Thousands of people graduate from colleges and universities each year with cybersecurity or computer science degrees only to find employers are less than thrilled about their hands-on, foundational skills. Here’s a look at a recent survey that identified some of the bigger skills gaps, and some thoughts about how those seeking a career in these fields can better stand out from the crowd.

Virtually every week KrebsOnSecurity receives at least one email from someone seeking advice on how to break into cybersecurity as a career. In most cases, the aspirants ask which certifications they should seek, or what specialization in computer security might hold the brightest future.
Rarely am I asked which practical skills they should seek to make themselves more appealing candidates for a future job. And while I always preface any response with the caveat that I don’t hold any computer-related certifications or degrees myself, I do speak with C-level executives in cybersecurity and recruiters on a regular basis and frequently ask them for their impressions of today’s cybersecurity job candidates.
A common theme in these C-level executive responses is that a great many candidates simply lack hands-on experience with the more practical concerns of operating, maintaining and defending the information systems which drive their businesses.
Granted, most people who have just graduated with a degree lack practical experience. But happily, a somewhat unique aspect of cybersecurity is that one can gain a fair degree of mastery of hands-on skills and foundational knowledge through self-directed study and old fashioned trial-and-error.
One key piece of advice I nearly always include in my response to readers involves learning the core components of how computers and other devices communicate with one another. I say this because a mastery of networking is a fundamental skill that so many other areas of learning build upon. Trying to get a job in security without a deep understanding of how data packets work is a bit like trying to become a chemical engineer without first mastering the periodic table of elements.
But please don’t take my word for it. The SANS Institute, a Bethesda, Md. based security research and training firm, recently conducted a survey of more than 500 cybersecurity practitioners at 284 different companies in an effort to suss out which skills they find most useful in job candidates, and which are most frequently lacking.
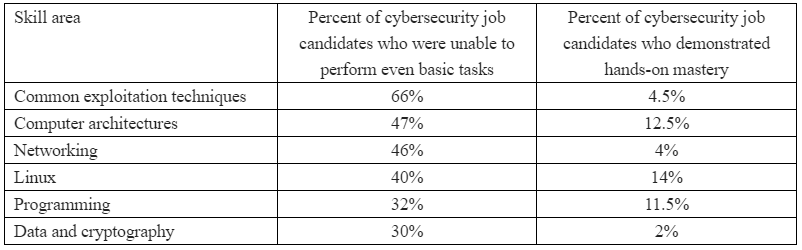
The survey asked respondents to rank various skills from “critical” to “not needed.” Fully 85 percent ranked networking as a critical or “very important” skill, followed by a mastery of the Linux operating system (77 percent), Windows (73 percent), common exploitation techniques (73 percent), computer architectures and virtualization (67 percent) and data and cryptography (58 percent). Perhaps surprisingly, only 39 percent ranked programming as a critical or very important skill (I’ll come back to this in a moment).
How did the cybersecurity practitioners surveyed grade their pool of potential job candidates on these critical and very important skills? The results may be eye-opening:
“Employers report that student cybersecurity preparation is largely inadequate and are frustrated that they have to spend months searching before they find qualified entry-level employees if any can be found,” said Alan Paller, director of research at the SANS Institute. “We hypothesized that the beginning of a pathway toward resolving those challenges and helping close the cybersecurity skills gap would be to isolate the capabilities that employers expected but did not find in cybersecurity graduates.”
The truth is, some of the smartest, most insightful and talented computer security professionals I know today don’t have any computer-related certifications under their belts. In fact, many of them never even went to college or completed a university-level degree program.
Rather, they got into security because they were passionately and intensely curious about the subject, and that curiosity led them to learn as much as they could — mainly by reading, doing, and making mistakes (lots of them).
I mention this not to dissuade readers from pursuing degrees or certifications in the field (which may be a basic requirement for many corporate HR departments) but to emphasize that these should not be viewed as some kind of golden ticket to a rewarding, stable and relatively high-paying career.
More to the point, without a mastery of one or more of the above-mentioned skills, you simply will not be a terribly appealing or outstanding job candidate when the time comes.
BUT..HOW?
So what should you focus on, and what’s the best way to get started? First, understand that while there are a near infinite number of ways to acquire knowledge and virtually no limit to the depths you can explore, getting your hands dirty is the fastest way to learning.
