Thousands of people graduate from colleges and universities each year with cybersecurity or computer science degrees only to find employers are less than thrilled about their hands-on, foundational skills. Here’s a look at a recent survey that identified some of the bigger skills gaps, and some thoughts about how those seeking a career in these fields can better stand out from the crowd.

Virtually every week KrebsOnSecurity receives at least one email from someone seeking advice on how to break into cybersecurity as a career. In most cases, the aspirants ask which certifications they should seek, or what specialization in computer security might hold the brightest future.
Rarely am I asked which practical skills they should seek to make themselves more appealing candidates for a future job. And while I always preface any response with the caveat that I don’t hold any computer-related certifications or degrees myself, I do speak with C-level executives in cybersecurity and recruiters on a regular basis and frequently ask them for their impressions of today’s cybersecurity job candidates.
A common theme in these C-level executive responses is that a great many candidates simply lack hands-on experience with the more practical concerns of operating, maintaining and defending the information systems which drive their businesses.
Granted, most people who have just graduated with a degree lack practical experience. But happily, a somewhat unique aspect of cybersecurity is that one can gain a fair degree of mastery of hands-on skills and foundational knowledge through self-directed study and old fashioned trial-and-error.
One key piece of advice I nearly always include in my response to readers involves learning the core components of how computers and other devices communicate with one another. I say this because a mastery of networking is a fundamental skill that so many other areas of learning build upon. Trying to get a job in security without a deep understanding of how data packets work is a bit like trying to become a chemical engineer without first mastering the periodic table of elements.
But please don’t take my word for it. The SANS Institute, a Bethesda, Md. based security research and training firm, recently conducted a survey of more than 500 cybersecurity practitioners at 284 different companies in an effort to suss out which skills they find most useful in job candidates, and which are most frequently lacking.
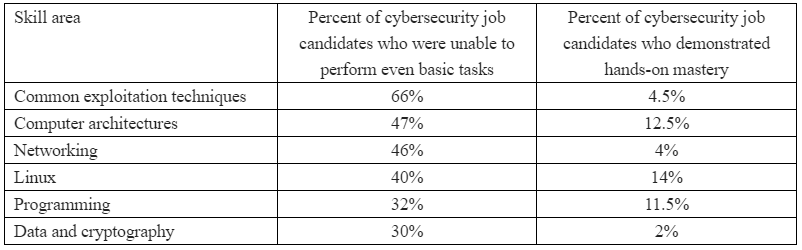
The survey asked respondents to rank various skills from “critical” to “not needed.” Fully 85 percent ranked networking as a critical or “very important” skill, followed by a mastery of the Linux operating system (77 percent), Windows (73 percent), common exploitation techniques (73 percent), computer architectures and virtualization (67 percent) and data and cryptography (58 percent). Perhaps surprisingly, only 39 percent ranked programming as a critical or very important skill (I’ll come back to this in a moment).
How did the cybersecurity practitioners surveyed grade their pool of potential job candidates on these critical and very important skills? The results may be eye-opening:
“Employers report that student cybersecurity preparation is largely inadequate and are frustrated that they have to spend months searching before they find qualified entry-level employees if any can be found,” said Alan Paller, director of research at the SANS Institute. “We hypothesized that the beginning of a pathway toward resolving those challenges and helping close the cybersecurity skills gap would be to isolate the capabilities that employers expected but did not find in cybersecurity graduates.”
The truth is, some of the smartest, most insightful and talented computer security professionals I know today don’t have any computer-related certifications under their belts. In fact, many of them never even went to college or completed a university-level degree program.
Rather, they got into security because they were passionately and intensely curious about the subject, and that curiosity led them to learn as much as they could — mainly by reading, doing, and making mistakes (lots of them).
I mention this not to dissuade readers from pursuing degrees or certifications in the field (which may be a basic requirement for many corporate HR departments) but to emphasize that these should not be viewed as some kind of golden ticket to a rewarding, stable and relatively high-paying career.
More to the point, without a mastery of one or more of the above-mentioned skills, you simply will not be a terribly appealing or outstanding job candidate when the time comes.
BUT..HOW?
So what should you focus on, and what’s the best way to get started? First, understand that while there are a near infinite number of ways to acquire knowledge and virtually no limit to the depths you can explore, getting your hands dirty is the fastest way to learning.
