/this-new-ios-13-feature-stops-strangers-and-spam-callers-from-ringing-your-iphone/
That wouldn’t help.
I have my credit card companies’ and banks’ phone numbers in my contacts.
Same goes for text messages, as TD won’t even verify if they sent them.
I always do business in the bank, never on the phone, and the bank manager knows that.
My 85 year old dad is that way.
He just can’t resist answering the random calls on his cell.
(He also grumbles about not being able to figure out how to answer his cell… go figure.)
re: Credit union (CU) vs Bank discussion going on above:
The folks bank with a CU. Not a small one, SCEFCU, but still more hometown than a bank.
Whenever ma or pa jack up their banking, we have a gal we call at the CU who straightens it out for us.
Try that at Wells Fargo.
Despite my years of admonishing them about paying bills by check via the USPS, they continued to do so.
It took some bonehead mailbox thief grabbing a $3400.00 check out of the box, putting their name on it, and using their iPhone to deposit it to finally open their eyes.
Called our gal at the CU and the money was back in the parents’ account the next day.
typo in 1st sentence – ‘use use’
I just got my phone setup with the Privacy app to generate disposable credit card numbers. Had to use their desktop portal in order to use my routing number for the payment setup, as both my credit union & visa debit card are not on their list
This article just reinforces the concept that I need to use cash whenever possible, to never use a standard credit/debit card online or in stores
I’ve been asking cashiers about their database security. Most have no idea that was a thing. Some know it’s important, but have no answer because upper management doesn’t ‘get it’
And a few are much too quick to say their security is flawless because it’s handled by highly paid professionals…Uhaul was one like that. Didn’t know who was handling IT security, no idea how good it was, but still insisted that they were too small a target & too professional to bother getting worried about it
Osiris’ comment above highlights something important “This also permits one to listen to the message several times, and avoid the urgency-to-react factor. That’s a favorite social engineering tactic.”
Scammers use techniques such as urgency-to-react to trigger physiologic responses that tend to impair cognitive processing. These physiologic processes are involved in high stress situations. If we know how do deal with them then we are less likely to fall for the scam. The key is that we need to reset our physiology as otherwise our cognitive skills will not be available. The team I work with teaches this to first responders so they don’t make mistakes under pressure. I describe how it can be applied to avoiding a scam in a blog post
https://fullcapacityliving.com/2020/03/30/scammers-and-unease/
Good report, good analysis. My favorite spam call was while on my mobile, I got a call from my mobile. No spam, ever.
I was a victim; didn’t get the phone call, though. On March 20, I got a push alert regarding activity on my card. I clicked “no” and got a push to call the bank (Citi). I called (the number on the card) and the nightmare started: I had evidently just called in (from my old landline that I still maintain) and approved the charges. After I was able to provide credentials proving who I was, Citi told me the call came from my home phone.
They took all my info, immediately cancelled both our cards, and froze the illegal charges (over $15K). I called our landline provider and had the number changed, froze the cards we don’t use often, and checked every account that had the old number on it.
I am still working on getting over $500 credited back ($125 of which is for a Holiday Inn in Washington state – I’ve *never* been west of the Rockies!).
I also am one of those that never answer the phone (leave a message or get blocked!). I also run a lot of security/privacy apps on my systems. This experience has left me shaken; I’m waiting for the next shoe to drop.
hehe…
I’m sitting at work out here on the left coast when I get a text from my bank that I am getting some plastic surgery in Detroit MI.
I haven’t been in Detroit since 2002.
I can confirm that this is happening. They will be on the other end with the customer and also talking to customer service. They have enough information to pass authentication except recent transaction history, but are also failing voice biometrics. It also creates a problem when you try to contact the customer as they are still on the phone with the impersonator. Now sometimes they will not be on the phone with the customer at the same time as this raises all sorts of red flags. They like to go the route of sending an SMS code. Basically it is either your 2FA code to get into your OLB/if they need to talk to customer service, or it is the provisioning code for mobile wallets like Apple Pay.
When I read these scams (and I believe a similar one Brian reported on in last few weeks)…
I can’t help but wonder just where these scammers are getting the baseline data to start with.
And then I remember the Equifax hack that compromised all the bits and the bytes necessary to begin building the background to convince a bank they are you. Like your address, phone number, what credit cards you carry, social.
Basically everything you need to start building the appearance of being someone else, even if it won’t directly allow creation of such a scammer identity. If I recall, it was half of all credit reports in the US. Man, we’re basically all compromised.
What’s also interesting here is the reversal of technique. Rather than using such data to get into your bank/cc accounts directly…they use them to convince YOU they are the bank/cc., to then overcome more stringent banking controls (Citi excepted).
I know that isn’t necessarily new, but it seems like a patient, somewhat complex approach. Which I’m surprised these scammers would even pursue. And that is what is scary new.
I wonder if there is any specific reason for only going for $10K with all that work? Is it like IRS regs regarding reporting thresholds (I doubt it). If you go to this effort, you’d think they’d go higher. Maybe that’s all the guy had in his account.