No, I’m not talking about breaking into someone’s network, or hacking some poor website. Please don’t do that without permission. If you must target third-party services and sites, stick to those that offer recognition and/or incentives for doing so through bug bounty programs, and then make sure you respect the boundaries of those programs.
Besides, almost anything you want to learn by doing can be replicated locally. Hoping to master common vulnerability and exploitation techniques? There are innumerable free resources available; purpose-built exploitation toolkits like Metasploit, WebGoat, and custom Linux distributions like Kali Linux that are well supported by tutorials and videos online. Then there are a number of free reconnaissance and vulnerability discovery tools like Nmap, Nessus, OpenVAS and Nikto. This is by no means a complete list.
Set up your own hacking labs. You can do this with a spare computer or server, or with older hardware that is plentiful and cheap on places like eBay or Craigslist. Free virtualization tools like VirtualBox can make it simple to get friendly with different operating systems without the need of additional hardware.
Or look into paying someone else to set up a virtual server that you can poke at. Amazon’s EC2 services are a good low-cost option here. If it’s web application testing you wish to learn, you can install any number of web services on computers within your own local network, such as older versions of WordPress, Joomla or shopping cart systems like Magento.
Want to learn networking? Start by getting a decent book on TCP/IP and really learning the network stack and how each layer interacts with the other.
And while you’re absorbing this information, learn to use some tools that can help put your newfound knowledge into practical application. For example, familiarize yourself with Wireshark and Tcpdump, handy tools relied upon by network administrators to troubleshoot network and security problems and to understand how network applications work (or don’t). Begin by inspecting your own network traffic, web browsing and everyday computer usage. Try to understand what applications on your computer are doing by looking at what data they are sending and receiving, how, and where.
ON PROGRAMMING
While being able to program in languages like Go, Java, Perl, Python, C or Ruby may or may not be at the top of the list of skills demanded by employers, having one or more languages in your skillset is not only going to make you a more attractive hire, it will also make it easier to grow your knowledge and venture into deeper levels of mastery.
It is also likely that depending on which specialization of security you end up pursuing, at some point you will find your ability to expand that knowledge is somewhat limited without understanding how to code.
For those intimidated by the idea of learning a programming language, start by getting familiar with basic command line tools on Linux. Just learning to write basic scripts that automate specific manual tasks can be a wonderful stepping stone. What’s more, a mastery of creating shell scripts will pay handsome dividends for the duration of your career in almost any technical role involving computers (regardless of whether you learn a specific coding language).
GET HELP
Make no mistake: Much like learning a musical instrument or a new language, gaining cybersecurity skills takes most people a good deal of time and effort. But don’t get discouraged if a given topic of study seems overwhelming at first; just take your time and keep going.
That’s why it helps to have support groups. Seriously. In the cybersecurity industry, the human side of networking takes the form of conferences and local meetups. I cannot stress enough how important it is for both your sanity and career to get involved with like-minded people on a semi-regular basis.
Many of these gatherings are free, including Security BSides events, DEFCON groups, and OWASP chapters. And because the tech industry continues to be disproportionately populated by men, there are also a number cybersecurity meetups and membership groups geared toward women, such as the Women’s Society of Cyberjutsu and others listed here.
Unless you live in the middle of nowhere, chances are there’s a number of security conferences and security meetups in your general area. But even if you do reside in the boonies, the good news is many of these meetups are going virtual to avoid the ongoing pestilence that is the COVID-19 epidemic.
In summary, don’t count on a degree or certification to prepare you for the kinds of skills employers are going to understandably expect you to possess. That may not be fair or as it should be, but it’s likely on you to develop and nurture the skills that will serve your future employer(s) and employability in this field.
I’m certain that readers here have their own ideas about how newbies, students and those contemplating a career shift into cybersecurity can best focus their time and efforts. Please feel free to sound off in the comments. I may even update this post to include some of the better recommendations.




…think of it like tennis – the more you practice and play the better you get…
…start with networking, after a year move to apps, etc…
I earned $5000 ultimately by using operating online only for 5 to 8 hours on my computer and this was so smooth that i personally couldn’t accept as true with before working on this website. if you too need to earn this sort of huge cash then come and be part of us. do this internet-website online…………
Yes, I used to be good at PONG……
As for Table Tennis, my cat was much better.
