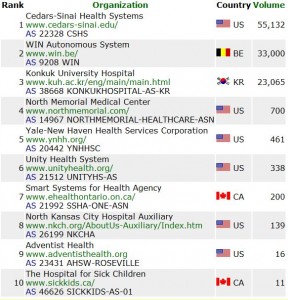
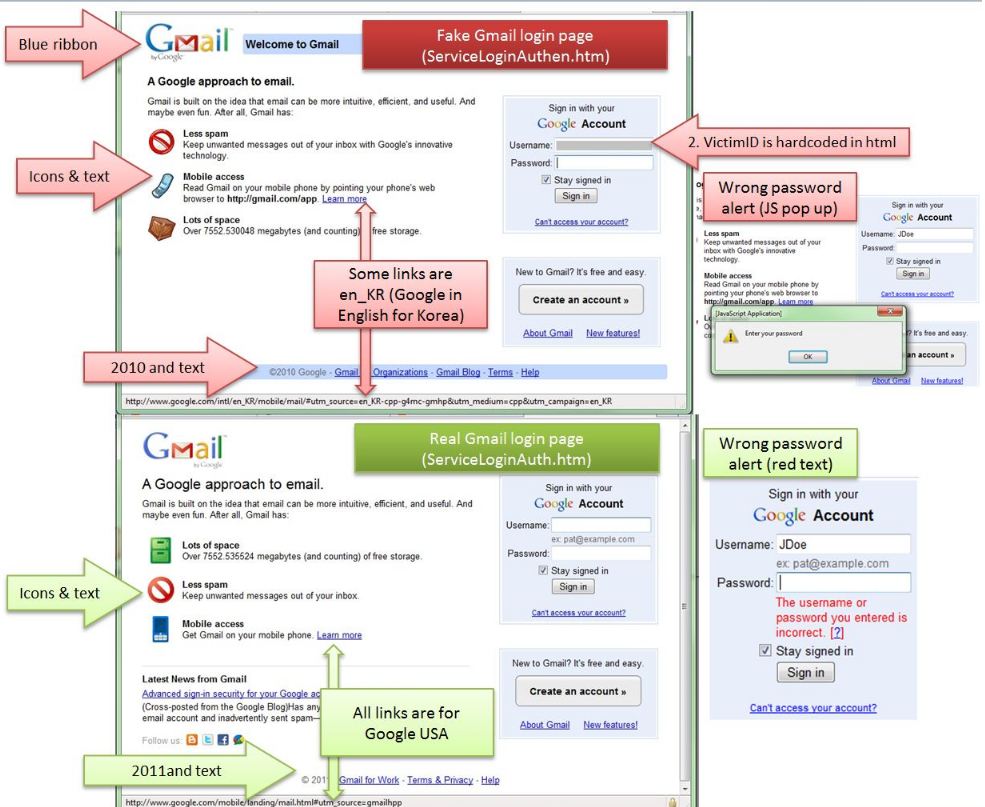
New research suggests that the majority of personal computers infected with malicious software may have arrived at that state thanks to a bustling underground market that matches criminal gangs who pay for malware installs with enterprising hackers looking to sell access to compromised PCs.
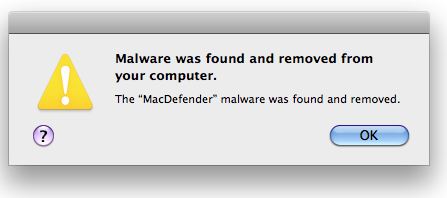
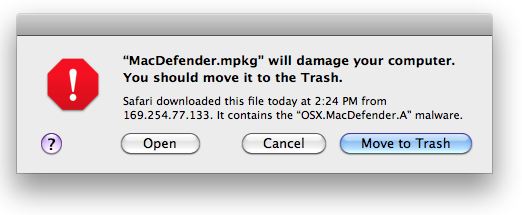
Pay-per-install (PPI) services are advertised on shadowy underground Web forums. Clients submit their malware—a spambot, fake antivirus software, or password-stealing Trojan—to the PPI service, which in turn charges rates from $7 to $180 per thousand successful installations, depending on the requested geographic location of the desired victims.
The PPI services also attract entrepreneurial malware distributors, or “affiliates,” hackers who are tasked with figuring out how to install the malware on victims’ machines. Typical installation schemes involve uploading tainted programs to public file-sharing networks; hacking legitimate websites in order to automatically download the files onto visitors; and quietly running the programs on PCs they have already compromised. Affiliates are credited only for successful installations, via a unique and static affiliate code stitched into the installer programs and communicated back to the PPI service after each install.
In August 2010, researchers at the University of California, Berkeley, and the Madrid Institute for Advanced Studies in Software Development Technologies infiltrated four competing PPI services by surreptitiously hijacking multiple affiliate accounts. They built an automated system to regularly download the installers being pushed by the different PPI services.
The snippet above is the introduction to a story I wrote for MIT Tech Review. Read the whole piece at this link.