
Image: Shutterstock, iHaMoo.
Adam Griffin is still in disbelief over how quickly he was robbed of nearly $500,000 in cryptocurrencies. A scammer called using a real Google phone number to warn his Gmail account was being hacked, sent email security alerts directly from google.com, and ultimately seized control over the account by convincing him to click “yes” to a Google prompt on his mobile device.
Griffin is a battalion chief firefighter in the Seattle area, and on May 6 he received a call from someone claiming they were from Google support saying his account was being accessed from Germany. A Google search on the phone number calling him — (650) 203-0000 — revealed it was an official number for Google Assistant, an AI-based service that can engage in two-way conversations.
At the same time, he received an email that came from a google.com email address, warning his Google account was compromised. The message included a “Google Support Case ID number” and information about the Google representative supposedly talking to him on the phone, stating the rep’s name as “Ashton” — the same name given by the caller.
Griffin didn’t learn this until much later, but the email he received had a real google.com address because it was sent via Google Forms, a service available to all Google Docs users that makes it easy to send surveys, quizzes and other communications.
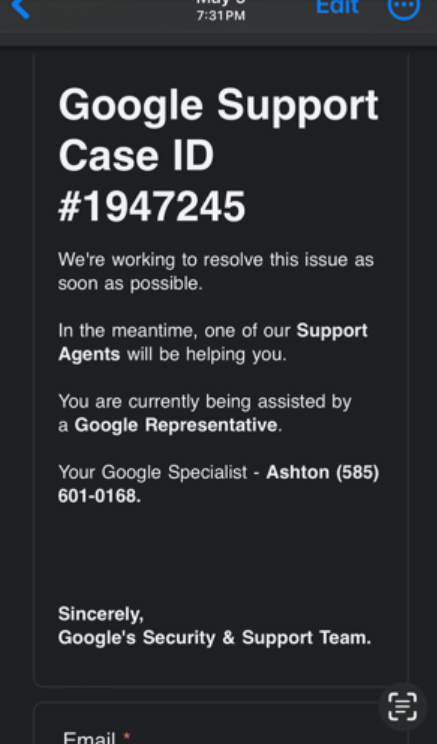
A phony security alert Griffin received prior to his bitcoin heist, via Google Forms.
According to tripwire.com’s Graham Cluely, phishers will use Google Forms to create a security alert message, and then change the form’s settings to automatically send a copy of the completed form to any email address entered into the form. The attacker then sends an invitation to complete the form to themselves, not to their intended victim.
“So, the attacker receives the invitation to fill out the form – and when they complete it, they enter their intended victim’s email address into the form, not their own,” Cluely wrote in a December 2023 post. “The attackers are taking advantage of the fact that the emails are being sent out directly by Google Forms (from the google.com domain). It’s an established legitimate domain that helps to make the email look more legitimate and is less likely to be intercepted en route by email-filtering solutions.”
The fake Google representative was polite, patient, professional and reassuring. Ashton told Griffin he was going to receive a notification that would allow him to regain control of the account from the hackers. Sure enough, a Google prompt instantly appeared on his phone asking, “Is it you trying to recover your account?”
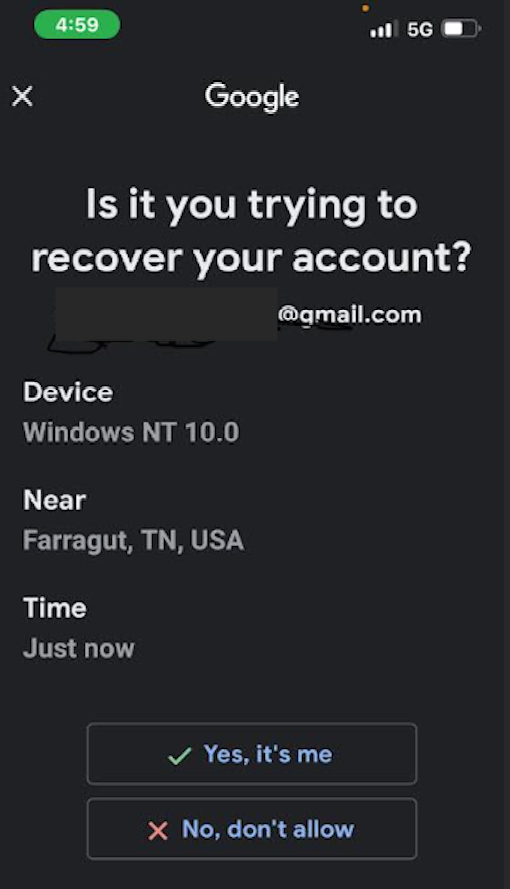
Adam Griffin clicked “yes,” to an account recovery notification similar to this one on May 6.
Griffin said that after receiving the pop-up prompt from Google on his phone, he felt more at ease that he really was talking to someone at Google. In reality, the thieves caused the alert to appear on his phone merely by stepping through Google’s account recovery process for Griffin’s Gmail address.
“As soon as I clicked yes, I gave them access to my Gmail, which was synched to Google Photos,” Griffin said.
