Distributed denial-of-service (DDoS) attacks designed to silence end users and sideline Web sites grew with alarming frequency and size last year, according to new data released this week. Those findings dovetail quite closely with the attack patterns seen against this Web site over the past year.
Arbor Networks, a major provider of services to help block DDoS assaults, surveyed nearly 300 companies and found that 38% of respondents saw more than 21 DDoS attacks per month. That’s up from a quarter of all respondents reporting 21 or more DDoS attacks the year prior.
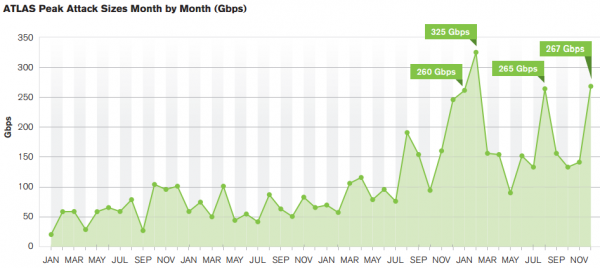
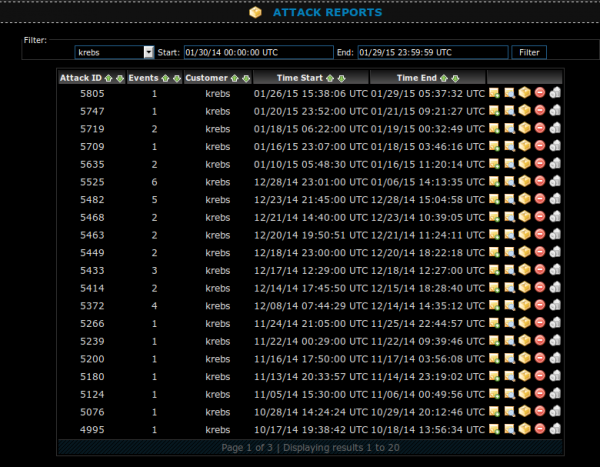
KrebsOnSecurity is squarely within that 38 percent camp: In the month of December 2014 alone, Prolexic (the Akamai-owned company that protects my site from DDoS attacks) logged 26 distinct attacks on my site. That’s almost one attack per day, but since many of the attacks spanned multiple days, the site was virtually under constant assault all month.
Arbor also found that attackers continue to use reflection/amplification techniques to create gigantic attacks. The largest reported attack was 400 Gbps, with other respondents reporting attacks of 300 Gbps, 200 Gbps and 170 Gbps. Another six respondents reported events that exceeded the 100 Gbps threshold. In February 2014, I wrote about the largest attack to hit this site to date — which clocked in at just shy of 200 Gbps.
According to Arbor, the top three motivations behind attacks remain nihilism vandalism, online gaming and ideological hacktivism— all of which the company said have been in the top three for the past few years.
“Gaming has gained in percentage, which is no surprise given the number of high-profile, gaming-related attack campaigns this year,” the report concludes.
Longtime readers of this blog will probably recall that I’ve written plenty of stories in the past year about the dramatic increase in DDoS-for-hire services (a.k.a. “booters” or “stressers”). In fact, on Monday, I published Spreading the Disease and Selling the Cure, which profiled two young men who were running both multiple DDoS-for-hire services and selling services to help defend against such attacks. Continue reading