In the wake of long-overdue media attention to revelations that a business unit of credit bureau Experian sold consumer personal data directly to an online service that catered to identity thieves, Experian is rightfully trying to explain its side of the story by releasing a series of talking points. This blog post is an attempt to add more context and fact-checking to those talking points.
Experian has posted several articles on its Web properties that lament the existence of “inaccurate information about Experian circulating in news outlets and other Web sites.”
“It’s no surprise that cybercrime and data breaches are hot topics for media and bloggers these days,” wrote Gerry Tschopp, senior vice president of public affairs at Experian. “Unfortunately, because of all the attention paid to these topics, we’ve seen some inaccurate information about Experian circulating in news outlets and other Web sites. I want to take a moment to clarify the facts and events.”
I’ve read this clarification closely, and it seems that Experian’s latest talking points deserve some clarification and fact-checking of their own. Below are Experian’s assertions of the facts (in bold), followed by some supplemental information glossed over by said statements of fact.
-No Experian database was accessed. The data in question have at all relevant times been owned and maintained, not by Experian, but by a company called US Info Search.
As all of my stories on this incident have explicitly stated, the government has said the data was not obtained directly from Experian, but rather via Columbus, Ohio-based US Info Search. US Info Search had a contractual agreement with a California company named Court Ventures, whereby customers of Court Ventures had access to the US Info Search data as well as Court Ventures’ data, and vice versa. Experian came into the picture in March 2012, when it purchased Court Ventures (along with all of its customers — including the proprietor of the identity theft service).
For its part, US Info Search says Experian’s explanation of the events is based on false statements and misrepresentations, and that the proprietor of the ID theft service paid Experian for his access using large cash payments sent to Experian via wire from Singapore.
“Experian provided access to records via a gateway that used multiple data sources and the suspect never had access to our service,” US Info Search CEO Marc Martin said in a written statement. “We, like many others, provide data to Experian, who in turn sold data to customers they approved and monitored. Our agreement with Court Ventures and subsequently Experian was to provide information that was being used for identity verification and fraud prevention.
-Further, Experian’s only involvement was that it purchased the assets of a company, Court Ventures, that provided access to US Info Search’s data to Court Ventures’ customers. Under that contract, customers of Court Ventures, including the criminal in this case, could access US Info Search’s data. This was not an Experian database, and specifically, this was not a credit database.
Experian has a duty to conduct “due diligence” on companies it wishes to acquire, because it knows that in purchasing a company it will acquire all of the company’s assets — including whatever debts, liabilities or poor decisions the previous owners may have incurred that end up creating problems down the road. Experian wants to blame everyone else, but by its own admission, Experian didn’t conduct proper due diligence on Court Ventures before acquiring the company. Addressing a U.S. Senate committee last December, Experian’s senior vice president of government policy, Tony Hadley, allowed that “during the due diligence process, we didn’t have total access to all the information we needed in order to completely vet that, and by the time we learned of the malfeasance nine months had expired, and the Secret Service came to us and told us of the incident. We were a victim, and scammed by this person.”
Also, if it wasn’t clear by now, Experian’s PR mantra on this crisis has been that “no Experian database was accessed,” in this fraud. But this mantra draws attention away from the real victim: Consumers whose information was sold by Experian’s company directly to an identity theft service. A critical question to ask to this line of thinking is: Why does it matter whose database it is, if it contains personal info and Experian profited from its sale? Continue reading →






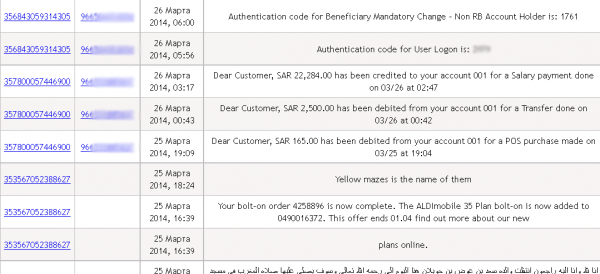

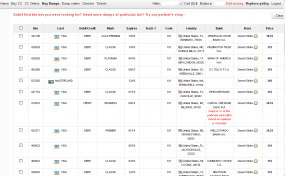
![The administration page of ssndob[dot]ru. Note the logged in user, ssndob@ssa.gov, is the administrator.](https://krebsonsecurity.com/wp-content/uploads/2014/03/ssndobadmin-600x444.png)