Unfortunately for Griffin, years ago he used Google Photos to store an image of the secret seed phrase that was protecting his cryptocurrency wallet. Armed with that phrase, the phishers could drain all of his funds.
“From there they were able to transfer approximately $450,000 out of my Exodus wallet,” Griffin recalled.
Griffin said just minutes after giving away access to his Gmail account he received a call from someone claiming to be with Coinbase, who likewise told him someone in Germany was trying to take over his account.
Griffin said a follow-up investigation revealed the attackers had used his Gmail account to gain access to his Coinbase account from a VPN connection in California, providing the multi-factor code from his Google Authenticator app. Unbeknownst to him at the time, Google Authenticator by default also makes the same codes available in one’s Google account online.
But when the thieves tried to move $100,000 worth of cryptocurrency out of his account, Coinbase sent an email stating that the account had been locked, and that he would have to submit additional verification documents before he could do anything with it.
GRAND THEFT AUTOMATED
Just days after Griffin was robbed, a scammer impersonating Google managed to phish 45 bitcoins — approximately $4,725,000 at today’s value — from Tony, a 42-year-old professional from northern California. Tony agreed to speak about his harrowing experience on condition that his last name not be used.
Tony got into bitcoin back in 2013 and has been investing in it ever since. On the evening of May 15, 2024, Tony was putting his three- and one-year-old boys to bed when he received a message from Google about an account security issue, followed by a phone call from a “Daniel Alexander” at Google who said his account was compromised by hackers.
Tony said he had just signed up for Google’s Gemini AI (an artificial intelligence platform formerly known as “Bard”), and mistakenly believed the call was part of that service. Daniel told Tony his account was being accessed by someone in Frankfurt, Germany, and that he could evict the hacker and recover access to the account by clicking “yes” to the prompt that Google was going to send to his phone.
The Google prompt arrived seconds later. And to his everlasting regret, Tony clicked the “Yes, it’s me” button.
Then came another call, this one allegedly from security personnel at Trezor, a company that makes encrypted hardware devices made to store cryptocurrency seed phrases securely offline. The caller said someone had submitted a request to Trezor to close his account, and they forwarded Tony a message sent from his Gmail account that included his name, Social Security number, date of birth, address, phone number and email address.
Tony said he began to believe then that his Trezor account truly was compromised. The caller convinced him to “recover” his account by entering his cryptocurrency seed phrase at a phishing website (verify-trezor[.]io) that mimicked the official Trezor website.
“At this point I go into fight or flight mode,” Tony recalled. “I’ve got my kids crying, my wife is like what the heck is going on? My brain went haywire. I put my seed phrase into a phishing site, and that was it.”
Almost immediately, all of the funds he was planning to save for retirement and for his children’s college fund were drained from his account.
“I made mistakes due to being so busy and not thinking correctly,” Tony told KrebsOnSecurity. “I had gotten so far away from the security protocols in bitcoin as life had changed so much since having kids.”
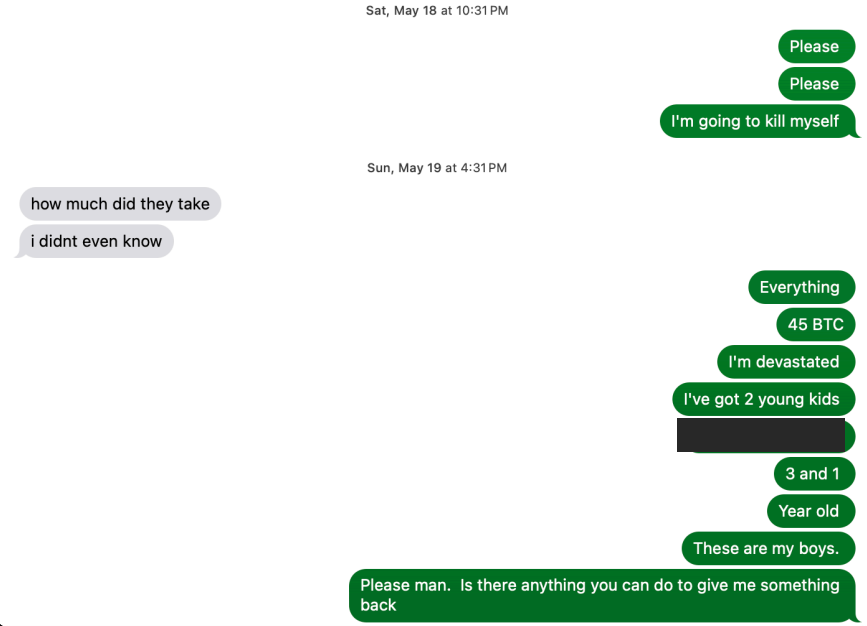
Tony shared this text message exchange of him pleading with his tormentors after being robbed of 45 bitcoins.
Tony said the theft left him traumatized and angry for months.
“All I was thinking about was protecting my boys and it ended up costing me everything,” he said. “Needless to say I’m devastated and have had to do serious therapy to get through it.”
