The FBI confirmed this week that a relatively new ransomware group known as DarkSide is responsible for an attack that caused Colonial Pipeline to shut down 5,550 miles of pipe, stranding countless barrels of gasoline, diesel and jet fuel on the Gulf Coast. Here’s a closer look at the DarkSide cybercrime gang, as seen through their negotiations with a recent U.S. victim that earns $15 billion in annual revenue.

Colonial Pipeline has shut down 5,500 miles of fuel pipe in response to a ransomware incident. Image: colpipe.com
New York City-based cyber intelligence firm Flashpoint said its analysts assess with a moderate-strong degree of confidence that the attack was not intended to damage national infrastructure and was simply associated with a target which had the finances to support a large payment.
“This would be consistent with DarkSide’s earlier activities, which included several ‘big game hunting’ attacks, whereby attackers target an organization that likely possesses the financial means to pay the ransom demanded by the attackers,” Flashpoint observed.
In response to public attention to the Colonial Pipeline attack, the DarkSide group sought to play down fears about widespread infrastructure attacks going forward.
“We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for other our motives [sic],” reads an update to the DarkSide Leaks blog. “Our goal is to make money, and not creating problems for society. From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
First surfacing on Russian language hacking forums in August 2020, DarkSide is a ransomware-as-a-service platform that vetted cybercriminals can use to infect companies with ransomware and carry out negotiations and payments with victims. DarkSide says it targets only big companies, and forbids affiliates from dropping ransomware on organizations in several industries, including healthcare, funeral services, education, public sector and non-profits.
Like other ransomware platforms, DarkSide adheres to the current badguy best practice of double extortion, which involves demanding separate sums for both a digital key needed to unlock any files and servers, and a separate ransom in exchange for a promise to destroy any data stolen from the victim.
At its launch, DarkSide sought to woo affiliates from competing ransomware programs by advertising a victim data leak site that gets “stable visits and media coverage,” as well as the ability to publish victim data by stages. Under the “Why choose us?” heading of the ransomware program thread, the admin answers:
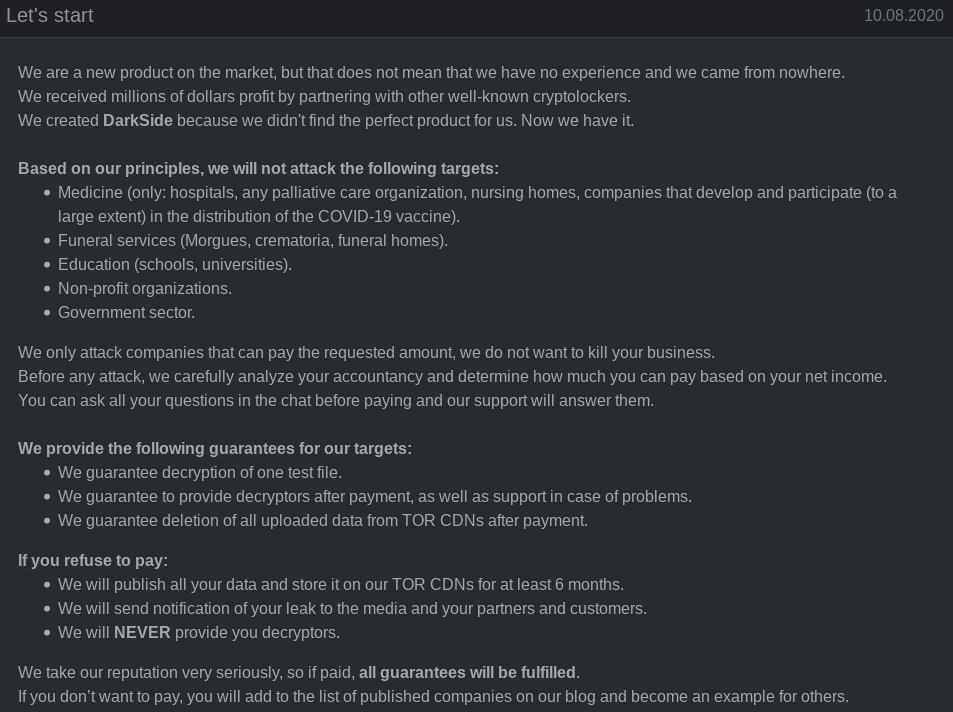
An advertisement for the DarkSide ransomware group.