I agree with Krebs. Hang Up. But also as others have noted, put a freeze on your credit checks. It will at least stem the bleeding. Great short read, as always.
And despite my own training, these articles are a reminder. We can all be duped. Wow.
It seems that majority of such cases are in US. At least based on articles here. Here in Europe, I can’t imagine that just with call I would get some information about transactions.
So maybe EMV transactions, 3Dsecure for internet payments may limit scope of frauds.
Or do the same frauds occur in Europe too?
Find the equivalent of Brian Krebs in Europe. Who is reporting this stuff over there?
<>
My experience has been that credit unions are way behind when it comes to IT security. CUs were great 20 years ago because of their local service, and low fees. But now, there is so much riding on cybersecurity and from my experience CUs are sitting ducks. I don’t know of any that offer MFA; one in my area uses member account numbers as on-line user names. In that case a user’s ONLY security is a long random password string and some limit the character set available for that.
Credit Unions often use off the shelf financial institution server software they customize with their own branding and offer boiler plate text telling users their security is important…but do nothing more than offer knowledge base Q&As for added security.
I blame CU management for this. They are likely MBAs with little knowledge of what is taking place with regard to account security. They have “security managers” but these people are focused on account holders not defaulting on loans–that’s the kind of security they are worried about.
I find the larger banks such as JP Morgan Chase a better bet simply because they can afford a security focused IT budget but the big banks are better, not perfect.
So where is the FCC in all this? No regulation means no protection.
I found that it is actually safer to go online to see my account than call the institution. I had a weak password and never got around to changing it because I had to go through the bank to get it done ( no excuse though). Someone broke into my account by cracking the password, but I’m not sure how much good it did him; because if ANYTHING changes. like the IP address, or device, or the operating system, or browser used; the attempt will go to 2 factor authorization sent to the source of your choice.
I wondered why I was constantly having to use 2nd factor all of a sudden, but I figured it was just good policy; but sure as hell, I saw a suspicious “micro-payment” from PayPal, and knew something wasn’t right. As soon as I changed my password and blocked PayPal, all the problems stopped. Like a dummy, I didn’t even think about how anyone could start a new PayPal account using your banking information to rob your account blind. It was stupid backward thinking on my part!!
Just wondering why Krebs facebook page is gone?
How would we know if the infected people who survive aren’t aliens taking over a host, and the people who died from the virus aren’t failed alien takeovers or something more…. food.
TPTB demand human flesh in order to maintain their human appearance.
3rd crack rock from the ghetto instructed us on how aliens would hide themselves as humans.
I have a $10 flip phone that costs $30 for 90 days of use with a few hours of airtime. I’m thinking about changing my bank contact info to that one since I seldom use it and it’s not paid for on my regular cell phone bill.
I’d also recommend this to anyone who is thinking of buying or selling a home, my cell phone gets a call or text a week from someone wanting to buy my house even though I’m not selling. I suspect they get the number from public docs used in closing since they know my address.
No, I would not have been fooled. And to “hang up” I say, I would not even have answered the phone. All calls to me from an unknown number are ignored.
My bank has a secure way to communicate with me through their website. They notify me by email that I have a message, and then I must log in to read it.
A hacker just sends you that “you have waiting messages” email. You click on that link, you go to a site that looks IDENTICAL to your bank’s… and type in your name/password… giving it directly to the hacker.
Let’s face it… every “this is the solution” in this article, and this comment list… is VERY simple for a hacker to break through anyway.
Glad that my bank asks for an answer to the security questions they have on file when calling AND that I provided random answers for those questions. Random generated from a password manager.
Mother’s Maiden Name: d41d8cd98f00b204e
Good luck guessing that answer.
You’re changing it today, right?
A lot of people say to just hang up. However, I think the opposite is true. The more people keep them on the phone for as long as possible, the more their business model falls apart.
I’ve kept scammers on calls for close to 10 minutes pretending to get information, acting concerned, etc, which prevents them from talking to real victims. The phone calls are cheap for them, but the labor, equipment, etc, is a lot more expensive to scale.
From a consumer side…yes, hang up and call your bank/FI/insurance company directly if needed to confirm any other suspicious activity. However, the call centers are just as much under attack as consumers. Long hold times, WFH distractions and it’s a war they are not going to win on thier own. https://www.pindrop.com/blog/flash-report-five-insights-of-covid-19-in-the-contact-center/
Brian — feel free to reach out, I think they is an authentication piece of this story missing and happy to discuss.
“Dozens of cybercrime shops traffic in this stolen data, which is more traditionally used to defraud online merchants.”
I don’t think that’s accurate. If valid credit card data is provided to the bank by merchant, I think the bank pays. In any event, we’re the ones defrauded, because banks and merchants don’t take these payments out of the CEO’s salary; they pass the cost on to us. There’s an easy fix, and it simply requires re-purposing drones from targeting terrorists who aren’t hurting US citizens and instead targeting cybercriminals who are.