MISERY LOVES COMPANY
Tony told KrebsOnSecurity that in the weeks following the theft of his 45 bitcoins, he became so consumed with rage and shame that he was seriously contemplating suicide. Then one day, while scouring the Internet for signs that others may have been phished by Daniel, he encountered Griffin posting on Reddit about the phone number involved in his recent bitcoin theft.
Griffin said the two of them were initially suspicious of each other — exchanging cautious messages for about a week — but he decided Tony was telling the truth after contacting the FBI agent that Tony said was working his case. Comparing notes, they discovered the fake Google security alerts they received just prior to their individual bitcoin thefts referenced the same phony “Google Support Case ID” number.
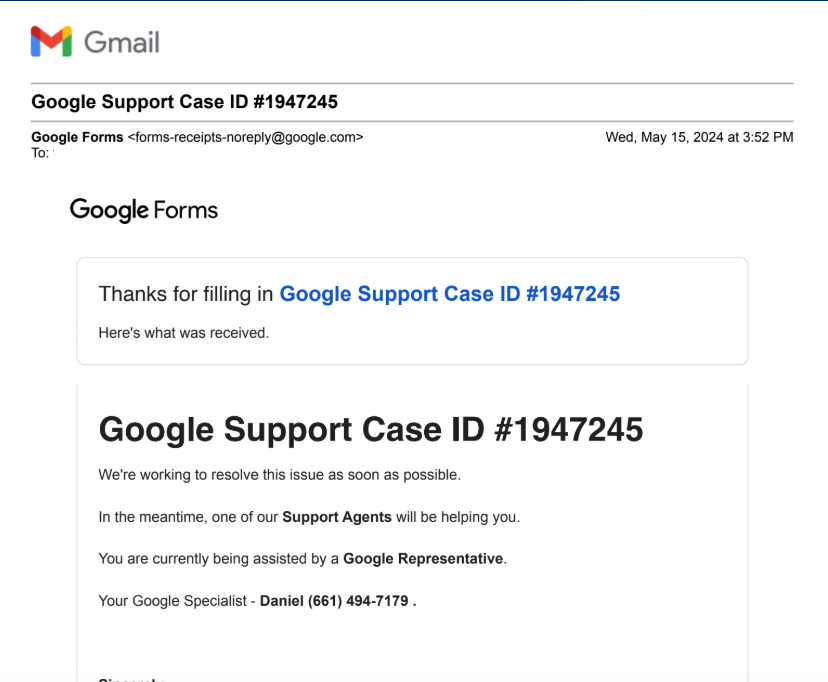
Adam Griffin and Tony said they received the same Google Support Case ID number in advance of their thefts. Both were sent via Google Forms, which sends directly from the google.com domain name.
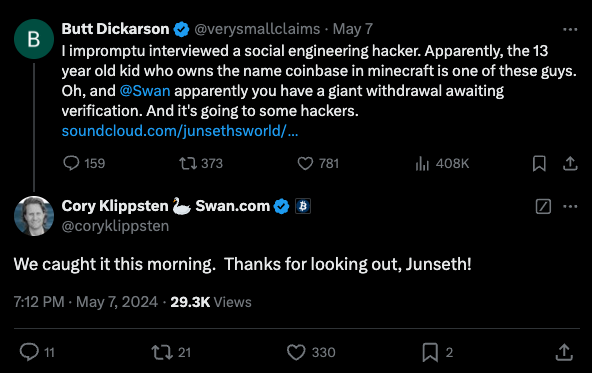
More importantly, Tony recognized the voice of “Daniel from Google” when it was featured in an interview by Junseth, a podcaster who covers cryptocurrency scams. The same voice that had coaxed Tony out of his considerable cryptocurrency holdings just days earlier also had tried to phish Junseth, who played along for several minutes before revealing he knew it was a scam.
Daniel told Junseth he was a teenager and worked with other scam callers who had all met years ago on the game Minecraft, and that he recently enjoyed a run of back-to-back Gmail account compromises that led to crypto theft paydays.
“No one gets arrested,” Daniel enthused to Junseth in the May 7 podcast, which quickly went viral on social media. “It’s almost like there’s no consequences. I have small legal side hustles, like businesses and shit that I can funnel everything through. If you were to see me in real life, I look like a regular child going to school with my backpack and shit, you’d never expect this kid is stealing all this shit.”
Daniel explained that they often use an automated bot that initiates calls to targets warning that their account is experiencing suspicious activity, and that they should press “1” to speak with a representative. This process, he explained, essentially self-selects people who are more likely to be susceptible to their social engineering schemes. [It is possible — but not certain — that this bot Daniel referenced explains the incoming call to Griffin from Google Assistant that precipitated his bitcoin heist].
Daniel told Junseth he and his co-conspirators had just scored a $1.2 million theft that was still pending on the bitcoin investment platform SwanBitcoin. In response, Junseth tagged SwanBitcoin in a post about his podcast on Twitter/X, and the CEO of Swan quickly replied that they caught the $1.2 million transaction that morning.
Apparently, Daniel didn’t appreciate having his voice broadcast to the world (or his $1.2 million bitcoin heist disrupted) because according to Junseth someone submitted a baseless copyright infringement claim about it to Soundcloud, which was hosting the recording.