“High trust level of our targets. They pay us and know that they’re going to receive decryption tools. They also know that we download data. A lot of data. That’s why the percent of our victims who pay the ransom is so high and it takes so little time to negotiate.”
In late March, DarkSide introduced a “call service” innovation that was integrated into the affiliate’s management panel, which enabled the affiliates to arrange calls pressuring victims into paying ransoms directly from the management panel.
In mid-April the ransomware program announced new capability for affiliates to launch distributed denial-of-service (DDoS) attacks against targets whenever added pressure is needed during ransom negotiations.
DarkSide also has advertised a willingness to sell information about upcoming victims before their stolen information is published on the DarkSide victim shaming blog, so that enterprising investment scammers can short the company’s stock in advance of the news.
“Now our team and partners encrypt many companies that are trading on NASDAQ and other stock exchanges,” DarkSide explains. “If the company refuses to pay, we are ready to provide information before the publication, so that it would be possible to earn in the reduction price of shares. Write to us in ‘Contact Us’ and we will provide you with detailed information.”
DarkSide also started recruiting new affiliates again last month — mainly seeking network penetration testers who can help turn a single compromised computer into a full-on data breach and ransomware incident.
“We have grown significantly in terms of the client base and in comparison to other projects (judging by the analysis of publicly available information), so we are ready to grow our team and a number of our affiliates in two fields,” DarkSide explained. The advertisement continued:
“Network penetration testing. We’re looking for one person or a team. We’ll adapt you to the work environment and provide work. High profit cuts, ability to target networks that you can’t handle on your own. New experience and stable income. When you use our product and the ransom is paid, we guarantee fair distribution of the funds. A panel for monitoring results for your target. We only accept networks where you intend to run our payload.”
DarkSide has shown itself to be fairly ruthless with victim companies that have deep pockets, but they can be reasoned with. Cybersecurity intelligence firm Intel 471 observed a negotiation between the DarkSide crew and a $15 billion U.S. victim company that was hit with a $30 million ransom demand in January 2021, and in this incident the victim’s efforts at negotiating a lower payment ultimately reduce the ransom demand by almost two-thirds.
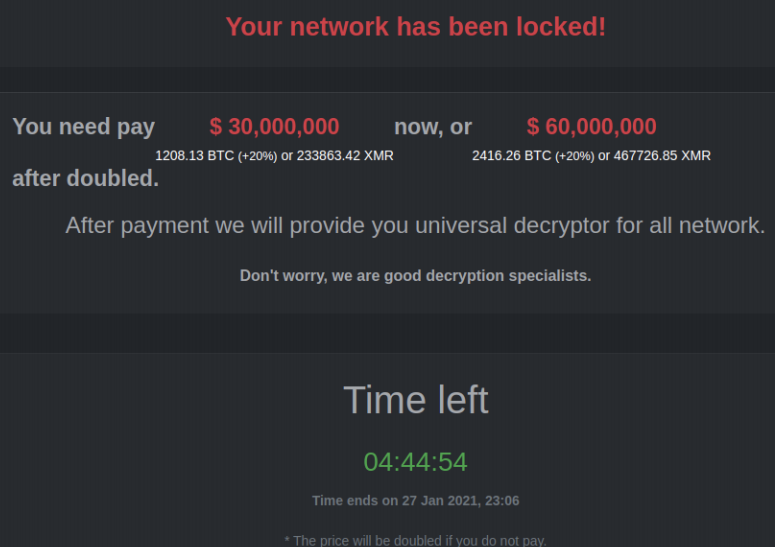
The DarkSide ransomware note.
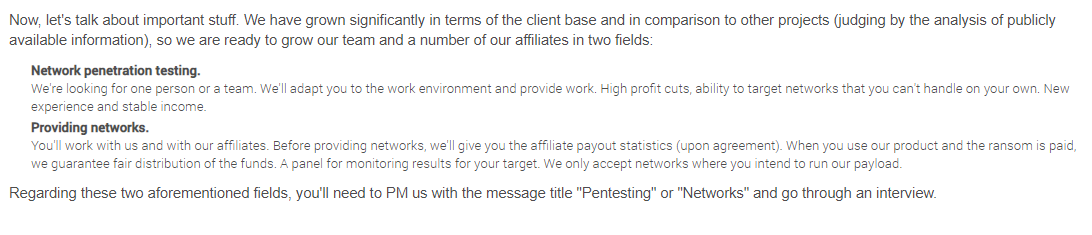
The first exchange between DarkSide and the victim involved the usual back-and-forth establishing of trust, wherein the victim asks for assurances that stolen data will be deleted after payment.