No, I’m not talking about breaking into someone’s network, or hacking some poor website. Please don’t do that without permission. If you must target third-party services and sites, stick to those that offer recognition and/or incentives for doing so through bug bounty programs, and then make sure you respect the boundaries of those programs.
Besides, almost anything you want to learn by doing can be replicated locally. Hoping to master common vulnerability and exploitation techniques? There are innumerable free resources available; purpose-built exploitation toolkits like Metasploit, WebGoat, and custom Linux distributions like Kali Linux that are well supported by tutorials and videos online. Then there are a number of free reconnaissance and vulnerability discovery tools like Nmap, Nessus, OpenVAS and Nikto. This is by no means a complete list.
Set up your own hacking labs. You can do this with a spare computer or server, or with older hardware that is plentiful and cheap on places like eBay or Craigslist. Free virtualization tools like VirtualBox can make it simple to get friendly with different operating systems without the need of additional hardware.
Or look into paying someone else to set up a virtual server that you can poke at. Amazon’s EC2 services are a good low-cost option here. If it’s web application testing you wish to learn, you can install any number of web services on computers within your own local network, such as older versions of WordPress, Joomla or shopping cart systems like Magento.
Want to learn networking? Start by getting a decent book on TCP/IP and really learning the network stack and how each layer interacts with the other.
And while you’re absorbing this information, learn to use some tools that can help put your newfound knowledge into practical application. For example, familiarize yourself with Wireshark and Tcpdump, handy tools relied upon by network administrators to troubleshoot network and security problems and to understand how network applications work (or don’t). Begin by inspecting your own network traffic, web browsing and everyday computer usage. Try to understand what applications on your computer are doing by looking at what data they are sending and receiving, how, and where.
ON PROGRAMMING
While being able to program in languages like Go, Java, Perl, Python, C or Ruby may or may not be at the top of the list of skills demanded by employers, having one or more languages in your skillset is not only going to make you a more attractive hire, it will also make it easier to grow your knowledge and venture into deeper levels of mastery.
It is also likely that depending on which specialization of security you end up pursuing, at some point you will find your ability to expand that knowledge is somewhat limited without understanding how to code.
For those intimidated by the idea of learning a programming language, start by getting familiar with basic command line tools on Linux. Just learning to write basic scripts that automate specific manual tasks can be a wonderful stepping stone. What’s more, a mastery of creating shell scripts will pay handsome dividends for the duration of your career in almost any technical role involving computers (regardless of whether you learn a specific coding language).
GET HELP
Make no mistake: Much like learning a musical instrument or a new language, gaining cybersecurity skills takes most people a good deal of time and effort. But don’t get discouraged if a given topic of study seems overwhelming at first; just take your time and keep going.
That’s why it helps to have support groups. Seriously. In the cybersecurity industry, the human side of networking takes the form of conferences and local meetups. I cannot stress enough how important it is for both your sanity and career to get involved with like-minded people on a semi-regular basis.
Many of these gatherings are free, including Security BSides events, DEFCON groups, and OWASP chapters. And because the tech industry continues to be disproportionately populated by men, there are also a number cybersecurity meetups and membership groups geared toward women, such as the Women’s Society of Cyberjutsu and others listed here.
Unless you live in the middle of nowhere, chances are there’s a number of security conferences and security meetups in your general area. But even if you do reside in the boonies, the good news is many of these meetups are going virtual to avoid the ongoing pestilence that is the COVID-19 epidemic.
In summary, don’t count on a degree or certification to prepare you for the kinds of skills employers are going to understandably expect you to possess. That may not be fair or as it should be, but it’s likely on you to develop and nurture the skills that will serve your future employer(s) and employability in this field.
I’m certain that readers here have their own ideas about how newbies, students and those contemplating a career shift into cybersecurity can best focus their time and efforts. Please feel free to sound off in the comments. I may even update this post to include some of the better recommendations.




The BIGGEST cyber threat really is due to employee’s getting exploited by a social engineering attack. This is mentioned in so much literature and what was cause of most recent Twitter attack- social engineering.
Management needs to really improve in this area, I am addressing this area using Industrial Psychology Theories, IT Models and more. I am working on strategies for managers to ’empower employees for cybersecurity practices using my decades of experience in IT and PhD in Industrial Psychology.
