Over the past six months, “fans” of this Web site and its author have shown their affection in some curious ways. One called in a phony hostage situation that resulted in a dozen heavily armed police surrounding my home. Another opened a $20,000 new line of credit in my name. Others sent more than $1,000 in bogus PayPal donations from hacked accounts. Still more admirers paid my cable bill for the next three years using stolen credit cards. Malware authors have even used my name and likeness to peddle their wares.
But the most recent attempt to embarrass and fluster this author easily takes the cake as the most elaborate: Earlier this month, the administrator of an exclusive cybercrime forum hatched and executed a plan to purchase heroin, have it mailed to my home, and then spoof a phone call from one of my neighbors alerting the local police. Thankfully, I had already established a presence on his forum and was able to monitor the scam in real time and alert my local police well in advance of the delivery.
This would-be smear campaign was the brainchild of a fraudster known variously online as “Fly,” “Flycracker,” and MUXACC1 (muxa is transliterated Russian for “муха” which means “fly”). Fly is the administrator of the fraud forum “thecc[dot]bz,” an exclusive and closely guarded Russian language board dedicated to financial fraud and identity theft.
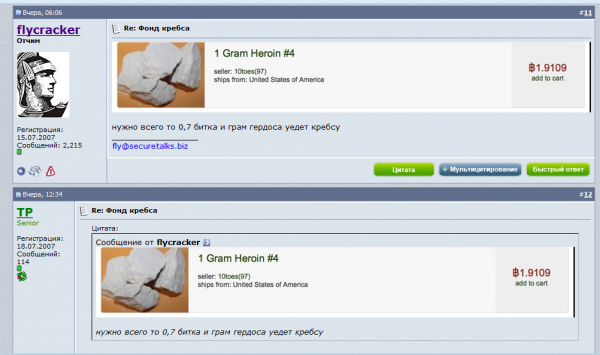
On July 14, Flycracker posted a new forum discussion thread titled, “Krebs Fund,” in which he laid out his plan: He’d created a bitcoin wallet for the exclusive purpose of accepting donations from other members. The goal: purchase heroin in my name and address from a seller on the Silk Road, an online black market that is only reachable via the Tor network. In the screenshot pictured above, Flycracker says to fellow members:
“Guys, it became known recently that Brian Krebs is a heroin addict and he desperately needs the smack, so we have started the “Helping Brian Fund”, and shortly we will create a bitcoin wallet called “Drugs for Krebs” which we will use to buy him the purest heroin on the Silk Road. My friends, his withdrawal is very bad, let’s join forces to help the guy! We will save Brian from the acute heroin withdrawal and the world will get slightly better!”
Together, forum members raised more than 2 bitcoins – currently equivalent to about USD $200. At first, Fly tried to purchase a gram of heroin from a Silk Road vendor named 10toes, an anonymous seller who had excellent and plentiful feedback from previous buyers as a purveyor of reliably good heroin appropriate for snorting or burning and inhaling (see screnshot below).
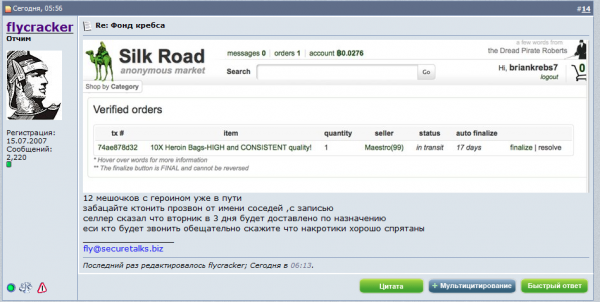
For some reason, that transaction with 10toes fell through, and Flycracker turned to another Silk Road vendor — Maestro — from whom he purchased a dozen baggies of heroin of “HIGH and consistent quality,” to be delivered to my home in Northern Virginia earlier today. The purchase was made using a new Silk Road account named “briankrebs7,” and cost 1.6532 bitcoins (~USD $165).
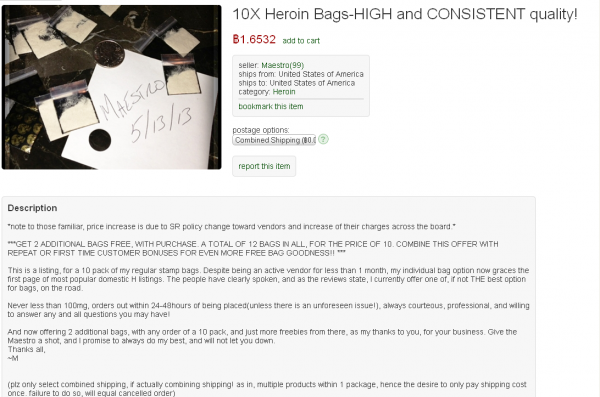
Flycracker ultimately bought 10 small bags of smack from Silk Road seller “Maestro.” The seller threw in two extra bags for free (turns out he actually threw in three extra bags).
In the screen shot below, Fly details the rest of his plan:
“12 sacks of heroin [the seller gives 2 free sacks for a 10-sacks order] are on the road, can anyone make a call [to the police] from neighbors, with a record? Seller said the package will be delivered after 3 days, on Tuesday. If anyone calls then please say that drugs are hidden well.”
Last week, I alerted the FBI about this scheme, and contacted a Fairfax County Police officer who came out and took an official report about it. The cop who took the report just shook his head incredulously, and kept saying he was trying to unplug himself from various accounts online with the ultimate goal of being “off the Internet and Google” by the time he retired. Before he left, the officer said he would make a notation on my report so that any officer dispatched to respond to complaints about drugs being delivered via mail to my home would prompted to review my report.
FOLLOWING THE MONEY
I never doubted Flycracker”s resolve for a minute, but I still wanted to verify his claims about having made the purchase. On that front I received assistance from Sara Meiklejohn, a graduate student at the University of California, San Diego who’s been analyzing the role of bitcoin and anonymity on the Silk Road. Meiklejohn confirmed that the bitcoin wallet linked to in Fly’s forum thread was indeed used to deposit two bitcoins into a purse controlled by anonymous individuals who help manage commerce on the Silk Road.
Meiklejohn and fellow researcher Damon McCoy, an assistant professor of computer science at George Mason University, have been mapping out a network of bitcoin wallets that are used exclusively by the curators of the Silk Road. If you wish to transact with merchants on the Silk Road, you need to fund your account with bitcoins. The act of adding credits appears to be handled by a small number of bitcoin purses.
“All Silk Road purchases are handled internally by Silk Road, which means money trades hands from the Silk Road account of the buyer to the Silk Road account of the seller,” explained Meiklejohn, author of the paper, A Fistful of Bitcoins: Characterizing Payments Among Men with No Names, to be released in October 2013 at the ACM Internet Measurement Conference in Barcelona, Spain.








![Anonymous antivirus scanning service -- captain-checker[dot]com -- bundled with the Styx exploit pack.](https://krebsonsecurity.com/wp-content/uploads/2013/07/c-checker-285x93.png)