When the victim counter-offered to pay just $2.25 million, DarkSide responded with a lengthy, derisive reply, ultimately agreeing to lower the ransom demand to $28.7 million.
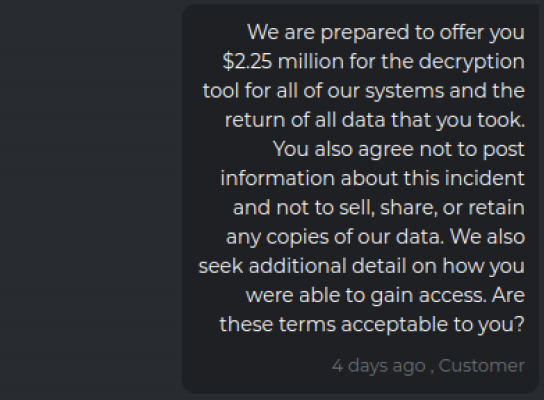
“The timer it [sic] ticking and in in next 8 hours your price tag will go up to $60 million,” the crooks replied. “So, you this are your options first take our generous offer and pay to us $28,750 million US or invest some monies in quantum computing to expedite a decryption process.”
Image: Intel 471.
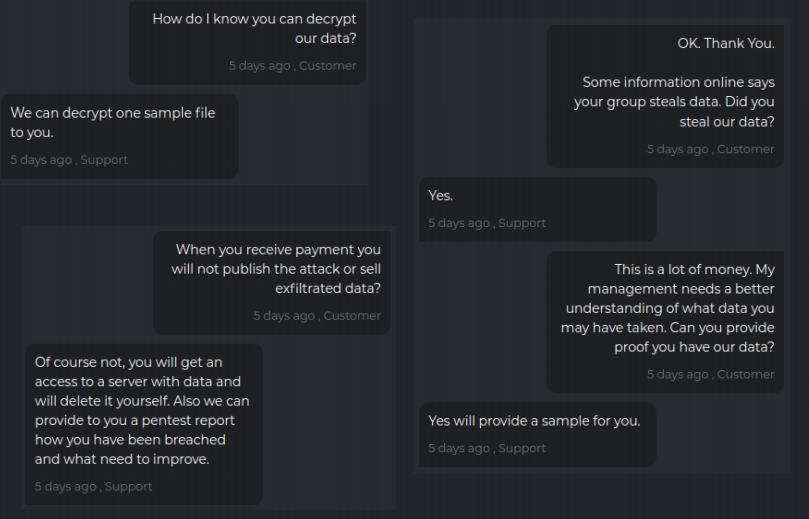
The victim complains that negotiations haven’t moved the price much, but DarkSide countered that the company can easily afford the payout. “I don’t think so,” they wrote. “You aren’t poor and aren’t children if you f*cked up you have to meet the consequences.”
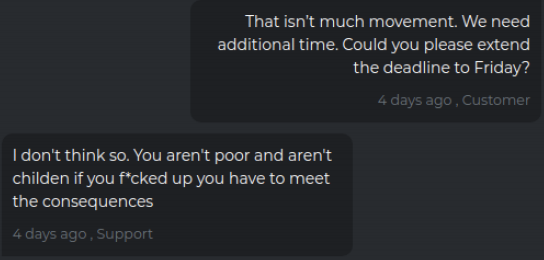
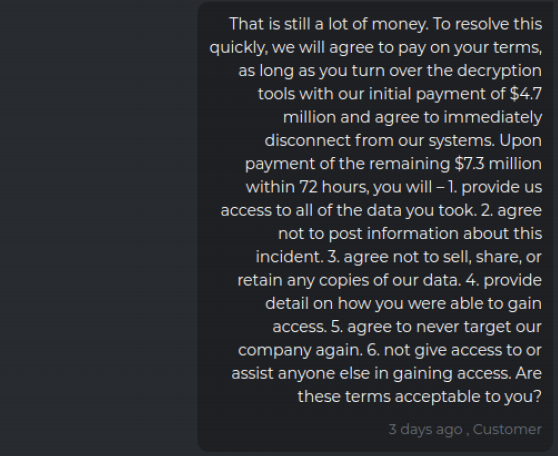
The victim firm replies a day later saying they’ve gotten authority to pay $4.75 million, and their tormentors agree to lower the demand significantly to $12 million.