See my NEW website: cybersecorgpsych.com
FYI: Yes, I too have just completed a Master’s in CyberSecurity and studied for CISSP and CEH. Via CEH I learned languages and CISSP learned much about networks and cryptology. Of course, no job offers, even though I also worked as PM managing many cybersecurity projects. Also as a PM I have over and over again been disappointed by programmers who never really knew how to program, they get their jobs from their friends.
Are you saying that you can’t get a job, even with your skillset? I was under the impression that the industry was expanding and potential positions and opportunities were growing?
…while true, training against phishing is not what’s needed if the barn door is open…
…knowledge about the barn door is first, anti-phishing training is secondary…
@Dinne, so I see where you say you’ve “learned” and “studied”… how much of this knowledge is actual practical experience as a security or IT sys admin, analyst or engineer working in real situations on real problems?
If I were starting out now, I would focus on cloud technologies in order to acquire a broad base of knowledge. You can get a cloud server at Amazon EC2 for no charge, and then work you butt off learning how all the Amazon, Google and Microsoft cloud products work. Forget the certifications. Passion and practical experience are far more important.
With basic cloud knowledge you should be able get a job pretty quickly at an IT firm or similar, and the great part is you can demonstrate to any prospective employer what you are capable of by simply showing them the servers, network infrastructure and cybersecurity defenses you’ve created in the cloud.
I caution against vendor specific technologies for new cyber security professions. Yes, hitting on specific buzzwords will get you past the HR reps, and get a quick interview… but as Krebs mentioned, there MUST be a core competency in agnostic computing/networking systems.
Learning the specifics of Amazon, Google and Microsoft comes AFTER the core competencies. That is why “cloud” is still regarded as a buzzword, because it’s just “someone else’s computer”. Cloud security is still the same, but with added layers of complexity and proprietary systems. Learn the basics first, and then learning how AWS, Google and Azure do their implementations will come easier.
I am making a good salary online from home.I’ve made 97,999 dollar.s so for last 5 months working online and I’m a full time student. I’m using an online business opportunity I’m just so happy that I found out about it……… Read More
Hello Brian,
Thank you for the article –
I am currently working in the cyber field and can confirm you have covered several relevant areas and technologies that cybersecurity professionals should focus on developing knowledge and skillsets.
I’d like to provide an additional area of focus that has been relevant in my professional experience and is growing in significance within the cybersecurity realm –
API Services play an essential role in the infrastructure and operations of most modern organizations. APIs provide solutions for integrating disconnected applications/systems and can extend functional capabilities through requestable services. Rapid growth in API adoption across organizations has led to increasing availability and accessibility of attack vectors as implementations commonly involve the transmission of sensitive information and capacity to control executable operations, and endpoints with varying levels of exposure where inbound and/or outbound requests are processed. Understanding networking, and data security fundamentals in addition to gaining proficiency API development and testing, can be powerful tools for modern cyber professionals to leverage in their toolbox in meeting the high demand of required skills to help organizations prioritize api security.
Field this question from interns all of the time. I always recommend starting at the help desk. Work on your troubleshooting skills and get to know the systems you are trying to either protect or attack.
Good write-up, nice to have some suggestions from the majority of the focus areas.
Couldn’t agree more about strong networking skills. If they have those, you can teach security on the job.
The BIGGEST cyber threat really is due to employee’s getting exploited by a social engineering attack. This is mentioned in so much literature and what was cause of most recent Twitter attack- social engineering.
My whole career has been spent at mid size companies and I’ve interviewed a lot of security candidates. The hardest skills to find have been:
1- How to secure public cloud environments (IAM, networking, disaster recovery, secret management, etc).
2- How to understand and write Infrastructure as Code (eg Terraform) configuration to enforce appropriate security controls.
3- How to build and configure automation to detect and alert on/remediate policy violations.
My companies have always needed security candidates to not only be able to create security policies (while balancing business and productivity needs), but also play a leading, hands on role implementing those policies. Those core public cloud DevSecOps skills have always taken priority over ability to pentest the applications themselves since that’s easier to outsource.
Your requirements is actually akin to finding a unicorn.
You may want to get a security guy who can review or add onto a devops/sysadmin who is writing those lines of codes/lambdas/terraform.
