U.S. federal prosecutors in Atlanta today unsealed indictments against two Vietnamese men and a Canadian citizen in connection with what’s being called “one of the largest reported data breaches in U.S. history.” The government isn’t naming the victims in this case, but all signs point to the 2011 hack of Texas-based email marketing giant Epsilon.
 The government alleges the defendants made more than $2 million blasting out spam to more than one billion email addresses stolen from several email service providers (ESPs), companies that manage customer email marketing on behalf of major corporate brands. The indictments further allege that the men sent the junk missives by hijacking the email servers used by these ESPs.
The government alleges the defendants made more than $2 million blasting out spam to more than one billion email addresses stolen from several email service providers (ESPs), companies that manage customer email marketing on behalf of major corporate brands. The indictments further allege that the men sent the junk missives by hijacking the email servers used by these ESPs.
“This case reflects the cutting-edge problems posed by today’s cybercrime cases, where the hackers didn’t target just a single company; they infiltrated most of the country’s email distribution firms,” said Acting U.S. Attorney John Horn. “And the scope of the intrusion is unnerving, in that the hackers didn’t stop after stealing the companies’ proprietary data—they then hijacked the companies’ own distribution platforms to send out bulk emails and reaped the profits from email traffic directed to specific websites.”
To be clear, prosecutors haven’t specifically outed Epsilon as the victim, nor did they name any of the other email service providers (ESPs) allegedly harmed by the defendants. But a press release issued today Horn’s office states that “the data breach into certain ESPs was the subject of a congressional inquiry and testimony before a U.S House of Representatives subcommittee on June 2, 2011.”
That date aligns with a June 2, 2011 House Energy and Commerce Committee panel on the data breaches at Sony and Epsilon. Epsilon officials could not be immediately reached for comment.
Update, 11:27 p.m. ET: Epsilon confirmed that it is among the victims in this case. See the end of this story for their full statement.
Original story:
In early April 2011, customers at dozens of Fortune 500 companies began complaining of receiving spam to email addresses they’d created specifically for use with those companies. On April 2, 2011, Epsilon started notifying consumers that hackers had stolen customer email addresses and names belonging to a “subset of its clients.”
Those clients were ESPs that send email to customers on behalf of some the biggest firms in the world. Epsilon didn’t name which ESPs were impacted, but the voluminous complaints from consumers about spam indicated that those ESPs served a broad range of major companies, including JP Morgan Chase, U.S. Bank, Barclays, Kroger, McDonalds, Walgreens, and Honda, to name but a few.
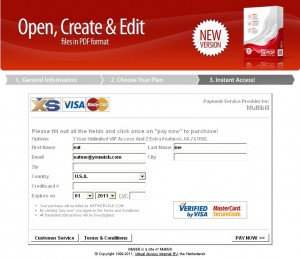
A scam web site that tried to sell copies of Adobe Reader.
As I noted in that April 2011 story, consumers had complained of received junk email with links to sites that tried to sell versions of software made by Adobe Systems Inc. Some of the sites reportedly even tried to sell copies of Adobe Reader — software that Adobe gives away for free.
Sure enough, the men indicted today are accused of hacking into a major ESP to steal more than a billion email addresses, which they allegedly used to promote knockoff versions of Adobe software (among other dubious products).
Prosecutors in Atlanta today unsealed indictments against Viet Quoc Nguyen and Giang Hoang Vu, both citizens of Vietnam who resided for a period of time in the Netherlands. The government also unsealed an indictment against David-Manuel Santos Da Silva, a Canadian citizen who was charged with conspiring with Nguyen and others to launder the proceeds of Nguyen’s alleged computer hacking offenses.
The government alleges that Nguyen used various methods — including targeted email phishing campaigns — to trick recipients at email marketing firms into clicking links to sites which attempted to exploit browser vulnerabilities in a bid to install malicious software. For more on those targeted attacks, see my Nov. 24, 2010 story, Spear Phishing Attacks Snag E-Mail Marketers.
Continue reading →
 Not sure whether your browser has Flash installed or what version it may be running? Browse to this link. The newest, patched version is 17.0.0.134 for Windows and Mac users. Adobe Flash Player installed with Google Chrome, as well as Internet Explorer on Windows 8.x, should automatically update to version 17.0.0.134.
Not sure whether your browser has Flash installed or what version it may be running? Browse to this link. The newest, patched version is 17.0.0.134 for Windows and Mac users. Adobe Flash Player installed with Google Chrome, as well as Internet Explorer on Windows 8.x, should automatically update to version 17.0.0.134.












