Thousands of people graduate from colleges and universities each year with cybersecurity or computer science degrees only to find employers are less than thrilled about their hands-on, foundational skills. Here’s a look at a recent survey that identified some of the bigger skills gaps, and some thoughts about how those seeking a career in these fields can better stand out from the crowd.

Virtually every week KrebsOnSecurity receives at least one email from someone seeking advice on how to break into cybersecurity as a career. In most cases, the aspirants ask which certifications they should seek, or what specialization in computer security might hold the brightest future.
Rarely am I asked which practical skills they should seek to make themselves more appealing candidates for a future job. And while I always preface any response with the caveat that I don’t hold any computer-related certifications or degrees myself, I do speak with C-level executives in cybersecurity and recruiters on a regular basis and frequently ask them for their impressions of today’s cybersecurity job candidates.
A common theme in these C-level executive responses is that a great many candidates simply lack hands-on experience with the more practical concerns of operating, maintaining and defending the information systems which drive their businesses.
Granted, most people who have just graduated with a degree lack practical experience. But happily, a somewhat unique aspect of cybersecurity is that one can gain a fair degree of mastery of hands-on skills and foundational knowledge through self-directed study and old fashioned trial-and-error.
One key piece of advice I nearly always include in my response to readers involves learning the core components of how computers and other devices communicate with one another. I say this because a mastery of networking is a fundamental skill that so many other areas of learning build upon. Trying to get a job in security without a deep understanding of how data packets work is a bit like trying to become a chemical engineer without first mastering the periodic table of elements.
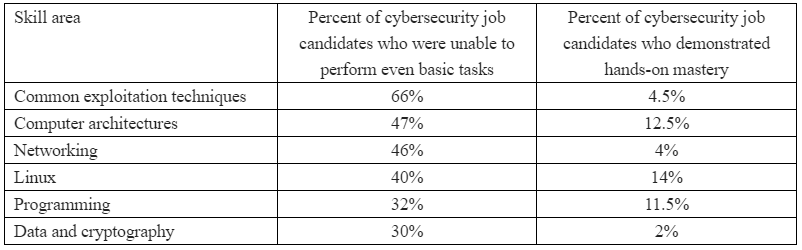
But please don’t take my word for it. The SANS Institute, a Bethesda, Md. based security research and training firm, recently conducted a survey of more than 500 cybersecurity practitioners at 284 different companies in an effort to suss out which skills they find most useful in job candidates, and which are most frequently lacking.
The survey asked respondents to rank various skills from “critical” to “not needed.” Fully 85 percent ranked networking as a critical or “very important” skill, followed by a mastery of the Linux operating system (77 percent), Windows (73 percent), common exploitation techniques (73 percent), computer architectures and virtualization (67 percent) and data and cryptography (58 percent). Perhaps surprisingly, only 39 percent ranked programming as a critical or very important skill (I’ll come back to this in a moment).
How did the cybersecurity practitioners surveyed grade their pool of potential job candidates on these critical and very important skills? The results may be eye-opening:
“Employers report that student cybersecurity preparation is largely inadequate and are frustrated that they have to spend months searching before they find qualified entry-level employees if any can be found,” said Alan Paller, director of research at the SANS Institute. “We hypothesized that the beginning of a pathway toward resolving those challenges and helping close the cybersecurity skills gap would be to isolate the capabilities that employers expected but did not find in cybersecurity graduates.”
The truth is, some of the smartest, most insightful and talented computer security professionals I know today don’t have any computer-related certifications under their belts. In fact, many of them never even went to college or completed a university-level degree program.
Rather, they got into security because they were passionately and intensely curious about the subject, and that curiosity led them to learn as much as they could — mainly by reading, doing, and making mistakes (lots of them).
I mention this not to dissuade readers from pursuing degrees or certifications in the field (which may be a basic requirement for many corporate HR departments) but to emphasize that these should not be viewed as some kind of golden ticket to a rewarding, stable and relatively high-paying career.
More to the point, without a mastery of one or more of the above-mentioned skills, you simply will not be a terribly appealing or outstanding job candidate when the time comes.
BUT..HOW?
So what should you focus on, and what’s the best way to get started? First, understand that while there are a near infinite number of ways to acquire knowledge and virtually no limit to the depths you can explore, getting your hands dirty is the fastest way to learning.
