A 31-year-old Canadian man has been arrested and charged with fraud in connection with numerous ransomware attacks against businesses, government agencies and private citizens throughout Canada and the United States. Canadian authorities describe him as “the most prolific cybercriminal we’ve identified in Canada,” but so far they’ve released few other details about the investigation or the defendant. Helpfully, an email address and nickname apparently connected to the accused offer some additional clues.

Matthew Philbert, in 2016.
Matthew Philbert of Ottawa, Ontario was charged with fraud and conspiracy in a joint law enforcement action by Canadian and U.S. authorities dubbed “Project CODA.” The Ontario Provincial Police (OPP) on Tuesday said the investigation began in January 2020 when the U.S. Federal Bureau of Investigation (FBI) contacted them regarding ransomware attacks that were based in Canada.
“During the course of this investigation, OPP investigators determined an individual was responsible for numerous ransomware attacks affecting businesses, government agencies and private individuals throughout Canada as well as cyber-related offenses in the United States,” reads an OPP statement.
“A quantity of evidentiary materials was seized and held for investigation, including desktop and laptop computers, a tablet, several hard drives, cellphones, a Bitcoin seed phrase and a quantity of blank cards with magnetic stripes,” the statement continues.
The U.S. indictment of Philbert (PDF) is unusually sparse, but it does charge him with conspiracy, suggesting the defendant was part of a group. In an interview with KrebsOnSecurity, OPP Detective Inspector Matt Watson declined to say whether other defendants were being sought in connection with the investigation, but said the inquiry is ongoing.
“I will say this, Philbert is the most prolific cybercriminal we’ve identified to date in Canada,” Watson said. “We’ve identified in excess of a thousand of his victims. And a lot of these were small businesses that were just holding on by their fingernails during COVID.”
A DARK CLOUD
There is a now-dormant Myspace account for a Matthew Philbert from Orleans, a suburb of Ottawa, Ontario. The information tied to the Myspace account matches the age and town of the defendant. The Myspace account was registered under the nickname “Darkcloudowner,” and to the email address dark_cl0ud6@hotmail.com.
A search in DomainTools on that email address reveals multiple domains registered to a Matthew Philbert and to the Ottawa phone number 6138999251 [DomainTools is a frequent advertiser on this site]. That same phone number is tied to a Facebook account for a 31-year-old Matthew Philbert from Orleans, who describes himself as a self-employed “broke bitcoin baron.”
Mr. Philbert did not respond to multiple requests for comment.
According to cyber intelligence firm Intel 471, that dark_cl0ud6@hotmail.com address has been used in conjunction with the handle “DCReavers2” to register user accounts on a half-dozen English-language cybercrime forums since 2008, including Hackforums, Blackhatworld, and Ghostmarket.
Perhaps the earliest and most important cybercrime forum DCReavers2 frequented was Darkode, where he was among the first two-dozen members. Darkode was taken down in 2015 as part of an FBI investigation sting operation, but screenshots of the community saved by this author show that DCReavers2 was already well known to the Darkode founders when his membership to the forum was accepted in May 2009.
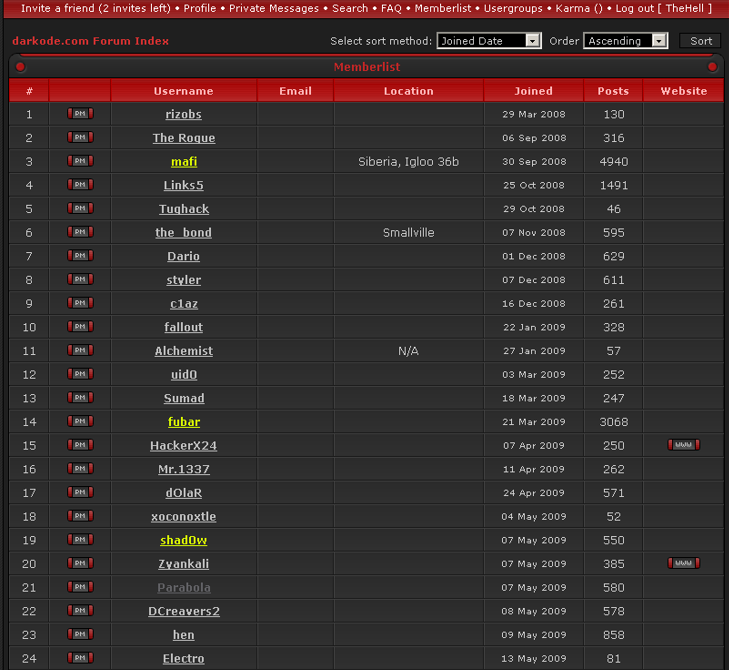
DCReavers2 was just the 22nd account to register on the Darkode cybercrime forum.
Most of DCReavers’s posts on Darkode appear to have been removed by forum administrators early on (likely at DCReavers’ request), but the handful of posts that survived the purge show that more than a decade ago DCReavers2 was involved in running botnets, or large collections of hacked computers.
“My exploit pack is hosted there with 0 problems,” DCReaver2 says of a shady online provider that another member asked about in May 2010.