I would add that a good understanding of privacy protection and how to meet compliance is an excellent skill to have. IAPP has lots of free resources and it’s not much to join as a student. The practical nuts and bolts of engineering a good defense also relies on the privacy principles of your home country. A well rounded candidate is alway preferred.
Very true – at my 1st contract, I worked under HIPAA rules, and this followed me for the rest of my career, and was a big advantage as a candidate for hire.
Steve Gibson in his podcast says that programming in assembly is an essential skill too.
Hire HS grads and train them yourselves. You will have a great employee for life!
Hi Mr.Schuster,
Does your company train HS students? What types of students does your company look for?
That doesn’t work out too well in this industry. That may work for certain trades… but in cyber, employers know better.
The turn around time for a cybersecurity profession is much shorter. In Silicon Valley, it is expected that people move on within a few years. Do not expect to get an “employee for life”. You’ll be lucky to get 5 years in some specialties.
Reality says that hiring your own staff for entry level tasks, if you are medium to small, is a money losing proposition. We have leveraged vendor monitoring and event management for a lot of what we do as you can’t pay enough to keep people for more than a year.
“passionately and intensely curious about the subject, and that curiosity led them to learn as much as they could — mainly by reading, doing, and making mistakes ”
I would agree the above and I would also include being able to demonstrate some type of skill set that you’ve been doing for years.
One of the people who got be curious in cybersecurity is Julian Haight , without him I wouldn’t be here on this website.
Dear Brian,
Very nice blog, one aspect which I think you must add is from a soft skills perspective, it is very important for the person identifying the security issue to communicate the business impact in economic terms. Gone are days when the claim to fame was discovering a technical issue, it is much more important today to have an understanding of the business impact.
Good point. The second post in the Comments is so poorly written that I’m not sure it isn’t spam. If it is, indeed, genuine, then it is a perfect example of a failure to communicate anything.
Perhaps part of the issue is that member of the C-Suite (and perhaps job seekers?) see Cybersecurity as a wholly separate discipline that has traditional entry level roles, when in reality, it’s an offshoot of IT. Many roles in Cyber benefit from having spent several years as a network or systems administrator (for roles centered around digital forensics and incident response), or even a web developer (for web application vulnerability testing, or code review). Granted, there are some roles under the larger Cyber umbrella that could readily accept traditional entry level job seekers (usually governance, risk, & compliance), but they’re not seen in the same glamorous light as some of the other roles, which is unfortunate.
I work for a relatively small US company… My Threat teams consist of 11 engineers which are clueless to TCP/3389. You talk network to them and their eyes glaze over faster than a donuts. Last week they accepted a ticket to open TCP/5900 to a core server… Not Mainframe but pretty close…. We are a small 15 Billion $$ company in the US… But WTF. Every year we hire a pentester and I have a lot of fun with these idiot.
My Threat team is total morons…. Pentesters are FUN….
Heck, one of them was a Project Manager before moving to Infosec. Now my respect for PMs has dropped to all new lows… We keep asking out Threat team to take the Comptia Network+ exam but they failed twice.
Funny that a large company like Fiserv needs to console into a newly deployed router to change their WAN IP address on a BGP interface…. We gave Fiserv console access to fix their WAN on a brand new Verizon circuit. I even emailed my team to tell them their IP was wrong…. Made $20 buck on a bet for this one…. Love Indian engineers…
It does not matter what your job is, you go home and study when your family goes to bed…. So that Idiots like me don’t get to mock you on a website…
Whenever I read about the tension between ‘experience’ and ‘training’ I always think of this 1998 study:
Paradox in Project-Based Enterprise: The Case of Film Making
https://www.researchgate.net/profile/Michael_Arthur/publication/237128030_Paradox_in_Project-Based_Enterprise_The_Case_of_Film_Making/links/00b4952badeb3ebe27000000.pdf
It’s not a short read, but get a coffee and settle in.
Fascinating – thank you for sharing.
I’m not in any computer/networking career, but maybe start with asking how they defend their personal devices, network, privacy and identity.
Here is a starter suggestion: Set up the free tool wireshark on your computer and learn how to use it. Then try to answer questions like:
Is my computer part of a netbot?