What we need, and I know this is unpopular, is more emphasis on writing secure code in the first place. Mastery of a language should be preferable to knowing a little about a dozen languages.
Sure, we need the IT security folks, but writing secure code goes hand in hand with IT security and infrastructure security. We have too many people who don’t know how to handle the simplest forms of exploits in a language (buffer overflows, for an example)… and without that knowledge knowing about IT and network security is missing its key component.
I’ve been writing software for over 25 years, and I can say for every new fad, none of them address the real problem. Most of them change the hubcaps on the car when you REALLY need to fix the brakes.
It’s not diminishing those who do devops and the like, but doing that sort of thing is like learning calculus before you know algebra. And colleges aren’t helping in that arena either unfortunately. :-/
Most companies don’t write their own code. Good security may start with development, but a new cybersecurity professional doesn’t need to start as a developer. It helps to be able to read code, and maybe write in some interpreted languages… but fundamentals of security comes from understanding the network stack more so than C++
Thanks for that article! The same you say is true for “how to become a network engineer”.
One thing you might add to the list: A good grasp of the English language (if you are not a native speaker). No need to be perfect, but a candidate should be able to read documentation and talk and understand English.
I think many also discount the communication skills required for such a position. Security managers are expected to have technical skills but much of their position will be telling upper management what needs to happen to meet their goals and conveying how to meet those goals with the different teams involved across the spectrum of technology.
Quality writing is also very important and should not be discounted or ignored when communicating to management or even senior team members.
I think you can find better sources for Shell Scripting then ones not using HTTPS (http://linuxcommand.org), especially given the topic at hand…
Interesting. Very good write-up. And, remember, you don’t have to be outstanding. Be profecient. Remember you will be starting as a team player, not the department head. The dept head, may know nothing except they are in charge. They have a degree in being in charge, and they can make or break your future.
If you have to have a degree, make it useful, design, development, planning, research. New systems are coming. Will we create new problems, or new solutions. And it all starts with one question asked. But, how do you get them to stop and listen? With no ” degree”?
CTF, Capture the flags have helped me a ton.
hackthebox and watching ippsec on youtube.
Tryhackme is another beginner friendly resource for learning the basics of security.
John Hammond is another resource on youtube to watch.
Very good article Brian. I will point out that there are various levels and requirements for cybersecurity professionals. Engineers and those on the front line of work are definitely what you refer to in your article. In my experience, network knowledge is essential otherwise you will fail. If you don’t know how a packet traverses from the internet to the DMZ / firewall / IPS/IDS / WLAN / LAN / PC – then you will not be a strong candidate. Plus that networking path assumes you are very familiar with a firewall and IPS/IDS.
That being said, there are skills required for cybersecurity that involve audit, reporting, educating, building policies and procedures that are not always the strength of the in-depth technical person. The cybersecurity requirements in an organization are widening beyond the “front-line” engineer.
But, as Brian indicates, if you want to excel in the area, you need self-motivation and the perseverance to read, learn, try (fail) and try again. There is enough technical education on the web to succeed.
This is coming from 10-years of experience in IT: learn to troubleshoot problems. Many people lack the ability to solve problems when there isn’t a clear set of instruction to follow: an essential skill for someone in Security who’s job it often is to identity problems that *might* be there (but also might not!)
Talk to a seasoned car mechanic and ask him to teach you about troubleshooting methodology. The skills are more transferable than you might think.
I absolutely agree. Another suggestion seen here, was to start off at help desk. Build troubleshooting skills.
You’d be surprise how often it is overlooked by really smart people who are so far deep in the weeds they don’t have a good methodology of logical inference that is needed to eliminate the possibilities down to testable hypothesis.
+1 on the CTF suggestion. It’s high-intensity learning where you are forced to familiarize yourself with details of all kinds of technologies on the clock and come up with working solutions. I find it incredibly valuable for quick learning and, frankly, learning how to stay cool under pressure, which is badly needed for today’s security jobs. ctftime.org is a great directory of online CTFs worldwide.
Also, check out wechall.net – a directory of dozens of challenge sites where you can learn hands-on hacking techniques (without the time pressure of a CTF).
Finally, keep in mind that not all certifications are created equal. While CISSP and CEH are mostly “book” exams, some other certifications are intensely practical (e.g. Offensive Security suite – OSCP and others)
On your point about certifications… it is absolutely true that there are huge differences.