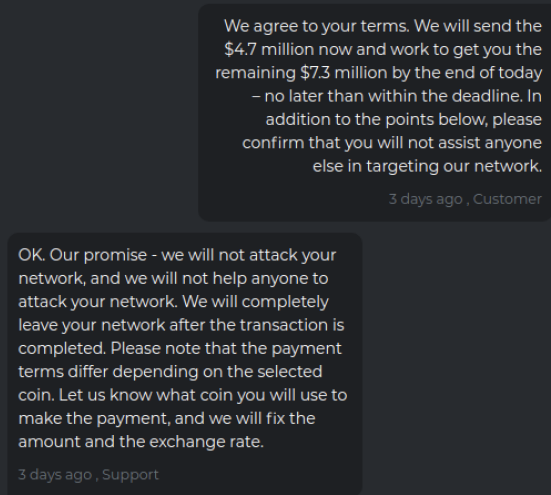
The victim replies that this is still a huge amount, and it tries to secure additional assurances from the ransomware group if it agrees to pay the $12 million, such as an agreement not to target the company ever again, or give anyone access to its stolen data. The victim also tried to get the attackers to hand over a decryption key before paying the full ransom demand.
The crime gang responded that its own rules prohibit it from giving away a decryption key before full payment is made, but they agree to the rest of the terms.
The victim firm agrees to pay an $11 million ransom, and their extortionists concur and promise not to attack or help anyone else attack the company’s network going forward.
Flashpoint assesses that at least some of the criminals behind DarkSide hail from another ransomware outfit called “REvil,” a.k.a. “Sodinokibi” (although Flashpoint rates this finding at only “moderate” confidence). REvil is widely considered to be the newer name for GandCrab, a ransomware-as-a-service offering that closed up shop in 2019 after bragging that it had extorted more than $2 billion.
Experts say ransomware attacks will continue to grow in sophistication, frequency and cost unless something is done to disrupt the ability of crooks to get paid for such crimes. According to a report late last year from Coveware, the average ransomware payment in the third quarter of 2020 was $233,817, up 31 percent from the second quarter of last year. Security firm Emsisoft found that almost 2,400 U.S.-based governments, healthcare facilities and schools were victims of ransomware in 2020.
Last month, a group of tech industry heavyweights lent their imprimatur to a task force that delivered an 81-page report to the Biden administration on ways to stymie the ransomware industry. Among many other recommendations, the report urged the White House to make finding, frustrating and apprehending ransomware crooks a priority within the U.S. intelligence community, and to designate the current scourge of digital extortion as a national security threat.
Further reading: Intel 471’s take on the Colonial Pipeline attack.





I would have thought that 11 mill can buy a pretty healthy cyber security outfit. Too late now I guess.
11 mil might get you a good team of people, but any major enterprise buying software to load up their systems with the requisite controls needed is gonna spend well over 11 million doing so. A good EDR package can easily be double that cost for a fortune 500 company.
Send in the assassins, F me F you!. Thats how the world works. Any other response is virtue signaling.
https://www.adamsmith.org/blog/stop-saying-virtue-signalling#:~:text=Good%20university%20degrees%20might%20be,means%20%E2%80%93%20it's%20credible%20and%20honest.
Or you back up your data like anyone with at least half a brain in this digital age should do.
I’m sorry but people ignoring Cybersecurity this blatantly are basically begging to be robbed blind.
Or….we treat them like Unlawful Combatants and send them to Club Gitmo. It is a form of terrorism after all. Grill the perps for a few months, may be they are part of a broader conspiracy.
Relax. Not all crime is the dreaded T Word. If you dilute the word terrorism, by over extending the definition to include everything like extortion… Then real terrorists aren’t taken seriously.
yeah lets torture!!
You have to find them to send them anywhere and that is unlikely to happen.