The complaint alleged the recording included a copyrighted song, but that wasn’t true: Junseth later posted a raw version of the recording to Telegram, and it clearly had no music in the background. Nevertheless, Soundcloud removed the audio file.
“All these companies are very afraid of copyright,” Junseth explained in a May 2024 interview with the podcast whatbitcoindid.com, which features some of the highlights from his recorded call with Daniel.
“It’s interesting because copyright infringement really is an act that you’re claiming against the publisher, but for some reason these companies have taken a very hard line against it, so if you even claim there’s copyrighted material in it they just take it down and then they leave it to you to prove that you’re innocent,” Junseth said. “In Soundcloud’s instance, part of declaring your innocence is you have to give them your home address and everything else, and it says right on there, ‘this will be provided to the person making the copyright claim.'”
AFTERMATH
When Junseth asked how potential victims could protect themselves, Daniel explained that if the target doesn’t have their Google Authenticator synced to their Google cloud account, the scammers can’t easily pivot into the victim’s accounts at cryptocurrency exchanges, as they did with Griffin.
By default, Google Authenticator syncs all one-time codes with a Gmail user’s account, meaning if someone gains access to your Google account, they can then access all of the one-time codes handed out by your Google Authenticator app.
To change this setting, open Authenticator on your mobile device, select your profile picture, and then choose “Use without an Account” from the menu. If you disable this, it’s a good idea to keep a printed copy of one-time backup codes, and to store those in a secure place.
You may also wish to download Google Authenticator to another mobile device that you control. Otherwise, if you turn off cloud synching and lose that sole mobile device with your Google Authenticator app, it could be difficult or impossible to recover access to your account if you somehow get locked out.
Griffin told KrebsOnSecurity he had no idea it was so easy for thieves to take over his account, and to abuse so many different Google services in the process.
“I know I definitely made mistakes, but I also know Google could do a lot better job protecting people,” he said.
In response to questions from KrebsOnSecurity, Google said it can confirm that this was a narrow phishing campaign, reaching a “very small group of people.”
“We’re aware of this narrow and targeted attack, and have hardened our defenses to block recovery attempts from this actor,” the company said in a written statement, which emphasized that the real Google will never call you.
“While these types of social engineering campaigns are constantly evolving, we are continuously working to harden our systems with new tools and technical innovations, as well as sharing updated guidance with our users to stay ahead of attackers,” the statement reads.
Both Griffin and Tony say they continue to receive “account security” calls from people pretending to work for Google or one of the cryptocurrency platforms.
“It’s like you get put on some kind of list, and then those lists get recycled over and over,” Tony said.
Griffin said that for several months after his ordeal, he accepted almost every cryptocurrency scam call that came his way, playing along in the vain hope of somehow tricking the caller into revealing details about who they are in real life. But he stopped after his taunting caused one of the scammers to start threatening him personally.
“I probably shouldn’t have, but I recorded two 30-minute conversations with these guys,” Griffin said, acknowledging that maybe it wasn’t such a great idea to antagonize cybercriminals who clearly already knew everything about him. “One guy I talked to about his personal life, and then his friend called me up and said he was going to dox me and do all this other bad stuff. My FBI contact later told me not to talk to these guys anymore.”
Sound advice. So is hanging up whenever anyone calls you about a security problem with one of your accounts. Even security-conscious people tend to underestimate the complex and shifting threat from phone-based phishing scams, but they do so at their peril.
When in doubt: Hang up, look up, and call back. If your response to these types of calls involves anything other than hanging up, researching the correct phone number, and contacting the entity that claims to be calling, you may be setting yourself up for a costly and humbling learning experience.
Understand that your email credentials are more than likely the key to unlocking your entire digital identity. Be sure to use a long, unique passphrase for your email address, and never pick a passphrase that you have ever used anywhere else (not even a variation on an old password).
Finally, it’s also a good idea to take advantage of the strongest multi-factor authentication methods offered. For Gmail/Google accounts, that includes the use of passkeys or physical security keys, which are heavily phishing resistant. For Google users holding measurable sums of cryptocurrency, the most secure option is Google’s free Advanced Protection program, which includes more extensive account security features but also comes with some serious convenience trade-offs.




It is important NOT to use the cloud (syncing) with Google Authenticator – or any TOTP-based authenticator app. Convenience can cost you dearly. Instead, when you first setup MFA for a site, screenshot the QR code, print it out, label it, and put it in a 3-ring binder. This give you the ability to recreate your authenticator codes if you ever lose your device, or add a tablet, etc.
The risk of being locked out by loss of keys is also a threat vector no? It goes up if they are physically stored on paper.
There are so many alternatives to keep keys secure. A printed cleartext QR code is not the to go cause IT’S CLEAR TEXT.
Crumple up the QR code for security.
How about just not using Google? Or is that not possible?
Head in the sand may sound like a good idea, but this sort of attack works across platforms, yes MS too.
Apple + Yubi Authenticator.