I find that CISSP is great for managers who aren’t expected to get a lot of time on keyboard.
SANS is great because although exams are open book, many of their questions are really based on practical experience that mostly come from doing the lab. The exams have started to include micro VMs for some lab questions that aren’t multiple choice.
Offensive Security’s OSCP is great, and highly coveted, but being a offensive in nature, it doesn’t really teach anyone how to be a good defender. SANS has many tracks that delineate between defensive, offensive, forensic, audit, etc. I wish Offsec would do that too, but not certain if that is too far from their wheel house.
If you live in Wisconsin and near Eau Claire – Check out ECInfoSec.com. We are look infosec meetup!
Virtual or in-person?
Brian, can you post a link to the SANS survey you referenced in this article?
Krebs-on, thanks for starting a conversation on a topic that deserves its own sub-Krebs.
Rarely does anyone raise the issues around soft skills. It’s great to know all the things, but its critical to know one’s self. I have seen people job hop or worse yet crash and/or burn out because they don’t enjoy the work critical to their success. There are paths that are more science and some that are more art; some jobs involve tons of human involvement and others that consist of many hours of personal time with the bits and the bytes.
It’s not just knowing what makes things tick, we each need to know what makes us tick.
Great article! I have emphasized these points to other in IT thinking CyberSec is all glorious because of its pay. This disciple is a culmination of all IT areas. Good luck finding a place that has entry level openings. The entry level spots have been outsourced to India and their 20 yro learn the basics and get a foot in the door to move up. Organizations also have been failing by just trying to promote current “senior” IT people to CyberSec. One might be an amazing DBA knowing how to secure a database but without a clue how the data gets there or how the OS your database sits on works you are limited. The network skill is a must and a great starting area.
I see it as the same as going for your medical degree. 4 years of foundation, 4 years of hands-on focus practice medicine and if you want to really specialize another 2-4 in a certain topic all while never stop learning. Getting a CyberSec degree in 4 years or less wont prepare much. Can I get a 4 year math degree never knowing math? Doubt it. All takes a lot of time.
…insatiable curiosity about how things work (or don’t work when troubleshooting) and the ability to explain plainly to non-techies…
…so networking, apps, curiosity, plain explanations – everything else rests on that (to borrow a phrase)…
“A common theme in these C-level executive responses is that a great many candidates simply lack hands-on experience with the more practical concerns of operating, maintaining and defending the information systems which drive their businesses.”
I find that comment both funny and disturbing considering most C-Level decisions are based mostly on “risk management” versus “vulnerability mitigation/remediation.”
To me, this comment really says it all. “Employers report that student cybersecurity preparation is largely inadequate and are frustrated that they have to spend months searching before they find qualified entry-level employees if any can be found,”.
“Employers” really need to understand that security/cybersecurity skills are learned over time and mostly by people working in various IT skills Help Desk, SYS Admin, DBD, developer and others. Security is also a mindset that cannot be taught in schools or certification training. But in my opinion the biggest failure among the C-suite is that they don’t want to hire the experience person, they want the entry level guy because they’re cheaper. If you want entry level, hire from within, give incentives to people in other fields who want to be learn security and who bring skills to the table that you can work with. In other words, teach a Help Desk Tech, a DBA or a SYS Admin to be a security professional, but don’t expect someone who doesn’t already have those skills to learn them in a few months and be ready to put them to use in the real world because they’ve passed a test.
I don’t know any “C-Suite” executives who do the hiring. They smartly delegate that to HR and department managers for that. The CISO or equivalent may attend one of the interviews, but a smart executive will defer to the technical people for the technical interview. Some places even have a candidate attend 4 phased interviews.
1) HR (phone)
2) Manager/supervisor
3) Peers/subordinates
4) Executive level
2 and 3 will be technical interviews, 1 and 4 will be administrative and cultural fit.
Seems like a lot, but once you have a hiring practiced formalized, it can go pretty smoothly.
Greetings!
Great article! To me two things matter most for IT and even more for security: A love and curiosity of how things work at a deeper level and the self-motivation to break systems down and rebuild them again. Preferably in an improved state and with a “let’s try something different” attitude to reach the desired outcome. Failures must be expected at all times but the perseverance and discipline to learn from and overcome these should be expected as well.
