Leaked online chats between the co-owners of the world’s largest pharmacy spam operation reveal the extent to which illicit organizations in Russia purchase political protection, and bribe public officials into initiating or stalling law enforcement investigations.
Last month, there was a leak of more than four years of chat logs seized by Russian police who had arrested and interrogated Dmitry Stupin, allegedly the co-owner of GlavMed and the now-defunct SpamIt, organizations that paid spammers millions of dollars each month to promote fly-by-night online pharmacies.
In the the Jan. 9, 2010 chat between Stupin and Igor Gusev, the alleged other owner of GlavMed and SpamIt, Gusev has just learned that he and his operation are under investigation by Russian authorities (Gusev would be formally charged with illegal business activities in October 2010, forcing the closure of SpamIt). Gusev says he may be able to purchase shelter from the charges by funneling money to key Russian politicians who have influence over investigators.
 Specifically, Gusev suggests purchasing a sponsorship of the Volleyball Federation of Russia. The price tag for this is an official sponsorship fee of 10 million rubles (about $350,000 USD), plus $150,000 in cash. The official head of the federation, Nikolai Patrushev, is a powerful man in Russian law enforcement. Patrushev was director of the Russian FSB, the successor organization to the KGB, from 1999 to 2008; he has been secretary of the Security Council of Russia since 2008.
Specifically, Gusev suggests purchasing a sponsorship of the Volleyball Federation of Russia. The price tag for this is an official sponsorship fee of 10 million rubles (about $350,000 USD), plus $150,000 in cash. The official head of the federation, Nikolai Patrushev, is a powerful man in Russian law enforcement. Patrushev was director of the Russian FSB, the successor organization to the KGB, from 1999 to 2008; he has been secretary of the Security Council of Russia since 2008.
Sources say it is typical for Russian sport leagues and charities to be used as vehicles for funneling money into the pockets of policymakers. One example comes from a book by Lennart Dahlgren, former head of the Russian division of Swedish furniture maker IKEA. In Despite Absurdity: How I Conquered Russia While It Conquered Me, Dahlgren writes of having to pay bribes of 30 million Rubles ($1 million USD) to Russian charities that helped funnel money to bureaucrats and top officials.
In this chat, translated from Russian into English, Gusev mentions that a close friend of his family is a director general of the Volleyball Federation;
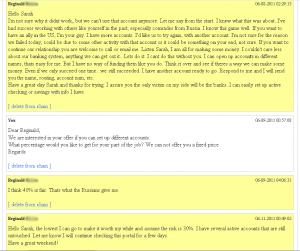
Gusev: We have big problems. Register fake mailbox somewhere. I will send you something very important.
Gusev: Let’s move Jabber to a new server and encrypt it. We’ll have a trusted communication channel. Everything is very bad 🙁
Gusev: asdas12334@mail.ru / mgadjadtwa2009. check the e-mail.
Gusev: Are you reading?
Stupin: Yes. Do not know what to say.
Gusev: There is nothing to say. We have only two ways: find someone from law enforcement, pay up and be under protection [or] be placed in jail for 7-9 years and do self-analysis. I have one more way out, but I could not decide regarding it in December, because it was very expensive. It is about 10 million rubles officially and 150K under the table.