Who are they going to arrest? Mr. Darkside? This is being attributed to a Russian group and they don’t know exactly who they are. Russia doesn’t extradite it’s citizens so the better thing to do is better cyber security practices. Companies spend on all kinds of crap but treat IT as some crap they have to spend money on. Once this stuff happens they suddenly understand why it’s important.
The idea that this is just a random group of guys interested in stealing a corporation’s lunch money doesn’t sit right with me. Their insistence that there is no broader geopolitical motive only makes it more suspicious. Is anything ever that simple these days?
We like to point the finger at Russia as the go-to bad guy for all of these spooky cyber crimes, but as it stands, much of America’s computer hardware and security software contains backdoors installed by Israeli tech companies. Coincidentally, Israelis also make up a lot of top players in the US oil markets. Would be interesting to see the market moves leading up to this and find out who, if anyone, is making money on it.
Not saying a gang of nerds in a Moscow basement couldn’t pull this off, but I think it’s worth paying attention to who has their hands on our equipment prior to its installation in American infrastructure. Russian attackers are at a distinct disadvantage on that front.
Everything you say somehow comes back to two things, something in relation to raising blacks at the expense of whites, or hating Israel. Find something else to do, you have children don’t you, you’re setting them up with a looooot of enemies by constantly trying to be controversial. Just some food for thought brother, might make less selfish social choices.
You should visit the Darkweb sometime. You wouldn’t believe the organized criminal activity that goes on. It doesn’t surprise me in the least that a group of hackers could pull this kind of criminal enterprise off without government influence. Look at the drug cartels who influence governments rather than the other way around.
It would not surprise me a single bit to learn that Darkside = Israeli Intelligence. Or they could very well be affiliated within or find sanctuary inside a Mossad safe-house to comfortably run these ops.
Ask a bank robber why he robs banks. That’s where the money is.
Profit motive is simple, but also is indeed all the motivation a person needs. Political motivations and conspiracy are the complex narratives that are usually false.
Occam’s Razor
lol they literally said who they were and are well known on the dark web. You are the type of person to not understand VPN or Torr browsers yet spout off nonsense about conspiracies lmfao. They are an illegal online business buddy. It’s not new and they cant be tracked with the tech we have today. Google the silkroad and then silkroad 2.0 to get a basic understanding of how blockchain info works and then maybe, just maybe, you would understand how dumb you sound saying Israel is attacking the US infrustructure while basically having a civil war between themselves and palestine. Sounds like a terrible idea strategically but it is a conspiracy after all. It does not need to make sense.
I agree it is pretty funny after just listening to Judge Jeanine on Fox specifically stating that in 2020 said that there was going to be a cyber-attack on pipelines and ransoms I wonder who’s behind this really?
Bhahaha..
It’s when CIA meets Customer Service!!
Who knew screwing with sheep’s was so easy!!
Bhahaha!!
Aren’t there insurance policies against this kind of thing?
Yes and the insurance companies only care about $$$- is it cheaper to pay out than to repair and restore systems?
However the promise of payout guarantees ransomware groups will only increase in activity.
There is but in the last year the cost of cyber risk insurance has gone way up and the coverage has gone way down.
insurance payouts are based on meeting a minimum set of controls. if they can demonstrate that you didn’t have those controls in place to mitigate your overall risk, then they might well not cover your losses, or drastically reduce their responsibility in making you whole again.
follow the money and you’ll find the scoundrels responsible
you can’t follow crypto
you’re a fool if you think crypto is untraceable.
So if that’s true, how did these guys nail more than one high dollar target?
They demand payment in crypto for the obvious reason that it works.
can’t trace monero
delusions of grandeur. 20 years of air and drone strikes did do anything to cabe dwelling donkey riders w pee shootrrs in afpak and your fanboi-ing of the idf is humorous since back in 2006 hassan and hezb-allah without an airforce or sams or aaa fire kicked israeli ass out of lebanon. the idf couldnt even get to the litani river and had to concede and withdraw. but you can fantasize all you want in your fetid little tiny head.
You cant track monero. That is why the IRS offered a $500k bounty to try.
All money is traceable. But tracks can be erased with varying degrees of difficulty.
Cash can be laundered, but takes lots of overhead and middlemen.
Crypto can be laundered in tumblers… But it’s vastly easier, automated, cheap, and quicker.
you’re a fool if you don’t understand how blockchain works and try to tell others THEY don’t know lmfao.
BOOMER ALERT!