No, I’m not talking about breaking into someone’s network, or hacking some poor website. Please don’t do that without permission. If you must target third-party services and sites, stick to those that offer recognition and/or incentives for doing so through bug bounty programs, and then make sure you respect the boundaries of those programs.
Besides, almost anything you want to learn by doing can be replicated locally. Hoping to master common vulnerability and exploitation techniques? There are innumerable free resources available; purpose-built exploitation toolkits like Metasploit, WebGoat, and custom Linux distributions like Kali Linux that are well supported by tutorials and videos online. Then there are a number of free reconnaissance and vulnerability discovery tools like Nmap, Nessus, OpenVAS and Nikto. This is by no means a complete list.
Set up your own hacking labs. You can do this with a spare computer or server, or with older hardware that is plentiful and cheap on places like eBay or Craigslist. Free virtualization tools like VirtualBox can make it simple to get friendly with different operating systems without the need of additional hardware.
Or look into paying someone else to set up a virtual server that you can poke at. Amazon’s EC2 services are a good low-cost option here. If it’s web application testing you wish to learn, you can install any number of web services on computers within your own local network, such as older versions of WordPress, Joomla or shopping cart systems like Magento.
Want to learn networking? Start by getting a decent book on TCP/IP and really learning the network stack and how each layer interacts with the other.
And while you’re absorbing this information, learn to use some tools that can help put your newfound knowledge into practical application. For example, familiarize yourself with Wireshark and Tcpdump, handy tools relied upon by network administrators to troubleshoot network and security problems and to understand how network applications work (or don’t). Begin by inspecting your own network traffic, web browsing and everyday computer usage. Try to understand what applications on your computer are doing by looking at what data they are sending and receiving, how, and where.
ON PROGRAMMING
While being able to program in languages like Go, Java, Perl, Python, C or Ruby may or may not be at the top of the list of skills demanded by employers, having one or more languages in your skillset is not only going to make you a more attractive hire, it will also make it easier to grow your knowledge and venture into deeper levels of mastery.
It is also likely that depending on which specialization of security you end up pursuing, at some point you will find your ability to expand that knowledge is somewhat limited without understanding how to code.
For those intimidated by the idea of learning a programming language, start by getting familiar with basic command line tools on Linux. Just learning to write basic scripts that automate specific manual tasks can be a wonderful stepping stone. What’s more, a mastery of creating shell scripts will pay handsome dividends for the duration of your career in almost any technical role involving computers (regardless of whether you learn a specific coding language).
GET HELP
Make no mistake: Much like learning a musical instrument or a new language, gaining cybersecurity skills takes most people a good deal of time and effort. But don’t get discouraged if a given topic of study seems overwhelming at first; just take your time and keep going.
That’s why it helps to have support groups. Seriously. In the cybersecurity industry, the human side of networking takes the form of conferences and local meetups. I cannot stress enough how important it is for both your sanity and career to get involved with like-minded people on a semi-regular basis.
Many of these gatherings are free, including Security BSides events, DEFCON groups, and OWASP chapters. And because the tech industry continues to be disproportionately populated by men, there are also a number cybersecurity meetups and membership groups geared toward women, such as the Women’s Society of Cyberjutsu and others listed here.
Unless you live in the middle of nowhere, chances are there’s a number of security conferences and security meetups in your general area. But even if you do reside in the boonies, the good news is many of these meetups are going virtual to avoid the ongoing pestilence that is the COVID-19 epidemic.
In summary, don’t count on a degree or certification to prepare you for the kinds of skills employers are going to understandably expect you to possess. That may not be fair or as it should be, but it’s likely on you to develop and nurture the skills that will serve your future employer(s) and employability in this field.
I’m certain that readers here have their own ideas about how newbies, students and those contemplating a career shift into cybersecurity can best focus their time and efforts. Please feel free to sound off in the comments. I may even update this post to include some of the better recommendations.




Terrific article. I’m currently struggling to get responses to an academic study related to this very topic (Efficacy of Incident Response Certification in the Workforce). Any input cybersecurity professionals can lend would be extremely helpful; it’s very difficult to busy professionals like yourselves in one place. I will post my resutls soonest:
https://www.surveymonkey.com/r/efficacy_f4
This isn’t so different from my main field, except that I have become prejudiced against hiring anyone WITH certifications. So often they can’t code themselves out of a paper bag when given simple tasks because they have no practical experience behind their certifications.
