The author of a banking Trojan called Nuclear Bot — a teenager living in France — recently released the source code for his creation just months after the malware began showing up for sale in cybercrime forums. Now the young man’s father is trying to convince him not to act on a job offer in the United States, fearing it may be a trap set by law enforcement agents.
In December 2016, Arbor Networks released a writeup on Nuclear Bot (a.k.a. NukeBot) after researchers discovered the malware package for sale in the usual underground cybercrime forums for the price of USD $2,500.
The program’s author claimed the malware was written from scratch, but that it functioned similarly to the ZeuS banking trojan in that it could steal passwords and inject arbitrary content when victims visited banking Web sites.
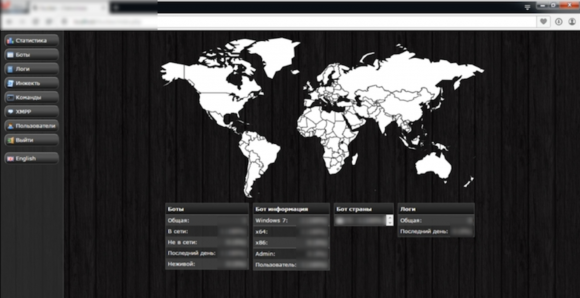
The administration panel for Nuclear Bot. Image: IBM X-Force.
Malware analysts at IBM’s X-Force research division also examined the code, primarily because the individual selling it claimed that Nuclear Bot could bypass Trusteer Rapport, an IBM security product that many banks offer customers to help blunt the effectiveness of banking trojans.
“These claims are unfounded and incorrect,” IBM’s researchers wrote. “Rapport detection and protection against the NukeBot malware are effective on all protection layers.”
But the malware’s original author — 18-year-old Augustin Inzirillo — begs to differ, saying he released the source code for the bot late last month in part because he wanted others be able to test his claims.
In an interview with KrebsOnSecurity, Inzirillo admits he wrote the Nuclear Bot trojan as a proof-of-concept to demonstrate a method he developed that he says bypasses Rapport. But he denies ever selling or marketing the malware, and maintains that this was done without his permission by an acquaintance with whom he shared the code privately.
“I’ve been interested in malware since I [was] a child, and I wanted to have a challenge,” Inzirillo said. “I was excited about this, and having nobody to share this with, I distributed the code to ‘friends’ who tried to profit off my work.”
After the source code for Nuclear Bot was released on Github, IBM followed up with a more in-depth examination of it, which argued that the author of the code appeared to release it in a failed bid to shore up his fragile ego.
According to IBM, a hacker calling himself “Gosya” tried to sell the malware in such a clumsy and inexperienced fashion that he managed to get himself banned from multiple cybercrime forums for violating specific rules about how such products should be sold.
“He did not have the malware tested and certified by forum admins, nor did he provide any test versions to members,” IBM researchers Limor Kessem and Ilya Kolmanovich wrote. “At the same time, he was attacked by existing competition, namely the FlokiBot vendor, who wanted to get down to the technical nitty gritty with him and find out if Gosya’s claims about his malware’s capabilities were indeed viable.”
The IBM authors continued:
“In posts where he replied to challenging questions, Gosya got nervous and defensive, raising suspicion among other forum members. This was likely a simple case of inexperience, but it cost him the trust of potential buyers.”
“For his next wrong move, Gosya started selling on additional forums under multiple monikers. When fraudsters realized that the same person was trying to vend under different names, they got even more suspicious that he was a ripper, misrepresenting or selling a product he does not possess. The issue got worse when Gosya changed the malware’s name to Micro Banking Trojan in one last attempt to buy it a new life.”
Inzirillo said the main reason he released his code was to prevent others from profiting off his creation. But now he says he regrets that decision as well.
“It was a big mistake, because now I know people will reuse my code to steal money from other people,” Inzirillo told KrebsOnSecurity in an online chat.
Inzirillo released the code on Github with a short note explaining his motivations, and included a contact email address at a domain (inzirillo.com) set up long ago by his father, Daniel Inzirillo.
KrebsOnSecurity also reached out to Augustin’s dad, and heard back from him roughly an hour before Augustin replied to requests for an interview. Inzirillo the elder said his son used the family domain name in his source code release as part of a misguided attempt to impress him.
“He didn’t do it for money,” said Daniel Inzirillo, whose CV shows he has built an impressive career in computer programming and working for various financial institutions. “He did it to spite all the cyber shitheads. The idea was that they wouldn’t be able to sell his software anymore because it was now free for grabs.”
Daniel Inzirillo said he’s worried because his son has expressed a strong interest in traveling to the United States after receiving a job offer from a supposed recruiter at a technology firm which said it was impressed by Augustin’s coding skills.
“I am very worried for him, because some technology company told him they wanted to fly him to the U.S. for a job interview as a result of him posting that online,” Daniel Inzirillo said. “There is a strong possibility that in one or two weeks he’s going to be flying to California, and I am concerned that maybe some guy in some law enforcement agency has his sights on him.” Continue reading →
 The biggest change this month for Windows users and specifically for people responsible for maintaining lots of Windows machines is that Microsoft has replaced individual security bulletins for patches with a single “Security Update Guide.”
The biggest change this month for Windows users and specifically for people responsible for maintaining lots of Windows machines is that Microsoft has replaced individual security bulletins for patches with a single “Security Update Guide.”




 “GameStop recently received notification from a third party that it believed payment card data from cards used on the GameStop.com website was being offered for sale on a website,” a company spokesman wrote in response to questions from this author.
“GameStop recently received notification from a third party that it believed payment card data from cards used on the GameStop.com website was being offered for sale on a website,” a company spokesman wrote in response to questions from this author.






 On Tuesday, the House approved a Senate resolution to roll back data privacy regulations enacted late last year at the Federal Communications Commission (FCC) that would block ISPs from selling to advertisers information about where you go and what you do online. President Trump has signaled his intent to sign the bill (
On Tuesday, the House approved a Senate resolution to roll back data privacy regulations enacted late last year at the Federal Communications Commission (FCC) that would block ISPs from selling to advertisers information about where you go and what you do online. President Trump has signaled his intent to sign the bill (

 Bowling Green State University in Ohio has more than 20,000 students and faculty, and like virtually any other mid-sized state school its Internet users are constantly under attack from scammers trying to phish login credentials for email and online services.
Bowling Green State University in Ohio has more than 20,000 students and faculty, and like virtually any other mid-sized state school its Internet users are constantly under attack from scammers trying to phish login credentials for email and online services.