Are my transmissions encrypted? If so, using what encryption method?
What are the addresses that my computer is communicating with? Who initiated the transmission? The list goes on.
Not sure this is a “start”.
Wireshark looks like Sanskrit if you don’t have networking fundamentals down.
You’ll need a class on the OSI Model among other things first, before Wireshark would make sense.
Looking back at my own BSCS education in the 80s I should have taken advantage of the COOP programs that they offered. This program worked with a number of companies (Texas Instruments was one, Bell South was another) and govt agencies (Naval Surface Weapons Center) and placed students for practical experience. Going into your junior year you would go to school a semester then work a semester(including summers). This program would take the student an additional year to complete but almost always the COOP students were a direct hire at a greater than entry level and almost always was hired by the company that they COPed in. I can’t think of a more applicable need for a COOP program than cyber security. By the time you graduate you would have a years worth of solid experience to bring with you to a prospective employer. A resume of even a new graduate wth that kind of experience was gold.
After a few years of grunt work I made it to a CIO position with the VA hospital here in Hampton Roads. Over the years I was able to work with a number of tech schools in the area to provide practical hands on experience that the students could take with.
Schools have been short sighted in providing good hands on practical training. The were blind to this back in the 80s and haven’t improved a bit.
Wow! In the town that I grew up in, if you didn’t have an good aptitude in math, you didn’t touch the Tyme Sharing System at all…..110 baud was fast back them!
Learning Advanced Basic from books only….Those were the days….
I would like to get into Cyber intelligence or analyst role. Since, I know my capability in knowing Chinese is valuable along with my interest in Cybersecurity. How can I get to analyzing foreign APTs similar to: https://intrusiontruth.wordpress.com/?
In my 20 years in Cybersecurity, there are two primary areas where candidates & junior staff are lacking:
1. Practical knowledge about networks and systems. Networking gets taught horribly in almost every university program. If you can’t explain what happens from when you plug a machine into a network until you are able to connect to some random website, you need to work on that (it’s not that hard).
2. Soft skills. Especially being able to present your ideas in writing or verbally. STEM people with advanced degrees often learn how to give a 10 minute technical talk (where attendees already know 8 of the 10 minutes of content). But have no idea how to talk to someone a few levels above them. They typically can talk all day about the technical details, but don’t start with “what’s the problem & why should you care” in the critical 30-60 seconds before they tune you out.
@Steve,
Learning about networking is so important. I feel like it’s overlooked, both in personal study and in university courses.
I changed careers into IT after 12 years doing something else entirely. I was interning with an IT training and consulting firm literally from the bottom level starting with A+, and a new intern joined us.
She was a CS grad from a good school in our city, and she really wanted to get into cybersecurity. She struggled with CCENT-level stuff because the school apparently focused very little on networking. She was a web developer, did APIs and cool, modem stuff, but… No networking knowledge.
*modern stuff
Meant “modern stuff”.
You’ve found a great lookalike domain attack.
Re: Softskills, that’s why I think everyone needs to do at least one year of helpdesk/desktop so that they learn how to explain what’s going on in non-techie.
So glad to see you link to Stevens for TCP.
My suggestion: learn the vertical you are wanting to break into, as well as the technical skills and capabilities. As a former bank CISO, my most successful hires were people who understood the challenges and frustrations that our specific users faced, and not only had empathy, but were able to understand our business goals, and how a bank/financial services org works. My best hire was an individual who started off at the bank as a teller, then a personal banker, then switched to application support, then IT support, and I poached him. He had such a complete grasp of the business, and could understand the issues people faced and had ideas on how to fix them.
employers should start paying even entry level positions more if they want their security engineers to be masters of several specific job titles which is what this article is implying they want.
Security engineers also have to spend a minimum of 30% of their time practicing and learning as the landscape is constantly changing. Employers need to understand and embrace this, which means sending their engineers to conferences, conventions and paying for security related trainings from third party vendors.
I guess what I’m trying to get at is that it’s not just inadequate applicants that’s the problem – it’s not only a practical and reasonable understanding from the employer on what it takes to be a master in the adequate fields, but also to maintain it.