I’ve hired entry level people, senior people, and jack-of-all-trades people. Never have I seen greater incompetence or greater inflexibility from anyone than a certified person. I’ve gotten to the point that if someone has a certification I consider it a warning sign that this person may lack the fundamental skills to do the job.
That’s my feeling too, things like pen-testing and secure development are an art form, you can train a random person to make them slightly better than they’d otherwise be but a good artist or security person needs actual talent. Almost all of the really good security people I know are self-educated, and the few who have something like a university education are good at what they do despite their university education, not because of it.
In approaching potential talent this way, you are robbing yourself. Not everyone is going to approach their career that way, and given how few security people there are for security roles, some people will need to be given the chance to grow into the role.
Same problem with university degrees… except worse, since they may have gone over a decade as a Walmart greeter, without any refresher.
If you are basing solely on certs, degrees, without looking at experience or running them through your own test… then you are looking for failure.
Certifications aren’t a panacea for a hiring manager, no more than Anti-virus is for endpoint security. It is a very valuable “layer” in an overall defense in depth strategy.
They valuable because they at least tell you their interests, where they put some time and effort. They may have the very basic understanding of the material.
And if you’re looking for skills in the “fine arts” of cyber… like coding, pen testing, etc… then certifications can only be a foundation, you should never have expected a full understanding of their skill level.
For those skills, you absolutely should conduct your own tests, and definitely look at their prior work (github).
That’s how you hire artists, right… you look at a portfolio.
I think that employers today have gotten it wrong. They do not want to train their employees. Perhaps that is why lots of employees are unsatisfied with their position and leave as soon as they can–going to another, similar employer. Even a well-educated, experienced employee may need some specific help/training for the particular job in question.
Perhaps this is because the people making hiring decisions are also not completely trained.
Regards,
As a cyber security student entering the final year of my very hands-on bachelor degree program this article made me feel much more optimistic about the job seeking process. I spend most of my free time learning how things work and setting up virtualized networks on an VMWare Esxi machine that I built for exactly that purpose. I also use Linux as my daily driver and am always downloading and installing new distros in VMs to see how they work and what sets them apart from the others. I am hoping my passion for this line of work comes through in interviews, although I expect to start at a network admin position before internally moving to cyber sec somewhere. If I do get that dream cyber sec position with a lateral career path right out of school, awesome.
Good path.
This article is just what I needed to read! I recently received my BS degree in Information Technology with a connection in Data Networking and CyberSecurity, however, I will say that this degree solely trained me for the role of a CIO and the adjacent roles that come with it. Which is great! But I’m brand new with IT, so I’m starting to see now that I should’ve started low level dust with getting my hands dirty, because I’m still entry level when it comes to skills listed in this article.
I do feel, however, that I have to question about what happened to companies training people? Don’t get me wrong, I understand that the basic concept of any role should always be understood by the applicant. This I agree with. But when it comes to using the tools, this is also something they want to know on expert level with 5 years experience? How will I get that experience if no one hires the entry level tech head lol personal, hands on experience by downloading software mentioned in this article, yes that’s cool and easy. But how to gain experience with no scenarios to practice with? I’m speaking solely on the fact that I’m new so if there’s a tool already that fits this description, someone let me know! Let’s network lol
I will look at what was mentioned in this article indeed! I appreciate your words, time and dedication for explaining “How” for newbies like me!
I think one of the reasons employers don’t want to offer training is because many employees, once they get the certifications they want, leave. As as example, years ago my company offered training to become an MCSE. Over 100 people took this training, which last over 6 months and required numerous certifications. Once complete, over 80 left the company or their current role in the company. Because of this, managers in the company are now against providing their employees training.
Many companies develop a voucher system, where they offer to pay for cert programs, like MCSE. And you can incur a minimum employment period by taking that deal. The contract can require payback if you leave before then.
Age old problem of book larning versus practical application. I worked, back in the 60s, for a metals producer, which was, because it was forced to be by lawsuits, state of the art for the time. The company invented new processes, requiring new measurement tools, so had glass blowers on staff through the 80s to build acid air proof cases which were unavailable on the market. They did well, and monetized all the new output, from precious metals, to acid, to fertilizers to liquified gases the new processes produced.
They also, naturally, hired a lot of engineers.
Almost a constant was the young engineer instituting a process change and being told by the grizzled old operator, who may have been a whiz in school but settled for becoming a pilot, or a gunner, or a foot soldier when he was young, “that won’t work.”