Okay sure… but Google Forms + Google AI can’t detect the phrase “sincerely, google’s security and support team” and an obvious-AF spoofing attempt coming FROM THEIR PLATFORM, via userland, and flag that for at least ONE intelligent human eyeball? It’s not like this is the very first scammer claiming to be Google for this exact purpose, and yet their OWN PLATFORM isn’t even looking for that BASIC STRING yet? It’s 2025 folks and Google is one of the biggest and paradoxically LAZIEST security paradigms around. Maybe it’s the sheer size of the operation that causes them to lose the ability to notice things like this. Solution? BREAK THEM TF UP. Their DEFAULT is to sync these things together making them more dangerous than if they weren’t, and there’s near-nobody looking over any aspect of this preemptively AFAICT. Talk about feature creep and loss of mission perspective! Yeah obviously I’m not defending M$ or similar, but at what point does Google’s “everything all at once, synced” business model get an ACTUAL security review? (No doubt they’ll farm that out to their own AI next..) This is a dang TEEN using their own platform against their own users, abusing their own default settings, and then they shrug and say “oh, it’s very limited and narrow and all that”? You know they could do better and yet it’s the ubiquity of their “solutions” that by default endanger people. At what point do they get serious about thinking through their OWN PLATFORM? A: When the market or regulation absolutely forces that, amid massive resistance from the alphabet itself. No excuses.
100% agree. Regulation is the only answer. Unfortunately Alphabet would have an army of lawyers and lobbyists in reserve for that battle, as they would not submit too easily I imagine; not in the US anyway. It may be up to the EU to lead the charge and set a precedent.
“In Soundcloud’s instance, part of declaring your innocence is you have to give them your home address and everything else, and it says right on there, ‘this will be provided to the person making the copyright claim.’”
Correct me if I’m wrong, but this means I could file several phony copyright claims on well-known youtubers/streamers/creators and get their videos taken down, and, if they wanna prove their innocence and get the video re-instated, they’d have to send me their home address and other information. Essentially doxing whoever the phony claim is regarding. Is this not a terrible system? Are there other ways to prove your innocence? Am I missing something? What’s stopping people from abusing this right now whenever they come across a content creator they don’t particularly like.
Griffin’s biggest mistake wasn’t “just one bad click.” It was ever putting a photo of his seed words onto Google Photos.
At that point they’re already into his email, his authentication codes, et al. Yes, of course putting your pw into an image that you cloud host is pretty dumb – But Google has millions of users and they will do dumb things. That doesn’t let Goog off the hook for what they allow in-platform, by default, to allow dumb mistakes to become trivially exploited by minecraft teens.
It’s also possible to use a third-party security tool like 1Password to generate TOTP codes instead of Google Authenticator. That’s another option to disconnect your Google email and MFA.
Reading stuff like this I feel lucky to be in the IT world where security is pounded into our heads constantly. I’ve carried this into my personal life as well, which I think has served me well. If only I could get friends and family to listen.
There’s no reason to answer phone calls. If it’s important they’ll leave a message. If it’s strange, you can investigate.
Never commingle credentials and authentication. Keep your passwords in a password manager behind a ridiculously complex password that only you could know, and never write this down. Use a separate app for your 2FA and that app should be stand-alone. Keep your 2FA backup codes in yet another place behind completely different credentials.
Salt/Pepper your passwords for your most important accounts. You can store the base of the password, but then either prefix or suffix that password with something that you can’t forget, but would be hard for someone else to guess, and never store this anywhere. That way if they get into your password manager somehow, they still can’t blindly use your passwords to get into your important accounts.
Be suspicious of all emails, especially those that appear “dramatic”, encouraging you to take action now, have misspellings, seem completely random, etc. Never trust. Always investigate. “But that’s so much work!” Which is more work, investigating a few emails or phone calls or losing your retirement?
Using “a ridiculously complex password” is unnecessary. Several years ago, Stanford said using 4 words comprising 20 characters including spaces in just as secure and easier to remember than random junk.
For example, replace a password of ‘X4g#_DJn^/Ff!0’ with ‘Purple horses wear green haircuts’
Just don’t use G-mail or have a Google account at all.
One other bit of advice.
If your phone gets stolen, they can get at your email. Yes you might have face or touch ID
protection, but if the phone is stolen while it’s unlocked, bad luck.
Someone I know had their iPhone stolen out of their backpack. The thieves changed passwords
on a couple of her accounts, and would have changed it on her Apple ID too, but for the fact
that, unusually, she did not have the email account which she used for her Apple ID
configured in her phone’s email client.
I’m sure that most of us would.
I can’t speak for Android, but iOS 18 came with the ability to require face or touch ID for
specific apps.
I highly recommend protecting your phone’s email client this way, in case your phone is stolen.
Also, have 2FA configured on anything that can cause you to spend money (e.g. Patreon), and
use a 2FA app instead of SMS codes.
Android 15 has a new security feature called “Private Space” that also hides some apps. It seems better than the similar iOS feature because it allows unlocking with a unique password rather than using the same thing that unlocks the normal apps to also unlock the hidden ones.
Thanks to Brian for pointing out how a scam email can appear to come from Google.com.
How did the criminals know these 2 victims were the owners of crypto?