Moreover regarding security, someone has to accept the fact that there are highly aggressive and technically superior actors involved so they must delve deeper and deeper into the systems while staying on their specialization’s technological edge, at all costs.
If someone is lured in security because of names and movies and the “coolness” of how it sounds and just go for certification papers but the above mentioned attitude is missing, there is a high chance they will fail in security. Catastrophically at some point.
A few hundred people in the field got real world experience while working in the UAB Computer Forensics Research Lab at UAB. DarkTower is also hiring student analysts – between just those two we have about 92 student analysts and programmers working to provide services to our government and corporate partners.
Interesting. Certificates are largely required by the government, thus contractors that do work for the government also desire them.
The FAANG type companies will grill you on what you know so things like certificates and even a college degree are not required (at least one directly mentioned that although I do have one).
Too many ways to cheat to get certificates and some people can memorize a ton of stuff to pass a test but have near zero ability to think, debug and problem solve so they don’t last long.
I’ve found the SANS courses to be the most interesting. CEH was a waste of time/money. CISSP is a tougher test but is very high level and not something I think is important especially for hands on people.
As someone in my 50s I found it amazing that we hired a EE graduate and he wasn’t require to take a single network course. He had no clue what the difference was between a MAC address and an IP address. Seems like every engineering student should have to take a basic network class.
The hacking courses/work is the most fun since you have a tangible goal. The defense stuff is much tougher since you only know when it fails.
And yeah, we graduate a ton of engineering, CS, etc. people who have no problem solving skills and can’t do the basic stuff.
So much of what you describe here is exactly why I created a training class to focus on hands-on skills. Certs are a box to check, but all the hiring managers we talk to want proof of hands on skills. So we created over 100 practical-based lab assignments to take beginners into their first jobs in Cybersecurity. We start with taking apart a computer, and rebuilding it as a home lab for experimenting with VMs, networking, and the tools in Kali and more.
I’d love to hear your thoughts on how the curriculum we designed aligns with what you see as the need in the industry: https://testing-www.codefellows.org/learn-cybersecurity/
We designed it to be taught with live-remote instruction, so people could attend from anywhere… which means we ship out students a complete lab kit with all the things a sysadmin and cyber pro needs to get started with getting hands dirty and building their own home cyber range. It was a lot of fun to put it all together and we are eager for feedback!
Two thirds of IT employees are in blind journey. Upon my knowledge it’s on finger tip (single digit) percent who show more interest on security systems
A typical survey response; technical skills over administrative/soft skills. IT hasn’t learned after almost 30 years that technical skills are only part of the equation.I’m generalizing but the majority of techies want to work with the technology and don’t want to sit in countless business meetings.
There is far more to Cybersecurity than just the technical component. Yet, employers continue to put techie’s in front of the business and wonder why the business and the techie are dissatisfied.
Thus, employers try to the find the holy grail; a person that has both the technical and the administrative/soft skills. The smartest organizations realize that they need to split the roles; the others end up with an employee that is set up for failure because a 50/50 split is unachievable.
Some great points, definitely tons of information for Linux distro’s around security.
As a holder of a Masters in Cyber Security and unable to crack this career after 20+ years as a programmer/ BA and data analyst, I have given up trying.
In medicine, not everyone has to be the neurosurgeon in the operating room. Nurses dont have to know how to use a scalpel, wardsmen dont need to know brain anatomy, anesthetists dont get blood on their hands…but together they make a team and their different skills make it work.
My software career has seen great changes to include different skills…but not in cybersecurity, everyone points to needing to know basic networking and hacking skills, and ironically continues to put the socially inept security engineer in customer facing roles. It just seems so short sighted, that the industry shuffles great technicians into the wrong roles and ignores those that can give great support.
I know the theory, I have a wealth of skills to offer, soft skills are exceptional…but the door in seems to be via the red team only. ..I dont wish to hack a box, but I’m keen to get into cybersecurity.
I think the worst part about having such a career would be having to say “cyber” all the time.
I started out as a programmer/analyst in 1986. Moved to Unix sys admin, then added Windows Server admin, and Linux. Became a part time network admin to cover for co-workers on vacation. Was an application admin also at the places I’ve worked. There’s no getting around knowing how the plumbing works at the deepest levels, and getting your hands dirty. When you know the weaknesses, you’re ready.