Conversations like this were frustratingly (for the operations staff) common.
Engineer, “We’re doing this.”
Operator, “That won’t work.”
Engineer – waves calculations.
Then, after the ensuing mess, production loss, and cleanup – not by the engineer, of course.
Engineer, “This will fix it,”
Operator, “No, that won’t work, either.”
Engineer – waves calculations, with diagrams/blueprints.
Ensuing mess.
Cleanup, rinse (often literally, but not by the engineer, or course) repeat. Until, finally.
Engineer, “why isn’t this working?
Operator, “Because, (some part of the process, built in 0r jury rigged for efficiency, is not included in your calculations, and variations in ingredient mix occur, like this, for example)”
Engineer, “Oh.”
later (a little or a lot, depending)
Company, “Oh, good, we finally got, and can predictably maintain, the result we wanted from the adjustment.”
Engineer (sometimes, at least) to operator, “Thanks.”
Operator, “You’re welcome, nice to meet you.”
Same old interactions now, I expect.
Meh, the analogy isn’t really applicable since there is a huge difference between the virtual world and the physical world.
Most medium sized companies have a development/test environment in which engineers can build their dream world at little to no cost or risk.
And if it works in that environment, there is a simple and safe process to make the change production too.
This is how Silicon Valley software companies have been able to out-innovate the manufacturing sector by an order of magnitude for the past 40 years.
If just starting out your career in cyber, get an entry level spot in a Security Operation Center (SOC), and work your way up. Learn the engineering side (tools), and the analysis side (logs/events). Effective communication skills are critical so find something like Toastmasters or something similar.
Nice article Brian. I am a senior-level position in my career and I agree with everything you said, especially about the programming and scripting skills. It’s not surprising but still disappointing that the C-levels think that programming skills are so unimportant. If you are going to be anything more than a somebody-else’s-script-runner in cyber security, you will need to have an understanding of at least C, but the more the better. And writing scripts is _invaluable_. I have met people whose entire job tasks could be automated with a couple days worth of scripting in Python. The ability to create that much value is mandatory for anybody I consider hiring.
I applied for a job as an ordinary IT position at a university once; and when I got there I immediately noticed it was a supercharged atmosphere, partially because of security concerns, but partially because the boss meant business and you didn’t mess with her. She ran a tight ship. So I wasn’t particularly disappointed when I learned I just missed the job because of ONE weakness – I had never compiled any software before – I was aware of the process but just didn’t have experience in that one item. So I lost, but I think I would have gone crazy in the 1st 3 months on that job, because of the tense atmosphere there. Funny thing was, I was trained at the same institution, so some of the network bosses knew I was a good candidate.
I entered the CyberSecurity field in 2012 after a work injury left me unable to physically work in my profession.
I obtained a BBS and MS in Computer Information Systems and thought I would have no problem getting a job given my technical and academic skills. Much to my dismay, I found that trying to enter this field when I was in my early 60s was an insurmountable task despite the fact I was a disabled veteran.. Internships went to younger students which made finding a fulltime job difficult. Many contractors and most government jobs wanted an existing security clearance and hired people with clearances (as I was told by people doing hiring).
After over 600 job applications I had enough. I got tired of losing out to other less-qualified applicants. Several of my graduate classmates over 40 had the same problems as I did. Those who were Black or Hispanic found very few jobs also.
In many cases no amount of technical skills will make up for being a minority or older.
Sam if it helps, I had the same experience as a white man from 20-30 years old. Employers would hire absolute trash that would screw them over as I watched from the outside.
Thanks D. At one point, career development at my school had me remove skills from my resume so I wouldn’t look overqualified.
I did the trick to only list the skills and number of years in resume that are required in the job post. Raving any dates to avoid over qualified. I got calls then from recruiters.
Too many skills listed on a resume does two things in the mind of a recruiter or hiring manager.
1) Over-qualified – will ask for too much money upfront or leave too soon after getting a better offer.
2) Paper tiger – Many manager simply do not believe you truly have such a wide assortment of skills unless they are backed up with experience from differing positions. Just out of college, at any age, doesn’t really net you 20 cyber skills, so many manager assume you are just pencil whipping.
Absolutely agree with your observations. Older workers, often with much more experience, get the shaft for younger, cheaper, and ‘more moldable’ candidates. I can get job as a contractor, and the employers are happy to have me as a resource, but know one wants to make me part of the team; and seems like it started for me after 45.