” Boomer Alert”??? I’m a Boomer, coding my research projects in Uni when it had to be done SPSS, Fortran, COBOL, C……Now I pentest on sterile hardware using VM and Whonix with Kali over proxy chains….at 68 years old. Stick your Boomer criticism up your ass, noob
Just out of curiosity, What are the means here for communications between a company which is paying and crackers? Via email, some chat software?, SMS?
The bad guys running the ransomware service typically have their own portal which has the chat function.
Pretty sure, despite their claim otherwise, they have stepped into the realm of “Geopolitics” by interfering with government operations in the US and Russia…Watch your back! I’m sure it will be quick and very painful as you will become a public example what happens when you cross that line.
The pipeline, as well as much of the US infrastructure, is in the hands of private industry.
Any overlap into geopolitics is incidental.
Pretty sure, despite their claim otherwise, they have stepped into the realm of “Geopolitics” by interfering with government operations in the US and Russia…Watch your back! I’m sure it will be quick and very painful as you will become a public example what happens when you cross that line.
You should visit the Darkweb sometime. You wouldn’t believe the organized criminal activity that goes on. It doesn’t surprise me in the least that a group of hackers could pull this kind of criminal enterprise off without government influence. Look at the drug cartels who influence governments rather than the other way around.
Obviously this gas crisis is Trump’s fault. The FBI, CIA, NSA, ad nauseum had to spend so many resources spying on Trump and any of his staff or supporters, lest they communicate with RUSSIA!!!, they had no resources left for cybersecurity.
That sounds absurd, but okay. Surely you’ve heard of redundancy in the tech world yeah? Who shut down which pipeline? Hmm, yeah exactly… In the tech world when you want to move critical infrastructure into a new space or server? The answer is you do it slowly over time.. This Biden administration pulled the carpet right out from under all of us and decided to use windmills.. How’d it go for Texas again? Hmm see now we’re learning…..
You cant track monero. That is why the IRS offered a $500k bounty to try.
Organised Crime has investments in some of the targets.
They don’t play by the rules, and hitmen are cheap.
The difficulty is identifying the perps.
They don’t care if they get a few others by mistake as well.
Just stating the obvious.
What do we know about Darkside’s cybersecurity? Do we have folks able to penetrate it and muddle their computer files? What are we waiting for?
If not their headquarters would seem an ideal target for a Predator attack.
Trump was reluctant to offend the Russians–probably because of business connections there. What is our excuse now?
Our folks seem inept and clueless. The Israelis would already have it done.
If in doubt, perhaps we could ask the Israelis to take care of it for us!!
They found the perfect victim:
Tech audit of Colonial Pipeline found ‘glaring’ problems
https://apnews.com/article/va-state-wire-technology-business-1f06c091c492c1630471d29a9cf6529d
DarkSide is a “gang” like Guccifer 2.0 was an “activist”.
Right…
Will anyone learn form this? Attacks on our infrastructure have happened (ie: water plant in Florida last year), make news, everyone gets animated about it, then it’s on to the next problem. The gov’t offers to step in and help and then nothing happens. It’s the same old thing every-time. Companies spend billions globally in payments to these attack groups. And yet here we are.
Will anyone learn form this? Attacks on our infrastructure have happened (ie: water plant in Florida last year), make news, everyone gets animated about it, then it’s on to the next problem. The gov’t offers to step in and help and then nothing happens. It’s the same old thing every-time. Companies spend billions globally in payments to these attack groups. And yet here we are.
We need to embolden American cybercriminals to attack russian networks the same way. How many American hacker groups exclusively target CIS countries? I can give you thousands of the reverse. Only tit for tat will bring them to the negotiating table to reduce these kinds of attacks.
I can use this information to assist my clients with their decision making on Cyber Security moving forward
So many users in these comments are in such a hurry to offer their opinion on topics they are blatantly ignorant to. This is the true American virus, the culturally American epidemic. There is no more time left to overcome this habit, if its not already too late.
1. The man who is trying to seem like the smartest in the room has the least value in society and his idiocy spreads like a plague. His opinion and advice and mindless chattering has a compounded negative effect on all that ripples outward.
2. Misinformation is death. It is a mortal sin. These seekers of attention must be stomped out at the very first sight. Herd them with aggression, they are highly offensive and extremely dangerous. Cull those who do not comply.