We don’t know that. But a number of cryptocurrency platforms have been hacked over the years, and those are a good starting point. Ledger had a huge user data leak a while back, something like 250k user accounts had their emails etc leaked. That’s just one example of many.
Ive noticed Ive gotten 5x more crypto phishing emails. Most impersonating Trezor. I think I may have signed up for it and my email is in the leak. They ask for KYC and always are from a bogus domain. I ended up port scanning them and one of them was using a legit hosting service from the Netherlands and they blocked my IP.
Its crazy they got the emails sent from a google.com domain. Very high end phishing attacks. The red alert is always the phone call.
I’ve worked in IT Sec for a while now, and I’ve dealt with a range of lower-level scams where “Microsoft” or the local telco call people to warn them their computer has been compromised. Most people seem aware now, but for those who are uncertain I’ve found asking them “When was the last time Microsoft or your Telco did something for you for free?” tends to be an eye-opener.
Unfortunately, this conversation usually happens after they’ve been called, but I use it when training groups or talking about security with staff, and it does seem to resonate, and get them thinking about scams. I know at least a few have passed it on to family and friends as well.
Here’s a free tip for “it pros”
it’s when you think your smarter then your online adversary
that’s when they have you by the balls..
Free tip for young “kids” criminals who think there are no consequences.
Ignorance is bliss until the tax man comith or worse.
Since switching to Google Authenticator after Raivo imploded I assumed that little green cloud icon meant my MFA keys were being backed up to the cloud, only viewable on my device…. not viewable from the cloud. Thanks for the tip.
This article also inspired me to ensure I had passkeys enabled anywhere I’m using TOTP MFA.
I agree perhaps Google could have done more, but once someone believes a person’s lies on the phone, it’s very hard for a company to program around a customer’s trust in bad actors.
It never ceases to amaze me that people don’t invest more in technology and security professionals when their wealth depends on it. It’s not just cryptocurrency, either, but much of our modern financial landscape is open to this kind of fraud. If you have $500k or millions of dollars to protect, paying someone who knows how to manage it even 1% of that sum is money well spent.
And I don’t even know where the myth that Google cares about people came from. They’re mainly an ad company now; don’t use them for anything else. Find a different ecosystem if you have different needs. The same can be said for many large jack-of-all-trades companies these days (Microsoft, Amazon, etc.). To them you’re just an anonymous piece of hay in a stack with a billion others, not some valued customer they’re going out of their way to actively protect.
“If you have $500k or millions of dollars to protect, paying someone who knows how to manage it even 1% of that sum is money well spent.”
How can such a person be sure that they’re hiring a guard rather than a thief?
As a truly epistemological question, it’s turtles all the way down. But if someone gave me a $5k retainer, I would easily be able to spell out the best practices I know for securing digital assets like cryptocurrencies. Ones that *don’t* involve giving them to me, and so I simply could not steal them. I would also suggest they go get a second opinion to independently verify my advice (or vice versa). A third or more, if they are really cautious. Tony would still have over $4.7 million if he had done that sort of basic due diligence.
How can you trust much of anything any more? I seem to trust the Internet less and less every day when it comes to money issues.
The other day I was trying to order something from a small man and wife store. It never did take my credit card number.
I got to looking and in trying to use a credit card there, it automatically signed me up without my permission for a payment service called “Link” which appears to be paired another service called “Stripe” and another called “Plaid”. To activate the system, they want my on-line banking username and password. Yikes!
I contacted the owners and offered to pay by check, but they said that they don’t accept checks. So now I am planning to go with a big store that presumably won’t use such a suspicious payment service. I would rather help the small mom and pop store out, but I have limits and giving out my on-line banking username and password is not something that I am willing to do.
MFA your accounts, and MFA your files too. To get to any of my data files:
o My computer/laptop/phone: You’ll need passwords to use my devices, another to access critical apps (email, bank, etc.) . My data files are also protected by file-based passwords (office type files, PDF files, etc.). So two-layers of defense for both apps and files.
o Cloud – You’ll need my cloud credentials (MFA protected). Since my critical data files are all invidually encrypted (as described above), you will need those passwords too.
It’s OK to store your files in any reputable/reliable cloud. Griffin should have individually protected his files. Protecting from potential break in’s aside – just keeping these files encrypted and away from Google’s prying eyes is a good thing too.
“account was being accessed from Germany”, “your credit card was used to charge something in Romania”, “did you just purchase an iPhone?”… I just answer “Yup” to all those scams. The scammers don’t know how to respond. A legit call would give me more details to confirm. Scammers don’t have details, just attention grabbing garbage.
What would be the most secure email? Something through a cloudflare registered domain? I use apple currently and two factor is forced on. The phone number on the account is a Google voice number and the google account has no email enabled and two factor.
Proton is good
goog should carry some of the blame for their anti security system that One access grants All access. Just like MS Passkey. Which is by far the worst security concept yet.
Crypto is not money, it is a token with potential value. There is good reason banks are insured and crypto is not.
Yup. Stupid is as stupid does….
I didn’t have any expectations concerning that title, but the more I was astonished. The author did a great job. I spent a few minutes reading and checking the facts. Everything is very clear and understandable. I like posts that fill in your knowledge gaps. This one is of the sort.