Many reputable companies mask certain PII that would disclose you as a protected class. Your resume should not show your age, but the application might. Hopefully, they have a good HR team that masks that application data, from the hiring managers or recruiters.
But yeah, discrimination is still a huge problem.
The security clearance issue is definitely a thing. If you don’t have one, don’t bother applying, they don’t have a lot of control even if they wanted you.
Sam,
So sorry to hear that you had to go through this. Don’t give up, keep looking. If you are able to apply, take a look at the US Government Jobs website, https://www.usajobs.gov/
“In many cases no amount of technical skills will make up for [this]”: I very much concur.
There are what we may call systemic failures in place.
These are mainly invisible to many people who have commented on here. Privilege works that way. Can the “average Joe” see how rarefied these discussions are? Especially since the average is a guy named Joe?
Generally, anything that cannot be hidden from management will result in difficulty finding a position. Yes, it can be extreme difficulty. To find a position:
Do not be differently-abled. Do not be female or other-gendered. Do not manifest any ethnicity other than White. Do not speak in a manner that suggests a differing background. Never appear to be over ~50 or even ~40. Et al, et al.
Only two of the above can be hidden for the sake of an interview. I belong to three, and cannot relocate to DC. Maybe there is at present no ready solution.
Perhaps it really is that difficult to find a position.
The situation is actually simple, no need to reinvent the wheel, it is called free market and Capitalism (that won finally everywhere, for good or bad) – YOU GET PAID WHAT YOUR WORK IS WORTH.
Certs/degrees/… – just to pass the HR filter. The line manager wants to know just one thing – what work a candidate can do on his/her first day of work, not in a month/half year, first day. Period.
There is beauty and ugliness of our field – to be Mechanical engineer, you have to have a degree, legally, no workarounds, but also no competition from those who don’t have it. In IT – no formal requirements, which also means every Joe can call himself a Cyber specialist and go figure his bluff.
The rest are just creative ways to live by it. You have a degree, CEH certificate, OSCP cert? Cool, tells me little. Can you secure Admin access to the Cisco router if I give you CLI right now? Can you look at Apache/Nginx logs and tell me if there was a breach ?
The great thing here is all of the cyber/IT knowledge is open and available almost to everyone and for free (except those in unfortunate circumstances/countries where having a piece of bread is struggle, alas). How you got these skills/knowledge of how-to – no one could care less. Both, Joe that set up GNX at home and did Cisco labs CCNA level, and Julia, who did BSc in Information Technology, or Adam who has had 3 years of Support experience – will use the same conf t / line vty 0 4/ access-group … to secure access to the router. And which way all of them acquired this skill – believe me, employer cares not, as long as they can do the job. And you have more than 1 way to prove you can do the job, BTW experience is not foolproof as well – people with advanced “soft skills” can lie into IT roles, abuse and manipulate people to hide own incompetence, then got finally busted, got rid of, but hey – on CV appears he worked for a full year!
You don’t have experience/degree ? No problem, show me Github repo with Cisco/Juniper/Fortigate/Malware Analysis configs of your labs you did and tell me how it went. Or write a blog documenting your labs, or do screenshots of your home labs. But do something to prove you have practical skills of use at this workplace.
Unfortunately, this way to get skills is hard – lots of hours, failed labs/configurations, blow to self-confidence, head aches, after work hours to do all that. And people tend to look at certs/degrees as a shortcut to ease the pain. But life isn’t a picnic.
One of the tools I used was to build and configure my own linux server at home. You can learn a lot about security that way … networking, authentication, firewall maintenance, intrustion detection, penetration testing, etc. It’s amazing how many penetration attempts are made in a single day!
Up front, I’m a huge Krebs fanboy and been for years. I’m a departmental CTO and hiring manager for a very large IT company. I have 3 IT degrees including a Ph.D. in cyber and have previously held a CISSP (some how I let this expire) and other certs (that I also let expire). I agree with everything Brian says with one exception. If you are new to IT without experience, certifications will help you gain credibility with recruiters and recruiting search engines in any IT discipline. There is no replacement for hands on keyboards. Certs will only help you with getting a job interview, your knowledge and experience even if it is learning at home, will get you a job.
