The founder of Liberty Reserve, a digital currency that has evolved as perhaps the most popular form of payment in the cybercrime underground, was reportedly arrested in Spain this week on suspicion of money laundering. News of the law enforcement action may help explain an ongoing three-day outage at libertyreserve.com: On Friday, the domain registration records for that site and for several other digital currency exchanges began pointing to Shadowserver.org, a volunteer organization dedicated to combating global computer crime.
![]() According to separate reports in The Tico Times and La Nacion, two Costa Rican daily newspapers, police in Spain arrested Arthur Budovsky Belanchuk, 39, as part of a money laundering investigation jointly run by authorities in New York and Costa Rica.
According to separate reports in The Tico Times and La Nacion, two Costa Rican daily newspapers, police in Spain arrested Arthur Budovsky Belanchuk, 39, as part of a money laundering investigation jointly run by authorities in New York and Costa Rica.
Update, May 28, 9:11 a.m. ET: Libertyreserve.com is now resolving again, but its homepage has been replaced by a notice saying “THIS DOMAIN NAME HAS BEEN SEIZED,” and features badges from the U.S. Treasury Dept., U.S. Secret Service, and the DHS.
Original story:
The papers cited Costa Rican prosecutor José Pablo González saying that Budovsky, a Costa Rican citizen of Ukrainian origin, has been under investigation since 2011 for money laundering using Liberty Reserve, a company he created in Costa Rica. “Local investigations began after a request from a prosecutor’s office in New York,” Tico Times reporter L. Arias wrote. “On Friday, San José prosecutors conducted raids in Budovsky’s house and offices in Escazá, Santa Ana, southwest of San José, and in the province of Heredia, north of the capital. Budovsky’s businesses in Costa Rica apparently were financed by using money from child pornography websites and drug trafficking.”
For those Spanish-speaking readers out there, Gonzalez can be seen announcing the raids in a news conference documented in this youtube.com video (the subtitles option for English do a decent job of translation as well).
Liberty Reserve is a largely unregulated money transfer business that allows customers to open accounts using little more than a valid email address, and this relative anonymity has attracted a huge number of customers from underground economies, particularly cybercrime.
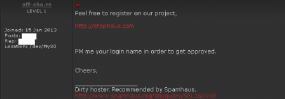
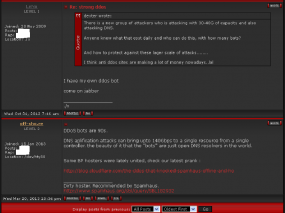
The trouble started on Thursday, when libertyreserve.com inexplicably went offline. The outage set off increasingly anxious discussions on several major cybercrime forums online, as many that work and ply their trade in malicious software and banking fraud found themselves unable to access their funds. For example, a bulletproof hosting provider on Darkode.com known as “off-sho.re” (a hacker profiled in this blog last week) said he stood to lose $25,000, and that the Liberty Reserve shutdown “could be the most massive ownage in the history of e-currency.”
That concern turned to dread for some after it became apparent that this was no ordinary outage. On Friday, the domain name servers for Libertyreserve.com were changed and pointed to ns1.sinkhole.shadowserver.org and ns2.sinkhole.shadowserver.org. Shadowserver is an all-volunteer nonprofit organization that works to help Internet service providers and hosting firms eradicate malware infections and botnets located on their servers.
In computer security lexicon, a sinkhole is basically a way of redirecting malicious Internet traffic so that it can be captured and analyzed by experts and/or law enforcement officials. In its 2011 takedown of the Coreflood botnet, for example, the U.S. Justice Department relied on sinkholes maintained by the nonprofit Internet Systems Consortium (ISC). Sinkholes are most often used to seize control of botnets, by interrupting the DNS names the botnet is programmed to use. Ironically, as of this writing Shadowserver.org is not resolving, possibly because the Web site is under a botnet attack (hackers from at least one forum threatened to attack Shadowserver.org in retaliation for losing access to their funds).
Reached via Twitter, a representative from Shadowserver declined to comment on the outage or about Liberty Reserve, saying “We are not able to provide public comment at this time.” I could find no official statement from the U.S. Justice Department on this matter either.
Libertyreserve.com is not the only virtual currency exchange that has been redirected to Shadowserver’s DNS servers. According to passive DNS data collected by the ISC, at least five digital currency exchanges —milenia-finance