Half of all “rogue” online pharmacies — sites that sell prescription drugs without requiring a prescription — got their Web site names from just two domain name registrars, a study released today found. The findings illustrate the challenges facing Internet policymakers in an industry that is largely self-regulated and rewards companies who market their services as safe havens for shadowy businesses.
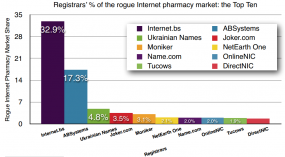
There are about 450 accredited domain name registrars worldwide, but at least one-third of all active rogue pharmacy sites are registered at Internet.bs, a relatively small registrar that purports to operate out of the Bahamas and aggressively markets itself as an “offshore” registrar. That’s according to LegitScript, a verification and monitoring service for online pharmacies.
LegitScript President John Horton said the company began to suspect that Internet.bs was courting the rogue pharmacy business when it became clear that the registrar has only two-tenths of one percent of the market share for new Web site name registrations. In a report (PDF) being released today, LegitScript said that a separate analysis of more than 9,000 “not recommended” pharmacies compiled by the National Association of Boards of Pharmacy suggested that Internet.bs is sponsoring nearly 44 percent of the Internet’s dodgy pill shops.
Asked whether he was concerned about allegations that his firm was targeting an industry that seeks out registrars who turn a blind eye to questionable businesses, Internet.bs President Marco Rinaudo replied that, on the contrary, LegitScript’s report was bound to be “excellent advertising for our company.”
Reached via phone at his home in Panama, Rinaudo said he was under no obligation to police whether his customers’ business may be in violation of some other nation’s laws, absent clear and convincing evidence that his registrants were operating illegally from their own country.
“Even though I understand they could bother some pharmacy lobby, if an industry likes us, what’s the problem with an online pharmacy, as long as they are operating legally from their own country?” Rinaudo asked. “We cannot accept pressure to shut down a legitimate business just because it is not pleasing to some political lobbying group. We and I personally make sure that all the domains that are in breach of an applicable law and for which we receive a complete report, will be acted on the same day.”