Dear Brian,
I am a little confused about the fact that you suggest that Google backs up the 2FA codes from the iPhone or Android to one’s Google account. Looking at my iPhone Google Authenticator app, I see that “your codes are being saved to your Google Account.” However, when I login to my Google account, there is no way I can actually view these codes (unless I am doing something wrong).
As I understand it, the criminal would need to be able to enter someone’s Google account. Then they have to hope that the person uses Google Authenticator and also backups their codes to the Google account. Then they need an iPhone or Android device, install Google Authenticator on it, and then login to the Google account (assuming they are not blocked by any additional security). At this point, the 2FA codes will populate themselves on the new device as they are downloaded from the cloud.
Then, the criminal must somehow have the credentials to the site of interest e.g. Coinbase or somehow manage to perform a reset using the Google email account and then later use the 2FA which they have populated into their app to access the account.
In other words, simply having access to the victims Google Account is not enough – the criminal must populate the 2FA codes in their own Authenticator app on their own device. It is not the case that the codes can be accessed by logging into Google on the web.
Is that correct?
In the example of the two victims mentioned in the story, they gave the phishers access to their Google accounts by clicking yes to the account recovery prompt they were sent. The attackers then used the access to those Google Authenticator codes to compromise third-party accounts tied to the app.
If a criminal has access to your Gmail and your one-time codes, they can effectively access any account tied to that Gmail account, if not directly then through a password reset, which would send a link to the compromised email account.
Hi Brian (again),
Thanks for the prompt reply. There is (as far as I know) no way to access the Google Authenticator codes from one’s google dot com account. The codes can be backed up to the account but you – as the account owner – cannot login to the web and see the codes (in the same way as you can view them on the Authenticator app on a phone).
So if someone has access to my google dot com account, they can see my email, photos, etc. But they cannot see my codes – even if my Authenticator app syncs the codes to my account. Right? You can only see the codes on the Authenticator app.
Hence my lack of understanding. How do the criminals access the one-time codes if they only have access to the Google account?
When you enable cloud sync for the google authenticator app, it will store the secret keys in the cloud and the secret keys are what is used to generate new codes.
Yes, I do understand this.
However, the impression one might get from the article is that gaining access to someone’s google dot com account, allows you to see the codes in the cloud e.g. on the web.
Whereas, as I understand it – correct me if I am incorrect – the hacker needs to have Google Authenticator on his phone, and login to the victim’s google account in order to generate the new codes.
This is a different process from phishing the google dot com account on the web.
Agree?
Would they not just link their own local instance of authenticator to the account?
My point is that – to achieve what the article suggests is happening – the hackers have to manage two things (as far as I understand it). First, they have to social engineer access to the target’s Google account. In the article’s case, they are calling the target and seemingly getting him to accept a password reset. Second, they have to login via their own Google Authenticator on their device. However, Google often demands 2FA even if 2FA is not set if one is logging in from an unfamiliar location. So, for all I know, the logging in on the Google Authenticator app would be blocked.
I don’t know the specifics – all I am saying is that if the hackers want access to the content of the Google account and also the Authenticator codes then it is a two-step process not one and that it is not possible to view the Authenticator codes on the Google web account.
If they control the email they (attackers) get the “is this you” email notification of someone trying to link authenticator to the account from strange phone / location. Right? And they click yes. If I’m wrong about that then I’m wrong about that detail, but they are getting past this step. I agree that it should NOT be that easy.
“only have access to the google account”
You’re asking how they accessed something… while they have access?
The simplest approach is that the phisher just signs into a phone/emulator with the app installed.
One could also just access the google API to fetch it the same way the app would.
Just because you cannot view it on some website doesn’t mean it is inaccessible – to the contrary, if you can access it in ANY way, anyone with the same level of access can in SOME way.
Senor Krebs..
fyi, it’s been documented that many german hackers have been footprinting and hacking for years
but via vpn or encrypt
How do you click on phone?
Would most traditional banks just sit by if one of their customers made an unusually large withdrawal? I would think that that they would try to add a little friction to the process of withdrawing all 4.5 million that it’s in a savings or checking account.
This is also something I find amazing. Here in the UK, if you try to transfer £5,000 to a regulated crypto exchange, you are likely to have the transfer suspended and have to spend ages dealing with intrusive anti-fraud measures. Yet in many of the stories I read from the US, it appears mainstream banks are allowing people to transfer six digit figures to crypto exchanges fairly casually, for example in ‘romance scams’. I simply do not understand how this can happen based on my experiences of the annoyance and restrictions when attempting to transfer a fraction of these amounts.
I have an Android cell phone with a 5 digit pin number. The number itself is the answer to a math problem and the math problem is easier to remember than the pin number. According to the security settings on my cell phone, it is encrypted (I don’t remember enabling the encryption).
I almost always have to call the caller back after having to enter the pin number and then figure out if the call is coming in via the cell phone company, Google Voice, or on Signal.
I also go through my apps occasionally to determine which ones I can delete. As far as I’m concerned, every app is a potential weak spot in the phone’s security.
