A security firm revealed today that mysql.com, the central repository for widely-used Web database software, was hacked and booby-trapped to serve visitors with malicious software. The disclosure caught my eye because just a few days ago I saw evidence that administrative access to mysql.com was being sold in the hacker underground for just $3,000.
Web security firm Armorize stated in its blog that mysql.com was poisoned with a script that invisibly redirects visitors to a Web site that uses the BlackHole exploit pack, an automated exploit toolkit that probes visiting browsers for a variety of known security holes.
“It exploits the visitor’s browsing platform (the browser, the browser plugins like Adobe Flash, Adobe PDF, etc, Java, …), and upon successful exploitation, permanently installs a piece of malware into the visitor’s machine, without the visitor’s knowledge,” say the researchers. “The visitor doesn’t need to click or agree to anything; simply visiting mysql.com with a vulnerable browsing platform will result in an infection.”
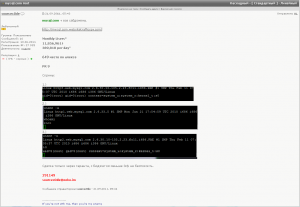
A screenshot of hacker on an exclusive Russian cybercrime forum selling root access to mysql.com for $3,000
Late last week, I was lurking on a fairly exclusive Russian hacker forum and stumbled upon a member selling root access to mysql.com. As part of his pitch, which was published on the criminal forum Sept. 21, the seller called attention to the site’s daily and monthly stats, and posted screen shots of a root login prompt in a bid to prove his wares.
The seller, ominously using the nickname “sourcec0de,” points out that mysql.com is a prime piece of real estate for anyone looking to plant an exploit kit: It boasts nearly 12 million visitors per month — almost 400,000 per day — and is ranked the 649th most-visited site by Alexa (Alexa currently rates it at 637).