Because there are no entry-level jobs in cybersecurity. Except for entry level SOC positions but those get taken up very quickly by co-op students and interns. All the security analyst roles listed on job forums, company websites, and hiring agencies I’ve seen are more senior roles that require minimum 5-7 years of experience, and they expect you to know everything. You need to have experience working with tools that are only available to enterprises. Not open-source tools but enterprise tools that it’s impossible to get.
And you also need to have soft skills, which can’t be overstated. You need to have professional business acumen and excellent communication skills.
So in my opinion there’s a discrepancy between what’s being reported about the cybersecurity skills gap, and the reality, there are actually no entry-level jobs in this field.
I have been doing computing since 1975 most of it on various scientific projects. Over the past 10 years, my computer-oriented academic research position has slowly moved into spending an enormous amount of time on securing the department. First it was securing the computers doing scientific computing. Later without any clear change of responsibilities, I picked up keeping the computers used by faculty and staff secure with a very small staff. Since we are scientists damn it, people use Windows, Mac, and Linux on the desktop (though nearly all large scale scientific computing uses Linux). So in this very heterogeneous environment with a small staff, I ended up responsible for the departments security.
I have not taken any courses in security but I do understand networks, PKI, Linux, and why opening port 3389 represents a risk that must weighed against people having to work remotely in a pandemic. All of this was learned seat of the pants – my degrees are in a scientific discipline. The department has about 200 faculty, staff, and grad students. Many of them have knowledge of computing and could likely overcome any restriction I put in place by being smart. Additionally most of the faculty have tenure and can’t be forced to do anything. We have had number of serious scares but relatively little damage (certainly there was an element of luck).
So in a nutshell what I learned is: people are the weakest link and you have to get them to cooperate voluntarily with slightly inconvenient practices that will keep them safe. There are too many people to police/monitor to force people to not do all of the risky things they want to do. You have get the vast majority of them to do the right thing so the number of hard cases is manageable.
I’ll give an example of the centrality of the users to security. A lab I work closely with recently ran a test sending out their own phishing emails and found that a worrying fraction of the staff logged into a bogus lab login page that they created and almost twice as many clicked on the attachment included with the bogus phishing email they received. Almost everyone was working remotely because of COVID and would have compromised their home computer if the attack had been real. This means the lab IT staff would not have had access to the affected systems. At a very computer literate lab where people have been warned and trained about phishing, many users still fell for it.
The point is that you need the people skills to get your users to cooperate. Learning how to deal with someone who views security procedures as an impediment to doing what they want to do is the most important skill. Even a huge, profitable tech company cannot police everything its users do. While certainly technical skills are required to protect an organization, it frequently comes down to fixing the weakest link: the users. While the most dangerous users are those at the top who have access to key data and can’t be forced to behave sensibly, any user can let something loose on the company intranet causing a huge mess – even an unpaid intern.
If I were looking for someone to do security at my organization, my hardest requirement would be that they be capable of explaining to people why following proper practices and reporting anything suspicious is hugely important and in their own best interest. Sure having the technical skills is important but in the end you have convince people not to do stupid stuff. I would be looking for a resume and references that say the candidate can get people to cooperate.
At a very computer literate lab where people have been warned and trained about phishing, many users still fell for it.
It is innate thing to do when people should be thinking about what would happen if one presses the button. Just to give you an example, when my classmate pushed the professor into using Zoom for online class for the rest of the semester because of its ease of getting on and off. My first thought would have been MS Team as the university uses for everyone. Luckily we never got Zoom bombed (whew!)
Naturally I decided to check its security. Lo behold, the weakest link was the ease obtaining meeting id to get into the meeting room aka Zoom bombing which media would report stories of people getting hit. Secondly, the company made no attempt to fix it until it became a problem which is common for a startup trying to become successful.
I have tremendous respect for the work you do Brian, bringing cybersecurity news into the mainstream. This article is another fine example, by raising issues of skill shortages in the field. As a CSO, I’m familiar with the challenges of finding the right talent. But as someone who’s been in n the field for 25 years, I think it’s important to look at the variety of opportunities in cybersecurity.
If you’re a big picture thinker, consider pursuing security architecture specialization. If you’re detailed oriented, consider rusk management — which includes the sub domains of vulnerability management and pen testing. Then there’s the often neglected realm of Identity and Access Management. There’s tremendous demand for authentication specialists these days. And of course there’s security leadership and governance, which includes policy, legal acumen, and good management skills.
As you can see there’s lots of opportunities in security that are only tangentially related to the threat hunting skills you identified above. Sure we need threat hunters and SOC Analysts, and bug hunters. But there’s so much more to do in the field of cybersecurity. The key is we need motivated self starters to fill that demand.