Great, the psycho contingent has arrived.
Here is another one today but a health service – so much for the ‘thiefs of honour’
https://www.rte.ie/news/health/2021/0514/1221537-hse-cyber-attack/
p
Conti is the group behind the Ireland Health System attack not Darkside
Unless the world takes this threat seriously, this will continue. A new “Manhattan Project” is needed to:
1. Develop and implement the means for a thorough and complete forensic investigation of crime conducted using
cloud networks and local networks.
a. A specific goal is to quickly identify and capture those responsible for cyber-crime.
b. Another goal is the rapid preparation of legal documentation required to take action. Delays only favor the
criminals.
2. Develop methods that make the adoption of restore points capable of negating the effects of ransomware and
malware.
3. Cloud vendors must fully completely disclose information on how the their networks score against STIGs and other
security standards. This must describe in laymen’s terms the risks to the exposure of financial, medical, IP, and
client data to their networks.
4. Legislation needs to be updated to make the penalties match the magnitude of the damage.
a. It should be illegal for those convicted of cyber-crime to touch any form of computer unless supervised by vetted
FBI, Interpol, CIA, NSA, etc. agents. This must be a lifetime ban.
b. Persons convicted of cyber-crime cannot be paroled if doing so puts the criminal in close proximity to a computer,
smartphone or any digital device.
c. It should be illegal for anyone to sell or profit from cyber-crime by selling stories to the media in any form.
d. Family members and peers of those convicted of cyber-crime must be investigated to determine the extent of
efforts to aid and abet cyber-crime.
e. Those who have conducted or aided in the execution of cyber-crime are personally liable for the damages and
additional penalties.
f. A new workflow is needed to remove impediments, the exchange of information, and on-going work of
international law enforcement agencies for cyber-crime cases.
In white hack college or good hack actually means at community college for only a few months the hack problem was in congress and Obama involved in creating a bill and plan with a national meeting that leaned toward insurance laws due to expenses or a truly secure company system being too expensive so just get cheaper insurance that covers damages if hacked. Looks to me there is deeper things goin on here like Obama and that gang posing as bad gangs hidden behind FBI doing normal harm work here ripping off money suffering the victims who are forced buy the product
Great Article
By the way security Researchers describe how DarkSide ransomware group operate when victims refuse to pay ransom
https://www.hackers-review.net/2021/05/security-researchers-talk-about.html
“Freedom itself was attacked by a faceless coward. We are a country awakened to danger and called to defend freedom and freedom will b defended. Our grief has turned to anger and anger to resolution. Whether we bring our enemies to justice or bring justice to our enemies, justice will be done.
I want to reassure the American people that the full resources of the federal government are working to assist U.S. to help the victims of these attacks.
Make no mistake. The United States will hunt down and punish those responsible and the nations that harbor for these cowardly acts.
Our military home and around the world is on high alert status.
From this day forward, any nation that continues to harbor or support e-terrorism will be regarded by the United States as a hostile regime. Our nation has been put on notice, we’re not immune from attack. We will take defensive measures against terrorism to protect Americans.
The resolve of our great nation is being tested. Make no mistake. We will show the world that we can pass this test.”
Money talks, total loss from these attacks is vastly more than the tiny ransoms paid out, so do a deal with one of putins cronies, $3b of clean money, and you have a quiet words with a few of your “innovatve” IT cowboys at home..
Although as many have also said, anyone getting caught out these day’s deserves everything they get hit with or for, it’s all basic stuff…
Perhaps we could get most of the world’s govs to sign up to an agreement declaring certain people or groups as “outlaw”, in its proper meaning, you are outside the protection of any laws, ANYONE wanting to rob or kill you is not committing an offence.
Fun life, looking over shoulder constantly,while working out if you dare trust anyone, ever, worrying everytime someone looks at you twice.
Knowing what the consequences will be if you get found out will put an awful lot of people off starting, you may possibly have little regard for law agencies etc, but they know what greed does to people, lots of desperate people in the world willing to risk much, outlaws make good, easier targets..
Declare them terrorists, find them and send in Seal Team 6 to capture/kill them.
Once the little wiener-heads realize their lives are on the line, they may think twice. As it is, they face almost no penalties for their perfidy. Up the ante.
And make it a felony to pay ransom to cyberthieves/terrorists.