Lastly, it’s not just about technical skills. Security engineers should also have at least a broad understanding of P&P (Policies and Procedures) as well as best practice security controls. Having skill sets in networking, Linux, exploitation techniques etc. is great but not knowing how and why they apply to the organization is going to be a big problem when trying to find and remediate security gaps because it requires variable solutions not a constant for every company – hence the need for compensating controls.
Great article Brian. Shared with several associates. In addition to a solid understanding of networking protocols, computer architectures, programming techniques and IT operations, I’d suggest developing critical thinking skills. Problem solving and analytical processes are difficult or impossible to teach – they can only be learned. Younger interns are sorely lacking. Nobody has coached them. Senior team must mentor and develop junior team members in developing an analytical approach and critical thinking skills.
How can you possibly be a cybersecurity expert if you do not understand networking or how servers and software work?
I would think that at the very least you would have a Network+ and a CCNA just to start.
Another thing is if you only have schooling and certs what you need next is a lot of experience and proper mentoring. A good IT person absolutely learns new things EVERY day.
I love this article.
I have been preaching this for years to my friends and New Comers to Cyber – there is Good source also By Daniel Miessler how to brak into Cyber a well written Path
Friend who is a network engineer, experienced and talented–got his Masters in IT security from a top rated university. Even with his Masters, he couldn’t get hired, as everyone said “experienced only” and he interviewed with many companies. After 6-8 months and multiple interviews he got hired–finally, then they reorganized and laid him and many other people off after 4-5 months. He’s given up on the field and made a lateral move. Timely article here Brian, thank you
I run a Secops team. I’m disheartened by the lack of skills around simple troubleshooting. Learn how to identify an issue, have a systematic approach to unpicking the problem with all the tools and data at your disposal, to identify root cause. This means you need to understand networking, operating systems and applications. If you can’t do this, you will struggle…
Hello Dear,
Totally agree with your words that most important is their practical skills. Because, this is not a job where you will be trained separately. If you have skills and practical knowledge only then you will have a successful career in cybersecurity field.
Learning and skill development is a slow process. Focus on thing at a time is the key. The skills listed in the article are all very important. However it takes time to grasp each one. So a person coming from a programming, system administration or computer network, identity management background can step up more easily.
I was a 1st- and 2nd-line manager for years (not in Cyber), but during all those years of interviewing and hiring, I looked more for someone’s demonstrable ability to learn over what they already knew (fully acknowledging that the schools were aligned with the trope “In theory, there’s no difference between theory and practice. In practice, that is hardly ever true.” They taught theory, but no practice. And I fully leveraged the team interview structure — I had another guy that would give them the technical grilling (“In a few words, what’s the practical difference between /dev/mem and /dev/kmem?”).
But the comments regarding soft skills cannot be emphasized enough, IMO. Because I mainly managed internal support teams, they needed to be articulate, with communications targeted to the level and orientation of their audience. I would use the old (over-used) interview question of “tell me how a toilet works”. I didn’t even care if they got the mechanics right — I wanted to see how they went about describing the process (visually vs. graphically, etc.).
And I absolutely tiered my internal team structure such that my ‘village elders’ had a dedicated slice of their time dedicated to mentoring and coaching.
Learning how regular expressions work is also something I have recommended to people who ask this question. So many things are made easier with a good understanding of regex (search & replace, Splunk field extraction & searching, IDS tools etc).
I see ads on TV all the time saying you can get a high paying job as a cyber security expert in as little a 9 months. Sign me up!
A great resource to learn web application security attacks https://application.security/free-application-security-training
Set the wayback machine for 2004. I was still a college student. My major was IT. I was roommates with a CS major.
I was up for an internship as a lab assistant at my college. Nothing fancy, re-image broken machines, help students get apps running, manage and support the lab network.
I turned it down (got a slightly better internship at a private company) My roommate got the gig. First day on the job, he called me. He had re-imaged a host and had no idea how to bind it to the domain. Junior year of his CS BS/MS program, couldnt actually join a windows host to a windows domain. Also couldnt do any networking (CS students didnt get any networking at that time).
I find the best is a mix of theoretical and practical. Practical ages the fastest, whereas theoretical is generally ageless. However, theoretical foundations arent usually useful for getting things done (for example, you can understand the RFC for TCP, but not know at all how to configure your core switch or border firewall).