Great article in terms of getting the right hands-0n skills that are required by the industry. I have an engineering background and changing my career into cyber security. Currently doing certifications and trying to get my fundamental concepts clear. I am in my mid 30s and I know this is gonna be challenging task to get into a new field after having worked for almost 8 years in a different industry. Wherever you go, its all about experience and how you apply your skills. Most importantly, soft skills are equally important especially when you have to make critical decisions.
I’ve been doing development within the Linux OS for 15 years and software programming for 26, but a newcomer to Cyber Security. I started doing VM’s, to netmap, wireshark, to my company supporting a bug bounty on a new website. That is where I realized I’m in a totally different field I know nothing of. I started studying for the Security+ certification, and about the same time I was already doing HTB penetration/CTF type of hacking.
In short, what I have found is the education arm and real life Cyber Security don’t jive at all. There is no college for metasploit, gobuster, reverse shells, sql injections. It’s all hands on. I also found everyone seems to operate just as an individual and not as a team of people doing knowledge sharing and there isn’t a really good community to share their knowledge. Many times it just happens by accident. The InfoSec clubs I’ve been to are terrific (before COVID) but a once a month meeting isn’t enough. Companies need to get involved as a group and sponsor bug bounty related programs. I could go on.
Thanks for reading. 🙂
There is no college? SANS is an accredited institution. Their Master’s Program is pretty robust.
You absolutely get hands on with metasploit, and a whole bunch of tools used in the real world. They update frequently and their instructors are not career teachers, but actual security practitioners. Also, they have a thriving community for continued support.
A low-cost method to understanding the digital technology behind computers, networks, the internet and now IoT devices is to make use of single board computers and microcontrollers. My business students have taken well to these hands-on assignments, and employers have shown interest. Introducing the next generation, especially at the grade school level, to the digital technology that not only underlies but can also improve their world is not easy or inexpensive, but is worth pursuing.
https://eprofessor.azurewebsites.net
Brain,
Check out an article on Self Development on Small Wars Journal by Col. Gregory Conti. smallwarsjournal.com
https://smallwarsjournal.com/jrnl/art/self-development-for-cyber-warriors
Brian,
I got my DoD 8570.01 Cyber certs through unemployment. I had experience but no certs and the government is hard over on certs. The state unemployment people were clueless for white collar, but I found a local tech college at a job fair that knew exactly how to get the funding for three certs.
I shared what I learned with several other unemployed gray-hairs and we all got approved and took the classes and cert exams.
This is such great advice. To start a career in cybersecurity isn’t straingforward and there are no open doors. All the strategies your suggested are what we call “hack your cybersecurity career” at MeetCyber – a global cybersecurity network.
When we can’t find an open door to enter, we should get curious and find a way to open it, or find a back door. Hacking your career can be equally as exciting as hacking a computer. And everything you suggested above, are the hacking techniqies we need to master! Thank you for sharing.
Hmmm, something the younger crowd has never liked to hear including my younger self – schooling isn’t enough, you gotta pay your dues…
Just seems surprising that any course purporting to train and certifiy cybersecurity professionals wouldn’t provide a dummy network for exercises in both hacking and response, or that exams for any diploma or certificate wouldn’t include serious challenges on a prepared network. For trainees to DIY their own networks and security challenges with them seems to encourage a lot of self-deception, and be unlikely to win over a selection committee.
Wow, this is pretty spot-on. Thanks Brian.
Also, studying a bunch of job descriptions might help in getting a feel for what employers want and need or discovering new hiring trends.
Here https://infosec-jobs.com may be a good resource as it’s one of the few job boards dedicated to InfoSec exclusively, covering a huge variety of different roles and levels of experience.
Great article! yeah more than the certificates, I have also been focusing on gaining skills. 2 years back I become a Cyber Security Engineer and I really like what I am doing. Also if anyone is interested, there are great resources to get started/learn:
https://github.com/enaqx/awesome-pentest#network-device-discovery-tools
This article is indeed, spot on. Hopefully it helps prepare some good candidates walking through the door.
– A CISO for a State government Dept.
My advice, find a nonprofit and help them with their technology infrastructure. They need the help and you will learn a lot.
My nonprofit used teens looking for service credits, college interns, and IT/IS students looking for hands on experience.