One thing that I have thought about but not yet looked into doing is to use my old 3G smart phone as a wifi phone and split the tasks between them. I have the FreeOTP app but I don’t have much use for it away from the office unless maybe on my laptop. With the FreeOTP installed on the wifi phone, I could leave it at office if I didn’t need to carry it with me.
What would be really great, though, is if companies would send text messages via Signal for those of us who use Signal.
I read this article yesterday, and heard about Trezor for the first time(I have no investments in crypto). Then this morning, I received an email purporting to come from them to activate SecureEase, which they say should secure my wallet.
The actual sender was MS_eYAFr1@biud.com[.]br
How this possible, @kreb – has your mailing list being leaked?
You really think your email is only possibly on the wide world web because of BK’s mailing list? It’s called spam, they send it to more than just you personally. The fact that it’s coincidentally on point is as prescient as you imagine it to be.
@mealy
Do you automatically disregard any coincidence so long any other reason is possible?
I don’t think that is wise. But you do you, and I’ll do me.
Since you offer no useful evidence, yes, your “leak” hypothesis can be easily discarded. This site attracts many security professionals who probably, like me, give Brian a unique email address. So there would be better evidence of a compromise than your “actual sender” analysis. I know about Brian’s work because I started getting spam to an email address I had only given to TD Ameritrade, and he was reporting on that cluster of a breach. That was back in 2007; you’re breaking no new ground here. I respect him all the more for allowing your wild-goose-chase of a public accusation on his site. And I’m sure he’ll be the first to report it if he ever *does* suffer from such a breach!
As a regular here, mealy usually says it like it is. His comment may have been a bit on the snarky side and left you miffed but, he is not wrong.
As Impossibly Stupid also points out it is easy to jump to conclusions and point the finger of blame in the wrong direction however the best way to tackle this, is address the root cause, ie; email security.
There 2 free email masking/protection service I can suggest;
https://duckduckgo.com/email
https://relay.firefox.com/
both are email forwarding services that removes multiple types of hidden email trackers and lets you create multiple unique private email addresses on the fly, a bit like a post office box protects your residential address. Every time you visit a site or require email authentication, generate a new random address that is attached to your real email address. Simple.
First of all, at no time did I claim that Kreb is the definite reason for this. Neither do I think that Kreb would hide the fact that he was breached if he knew he was breached.
My approach to coincidences is not to just ignore them, but to explore every avenue. Also, many times that people are breached, they don’t know about it until it’s leaked or someone alerts to the fact or even to the possibility.
@mealy and @impossibly stupid – there is no need to get defensive on Krebs behalf. I’ve been following his blog for about 4 years now and have only respect for him and the work that he does. If someone suspected that there is a leak in my company(and people have reported as such to me in the past), I simply appreciate the heads up and look into it. I therefore do the same to others.
Hang on. You got spam in your inbox and suspect my site is responsible? If you have anything other than suspicions, please share.
Hi Brian,
All I have is the coincident like I mentioned. I’d never heard of Trezor and got a spam email about it the day after reading about it here.
The email address I subscribed with is not the same as the one I’m using to comment with here. I can give you more technical details about the email etc, if there is a direct email that I can communicate with you. Send me an email if you’re interested.
Hi Brian,
All I have is the coincident like I mentioned. I’d never heard of Trezor and got a spam email about it the day after reading about it here.
The email address I subscribed with is not the same as the one I’m using to comment with here. I can give you more technical details about the email etc, if there is a direct email that I can communicate with you. Send me an email if you’re interested.
I was deeply worried after reading this and then I remembered I have no money anywhere, so now I feel relieved…
Again, this is the “One Simple Rule” that could have protected against all of these – if you have an inbound call asking for information, get their ID/Name/Company extension or whatever, then say you’ll call back on the official number to discuss further. I’ve had legit inbound calls get very annoyed at me doing that, but I refuse to do anything unless I call back a valid number I found on the official website.
All the other things about not syncing auth/anything security to cloud, good security protocol, etc are all good, but that one weird trick with inbounds would stop every non-targeted social engineering attacks that I’ve heard of.
Phone call from my bank’s local branch. The one I use, I confirmed the number on their web page. Good to go ? Nah. The number had been cloned. I like the idea of asking for a number and calling back.
A phone call from Google? As if! Who would think such a thing exists? Maybe my world view is wrong, but I believe ANY call from “Google” about my gmail account MUST be a scammer, because Google has no intention of spending even 1/20th of a penny on supporting an email customer.
“I just won’t take calls from people named Ashton. No worries here.”
Google could help block an app attached to your account by integrating a LOCK NOTE feature within KEEP as Apple has with Apple NOTES..
I quit using Google Authenticator long ago, when I realized the app has no password, PIN, or biometric login to access it. That, alone, is a problem. Especially if someone commits the “IPhone in the bar” attack where they grab your unlocked phone and run.
This whole crypto Ponzi scheme is going to hit the dirt HARD, when it does. The time is unknown, but the fact that it WILL happen IS known.
Anyone who would put their entire retirement and kid’s college funds into Cryptocurrency has a serious lack of good judgement. I feel compassion for the man, but…my God, when is this madness going to end? End it will, but WHEN??