Searching the Web on “DCreavers2” brings up a fascinating chat conversation allegedly between DCReavers2 and an individual in Australia who was selling access to an “exploit kit,” commercial crimeware designed to be stitched into hacked or malicious sites and exploit a variety of Web-browser vulnerabilities for the purposes of installing malware of the customer’s choosing.
In that 2009 chat, indexed by the researchers behind the website exposedbotnets.com, DCReavers2 uses the Dark_Cl0ud6 email address and actually shares his real name as Matthew Philbert. DCReavers2 also says his partner uses the nickname “The Rogue,” which corresponds to a former Darkode administrator who was the second user ever registered on the forum (see screenshot above).
In that same conversation, DCReavers2 discusses managing a botnet built on ButterFly Bot. Also known as “Mariposa,” ButterFly was a plug-and-play malware strain that allowed even the most novice of would-be cybercriminals to set up a global operation capable of harvesting data from thousands of infected PCs, and using the enslaved systems for crippling attacks on Web sites. The ButterFly Bot kit sold for prices ranging from $500 to $2,000.
An advertisement for the ButterFly Bot.
The author of ButterFly Bot — Slovenian hacker Matjaz “Iserdo” Skorjanc — was Darkode’s original founder back in 2008. Arrested in 2010, Skorjanc was sentenced to nearly five years in prison for selling and supporting Mariposa, which was used to compromise millions of Microsoft Windows computers.
Upon release from prison, Skorjanc became chief technology officer for NiceHash, a cryptocurrency mining service. In December 2017, $52 million worth of Bitcoin mysteriously disappeared from NiceHash coffers. In October 2019, Skorjanc was arrested in Germany in response to a U.S.-issued international arrest warrant for his extradition.
The indictment (PDF) tied to Skorjanc’s 2019 arrest also names several other alleged founding members of Darkode, including Thomas “Fubar” McCormick, a Massachusetts man who was allegedly one of the last administrators of Darkode. Prosecutors say McCormick also was a reseller of the Mariposa botnet, the ZeuS banking trojan, and a bot malware he allegedly helped create called “Ngrbot.” The U.S. federal prosecution against Skorjanc and McCormick is ongoing.
At the time the FBI dismantled Darkode in 2015, the Justice Department said that out of 800 or so crime forums worldwide, Darkode was the most sophisticated English-language forum, and that it represented “one of the gravest threats to the integrity of data on computers in the United States and around the world.”
Some of Darkode’s core members were either customers or sellers of various “locker” kits, which were basically web-based exploits that would lock the victim’s screen into a webpage spoofing the FBI or Justice Department and warning that victims had been caught accessing child sexual abuse material. Victims who agreed to pay a “fine” of several hundred dollars worth of GreenDot prepaid cards could then be rid of the PC locker program.
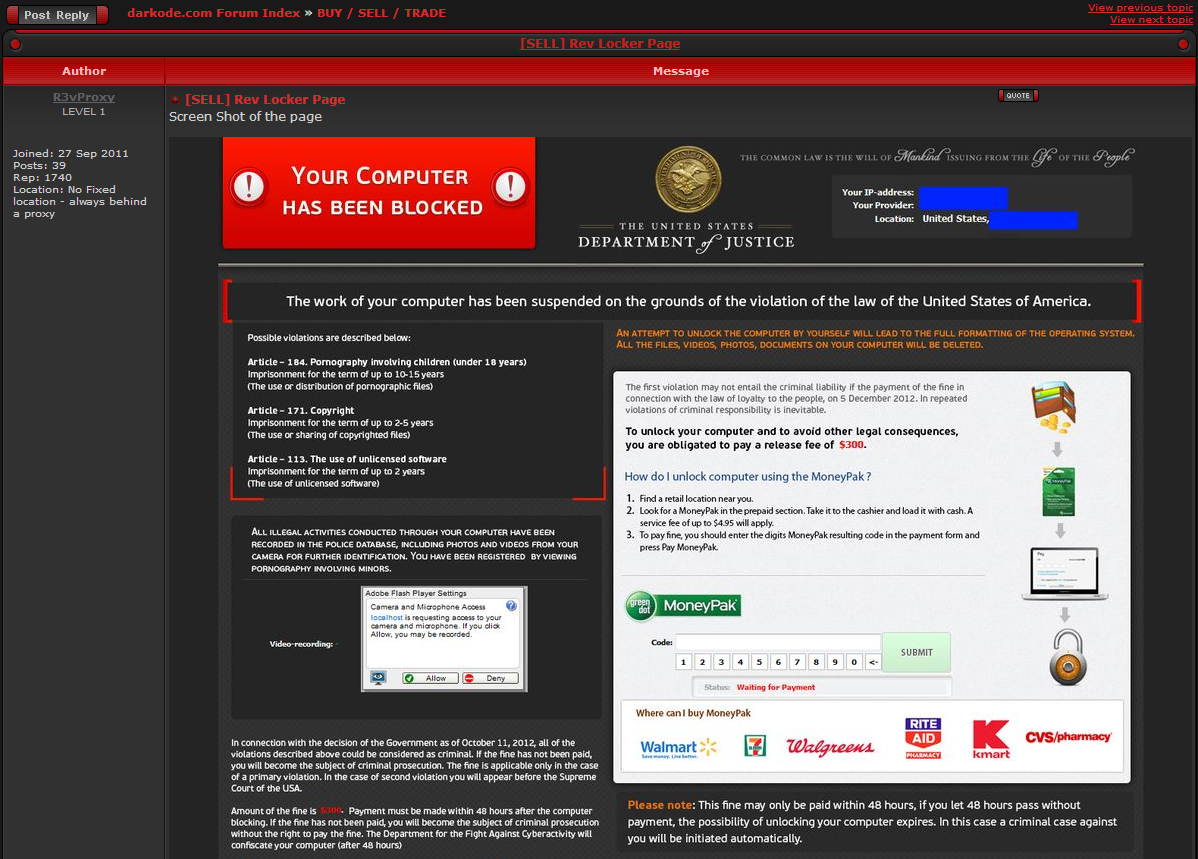
A 2012 sales thread on Darkode for Rev Locker.