Most IS students had never seen the inside of a computer, most IT students could not create a batch file or a script.
First thing to do is to be a hacker. Second thing to do is to learn how to do low level code – understand the underlying hardware. Know what a register is – learn what DMA is. Learn what a network stack is… learn assembly for the various flavors of processors out there. Learn the various architectures. Instead of going out to party, go find some network appliance and see if you can break it. Do that over and over again.
Learn the Pieces of Shit OS’s they use and exploit the holes written in the code due to a proliferation of “man-bun-java-jockey, pitiful python pirates” that simply use the BSP (Board Support Package) from the various vendors for ARM A series stuff for final production code – – – because they have little clue as to how it all works, learn how to exploit that.
Learn what an ARM M core is and how it differs from the A series. Learn embedded programming since most edge devices are based on these microcontrollers… Hell, know the difference between a microcontroller and a microprocessor.
Learn how to fingerprint these OS’s. Learn what a MAC/PHY is and how it’s used. Learn how crypto works.
Learn how most humans – that should never be using a computer – can be fooled into doing even more stoopid. Show them that “Practicing Safe Hex” is key. Learn about social engineering, learn about the silly ways that clueless users can be fooled. Do it yourself to your colleagues…
I was lucky enough that when I moved to the D.C. in 1999 that I could only get Covad DSL. And the guy I got it from was Steve Crocker, who wrote RFC 1 (and fucking learn what an RFC is)
I asked him if IPV6 and the like would make a difference in computers and networking being more secure.
“Nope…” was his response. “None of this (ARAPNET) was ever meant to be used as a public switched network” So the commercialization of what Adams and the others did was way beyond the capabilities of most humans to effectively and securely use.
And fucking be passionate about it, see the art in it. At NETSEC (started by two ex-NSA guys) I met some of the best hackers out there. Just F’ing amazing. Most typed > 140 WPM since that’s all they did – they loved it.
One told me – “Security is a practice – not a product” Learn how to teach Practicing Safe Hex (that saying should date me)
I still get calls from those guys that mention, “You see Mr Robot (or whatever the hell it’s called) … see the screen at 15 minutes in?”
“Yea – that’s your exploit/rootkit… maybe you should sue for copyright infringement…” I reply.
You really got to be into this to be worth a shit. Passion.
There’s a great interview with Greg Chaitin the discoverer of the omega number:
https://youtu.be/7OSvTv2SvEM?t=1560
Should start at 26 minutes into it
I say discover but it’s really both (see earlier in the vid where they talk to famous mathematician Roger Pemrose about this – https://youtu.be/7OSvTv2SvEM?t=275 – at about 4:35 into the vid).
But I digress –
See that Chaitin mentions of the passion required.
There’s another story in that series from a physicist that mentioned how his college roommates had posters of hot women and musicians on their wall in the dorm – he had the pic from the Solvay Conference ( https://upload.wikimedia.org/wikipedia/commons/6/6e/Solvay_conference_1927.jpg ) where Einstein/Schrodinger were basically proven wrong and Bohr/Heiseneberg prevailed.
That’s the kind of passion you need to be more than just a cog in the wheel of inadequacy that now seems to proliferate CompSci/Sec.
There’s a great story on my marketturd site (a sister to my main ajawamnet.com site) about one of the low level coders I work with – it’s in a rant called “Mama, I Wanna Be A Maker:
http://www.ajawamnet.com/ajawamnet/mama_i_wanna_be_a_maker.html
Scroll down to the part that starts ” … I recall having a client that had this coder, a PhD, working on a project I designed …”
That’s why you do something… further down on that webpage, see the excerpt from the Second Book of the Tao – The Story of the Woodcarver.
A lack of that is what leads to crap in the workforce.
And the one comment about bug bounty… well, do you recall the saying back in the days of the first reflashable BIOS’ to never use a BIOS that was dated on a Friday, since they’d be trying to hit a compile date (we call them artificial schedules) and get some sort of bonus, and it would brick your motherboard?
I’m dealing with that right now with the Altium app. They released a beta build over the weekend (I’m one of their beta sites) that totally hosed the PCB routing engine.
Here’s a vid I made you might enjoy – why new software sucks…. on my facefuck page:
https://www.facebook.com/wayne.mitzen/videos/1564714290368622/
WAM
http://www.ajawamnet.com
All your write-ups are awesome. Thank you. You are definitely the ‘guru’ of cyber security.