In many ways, lockers were the precursors to the modern cybercrime scourge we now know as ransomware. The main reason lockers never took off as an existential threat to organizations worldwide was that there is only so much money locker users could reasonably demand via GreenDot cards.
But with the ascendance and broader acceptance of virtual currencies like Bitcoin, suddenly criminal hackers could start demanding millions of dollars from victims. And it stands to reason that a great many Darkode members who were never caught have since transitioned from lockers, exploit kits and GreenDot cards to doing what every other self-respecting cybercrook seems to be involved with these days: Locking entire companies and industries for ransomware payments.
One final observation about the Philbert indictment: It’s good to see the Canadian authorities working closely with the FBI on important cybercrime cases. Indeed, this investigation is remarkable for that fact alone. For years I’ve been wondering aloud why more American cybercriminals don’t just move to Canada, because historically there has been almost no probability that they will ever get caught — let alone prosecuted there. With any luck, this case will be the start of something new.




Seems like they’ve had Fubar by the balls. This could be the first of many charges as a result.
“Set/Reset Deadlines as to THOMAS KENNEDY MCCORMICK (4): Sentencing memoranda due by 1/19/2022. (Text entry; no document attached.)” from https://www.docketbird.com/court-cases/USA-v-Skorjanc-et-al/dcd-1:2018-cr-00359-202210
Matthew Philbert calling himself “broke bitcoin baron.” is a bit narcissistic don’t you think ?
You seem to be mixing the spelling of his surname. I see “Philbert” and “Filbert” multiple times.
Status updates and info on the DoJ website here:
https://www.justice.gov/usao-dc/us-v-thomas-mccormick
For me it was difficult to understand and understand, so I want to ask.
Guilty or not guilty after all.
Quite an interesting case, in my opinion!
Guilty is a court judgement. One can look guilty as heck, and the court set you free. Evidence says he is not a nice guy. So I would bet on him not being a “saint”.
“For years I’ve been wondering aloud why more American cybercriminals don’t just move to Canada, because historically there has been almost no probability that they will ever get caught — let alone prosecuted there.”
I wonder if Philbert would have even been investigated by Canadian authorities if the FBI did not contact them. So, if one is a cybercriminal based in Canada, don’t alert the FBI by “attacking” US citizens, businesses, etc.
Thank you, I feel a little better knowing that at least some times, these leaches on hardworking people are taken off the street/net. And congrats to the FBI.
(I didn’t put any of my emotional comments about suggested punishments in this post, but it was difficult not to)
No ones gonna mention how Krebs said the hard R twice uncensored in this post?
ahh un bon vieux Quebecois du quebec. Mais finalement un canadien en petrin.
Eille le gros, penses-y ben mais le ti criss va devoir arrêter de manger dla poutine pour un boutte. Pauv lui.
Eille le gros, penses-y ben mais le ti criss va devoir arrêter de manger dla poutine pour un boutte. Pauv lui.
I know it’s unlikely to happen but I’d like to see a lot of victim physical revenge on one of these slime balls.
…I think, once the whole story is told, he’s just a dupe…
…maybe a criminal, but a dupe nonetheless…
It is great to see that the Canadian government works together with the U.S. investigators and getting rid of cyber criminals – the more the better.
However, there are so many things that could simply be fixed directly in the U.S. – phone scammer support organizations like Onvoy LLC, Intelliquent do their business completely untouched by the FTC, FBI and other organizations that could simply shut them down and take their CEOs to jail… Sad.
I’m betting a beer this guy was working with K!NG. He was successfully arrested and prosecuted in the U.K. several years ago, slinging Reverton via malvertising and laundering the proceeds through Green Dot and other means. Small cyber crime world.
“For years I’ve been wondering aloud why more American cybercriminals don’t just move to Canada, because historically there has been almost no probability that they will ever get caught — let alone prosecuted there.”
I’m guessing there is far more of story behind this… would love to hear it.
I asked one of the Canadian feds in reporting this piece what they thought of my assessment (in advance of my printing it here), and they said it was spot on and so sad but true.